0x00 前言
CTF 加解密合集:CTF 加解密合集
0x01 题目
给了一个秘钥,三个加密后的文件
0x02 Write Up
先获取n和e
# 导入公钥
with open(r"C:\Users\wdd\Downloads\flag\fujian\public.key", "rb") as f:
key = RSA.import_key(f.read())
n = key.n
e = key.e
然后通过n进行在线分解
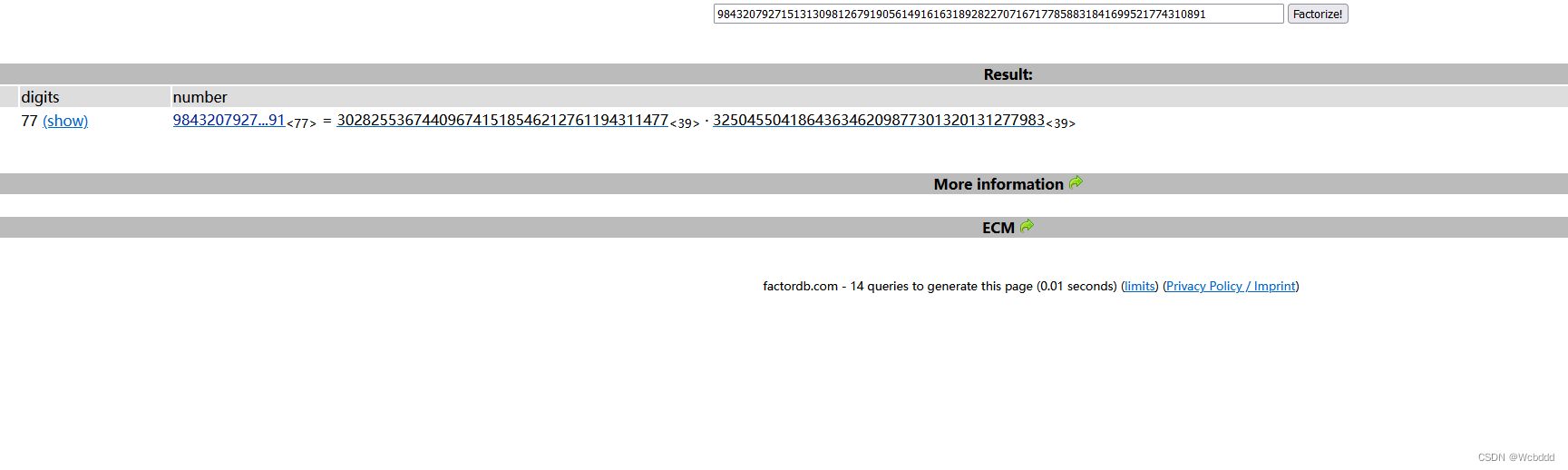
得到p和q
现在题目就变成了,已知p,q,e,c求m,脚本如下
from Crypto.PublicKey import RSA
import libnum
import gmpy2
# 导入公钥
with open(r"C:\Users\wdd\Downloads\flag\fujian\public.key", "rb") as f:
key = RSA.import_key(f.read())
n = key.n
e = key.e
print(n)
with open(r"C:\Users\wdd\Downloads\flag\fujian\encrypted.message1", "rb") as f:
c1 = libnum.s2n(f.read())
with open(r"C:\Users\wdd\Downloads\flag\fujian\encrypted.message2", "rb") as f:
c2 = libnum.s2n(f.read())
with open(r"C:\Users\wdd\Downloads\flag\fujian\encrypted.message3", "rb") as f:
c3 = libnum.s2n(f.read())
p = 302825536744096741518546212761194311477
q = 325045504186436346209877301320131277983
d = libnum.invmod(e, (p - 1) * (q - 1))
c = [c1, c2, c3]
flag = ''
for i in c:
m = pow(i, d, n)
m1 = str(libnum.n2s(int(m)))
flag += (m1.split("x00")[1])[:-3] # 以x00分段取后面那段,将 \n' 去掉
print(flag)
以上