最近花了很多精力在做chromium的GmSSL适配,协议和算法都已经完成,这篇文章是关于将SM2根证书预置到chromium中
我的开发测试环境是macos12.4,从chromium的代码和文档中得知证书获取和校验都是通过操作系统以及native api接口完成,如果需要国密证书验证和校验成功,需要对chromium做适配和开发,分为2步骤走:
1、chromium内置根证书
2、chromium调整验证流程
一、前提
1、在开始之前,您需要对开源项目chromium以及密码算法、安全通讯协议有一定的了解
2、你已经完成BoringSSL的密码算法、安全通讯协议的适配
二、国密根证书内置
1、下载根证书
这里我使用的是沃通和中国金融根证书
沃通
沃通SM2中级根证书-沃通WoTrus SSL证书!沃通CA SM2顶级根证书已经签发了如下中级根证书,用于颁发各种认证级别的SSL证书、客户端证书和时间戳证书。https://www.wotrus.com/root/SM2_intermediateca.htm
下载国密SM2根证书即可
中国金融
CPS_数字证书服务协议_证书体验平台_证书下载平台_证书链下载_申请表下载_全球服务器证书_相关下载_中国金融认证中心中国金融认证中心(CFCA)为客户提供专业的CPS、证书体验、证书下载、证书链下载、申请表下载、全球服务器证书、反欺诈全球服务器证书、证书服务协议、证书安全提示等方面综合、全面、立体的资料下载服务。https://www.cfca.com.cn/zhengshuzizhu/
在下载专区中下载生成证书链SM2

2、将证书转成pem格式
openssl x509 -in WoTrus-SM2.crt -out WoTrus-SM2.pem
openssl x509 -in CFCA_CS_SM2_CA.cer -out CFCA_CS_SM2_CA.pem3、获取指纹签名的sha256值
openssl x509 -fingerprint -sha256 -in WoTrus-SM2.pem
sha256 Fingerprint=B2:CF:D0:68:B4:D7:FC:A1:21:07:AF:41:65:CC:DA:61:34:38:DD:BD:90:16:9F:5F:4B:11:1C:AF:A2:21:D4:35去掉多余的信息得到值:B2CFD068B4D7FCA12107AF4165CCDA613438DDBD90169F5F4B111CAFA221D435
将WoTrus-SM2.pem改名为B2CFD068B4D7FCA12107AF4165CCDA613438DDBD90169F5F4B111CAFA221D435.pem
openssl x509 -fingerprint -sha256 -in CFCA_CS_SM2_CA.pem
sha256 Fingerprint=5F:C0:9A:7D:B2:B9:1E:87:6C:BE:A8:70:60:A9:FE:DF:02:91:69:81:50:97:78:53:BC:4B:5A:A6:54:98:9F:BD去掉多余的信息得到值:5FC09A7DB2B91E876CBEA87060A9FEDF0291698150977853BC4B5AA654989FBD
将CFCA_CS_SM2_CA.pem改名为B2CFD068B4D7FCA12107AF4165CCDA613438DDBD90169F5F4B111CAFA221D435.pem
三、chromium代码调整
主要调整的代码部分是net网络模块, 主要加上 chrome_root_store_supported支持
1、net/features.gni
chrome_root_store_supported默认只支持windows,调整下支持macos, 将
chrome_root_store_supported = is_win改为
chrome_root_store_supported = is_win || is_mac2、将pem文件放入指定位置
将B2CFD068B4D7FCA12107AF4165CCDA613438DDBD90169F5F4B111CAFA221D435.pem、B2CFD068B4D7FCA12107AF4165CCDA613438DDBD90169F5F4B111CAFA221D435.pem放到net/data/ssl/chrome_root_store/store/certs下
3、修改net/data/ssl/chrome_root_store/store/root_store.textproto文件
路径就是刚才放置的路径
# Network WoTrus-SM2
trust_anchors {
filename: "B2CFD068B4D7FCA12107AF4165CCDA613438DDBD90169F5F4B111CAFA221D435.pem"
}
# Network CFCA_CS_SM2_CA
trust_anchors {
filename: "5FC09A7DB2B91E876CBEA87060A9FEDF0291698150977853BC4B5AA654989FBD.pem"
}4、修gn工程文件net/data/ssl/chrome_root_store/BUILD.gn文件
将pem文件添加到build.gn中,编译后会生成chrome-root-store-inc.cc中间文件
# Generate C++ include file for the Chrome root store.
compiled_action("gen_root_store_inc") {
tool = "//net/tools/root_store_tool:root_store_tool"
# It'd be really nice to list an input as "store/certs/*", but it doesn't seem
# to work. So we list them all out.
inputs = [
"store/root_store.textproto",
"store/certs/02ed0eb28c14da45165c566791700d6451d7fb56f0b2ab1d3b8eb070e56edff5.pem",
"store/certs/0376ab1d54c5f9803ce4b2e201a0ee7eef7b57b636e8a93c9b8d4860c96f5fa7.pem",
….
"store/certs/fd73dad31c644ff1b43bef0ccdda96710b9cd9875eca7e31707af3e96d522bbd.pem",
"store/certs/B2CFD068B4D7FCA12107AF4165CCDA613438DDBD90169F5F4B111CAFA221D435.pem",
"store/certs/5FC09A7DB2B91E876CBEA87060A9FEDF0291698150977853BC4B5AA654989FBD.pem",
]
outputs = [ "${target_gen_dir}/chrome-root-store-inc.cc" ]
args = [
"--root-store-dir=" + rebase_path("store", root_build_dir),
"--write-cpp=" + rebase_path("${target_gen_dir}/chrome-root-store-inc.cc",
root_build_dir),
]
}自此静态证书部分添加完毕
下面对代码修改,以支持证书链的校验
5、调整证书信任存储代码
1) net/cert/internal/system_trust_store.cc
默认MACOS只支持从操作系统中获取证书并校验,这里改成浏览器内部预置证书校验
找到MACOS支持部分
修改下面代码
std::unique_ptr<SystemTrustStore> CreateSslSystemTrustStoreChromeRoot() {
return std::make_unique<DummySystemTrustStore>();
}为
#if BUILDFLAG(CHROME_ROOT_STORE_SUPPORTED)
std::unique_ptr<SystemTrustStore> CreateSslSystemTrustStoreChromeRoot() {
return std::make_unique<SystemTrustStoreChrome>(
std::make_unique<TrustStoreChrome>(), std::make_unique<TrustStoreMac>(kSecPolicyAppleSSL, TrustStoreMac::TrustImplType::kDomainCache, 512));
}
#else
std::unique_ptr<SystemTrustStore> CreateSslSystemTrustStoreChromeRoot() {
return std::make_unique<DummySystemTrustStore>();
}
#endif2) net/cert/cert_verify_proc.cc
增加BUILTIN_CERT_VERIFIER_FEATURE_SUPPORTED支持
修改静态方法
scoped_refptr<CertVerifyProc> CertVerifyProc::CreateBuiltinVerifyProc(
scoped_refptr<CertNetFetcher> cert_net_fetcher) {
return CreateCertVerifyProcBuiltin(std::move(cert_net_fetcher),
CreateSslSystemTrustStore());
}为
#if BUILDFLAG(CHROME_ROOT_STORE_SUPPORTED)
// static
scoped_refptr<CertVerifyProc> CertVerifyProc::CreateBuiltinVerifyProc(
scoped_refptr<CertNetFetcher> cert_net_fetcher) {
return CreateCertVerifyProcBuiltin(std::move(cert_net_fetcher),
CreateSslSystemTrustStoreChromeRoot());
}
#else
// static
scoped_refptr<CertVerifyProc> CertVerifyProc::CreateBuiltinVerifyProc(
scoped_refptr<CertNetFetcher> cert_net_fetcher) {
return CreateCertVerifyProcBuiltin(std::move(cert_net_fetcher),
CreateSslSystemTrustStore());
}
#endif3) services/cert_verifier/cert_verifier_creation.cc
修改证书校验创建流程
scoped_refptr<net::CertVerifyProc> CreateOldDefaultWithoutCaching(
scoped_refptr<net::CertNetFetcher> cert_net_fetcher) {
scoped_refptr<net::CertVerifyProc> verify_proc;
#if defined(OS_FUCHSIA) || defined(OS_LINUX) || defined(OS_CHROMEOS)
verify_proc =
net::CertVerifyProc::CreateBuiltinVerifyProc(std::move(cert_net_fetcher));
#else
verify_proc =
net::CertVerifyProc::CreateSystemVerifyProc(std::move(cert_net_fetcher));
#endif
return verify_proc;
}为
scoped_refptr<net::CertVerifyProc> CreateOldDefaultWithoutCaching(
scoped_refptr<net::CertNetFetcher> cert_net_fetcher) {
scoped_refptr<net::CertVerifyProc> verify_proc;
#if defined(OS_FUCHSIA) || defined(OS_LINUX) || defined(OS_CHROMEOS)
verify_proc =
net::CertVerifyProc::CreateBuiltinVerifyProc(std::move(cert_net_fetcher));
#elif BUILDFLAG(BUILTIN_CERT_VERIFIER_FEATURE_SUPPORTED)
// Create by david.chin on 07/26/2023
if (base::FeatureList::IsEnabled(net::features::kCertVerifierBuiltinFeature)) {
verify_proc =
net::CertVerifyProc::CreateBuiltinVerifyProc(std::move(cert_net_fetcher));
} else {
verify_proc =
net::CertVerifyProc::CreateSystemVerifyProc(std::move(cert_net_fetcher));
}
#else
verify_proc =
net::CertVerifyProc::CreateSystemVerifyProc(std::move(cert_net_fetcher));
#endif
return verify_proc;
}6、编译chromium,等待数小时
效果图
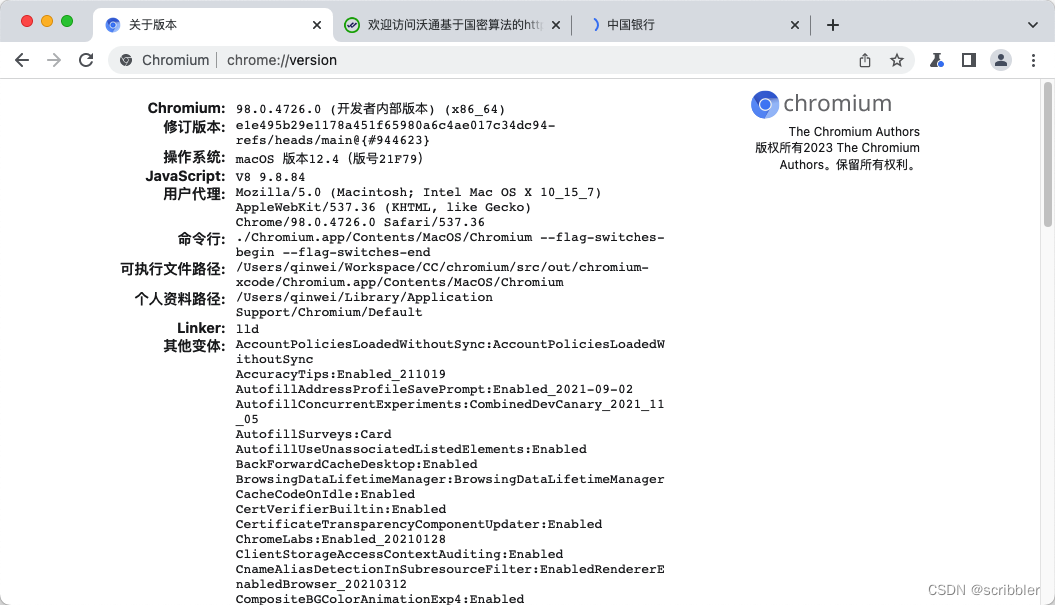
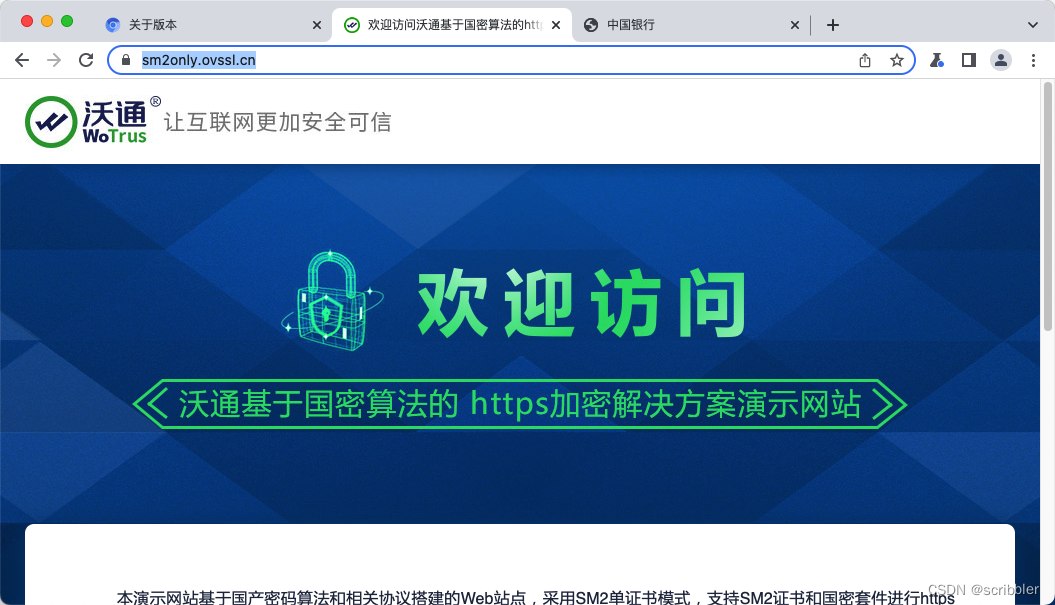
沃通测试网站
https://sm2only.ovssl.cn/
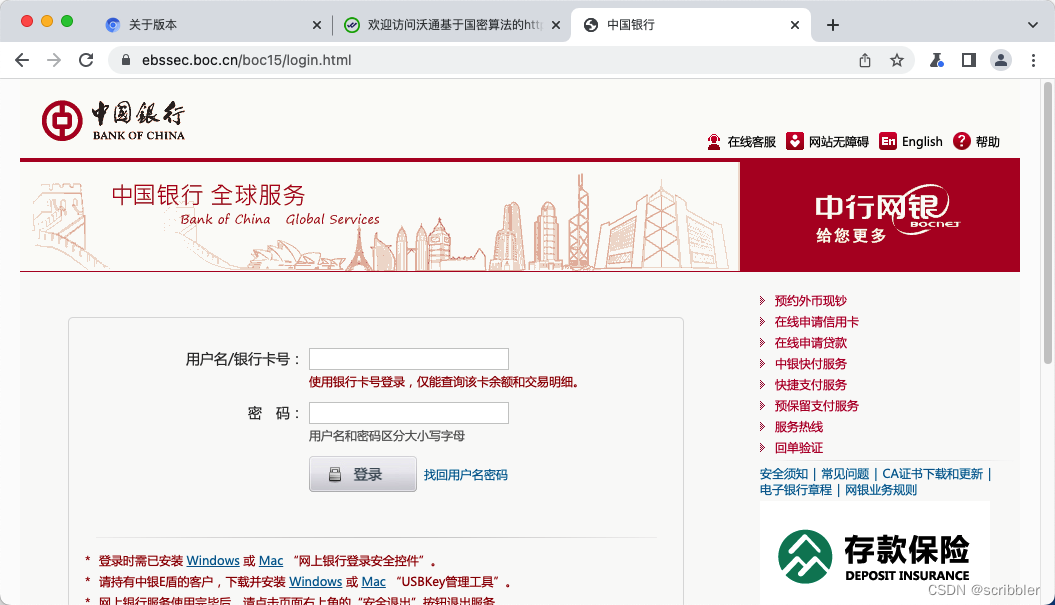
中国银行(只支持SM2)
https://ebssec.boc.cn/
四、写在最后
当然,国密的适配还有不少工作要做,这里只是做了macos的国密根证书内置,后续包括windows、linux、国产操作系统等适配会持续进行。