1、背景
由于jenkins运行在k8s上能够更好的利用动态agent进行构建。所以写了个部署教程,亲测无坑
2、部署
1、创建ns
kubectl create namespace devops
2、kubectl apply -f jenkins.yml
apiVersion: v1
kind: ServiceAccount
metadata:
name: jenkins
namespace: devops
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: jenkins
rules:
- apiGroups: ["extensions", "apps"]
resources: ["deployments", "ingresses"]
verbs: ["create", "delete", "get", "list", "watch", "patch", "update"]
- apiGroups: [""]
resources: ["services"]
verbs: ["create", "delete", "get", "list", "watch", "patch", "update"]
- apiGroups: [""]
resources: ["pods"]
verbs: ["create", "delete", "get", "list", "patch", "update", "watch"]
- apiGroups: [""]
resources: ["pods/exec"]
verbs: ["create", "delete", "get", "list", "patch", "update", "watch"]
- apiGroups: [""]
resources: ["pods/log", "events"]
verbs: ["get", "list", "watch"]
- apiGroups: [""]
resources: ["secrets"]
verbs: ["get"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: jenkins
namespace: devops
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: jenkins
subjects:
- kind: ServiceAccount
name: jenkins
namespace: devops
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: jenkins
namespace: devops
spec:
selector:
matchLabels:
app: jenkins
template:
metadata:
labels:
app: jenkins
spec:
serviceAccount: jenkins
initContainers:
- name: fix-permissions
image: busybox:1.35.0
command: ["sh", "-c", "chown -R 1000:1000 /var/jenkins_home"]
securityContext:
privileged: true
volumeMounts:
- name: jenkinshome
mountPath: /var/jenkins_home
containers:
- name: jenkins
image: jenkins/jenkins:2.414.1-lts-jdk11
imagePullPolicy: IfNotPresent
env:
- name: JAVA_OPTS
value: -Dhudson.model.DownloadService.noSignatureCheck=true
ports:
- containerPort: 8080
name: web
protocol: TCP
- containerPort: 50000
name: agent
protocol: TCP
readinessProbe:
httpGet:
path: /login
port: 8080
initialDelaySeconds: 60
timeoutSeconds: 5
failureThreshold: 12
volumeMounts:
- name: jenkinshome
mountPath: /var/jenkins_home
- name: localtime
mountPath: /etc/localtime
volumes:
- name: jenkinshome
hostPath:
path: /opt/jenkins/jenkins_data
- name: localtime
hostPath:
path: /etc/localtime
---
apiVersion: v1
kind: Service
metadata:
name: jenkins
namespace: devops
labels:
app: jenkins
spec:
selector:
app: jenkins
ports:
- name: web
port: 8080
targetPort: web
- name: agent
port: 50000
targetPort: agent
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: jenkins
namespace: devops
spec:
ingressClassName: nginx
rules:
- host: jenkins.k8s.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: jenkins
port:
name: web
注意:镜像建议使用最新版本,因为jenkin平台默认提供了最新的插件,且无法选择版本,所以如果jenkins版本过低会导致插件不兼容问题
3、本地电脑配置host解析后,就可以用域名访问
4、查看pod日志获取初始化密码,也可以查看/opt/jenkins/jenkins_data/secrets/initialAdminPassword
5、安装必要插件
中文插件: Localization: Chinese
pipeline插件:Pipeline
k8s插件: Kubernetes
代码库管理插件:Git
6、配置k8s连接信息
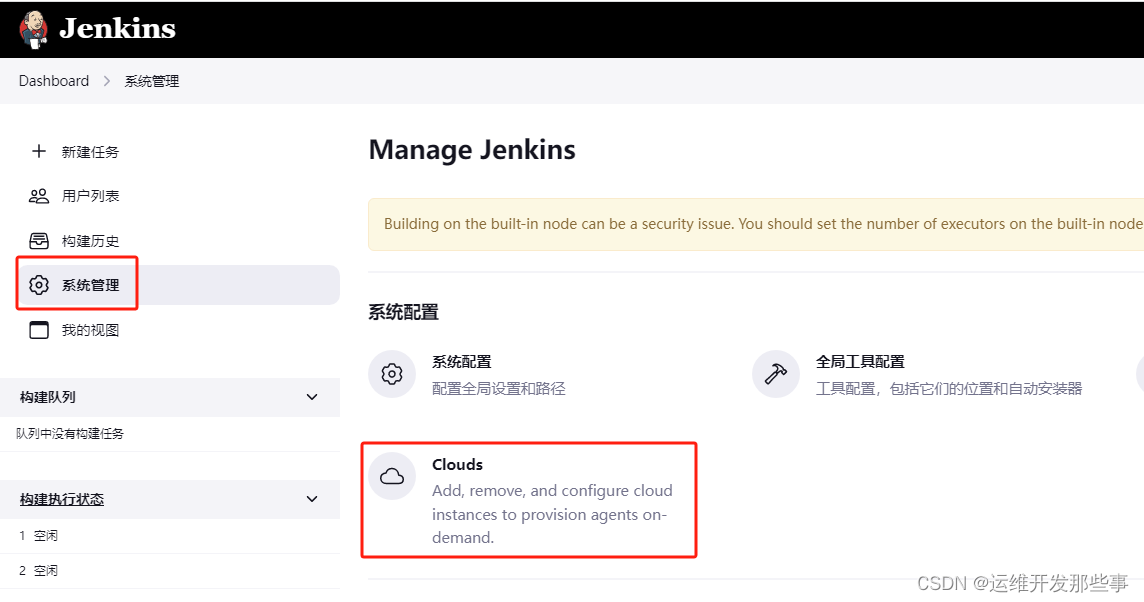

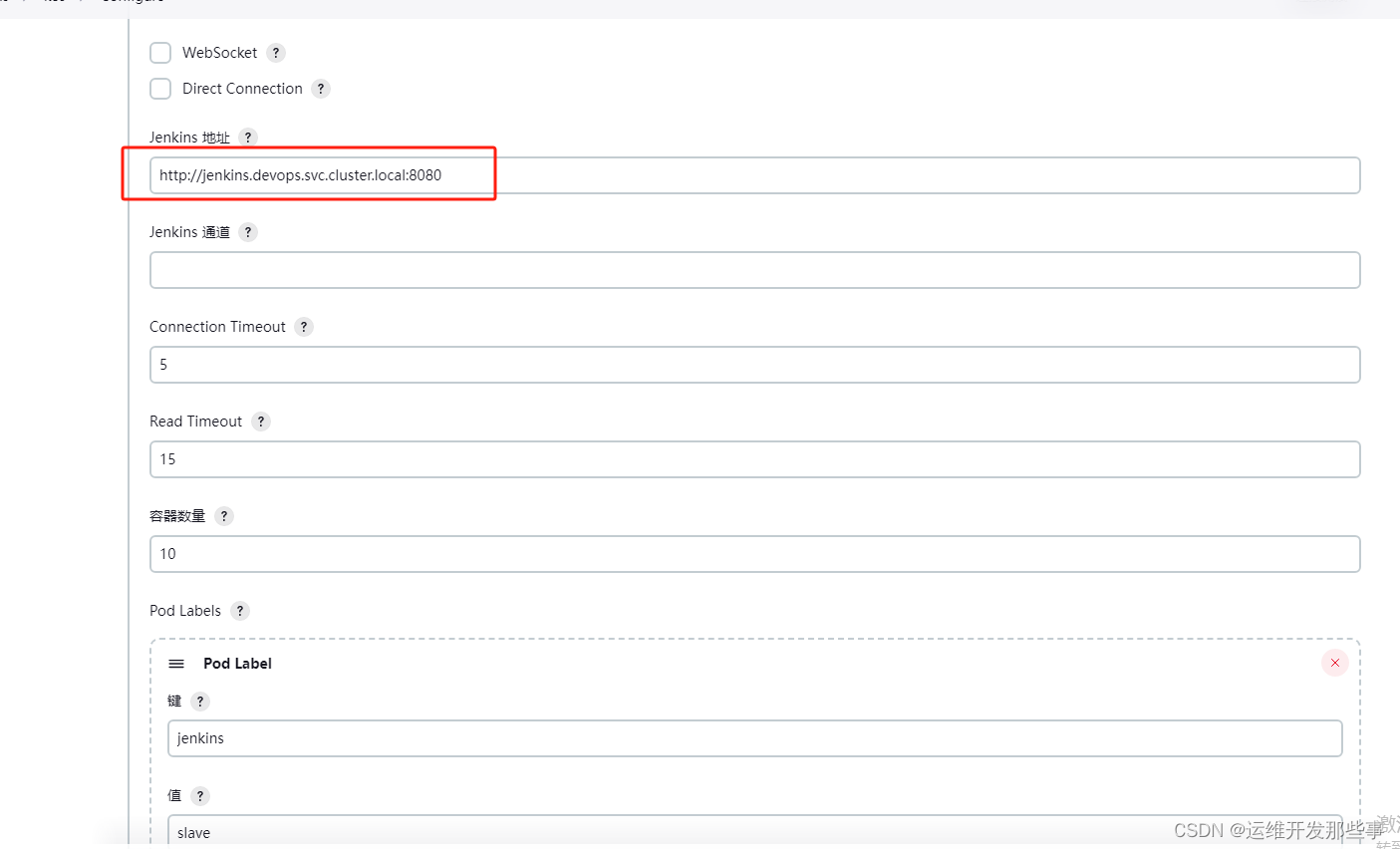
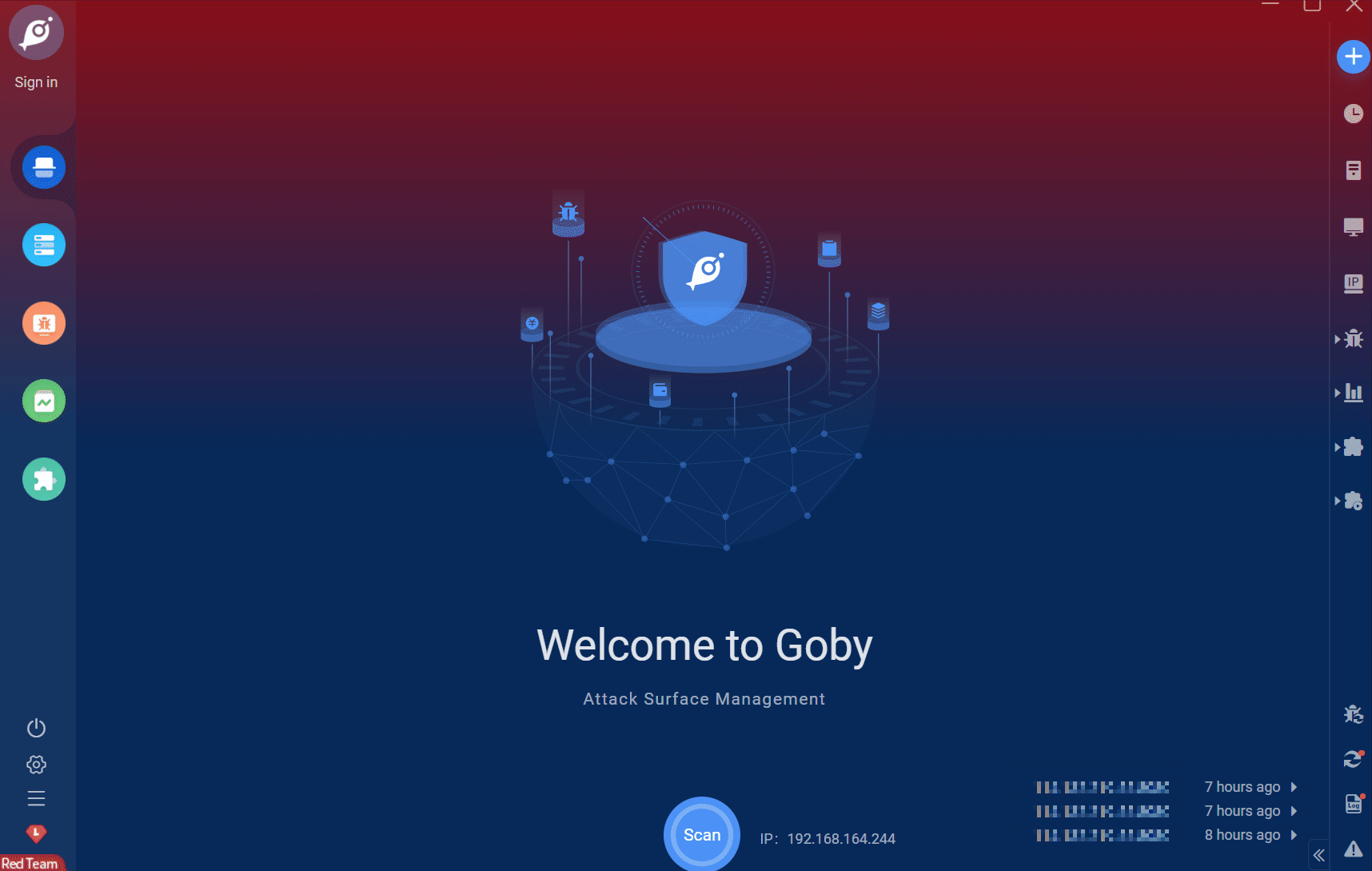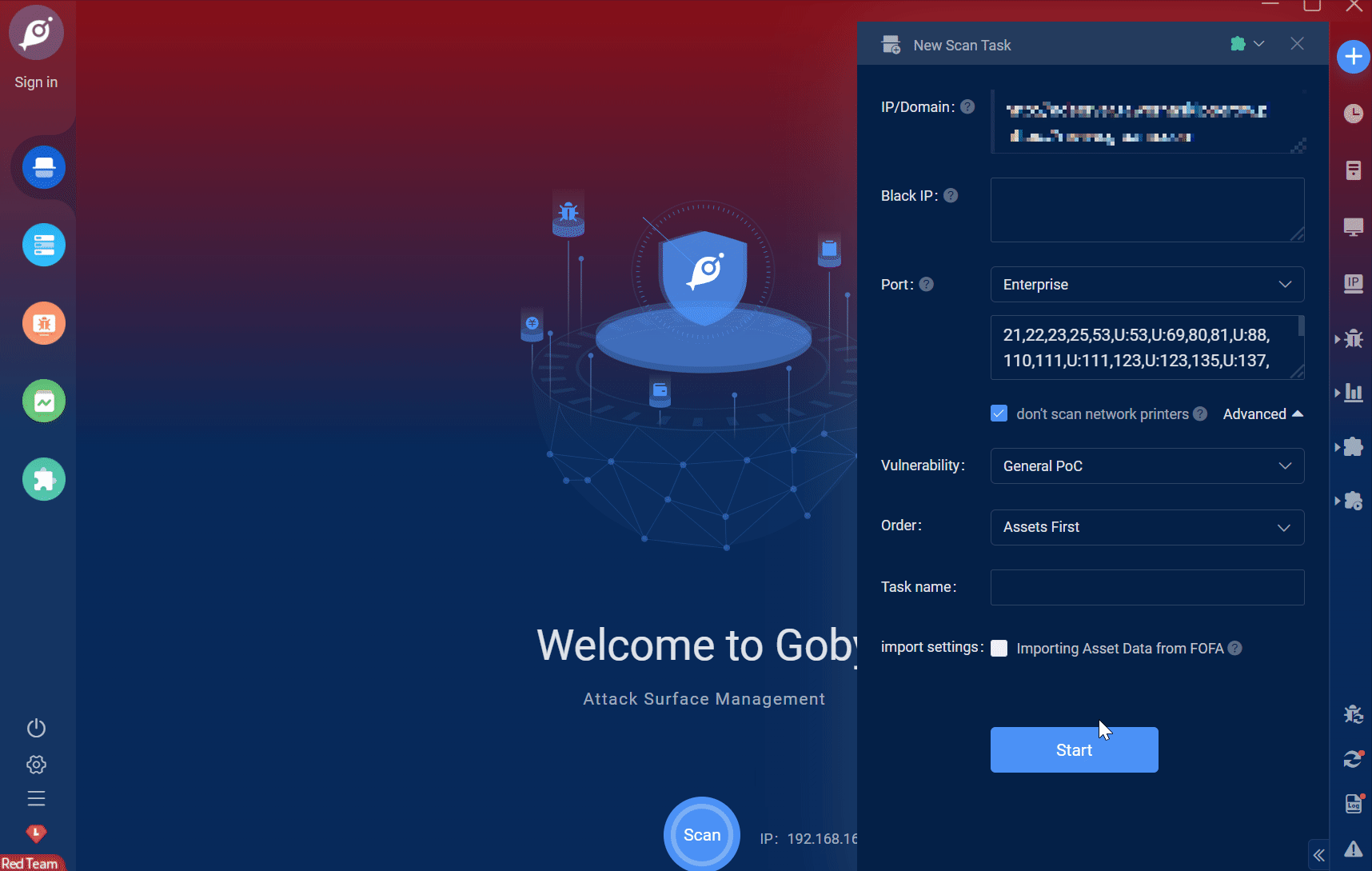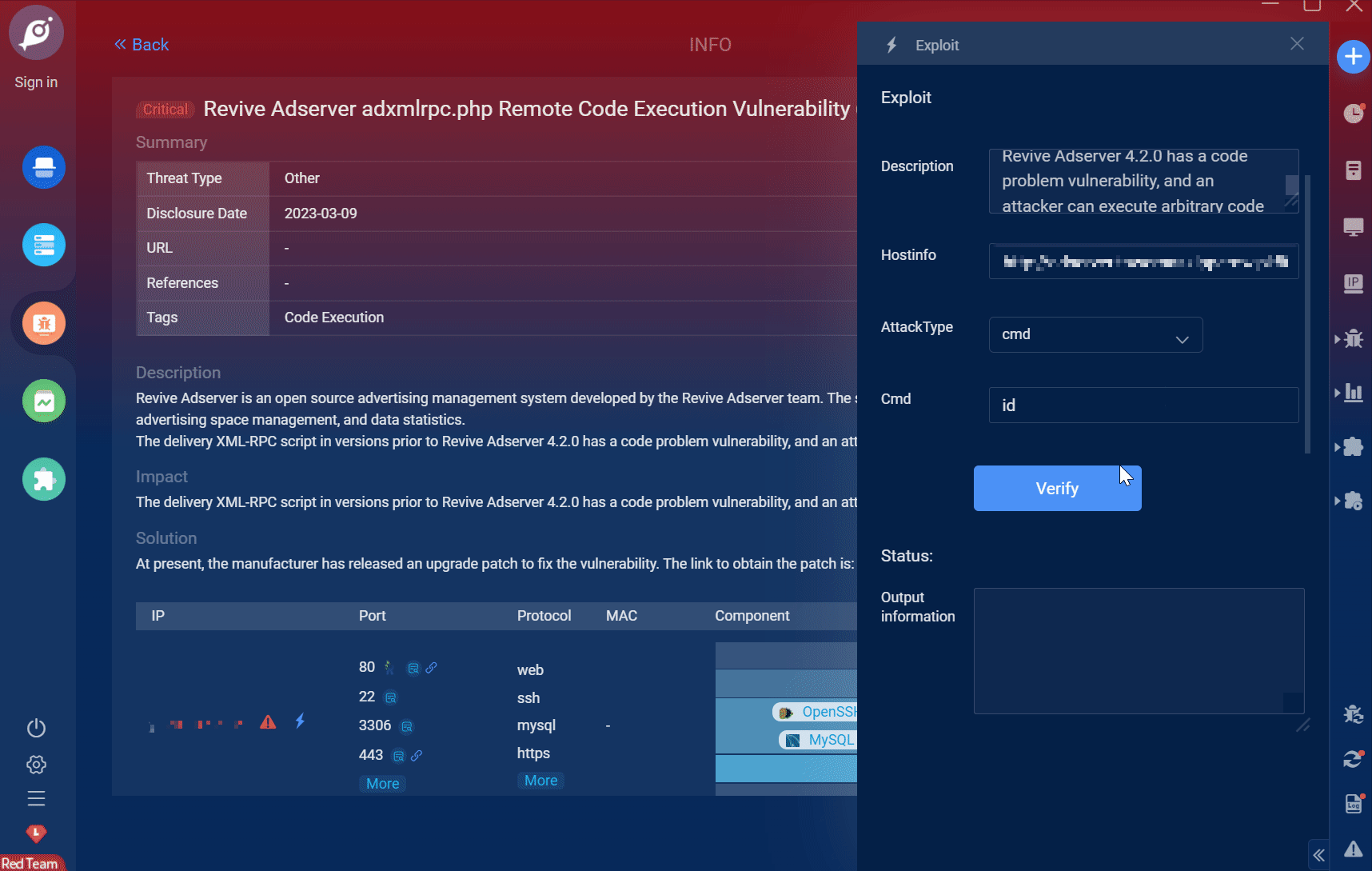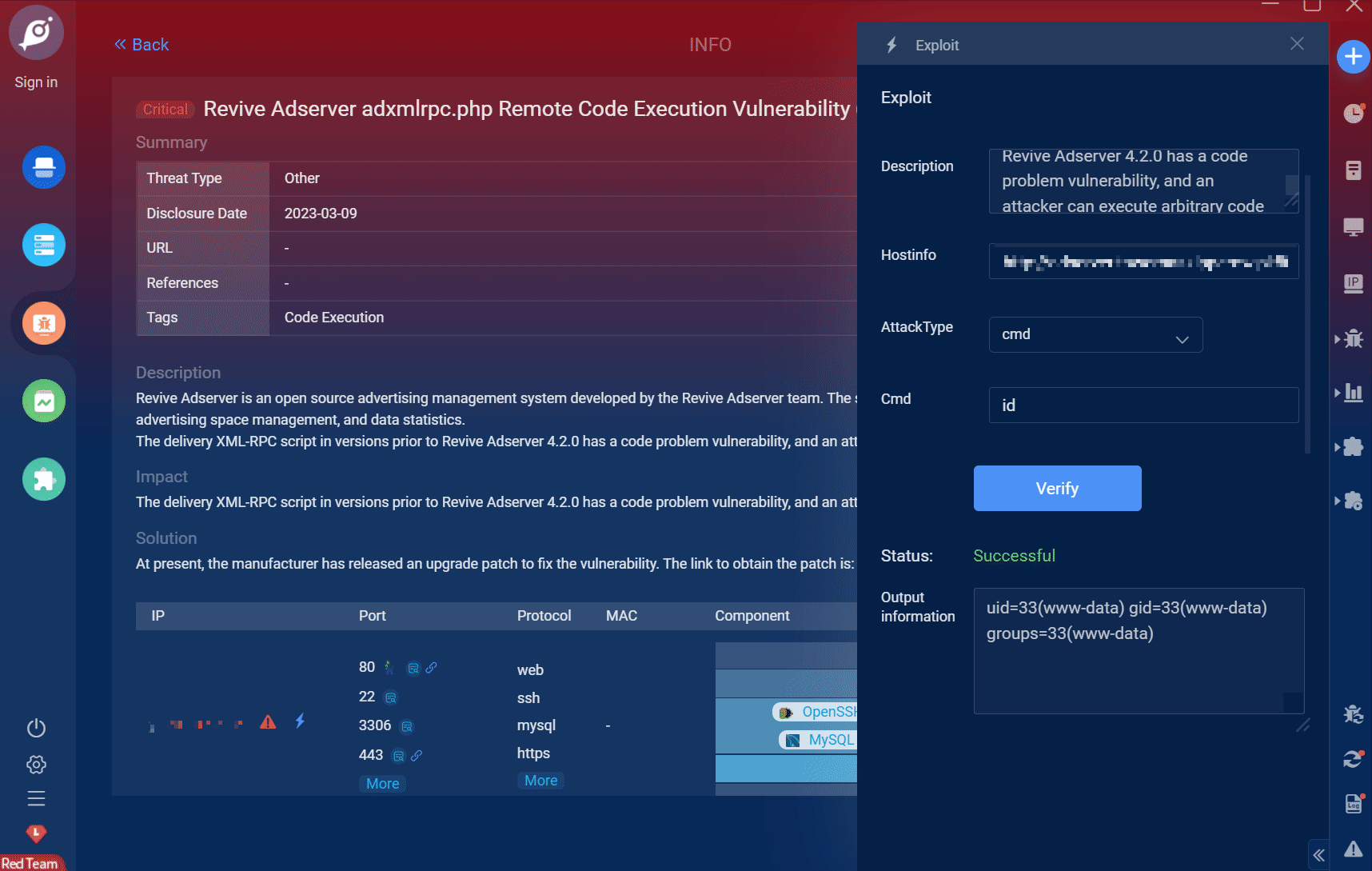
填写 以下内容 ,然后点击测试。
k8s地址 :https://kubernetes.default.svc.cluster.local
命名空间:devops
jenkins地址:http://jenkins.devops.svc.cluster.local:8080
由于之前部署的时候已经给jenkins用户访问k8s 的devops命名空间的权限,所以这里不需要配置kubeconfig认证也可直接访问
3、编写一条pipeline
这里用一个java项目的ci过程作为案例
def createVersion() {
// 定义一个版本号作为当次构建的版本,输出结果 20191210175842_69
return new Date().format('yyyyMMddHHmmss') + "_${env.BUILD_ID}"
}
pipeline{
agent{
kubernetes{
defaultContainer 'maven'
yaml '''
apiVersion: v1
kind: Pod
spec:
containers:
- name: maven
image: maven:3.8.1-jdk-8
command: ["sleep"]
args: ["99d"]
- name: docker
image: docker
command: ["sleep"]
args: ["99d"]
volumeMounts:
- mountPath: /var/run/docker.sock
name: docker-socket
volumes:
- name: docker-socket
hostPath:
path: /var/run/docker.sock
'''
}
}
environment {
tag = createVersion()
}
stages{
stage("pull code"){
steps{
script{
git 'https://gitee.com/uuei/java-devops-demo.git'
}
}
}
stage("mvn"){
steps{
script{
sh 'mvn clean package'
}
container('docker') {
script {
sh 'docker build -t java-demo:${tag} .'
}
}
}
}
}
}