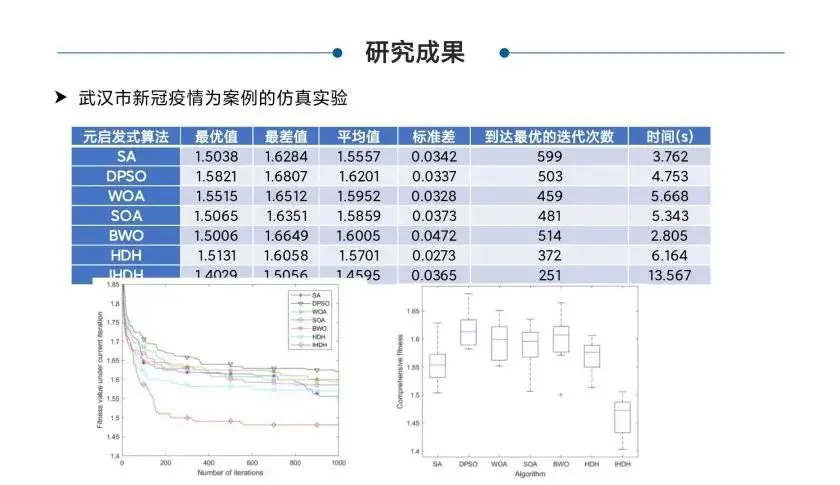
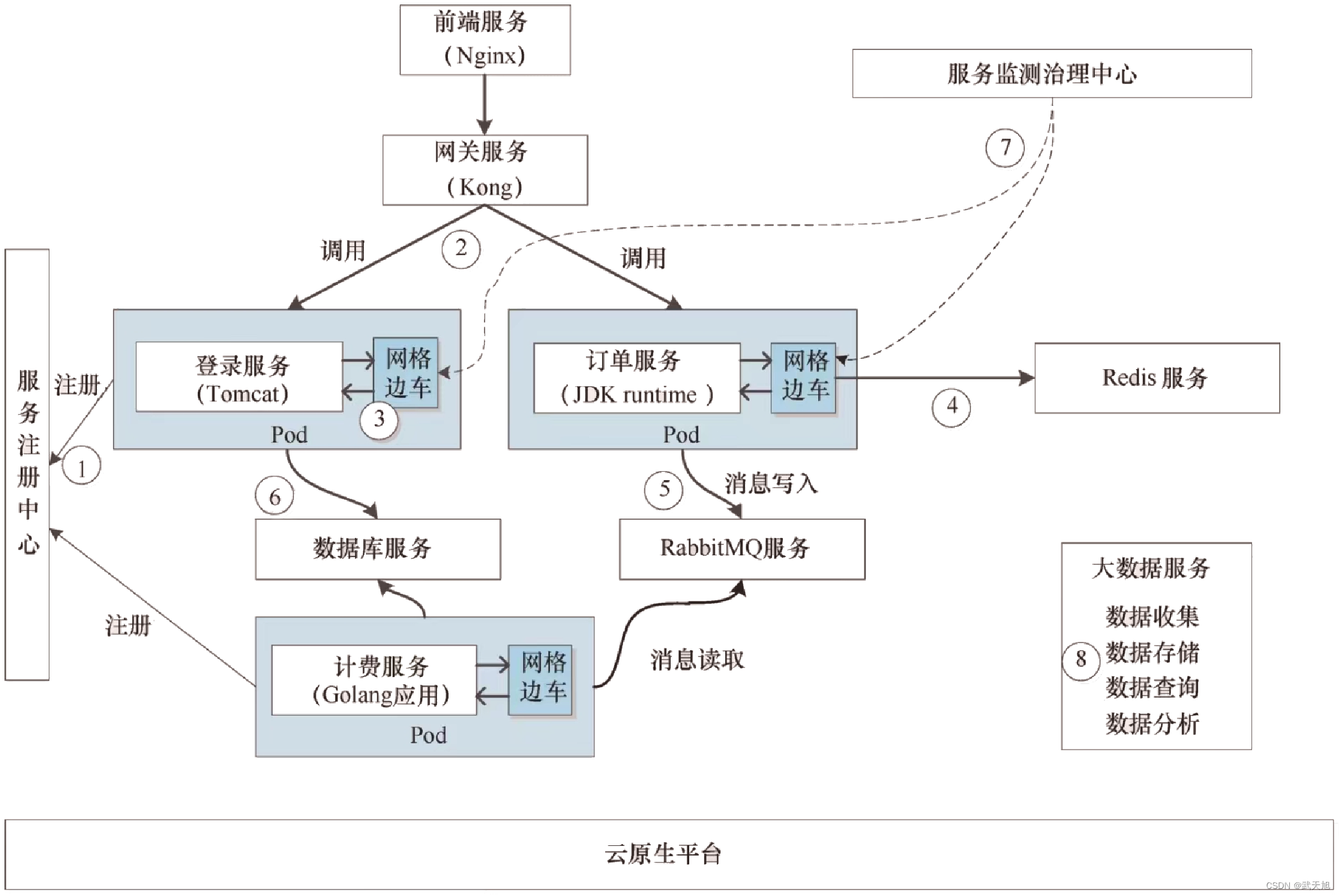
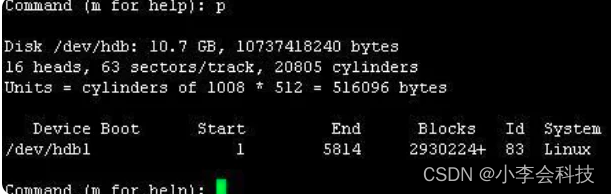
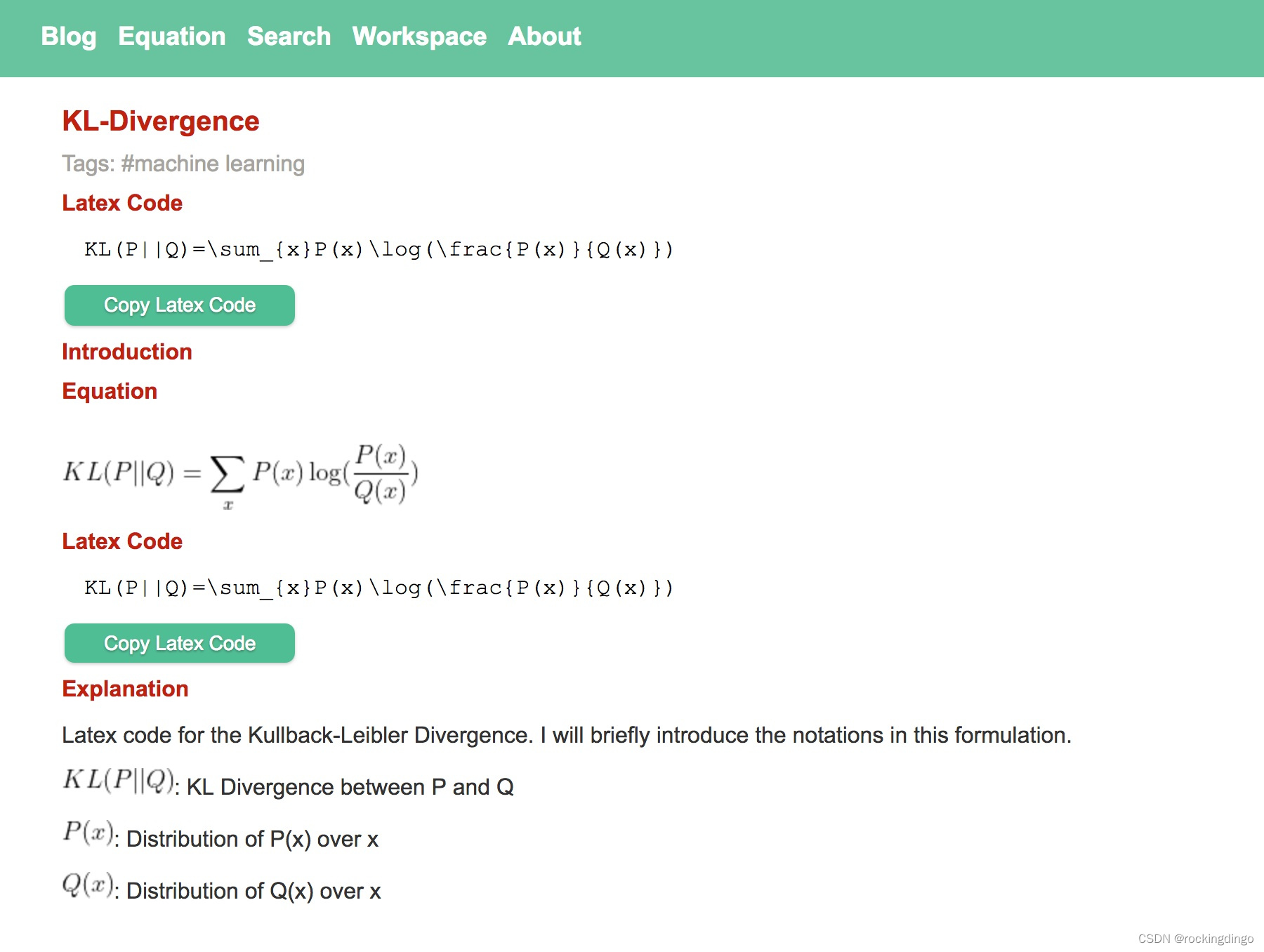
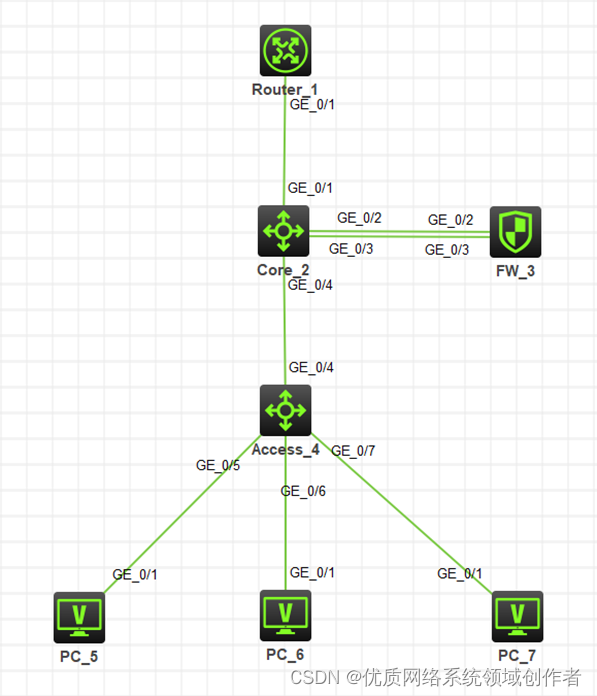
防火墙旁路部署在核心交换机上,内网有三个网段vlan 10:172.16.10.1/24、vlan 20:172.16.20.1/24、vlan30:172.16.30.1。要求内网网关在防火墙设备上,由防火墙作为DHCP服务器给终端下发地址,同时由防火墙来控制禁止vlan10访问vlan 20,禁止vlan20访问vlan30,其他不做限制。
配置思路:
1、 接入交换机根据业务需求,将不同的接口划入指定vlan
2、 接入交换机和核心交换机互联接口配置成trunk模式,放行三个业务vlan
3、 核心交换机与防火墙互联的链路1(G1/0/3)的接口配置成trunk模式,放行三个业务vlan,内网流量通过这跟线路进入防火墙
4、 核心交换机与防火墙互联的链路2(G1/0/2),交换机侧接口工作在access模式,划入vlan5。防火墙侧接口工作在三层模式,链路2三层互联,防火墙处理完的流量经过这跟链路回到核心交换机
5、 核心交换机与出口路由器配置互联地址,核心交换机写默认路由指向出口路由器,出口路由器针对内网网段写回程路由指向核心交换机,核心交换机写回程路由指向防火墙
6、 防火墙配置DHCP及安全策略
配置步骤
1、 配置接入交换机Access
sys
#创建业务vlan
[Access]vlan 10
[Access-vlan10]quit
[Access]vlan 20
[Access-vlan20]quit
[Access]vlan 30
[Access-vlan30]quit
[Access]
#根据业务需要将不同的终端接口划分到不同的vlan
[Access]inter GigabitEthernet 1/0/5
[Access-GigabitEthernet1/0/5]port access vlan 10
[Access-GigabitEthernet1/0/5]quit
[Access]
[Access]inter GigabitEthernet 1/0/6
[Access-GigabitEthernet1/0/6]port access vlan 20
[Access-GigabitEthernet1/0/6]quit
[Access]
[Access]inter GigabitEthernet 1/0/7
[Access-GigabitEthernet1/0/7]port access vlan 30
[Access-GigabitEthernet1/0/7]quit
[Access]
#将接入交换机上行口配置成trunk模式,允许vlan10、20、30通过,禁止vlan1通行
[Access]inter GigabitEthernet 1/0/4
[Access-GigabitEthernet1/0/4]port link-type trunk
[Access-GigabitEthernet1/0/4]port trunk permit vlan 10 20 30
[Access-GigabitEthernet1/0/4]undo port trunk permit vlan 1
[Access-GigabitEthernet1/0/4]qu
#保存配置
[Access] save force
2、 配置核心交换机Core
system-view
#创建业务vlan
[Core]vlan 10
[Core-vlan10]quit
[Core]vlan 20
[Core-vlan20]quit
[Core]vlan 30
[Core-vlan30]quit
[Core]vlan 5
[Core-vlan5]quit
[Core]vlan 6
[Core-vlan6]quit
[Core]
#配置连接接入交换机下行口为trunk模式,允许vlan10、20、30通过,禁止vlan1通行
[Core]inter GigabitEthernet 1/0/4
[Core-GigabitEthernet1/0/4]port link-type trunk
[Core-GigabitEthernet1/0/4]port trunk permit vlan 10 20 30
[Core-GigabitEthernet1/0/4]undo port trunk permit vlan 1
[Core-GigabitEthernet1/0/4]qu
[Core]
#配置连接防火墙的接口(链路1)为trunk模式,允许vlan10、20、30通过,禁止vlan1通行
[Core]inter GigabitEthernet 1/0/3
[Core-GigabitEthernet1/0/3]port link-type trunk
[Core-GigabitEthernet1/0/3]port trunk permit vlan 10 20 30
[Core-GigabitEthernet1/0/3]undo port trunk permit vlan 1
[Core-GigabitEthernet1/0/3]quit
[Core]
#配置连接防火墙的接口(链路2)属于vlan5
[Core]inter GigabitEthernet 1/0/2
[Core-GigabitEthernet1/0/2]port access vlan 5
[Core-GigabitEthernet1/0/2]quit
[Core]
#配置连接上行路由器的接口属于vlan6
[Core]inter g1/0/1
[Core-GigabitEthernet1/0/1]port access vlan 6
[Core-GigabitEthernet1/0/1]quit
[Core]
#配置交换机和防火墙的互联地址10.0.23.2/24
[Core]inter vlan 5
[Core-Vlan-interface5]ip address 10.0.23.2 24
[Core-Vlan-interface5]qu
[Core]
#配置交换机和路由器的互联地址10.0.12.2/24
[Core]inter vlan 6
[Core-Vlan-interface6]ip address 10.0.12.2 24
[Core-Vlan-interface6]quit
[Core]
#配置默认路由指向出口路由器
[Core]ip route-static 0.0.0.0 0 10.0.12.1
#配置内网网段回程路由指向防火墙
[Core]ip route-static 172.16.10.0 24 10.0.23.3
[Core]ip route-static 172.16.20.0 24 10.0.23.3
[Core]ip route-static 172.16.30.0 24 10.0.23.3
#保存配置
[Core] save force
3、 配置防火墙,默认登陆用户名和密码均为admin
Login: admin
Password: admin
sys
[H3C]sysname FW
#创建业务vlan
[FW]vlan 10
[FW-vlan10]quit
[FW]vlan 20
[FW-vlan20]quit
[FW]vlan 30
[FW-vlan30]quit
[FW]
#配置连接交换机的接口(链路1)为trunk模式,允许vlan10、20、30通过,禁止vlan1通行
[FW]inter GigabitEthernet 1/0/3
[FW-GigabitEthernet1/0/3]port link-mode bridge
[FW-GigabitEthernet1/0/3]port link-type trunk
[FW-GigabitEthernet1/0/3]port trunk permit vlan 10 20 30
[FW-GigabitEthernet1/0/3]undo port trunk permit vlan 1
[FW-GigabitEthernet1/0/3]quit
[FW]
#配置连接交换机的接口(链路2)互联地址10.0.23.3/24
[FW]inter GigabitEthernet 1/0/2
[FW-GigabitEthernet1/0/2]ip address 10.0.23.3 24
[FW-GigabitEthernet1/0/2]quit
[FW]
#创建业务vlan的网关接口
[FW]inter vlan 10
[FW-Vlan-interface10]ip address 172.16.10.1 24
[FW-Vlan-interface10]quit
[FW]
[FW]inter vlan 20
[FW-Vlan-interface20]ip address 172.16.20.1 24
[FW-Vlan-interface20]quit
[FW]
[FW]inter vlan 30
[FW-Vlan-interface30]ip address 172.16.30.1 24
[FW-Vlan-interface30]quit
[FW]
#创建业务vlan的dhcp地址池
[FW]dhcp server ip-pool vlan10
#配置地址池分配地址的网段
[FW-dhcp-pool-vlan10]network 172.16.10.0 mask 255.255.255.0
#配置地址池分配的网关地址
[FW-dhcp-pool-vlan10]gateway-list 172.16.10.1
#配置地址池分配的DNS地址
[FW-dhcp-pool-vlan10]dns-list 114.114.114.114 8.8.8.8
[FW-dhcp-pool-vlan10]quit
[FW]
[FW]dhcp server ip-pool vlan20
[FW-dhcp-pool-vlan20]network 172.16.20.0 mask 255.255.255.0
[FW-dhcp-pool-vlan20]gateway-list 172.16.20.1
[FW-dhcp-pool-vlan20]dns-list 114.114.114.114 8.8.8.8
[FW-dhcp-pool-vlan20]quit
[FW]
[FW]dhcp server ip-pool vlan30
[FW-dhcp-pool-vlan30]network 172.16.30.0 mask 255.255.255.0
[FW-dhcp-pool-vlan30]gateway-list 172.16.30.1
[FW-dhcp-pool-vlan30]dns-list 114.114.114.114 8.8.8.8
[FW-dhcp-pool-vlan30]quit
[FW]
#全局开启dhcp server功能
[FW]dhcp enable
[FW]
#配置默认路由指向核心交换机
[FW]ip route-static 0.0.0.0 0 10.0.23.2
[FW]
#将连接核心交换机的接口g1/0/3(内网流量进防火墙的接口)和网关接口加入trust安全域
[FW]security-zone name Trust
#二层口加安全域的时候,需要额外配置该接口允许通过的vlan
[FW-security-zone-Trust]import interface GigabitEthernet 1/0/3 vlan 10 20 30
[FW-security-zone-Trust]import interface Vlan-interface 10
[FW-security-zone-Trust]import interface Vlan-interface 20
[FW-security-zone-Trust]import interface Vlan-interface 30
[FW-security-zone-Trust]quit
[FW]
#配置将流量出防火墙的接口g1/0/2加入untrust安全域
[FW]security-zone name Untrust
[FW-security-zone-Untrust]import interface GigabitEthernet 1/0/2
[FW-security-zone-Untrust]quit
[FW]
#配置安全策略,安全策略按照dis cu conf security-policy-ip看到的顺序从上往下匹配
[FW]security-policy ip
#配置rule 1名称为toInternet,允许内网所有网段可以通过防火墙访问到路由器及上层网络。此时流量从g1/0/3(trust)进入设备,从g1/0/2(trust)出设备,所以需要放行trust到untrust源地址为172.16.10.0/24、172.16.20.0/24和172.16.30.0/24的流量
[FW-security-policy-ip]rule 1 name toInternet
[FW-security-policy-ip-1-toInternet]source-zone trust
[FW-security-policy-ip-1-toInternet]destination-zone untrust
[FW-security-policy-ip-1-toInternet]source-ip-subnet 172.16.10.1 24
[FW-security-policy-ip-1-toInternet]source-ip-subnet 172.16.20.1 24
[FW-security-policy-ip-1-toInternet]source-ip-subnet 172.16.30.1 24
[FW-security-policy-ip-1-toInternet]action pass
[FW-security-policy-ip-1-toInternet]quit
[FW-security-policy-ip]
#配置rule 2名称为dhcpserver,放行所有dhcp相关的流量,保证可以正常分配地址
[FW-security-policy-ip]rule 2 name dhcpserver
[FW-security-policy-ip-2-dhcpserver]service dhcp-client
[FW-security-policy-ip-2-dhcpserver]service dhcp-server
[FW-security-policy-ip-2-dhcpserver]action pass
[FW-security-policy-ip-2-dhcpserver]quit
[FW-security-policy-ip]
#配置rule 5名称为denyvlan10tovlan20,禁止vlan10访问vlan20。此时流量从g1/0/3(trust)进入设备,从1/0/3(trust)出设备,所以策略的匹配条件是trust到trust,源地址为172.16.10.0/24,目的地址为172.16.20.0/24,不配置规则动作为action pass,默认就是拒绝
[FW-security-policy-ip]rule 5 name denyvlan10tovlan20
[FW-security-policy-ip-5-denyvlan10tovlan20]source-zone trust
[FW-security-policy-ip-5-denyvlan10tovlan20]destination-zone trust
[FW-security-policy-ip-5-denyvlan10tovlan20]source-ip-subnet 172.16.10.0 24
[FW-security-policy-ip-5-denyvlan10tovlan20]destination-ip-subnet 172.16.20.0 24
[FW-security-policy-ip-5-denyvlan10tovlan20]quit
[FW-security-policy-ip]
#配置rule 10名称为denyvlan20tovlan30,禁止vlan20访问vlan30,原理同rule 5。
[FW-security-policy-ip]rule 10 name denyvlan20tovlan30
[FW-security-policy-ip-10-denyvlan20tovlan30]source-zone trust
[FW-security-policy-ip-10-denyvlan20tovlan30]destination-zone trust
[FW-security-policy-ip-10-denyvlan20tovlan30]source-ip-subnet 172.16.20.0 24
[FW-security-policy-ip-10-denyvlan20tovlan30]destination-ip-subnet 172.16.30.0 24
[FW-security-policy-ip-10-denyvlan20tovlan30]qu
.[FW-security-policy-ip]
#配置rule 15名称为permitother,允许内网其他vlan间互访,原理同rule 5。
[FW-security-policy-ip]rule 15 name permitother
[FW-security-policy-ip-15-permitother]source-zone trust
[FW-security-policy-ip-15-permitother]destination-zone trust
[FW-security-policy-ip-15-permitother]source-ip-subnet 172.16.10.0 24
[FW-security-policy-ip-15-permitother]source-ip-subnet 172.16.20.0 24
[FW-security-policy-ip-15-permitother]source-ip-subnet 172.16.30.0 24
[FW-security-policy-ip-15-permitother]action pass
[FW-security-policy-ip-15-permitother]qu
[FW-security-policy-ip]quit
[FW]
#保存配置
[FW] save force
4、 配置出口路由器
sys
[H3C]sysname Router
#配置路由器下行口为10.0.12.1/24
[Router]inter GigabitEthernet 0/1
[Router-GigabitEthernet0/1]ip address 10.0.12.1 24
[Router-GigabitEthernet0/1]quit
[Router]
#给内网三个网段写回程路由指向核心交换机
[Router]ip route-static 172.16.10.0 24 10.0.12.2
[Router]ip route-static 172.16.20.0 24 10.0.12.2
[Router]ip route-static 172.16.30.0 24 10.0.12.2
#保存配置
[Router] save force
一、结果验证
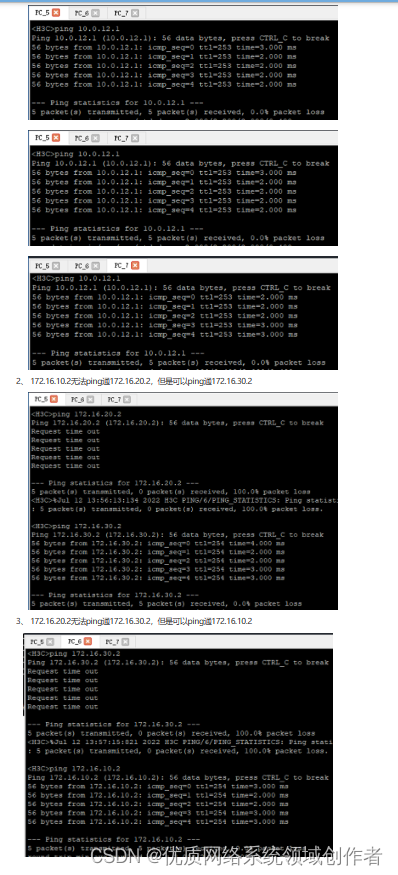
1、 三台pc均可ping通出口路由器
配置关键点
1、安全策略按照dis cu conf security-policy-ip看到的顺序从上往下匹配
2、配置安全策略前,先想一下流量走向,即流量从哪个接口进,又从哪个接口出,这样就可以根据接口确定源/目安全域了