查看网络
ifconfig 命令
┌──(root㉿kali)-[~] # eth0:有线网卡
└─# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.56.128 netmask 255.255.255.0 broadcast 192.168.56.255
inet6 fe80::20c:29ff:feb3:7991 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:b3:79:91 txqueuelen 1000 (Ethernet)
RX packets 39 bytes 17736 (17.3 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 45 bytes 17169 (16.7 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 4 bytes 240 (240.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4 bytes 240 (240.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
┌──(root㉿kali)-[~] # ifconfig -a 查看所有的接口
└─# ifconfig -a
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.56.128 netmask 255.255.255.0 broadcast 192.168.56.255
inet6 fe80::20c:29ff:feb3:7991 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:b3:79:91 txqueuelen 1000 (Ethernet)
RX packets 100 bytes 21639 (21.1 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 51 bytes 17593 (17.1 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 4 bytes 240 (240.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4 bytes 240 (240.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
┌──(root㉿kali)-[~]
└─# ifdown eth0
ifdown: unknown interface eth0
┌──(root㉿kali)-[~] # ifconfig eth0 down 停用eth0这块网卡
└─# ifconfig etho down
etho: ERROR while getting interface flags: 没有那个设备
┌──(root㉿kali)-[~]
└─# ifconfig eth0 down
┌──(root㉿kali)-[~]
└─# ifconfig
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 4 bytes 240 (240.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4 bytes 240 (240.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
┌──(root㉿kali)-[~] -a 查看所有活动和不活动的网卡
└─# ifconfig -a
eth0: flags=4098<BROADCAST,MULTICAST> mtu 1500
ether 00:0c:29:b3:79:91 txqueuelen 1000 (Ethernet)
RX packets 137 bytes 23889 (23.3 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 55 bytes 17865 (17.4 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 4 bytes 240 (240.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4 bytes 240 (240.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
┌──(root㉿kali)-[~] # ifconfig eth0 up 启用这块网卡
└─# ifconfig eth0 up
┌──(root㉿kali)-[~]
└─# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.56.128 netmask 255.255.255.0 broadcast 192.168.56.255
inet6 fe80::20c:29ff:feb3:7991 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:b3:79:91 txqueuelen 1000 (Ethernet)
RX packets 142 bytes 24471 (23.8 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 65 bytes 18883 (18.4 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 4 bytes 240 (240.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4 bytes 240 (240.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
iwconfig 检查无线网卡
┌──(root㉿kali)-[~]
└─# iwconfig
lo no wireless extensions.
eth0 no wireless extensions.
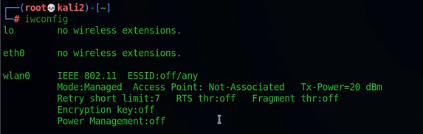
查看ifconfig 参数
# eth0: 网卡名称,不固定
# inet:IP地址
# netmask :子网掩码
# broadcast :广播地址
# inet6 :支持ipv6
# ether :mac地址
# 1000 :传输速率1000M
# RX packets:接收了多少个报文
# TX packets:发送了多少个报文
# RX errors:是否丢包
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.56.128 netmask 255.255.255.0 broadcast 192.168.56.255
inet6 fe80::20c:29ff:feb3:7991 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:b3:79:91 txqueuelen 1000 (Ethernet)
RX packets 142 bytes 24471 (23.8 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 65 bytes 18883 (18.4 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
ip 命令
查看IP地址 不能查看ip的状态 是否丢包
┌──(root㉿kali)-[~] # ip address show
└─# ip address show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:b3:79:91 brd ff:ff:ff:ff:ff:ff
inet 192.168.56.128/24 brd 192.168.56.255 scope global dynamic noprefixroute eth0
valid_lft 1380sec preferred_lft 1380sec
inet6 fe80::20c:29ff:feb3:7991/64 scope link noprefixroute
valid_lft forever preferred_lft forever
┌──(root㉿kali)-[~]
└─# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:b3:79:91 brd ff:ff:ff:ff:ff:ff
inet 192.168.56.128/24 brd 192.168.56.255 scope global dynamic noprefixroute eth0
valid_lft 1377sec preferred_lft 1377sec
inet6 fe80::20c:29ff:feb3:7991/64 scope link noprefixroute
valid_lft forever preferred_lft forever
┌──(root㉿kali)-[~]
└─# ip -help
Usage: ip [ OPTIONS ] OBJECT { COMMAND | help }
ip [ -force ] -batch filename
where OBJECT := { address | addrlabel | amt | fou | help | ila | ioam | l2tp |
link | macsec | maddress | monitor | mptcp | mroute | mrule |
neighbor | neighbour | netconf | netns | nexthop | ntable |
ntbl | route | rule | sr | tap | tcpmetrics |
token | tunnel | tuntap | vrf | xfrm }
OPTIONS := { -V[ersion] | -s[tatistics] | -d[etails] | -r[esolve] |
-h[uman-readable] | -iec | -j[son] | -p[retty] |
-f[amily] { inet | inet6 | mpls | bridge | link } |
-4 | -6 | -M | -B | -0 |
-l[oops] { maximum-addr-flush-attempts } | -br[ief] |
-o[neline] | -t[imestamp] | -ts[hort] | -b[atch] [filename] |
-rc[vbuf] [size] | -n[etns] name | -N[umeric] | -a[ll] |
-c[olor]}
更改IP地址
临时更改
ifconfig eth0 192.168.56.66 使用的是默认子网掩码 应用场景:排错,调试网络
┌──(root㉿kali)-[~]
└─# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:b3:79:91 brd ff:ff:ff:ff:ff:ff
inet 192.168.56.128/24 brd 192.168.56.255 scope global dynamic noprefixroute eth0
valid_lft 1202sec preferred_lft 1202sec
inet6 fe80::20c:29ff:feb3:7991/64 scope link noprefixroute
valid_lft forever preferred_lft forever
┌──(root㉿kali)-[~]
└─# ifconfig eth0 192.168.56.66
┌──(root㉿kali)-[~]
└─# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:b3:79:91 brd ff:ff:ff:ff:ff:ff
inet 192.168.56.66/24 brd 192.168.56.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:feb3:7991/64 scope link noprefixroute
valid_lft forever preferred_lft forever
## 为什么是临时更改,可以通过停用之后再启用,ip还是之前的
┌──(root㉿kali)-[~]
└─# ifconfig eth0 down
┌──(root㉿kali)-[~]
└─# ifconfig eth0 up
┌──(root㉿kali)-[~]
└─# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:b3:79:91 brd ff:ff:ff:ff:ff:ff
inet 192.168.56.128/24 brd 192.168.56.255 scope global dynamic noprefixroute eth0
valid_lft 1797sec preferred_lft 1797sec
inet6 fe80::20c:29ff:feb3:7991/64 scope link noprefixroute
valid_lft forever preferred_lft forever
## 指定IP地址的时候同时指定子网掩码
┌──(root㉿kali)-[~]
└─# ifconfig eth0 10.1.1.1
┌──(root㉿kali)-[~]
└─# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.1.1.1 netmask 255.0.0.0 broadcast 10.255.255.255
inet6 fe80::20c:29ff:feb3:7991 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:b3:79:91 txqueuelen 1000 (Ethernet)
RX packets 363 bytes 38409 (37.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 89 bytes 20795 (20.3 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 4 bytes 240 (240.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4 bytes 240 (240.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
##
┌──(root㉿kali)-[~]
└─# ifconfig eth0 10.1.1.1 netmask 255.255.255.0
┌──(root㉿kali)-[~]
└─# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.1.1.1 netmask 255.255.255.0 broadcast 10.1.1.255
inet6 fe80::20c:29ff:feb3:7991 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:b3:79:91 txqueuelen 1000 (Ethernet)
RX packets 388 bytes 39909 (38.9 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 90 bytes 20857 (20.3 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 4 bytes 240 (240.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4 bytes 240 (240.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
在Kali中如何使用无线网卡连接WiFi
- 先在主机中使用无线网卡连接WiFi
- 在对应官网下载网卡驱动
- 在虚拟机中添加USB控制器
- 查看网络接口 ifconfig -a
- 如果无线网络处于不活动状态,使用ifconfig wlan0 up 启用无线网卡
- 使用iwconfig 收集无线网卡的信息


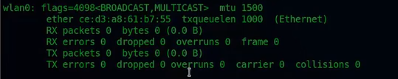
使用iwconfig 收集无线网卡的信息数据解析
## IEEE 802.11 : 无线网络的标准 包含 802.11 a/b/g/
## 802.11n(支持2.4GHz和5GHz 理论带宽最高600Mpbs)
##
wlan0 IEEE 802.11 EssID:off/any
Mode:Managed Access Point: Not-Associated Tx-Power=20 dBm
Retry short limit:7 RTs thr:off Fragment thr:off
Encryption key:off
Power Management :off
## 连接上WiFi的数据解析
## ESSID 无线WiFi标识
## Access Point: AP,无线接入点,值为MAC地址
## Mode:Managed :当前无线网卡的模式Managed :客户端模式,连接WiFi通常使用的模式;
## Mode:Monitor(监视)或(promiscuous 混插模式):在破解无线密码时,我们需要使用到混杂模式(promiscuous mode)或Moditor模式;在这种模式下,网卡处于嗅探状态(被成为Passive状态,被动状态)
## Bit Rate=150 Mb/s :传输速率
## Tx-Power:功率
wlan0 IEEE 802.11 ESSID:"Xiaomi 20A8"
Mode:Managed Frequency:2.437 GHz Access Point: 88:C3:97:C2:F1:4E
Bit Rate=150 Mb/s Tx-Power=20 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Encryption key:off
Power Management :off
Link Quality=70/70 Siqnal level=-36 dBm
Rx invalid nwid;0 Rx invalid crypt:0 Rx invalid frag:0
Tx excessive retries:0 Invalid misc:16Missed beacon:0
- 连接指定的WiFi:推荐使用图形化界面连接WiFi
PS:前提:NetworkManager 服务要开启(服务名称区分大小写) systemtcl status NetworkManager
在kali中查看你的无线网卡是否可以用于无线攻击
## iw list 查看无线网卡支持的模式
Supported interface modes :
*IBSS
*managed
*AP (有)
*AP/VLANt
*monitor (有)
*mesh point
*P2P-client
*P2P-GO
*outside context of a BSS
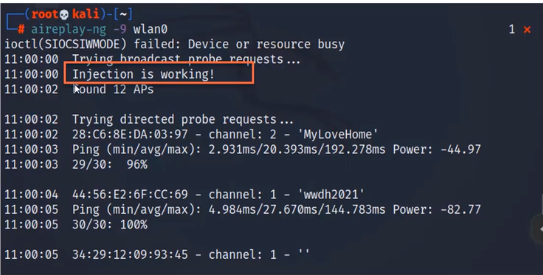
## 查看是否支持数据包的注入功能
aireplay-ng -9 wlan0
更改MAC地址
MAC地址的欺骗
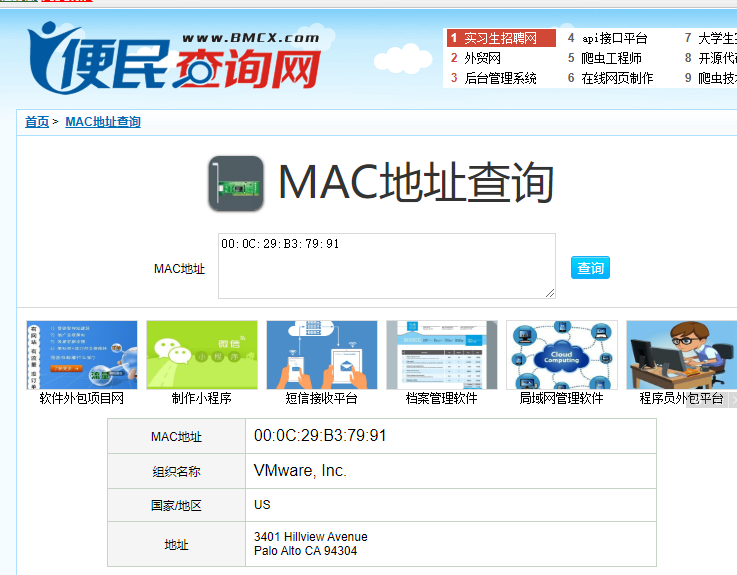
MAC地址是全球唯一的,48位,16进制表示;前24位代表厂商地址
防范:通常被用作一种安全措施,以防止黑客进入网络或追踪他们
攻击: 更改MAC地址来伪装成一个不同的MAC地址使得上述安全措施无效

#PS 地址查询 MAC地址
## ncpa.cpl --网络连接
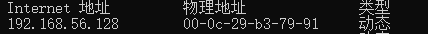
## arp协议 --把IP地址解析成MAC地址 arp -a 查看arp缓存
## arp -d 192.168.56.128 删除arp指定缓存
C:\Users\Administrator>arp -d 192.168.56.128
## kali中打开嗅探工具
## 更改MAC 地址
## 方法1: ifconfig eth0 hw ether 00:0c:29:76:ad:99
┌──(root㉿kali)-[~]
└─# ifconfig eth0 down
┌──(root㉿kali)-[~]
└─# ifconfig eth0 hw ether 00:0c:29:76:ad:99
┌──(root㉿kali)-[~]
└─# ifconfig eth0 up
┌──(root㉿kali)-[~]
└─# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.56.129 netmask 255.255.255.0 broadcast 192.168.56.255
inet6 fe80::20c:29ff:fe76:ad99 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:76:ad:99 txqueuelen 1000 (Ethernet)
RX packets 1541 bytes 115390 (112.6 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 185 bytes 30203 (29.4 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
┌──(root㉿kali)-[~]
└─# macchanger -s eth0
Current MAC: 00:0c:29:76:ad:99 (VMware, Inc.) ## 当前MAC地址
Permanent MAC: 00:0c:29:b3:79:91 (VMware, Inc.) ## 永久MAC地址
嗅探
打开kali 嗅探工具
选择监听
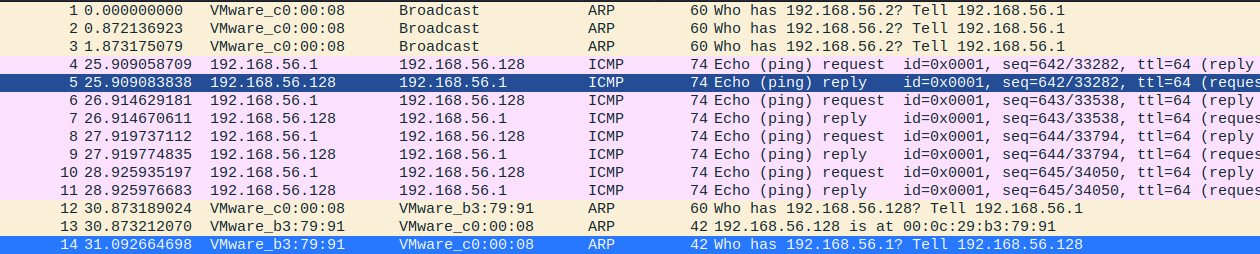
查看捕获数据
方法2:macchager 更改mac地址
┌──(root㉿kali)-[~]
└─# macchanger -h
GNU MAC Changer
Usage: macchanger [options] device
-h, --help Print this help
-V, --version Print version and exit
-s, --show Print the MAC address and exit
-e, --ending Don't change the vendor bytes
-a, --another Set random vendor MAC of the same kind
-A Set random vendor MAC of any kind
-p, --permanent Reset to original, permanent hardware MAC
-r, --random Set fully random MAC
-l, --list[=keyword] Print known vendors
-b, --bia Pretend to be a burned-in-address
-m, --mac=XX:XX:XX:XX:XX:XX
--mac XX:XX:XX:XX:XX:XX Set the MAC XX:XX:XX:XX:XX:XX
## macchanger eth0 -m 00:0c:29:76:ad:97
┌──(root㉿kali)-[~]
└─# macchanger eth0 -m 00:0c:29:76:ad:97
Current MAC: 00:0c:29:76:ad:99 (VMware, Inc.)
Permanent MAC: 00:0c:29:b3:79:91 (VMware, Inc.)
New MAC: 00:0c:29:76:ad:97 (VMware, Inc.)
通过DHCP服务器获取IP地址
DHCP协议 - 动态主机配置协议
Server:UDP/67 Linux下的DHCP服务(daemon,在后台进行)进程 dhcpd
Client:UDP/68
DHCP 服务器为子网上的所有机器分配 IP 地址,并在随时维护将 IP地址分配给哪台机器的日志文件。这使得它成为取证分析人员在攻击后追踪黑客的绝佳资源。出于这个原因,了解 DHCP 服务器的工作原理对一名黑客很有用。
## Linux下DHCP客户端调试工具 dhclient
┌──(root㉿kali)-[~]
└─# dhclient -h
Usage: dhclient [-4|-6] [-SNTPRI1dvrxi] [-nw] [-p <port>] [-D LL|LLT]
[--dad-wait-time <seconds>] [--prefix-len-hint <length>]
[--decline-wait-time <seconds>]
[--address-prefix-len <length>]
[-s server-addr] [-cf config-file]
[-df duid-file] [-lf lease-file]
[-pf pid-file] [--no-pid] [-e VAR=val]
[-sf script-file] [interface]*
dhclient {--version|--help|-h}
┌──(root㉿kali)-[~] ## dhclient -r 释放IP
└─# dhclient eth0 -r
Killed old client process
┌──(root㉿kali)-[~]
└─# dhclient eth0
┌──(root㉿kali)-[~]
└─# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.56.131 netmask 255.255.255.0 broadcast 192.168.56.255
inet6 fe80::20c:29ff:fe76:ad97 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:76:ad:97 txqueuelen 1000 (Ethernet)
RX packets 3121 bytes 216303 (211.2 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 279 bytes 45281 (44.2 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
配合嗅探工具进行分析
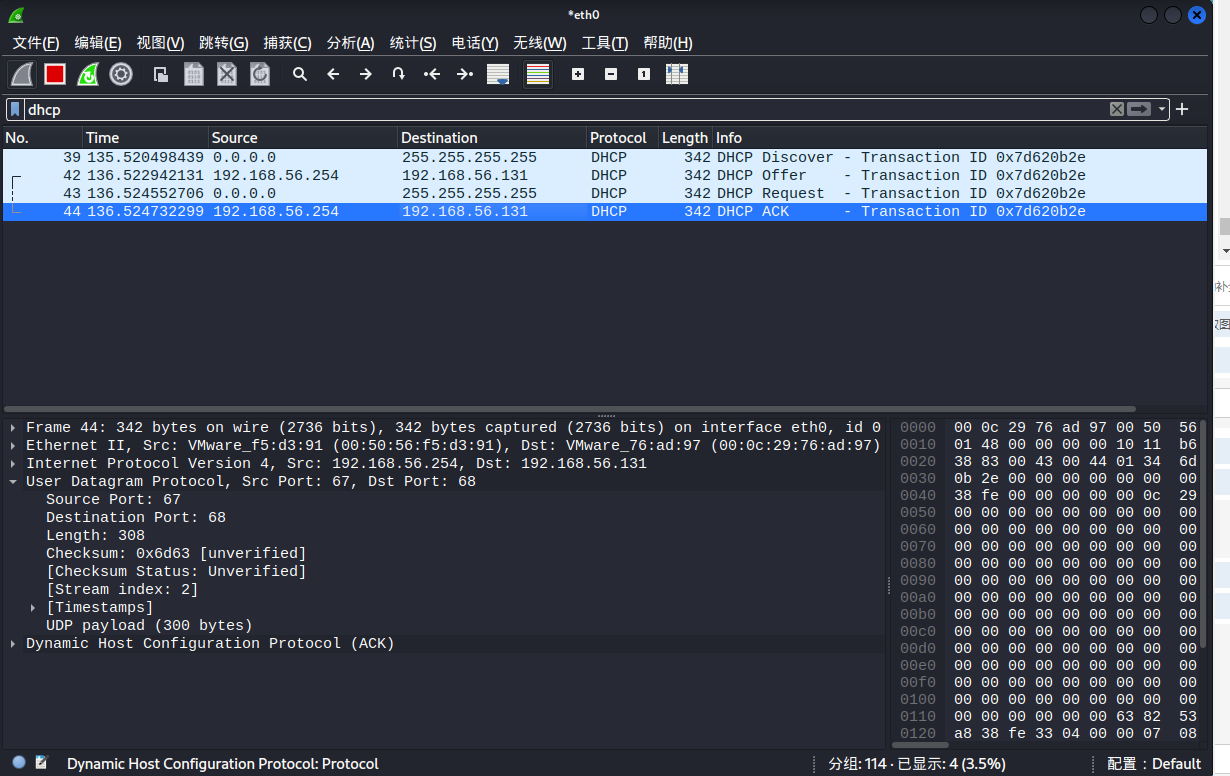
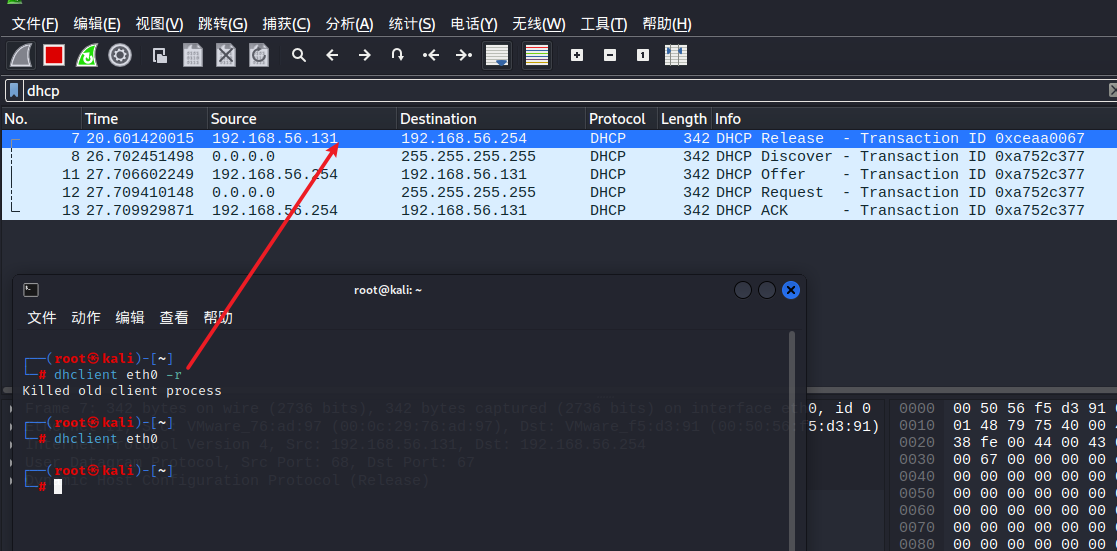
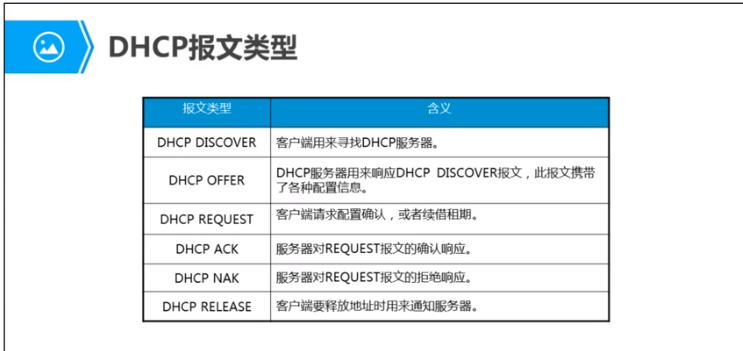
DCHP报文类型