前言
移动安全框架(MobSF)是一个自动化的一体化移动应用程序(Android/iOS/Windows)测试、恶意软件分析和安全评估框架,能够执行静态和动态分析。MobSF支持移动应用程序二进制文件(APK、XAPK、IPA和APPX)以及压缩源代码,并提供REST API,可与您的CI/CD或DevSecOps管道无缝集成。动态分析器可帮助您执行运行时安全评估和交互式仪器测试。
通过分析源码中对manifest的检测规则,来学习其可能存在的安全风险。
正文
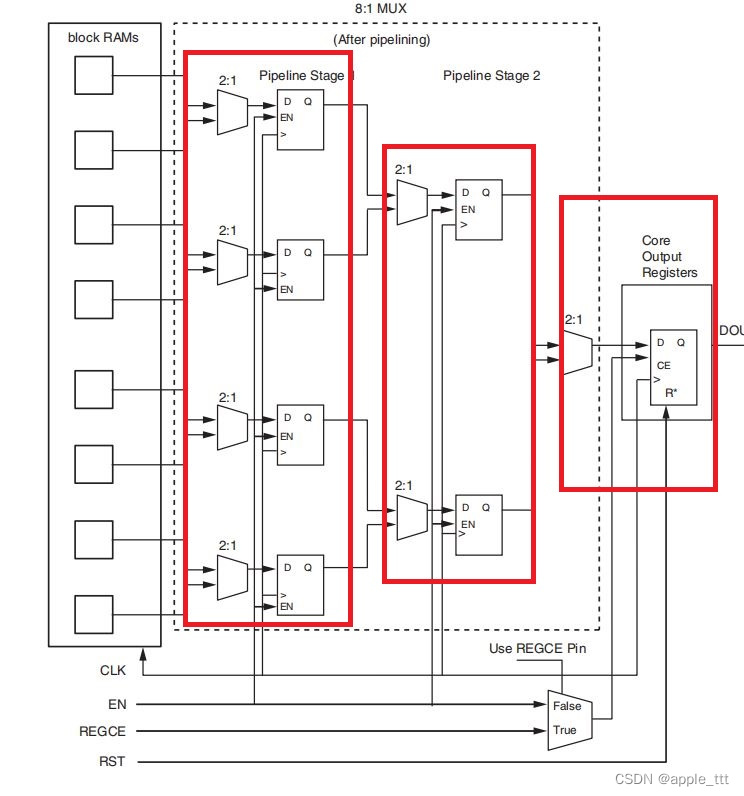
源码位置views/android/manifest_analysis.py的manifest_analysis函数
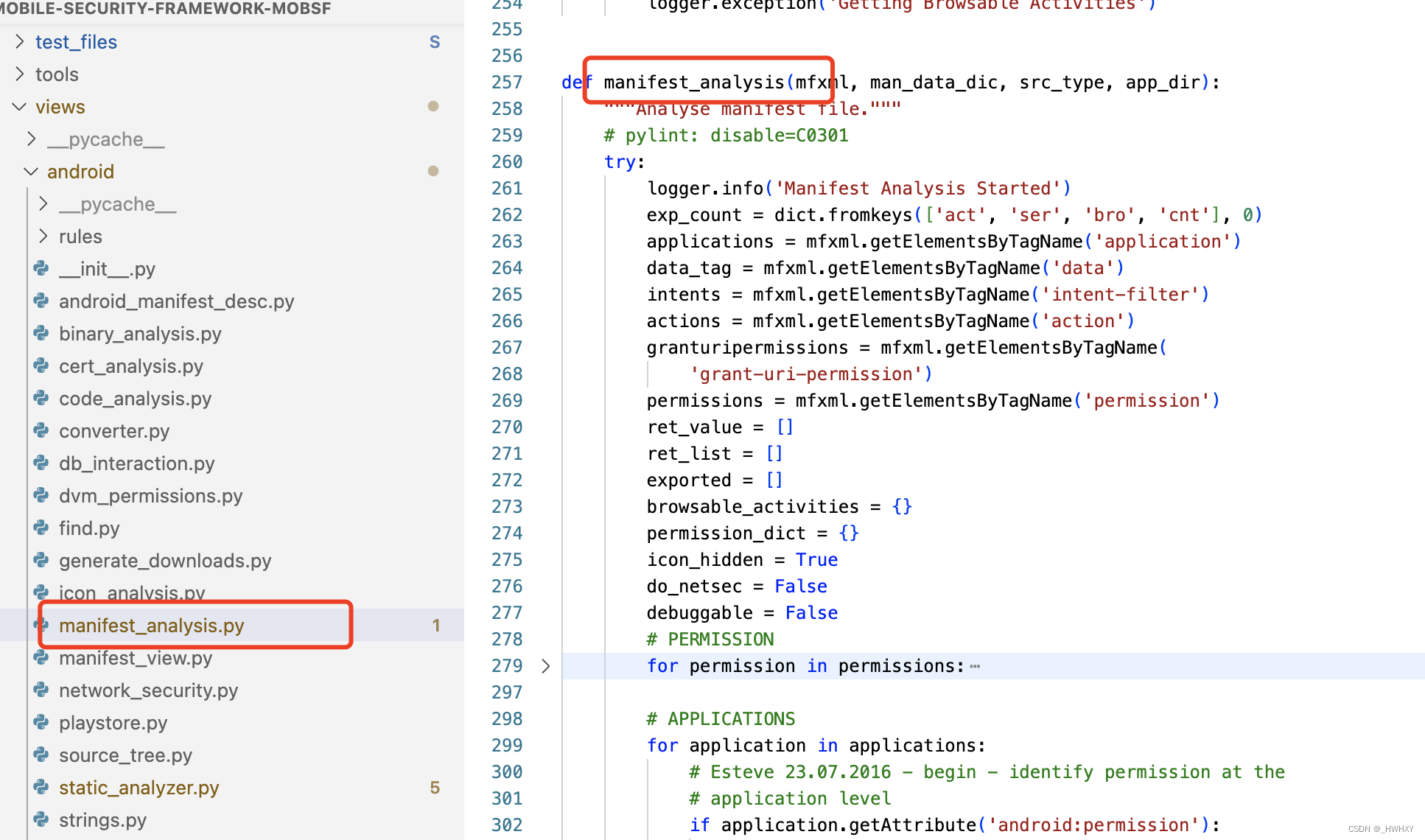
high*6
| 规则名 | 条件 | 级别 | 描述 |
| a_clear_text | android:usesCleartextTraffic=true | high | The app intends to use cleartext network traffic, such as cleartext HTTP, FTP stacks, DownloadManager, and MediaPlayer. The default value for apps that target API level 27 or lower is "true". Apps that target API level 28 or higher default to "false". The key reason for avoiding cleartext traffic is the lack of confidentiality, authenticity, and protections against tampering; a network attacker can eavesdrop on transmitted data and also modify it without being detected. |
| a_debuggable | android:debuggable=true | high | Debugging was enabled on the app which makes it easier for reverse engineers to hook a debugger to it. This allows dumping a stack trace and accessing debugging helper classes. |
| a_testonly | android:testOnly=true | high | It may expose functionality or data outside of itself that would cause a security hole. |
| a_launchmode | android:launchMode = singleInstance or singleTask | high | An Activity should not be having the launch mode attribute set to "singleTask/singleInstance" as it becomes root Activity and it is possible for other applications to read the contents of the calling Intent. So it is required to use the "standard" launch mode attribute when sensitive information is included in an Intent. |
| a_not_protected | android:exported=true | high | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. |
| a_improper_provider | android:pathPrefix == / | high | A content provider permission was set to allows access from any other app on the device. Content providers may contain sensitive information about an app and therefore should not be shared. |
warning*28
| 规则名 | 条件 | 级别 | 描述 |
| a_allowbackup | Application Data can be Backed up [android:allowBackup=true] | warning | This flag allows anyone to backup your application data via adb. It allows users who have enabled USB debugging to copy application data off of the device. |
| a_allowbackup_miss | Application Data can be Backed up [android:allowBackup] flag is missing. | warning | The flag [android:allowBackup] should be set to false. By default it is set to true and allows anyone to backup your application data via adb. It allows users who have enabled USB debugging to copy application data off of the device. |
| a_taskaffinity | TaskAffinity is set for Activity | warning | If taskAffinity is set, then other application could read the Intents sent to Activities belonging to another task. Always use the default setting keeping the affinity as the package name in order to prevent sensitive information inside sent or received Intents from being read by another application. |
| a_prot_normal | is Protected by a permission, but the protection level of the permission should be checked.[android:exported=true] | warning | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. It is protected by a permission. However, the protection level of the permission is set to normal. This means that a malicious application can request and obtain the permission and interact with the component. If it was set to signature, only applications signed with the same certificate could obtain the permission. |
| a_prot_danger | is Protected by a permission, but the protection level of the permission should be checked.[android:exported=true] | warning | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. It is protected by a permission. However, the protection level of the permission is set to dangerous. This means that a malicious application can request and obtain the permission and interact with the component. If it was set to signature, only applications signed with the same certificate could obtain the permission. |
| a_prot_unknown | is Protected by a permission, but the protection level of the permission should be checked.[android:exported=true] | warning | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. It is protected by a permission which is not defined in the analysed application. As a result, the protection level of the permission should be checked where it is defined. If it is set to normal or dangerous, a malicious application can request and obtain the permission and interact with the component. If it is set to signature, only applications signed with the same certificate can obtain the permission. |
| a_prot_normal_appl | is Protected by a permission at the application level, but the protection level of the permission should be checked.[android:exported=true] | warning | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. It is protected by a permission at the application level. However, the protection level of the permission is set to normal. This means that a malicious application can request and obtain the permission and interact with the component. If it was set to signature, only applications signed with the same certificate could obtain the permission. |
| a_prot_danger_appl | is Protected by a permission at the application level, but the protection level of the permission should be checked.[android:exported=true] | warning | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. It is protected by a permission at the application level. However, the protection level of the permission is set to dangerous. This means that a malicious application can request and obtain the permission and interact with the component. If it was set to signature, only applications signed with the same certificate could obtain the permission. |
| a_prot_unknown_appl | is Protected by a permission at the application, but the protection level of the permission should be checked.[android:exported=true] | warning | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. It is protected by a permission at the application level which is not defined in the analysed application. As a result, the protection level of the permission should be checked where it is defined. If it is set to normal or dangerous, a malicious application can request and obtain the permission and interact with the component. If it is set to signature, only applications signed with the same certificate can obtain the permission. |
| a_not_protected_filter | is not Protected.An intent-filter exists. | warning | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. The presence of intent-filter indicates that the %s is explicitly exported. |
| c_not_protected | is not Protected.[[Content Provider, targetSdkVersion < 17] | warning | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. It is a Content Provider that targets an API level under 17, which makes it exported by default, regardless of the API level of the system that the application runs on. |
| c_not_protected2 | would not be Protected if the application ran on a device where the the API level was less than 17.[Content Provider, targetSdkVersion >= 17] | warning | The Content Provider(%s %s) would be exported if the application ran on a device where the the API level was less than 17. In that situation, it would be shared with other apps on the device therefore leaving it accessible to any other application on the device. |
| c_prot_normal | is Protected by a permission, but the protection level of the permission should be checked.[Content Provider, targetSdkVersion < 17] | warning | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. It is protected by a permission. However, the protection level of the permission is set to normal. This means that a malicious application can request and obtain the permission and interact with the component. If it was set to signature, only applications signed with the same certificate could obtain the permission. |
| c_prot_danger | is Protected by a permission, but the protection level of the permission should be checked.[Content Provider, targetSdkVersion < 17] | warning | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. It is protected by a permission. However, the protection level of the permission is set to dangerous. This means that a malicious application can request and obtain the permission and interact with the component. If it was set to signature, only applications signed with the same certificate could obtain the permission. |
| c_prot_unknown | is Protected by a permission, but the protection level of the permission should be checked.[Content Provider, targetSdkVersion < 17] | warning | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. It is protected by a permission which is not defined in the analysed application. As a result, the protection level of the permission should be checked where it is defined. If it is set to normal or dangerous, a malicious application can request and obtain the permission and interact with the component. If it is set to signature, only applications signed with the same certificate can obtain the permission. |
| c_prot_normal_appl | is Protected by a permission at the application level, but the protection level of the permission should be checked.[Content Provider, targetSdkVersion < 17] | warning | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. It is protected by a permission at the application level. However, the protection level of the permission is set to normal. This means that a malicious application can request and obtain the permission and interact with the component. If it was set to signature, only applications signed with the same certificate could obtain the permission. |
| c_prot_danger_appl | is Protected by a permission at the application level, but the protection level of the permission should be checked.[Content Provider, targetSdkVersion < 17] | warning | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. It is protected by a permission at the application level. However, the protection level of the permission is set to dangerous. This means that a malicious application can request and obtain the permission and interact with the component. If it was set to signature, only applications signed with the same certificate could obtain the permission. |
| c_prot_unknown_appl | is Protected by a permission at application level, but the protection level of the permission should be checked.[Content Provider, targetSdkVersion < 17] | warning | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. It is protected by a permission at application level which is not defined in the analysed application. As a result, the protection level of the permission should be checked where it is defined. If it is set to normal or dangerous, a malicious application can request and obtain the permission and interact with the component. If it is set to signature, only applications signed with the same certificate can obtain the permission. |
| c_prot_normal_new | is Protected by a permission, but the protection level of the permission should be checked if the application runs on a device where the the API level is less than 17 [Content Provider, targetSdkVersion >= 17] | warning | The Content Provider (%s) would be exported if the application ran on a device where the the API level was less than 17. In that situation, it would still be protected by a permission. However, the protection level of the permission is set to normal. This means that a malicious application could request and obtain the permission and interact with the component. If it was set to signature, only applications signed with the same certificate could obtain the permission. |
| c_prot_danger_new | is Protected by a permission, but the protection level of the permission should be checked if the application runs on a device where the the API level is less than 17.[Content Provider, targetSdkVersion >= 17] | warning | The Content Provider(%s) would be exported if the application ran on a device where the the API level was less than 17. In that situation, it would still be protected by a permission. However, the protection level of the permission is set to dangerous. This means that a malicious application could request and obtain the permission and interact with the component. If it was set to signature, only applications signed with the same certificate could obtain the permission. |
| c_prot_unknown_new | is Protected by a permission, but the protection level of the permission should be checked if the application runs on a device where the the API level is less than 17.[Content Provider, targetSdkVersion >= 17] | warning | The Content Provider(%s) would be exported if the application ran on a device where the the API level was less than 17. In that situation, it would still be protected by a permission which is not defined in the analysed application. As a result, the protection level of the permission should be checked where it is defined. If it is set to normal or dangerous, a malicious application can request and obtain the permission and interact with the component. If it is set to signature, only applications signed with the same certificate can obtain the permission. |
| c_prot_normal_new_appl | is Protected by a permission at the application level should be checked, but the protection level of the permission if the application runs on a device where the the API level is less than 17.[Content Provider, targetSdkVersion >= 17] | warning | The Content Provider (%s) would be exported if the application ran on a device where the the API level was less than 17. In that situation, it would still be protected by a permission. However, the protection level of the permission is set to normal. This means that a malicious application could request and obtain the permission and interact with the component. If it was set to signature, only applications signed with the same certificate could obtain the permission. |
| c_prot_danger_new_appl | is Protected by a permission at the application level, but the protection level of the permission should be checked if the application runs on a device where the the API level is less than 17.[Content Provider, targetSdkVersion >= 17] | warning | The Content Provider(%s) would be exported if the application ran on a device where the the API level was less than 17. In that situation, it would still be protected by a permission. However, the protection level of the permission is set to dangerous. This means that a malicious application could request and obtain the permission and interact with the component. If it was set to signature, only applications signed with the same certificate could obtain the permission. |
| c_prot_unknown_new_appl | is Protected by a permission at the application level, but the protection level of the permission should be checked if the application runs on a device where the the API level is less than 17.[Content Provider, targetSdkVersion >= 17] | warning | The Content Provider(%s) would be exported if the application ran on a device where the the API level was less than 17. In that situation, it would still be protected by a permission which is not defined in the analysed application. As a result, the protection level of the permission should be checked where it is defined. If it is set to normal or dangerous, a malicious application can request and obtain the permission and interact with the component. If it is set to signature, only applications signed with the same certificate can obtain the permission. |
| a_dailer_code | Dailer Code: Found <br>[android:scheme="android_secret_code"] | warning | A secret code was found in the manifest. These codes, when entered into the dialer grant access to hidden content that may contain sensitive information. |
| a_sms_receiver_port | Data SMS Receiver Set on Port: Found<br>[android:port] | warning | A binary SMS receiver is configured to listen on a port. Binary SMS messages sent to a device are processed by the application in whichever way the developer choses. The data in this SMS should be properly validated by the application. Furthermore, the application should assume that the SMS being received is from an untrusted source. |
| a_high_intent_priority | High Intent Priority [android:priority] | warning | By setting an intent priority higher than another intent, the app effectively overrides other requests. |
| a_high_action_priority | High Action Priority [android:priority] | warning | By setting an action priority higher than another action, the app effectively overrides other requests. |
info*14
| 规则名 | 条件 | 级别 | 描述 |
| a_boot_aware | App is direct-boot aware [android:directBootAware=true] | info | This app can run before the user unlocks the device. If you're using a custom subclass of Application, and if any component inside your application is direct - boot aware, then your entire custom application is considered to be direct - boot aware.During Direct Boot, your application can only access the data that is stored in device protected storage. |
| a_network_sec | App has a Network Security Configuration [android:networkSecurityConfig] | info | The Network Security Configuration feature lets apps customize their network security settings in a safe, declarative configuration file without modifying app code. These settings can be configured for specific domains and for a specific app. |
| a_prot_sign | is Protected by a permission.[android:exported=true] | info | A%s %s is found to be exported, but is protected by permission. |
| a_prot_sign_sys | is Protected by a permission, but the protection level of the permission should be checked.[android:exported=true] | info | A%s %s is found to be exported, but is protected by a permission. However, the protection level of the permission is set to signatureOrSystem. It is recommended that signature level is used instead. Signature level should suffice for most purposes, and does not depend on where the applications are installed on the device. |
| a_prot_sign_appl | Protected by a permission at the application level.[android:exported=true] | info | A%s %s is found to be exported, but is protected by a permission at the application level. |
| a_prot_sign_sys_appl | is Protected by a permission at the application level, but the protection level of the permission should be checked.[android:exported=true] | info | A%s %s is found to be exported, but is protected by a permission at the application level. However, the protection level of the permission is set to signatureOrSystem. It is recommended that signature level is used instead. Signature level should suffice for most purposes, and does not depend on where the applications are installed on the device. |
| c_prot_sign | is Protected by a permission.[Content Provider, targetSdkVersion < 17] | info | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. It is protected by permission. |
| c_prot_sign_sys | is Protected by a permission, but the protection level of the permission should be checked.[Content Provider, targetSdkVersion < 17] | info | A%s %s is found to be exported, but is protected by a permission. However, the protection level of the permission is set to signatureOrSystem. It is recommended that signature level is used instead. Signature level should suffice for most purposes, and does not depend on where the applications are installed on the device. |
| c_prot_sign_appl | is Protected by a permission at the application level.[Content Provider, targetSdkVersion < 17] | info | A%s %s is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device. It is protected by permission at the application level. |
| c_prot_sign_sys_appl | is Protected by a permission at the application level, but the protection level of the permission should be checked.[Content Provider, targetSdkVersion < 17] | info | A%s %s is found to be exported, but is protected by a permission at the application level. However, the protection level of the permission is set to signatureOrSystem. It is recommended that signature level is used instead. Signature level should suffice for most purposes, and does not depend on where the applications are installed on the device. |
| c_prot_sign_new | is Protected by a permission.[Content Provider, targetSdkVersion >= 17] | info | The Content Provider(%s) would be exported if the application ran on a device where the the API level was less than 17. Nevertheless, it is protected by a permission. |
| c_prot_sign_sys_new | is Protected by a permission, but the protection level of the permission should be checked.[Content Provider, targetSdkVersion >= 17] | info | The Content Provider(%s) would be exported if the application ran on a device where the API level was less than 17. In that situation, it would still be protected by a permission. However, the protection level of the permission is set to signatureOrSystem. It is recommended that signature level is used instead. Signature level should suffice for most purposes, and does not depend on where the applications are installed on the device. |
| c_prot_sign_new_appl | is Protected by a permission at the application level.[Content Provider, targetSdkVersion >= 17] | info | The Content Provider(%s) would be exported if the application ran on a device where the the API level was less than 17. Nevertheless, it is protected by a permission. |
| c_prot_sign_sys_new_appl | is Protected by a permission at the application level, but the protection level of the permission should be checked.[Content Provider, targetSdkVersion >= 17] | info | The Content Provider(%s) would be exported if the application ran on a device where the API level was less than 17. In that situation, it would still be protected by a permission. However, the protection level of the permission is set to signatureOrSystem. It is recommended that signature level is used instead. Signature level should suffice for most purposes, and does not depend on where the applications are installed on the device. |
后话
上述的48个manifest的风险项应该是比较全的了,可以当做学习资料和风险checklist进行查询。