环境:centos7
工作流程:
- 当前的系统数据状态建立数据库
- 定期比较系统现状与数据库中的状态
- 属性改变有详细报告
- 分析报告发现入侵
1、安装相关软件包
[root@hello ~]# yum install epel-release -y
已加载插件:fastestmirror
Repository base is listed more than once in the configuration
base | 3.6 kB 00:00:00
epel | 4.7 kB 00:00:00
extras | 2.9 kB 00:00:00
[root@hello ~]# yum install tripwire -y
已加载插件:fastestmirror
Repository base is listed more than once in the configuration
Loading mirror speeds from cached hostfile
正在解决依赖关系
--> 正在检查事务
---> 软件包 tripwire.x86_64.0.2.4.3.7-1.el7 将被 安装
--> 解决依赖关系完成
生成密钥(123456)
[root@hello ~]# tripwire-setup-keyfiles
----------------------------------------------
The Tripwire site and local passphrases are used to sign a variety of
files, such as the configuration, policy, and database files.
Passphrases should be at least 8 characters in length and contain both
letters and numbers.
See the Tripwire manual for more information.
----------------------------------------------
Creating key files...
2、初始化数据库
[root@hello ~]# tripwire --init
Please enter your local passphrase:
Parsing policy file: /etc/tripwire/tw.pol
Generating the database...
*** Processing Unix File System ***
### Warning: File system error.
### Filename: /usr/sbin/fixrmtab
### 没有那个文件或目录
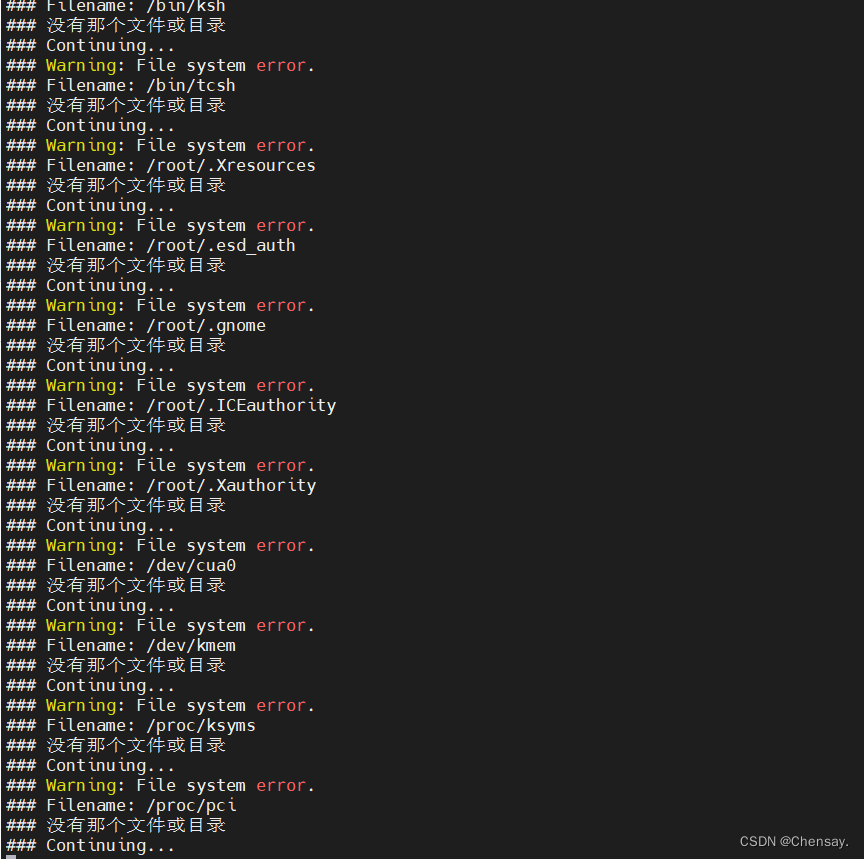
- 就地解决报错
[root@hello ~]# sh -c "tripwire --check | grep Filename > cat no-directory.txt
"
#将报错中不存在的目录和文件加到no-directory.txt中
### Warning: File system error.
### Filename: /usr/sbin/fixrmtab
### 没有那个文件或目录
[root@hello ~]# vim tripwire.sh
#写个脚本
for f in $(grep "Filename:" no-directory.txt | cut -f2 -d:); do
sed -i "s|\($f\) |#\\1|g" /etc/tripwire/twpol.txt
done
[root@hello ~]# twadmin -m P /etc/tripwire/twpol.txt
#重新签署配置
Please enter your site passphrase:
Wrote policy file: /etc/tripwire/tw.pol
[root@hello ~]# tripwire --init
#重新初始化
Please enter your local passphrase:
Parsing policy file: /etc/tripwire/tw.pol
Generating the database...
*** Processing Unix File System ***
3、测试:更改/etc/passwd文件(添加了以下k)
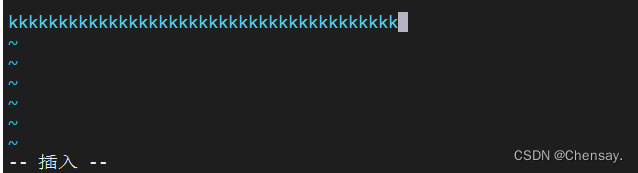
4、发现异常
[root@hello ~]# tripwire --check
Parsing policy file: /etc/tripwire/tw.pol
*** Processing Unix File System ***
Performing integrity check...
Wrote report file: /var/lib/tripwire/report/hello-20210518-114057.twr
Open Source Tripwire(R) 2.4.3.7 Integrity Check Report
Report generated by: root
Report created on: 2021年05月18日 星期二 11时40分57秒
Database last updated on: Never
===============================================================================
Report Summary:
===============================================================================
Host name: hello
Host IP address: 10.0.0.134
Host ID: None
Policy file used: /etc/tripwire/tw.pol
Configuration file used: /etc/tripwire/tw.cfg
Database file used: /var/lib/tripwire/hello.twd
Command line used: tripwire --check
===============================================================================
Rule Summary:
===============================================================================
-------------------------------------------------------------------------------
Section: Unix File System
-------------------------------------------------------------------------------
Rule Name Severity Level Added Removed Modified
--------- -------------- ----- ------- --------
User binaries 66 0 0 0
Tripwire Binaries 100 0 0 0
Libraries 66 0 0 0
Operating System Utilities 100 0 0 0
File System and Disk Administraton Programs
100 0 0 0
Kernel Administration Programs 100 0 0 0
Networking Programs 100 0 0 0
System Administration Programs 100 0 0 0
Hardware and Device Control Programs
100 0 0 0
System Information Programs 100 0 0 0
Application Information Programs
100 0 0 0
(/sbin/rtmon)
Critical Utility Sym-Links 100 0 0 0
Shell Binaries 100 0 0 0
Critical system boot files 100 0 0 0
Tripwire Data Files 100 0 0 0
System boot changes 100 0 0 0
OS executables and libraries 100 0 0 0
* Critical configuration files 100 0 0 1
Security Control 100 0 0 0
Login Scripts 100 0 0 0
* Root config files 100 0 0 2
Invariant Directories 66 0 0 0
Temporary directories 33 0 0 0
Critical devices 100 0 0 0
Total objects scanned: 17245
Total violations found: 3
===============================================================================
Object Summary:
===============================================================================
-------------------------------------------------------------------------------
# Section: Unix File System
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Rule Name: Critical configuration files (/etc/passwd)
Severity Level: 100
-------------------------------------------------------------------------------
Modified:
"/etc/passwd"
-------------------------------------------------------------------------------
Rule Name: Root config files (/root)
Severity Level: 100
-------------------------------------------------------------------------------
Modified:
"/root"
"/root/.viminfo"
===============================================================================
Error Report:
===============================================================================
No Errors
-------------------------------------------------------------------------------
*** End of report ***
Open Source Tripwire 2.4 Portions copyright 2000-2018 Tripwire, Inc. Tripwire is a registe red
trademark of Tripwire, Inc. This software comes with ABSOLUTELY NO WARRANTY;
for details use --version. This is free software which may be redistributed
or modified only under certain conditions; see COPYING for details.
All rights reserved.
Integrity check complete.
[root@hello ~]#