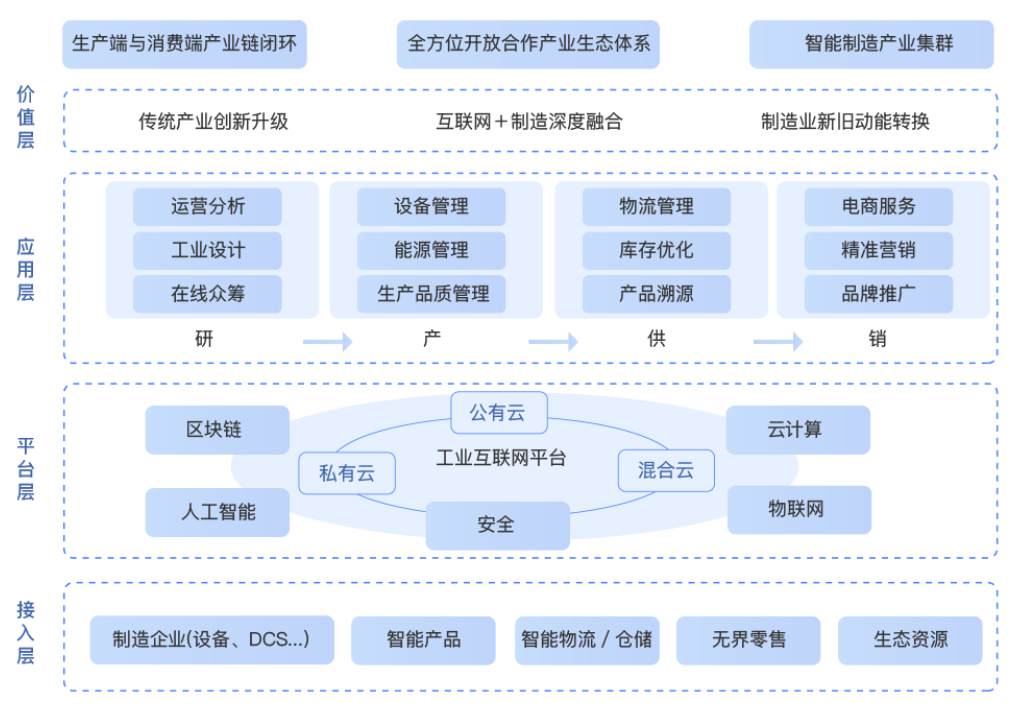
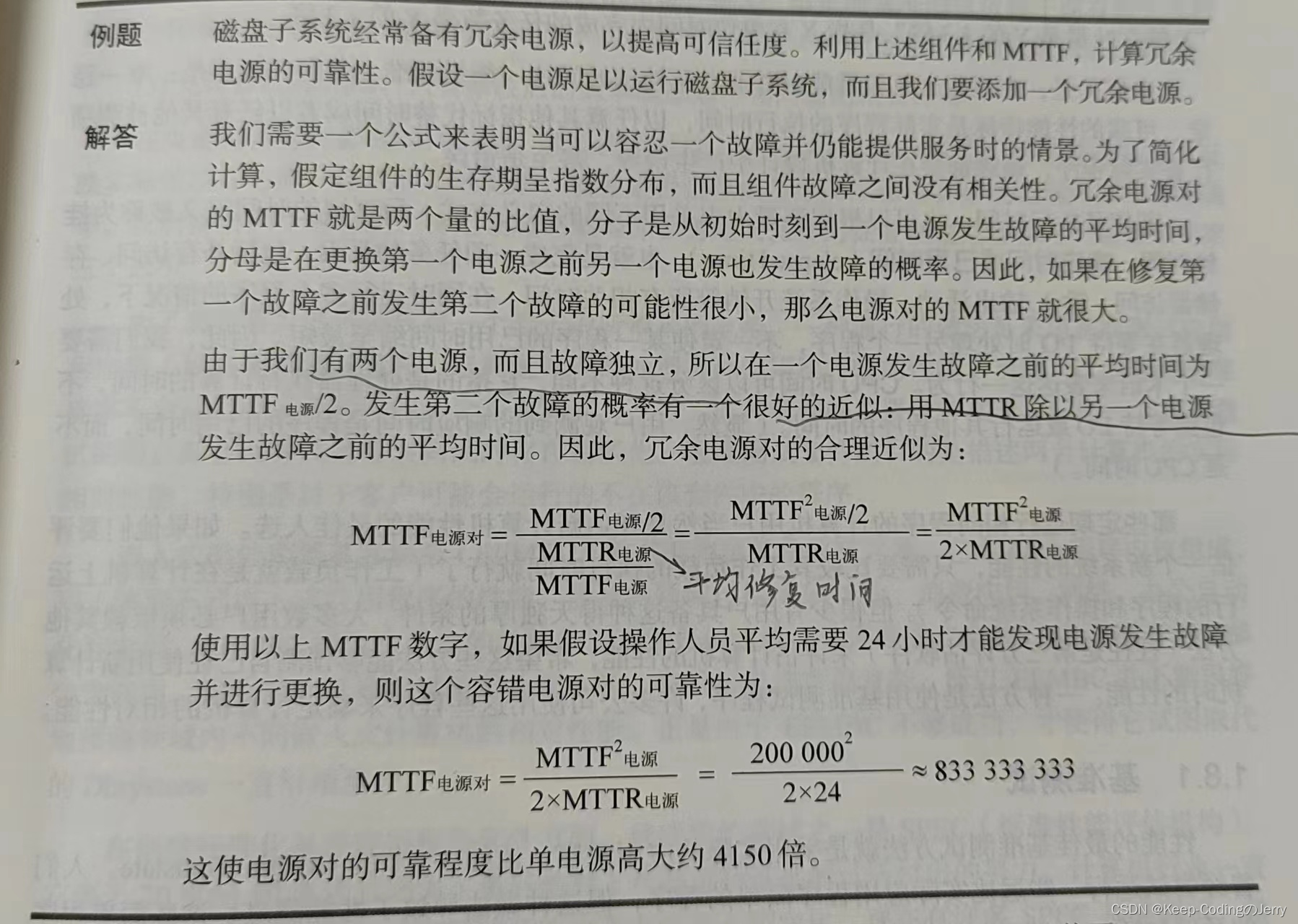
资料
- 使用 AWS CloudFormation StackSets 跨多个 AWS 账户和区域配置资源
- AWS cloudformation示例模板
- 堆栈集堆栈实例状态原因
很多组织使用大量的 AWS 账户,通常用 AWS Organizations 将这些账户组织为分层结构,分组为不同的组织部门 (OU)。并且希望确保每一个新账户都按照其内部标准进行设置,需要一致、可靠地设置 IAM 用户和角色、VPC 和 VPC 子网、安全组、配置规则、日志记录和 AWS Lambda 函数。cfn的stackset可以实现这一功能。

概念的区分
使用stackset,涉及到**stack sets(堆栈集),stack instances(堆栈实例),stacks(堆栈)**的概念
管理账户创建堆栈集,在目标账户中部署,更新和删除堆栈,需要在管理和目标账户之间建立信任关系。
权限模型,分为自管理权限和服务管理权限
- 自管理权限,用户自行维护创建stackset所需的iam角色,在账户之间建立信任关系
- 服务管理权限,通过aws organization服务自动创建角色和信任关系
堆栈集不能跨region,堆栈实例是对目标账户中堆栈的引用,和堆栈集是多对一关系

先决条件
需要在管理账户和目标账户进行配置,中国区只能使用自管理权限
Enabling trusted access with Amazon Organizations for Amazon CloudFormation StackSets isn’t currently supported in the China Beijing and Ningxia Regions.
账户的角色命名是强制规范的
The role in your administrator account should be named AWSCloudFormationStackSetAdministrationRole. The role in each of your target accounts should be named AWSCloudFormationStackSetExecutionRole.

1.在管理账户创建AWSCloudFormationStackSetAdministrationRole角色
可以直接使用以下命令使用cfn模板快速创建
aws cloudformation create-stack \
--stack-name MyStacksetAdminRole \
--template-url https://s3.amazonaws.com/cloudformation-stackset-sample-templates-us-east-1/AWSCloudFormationStackSetAdministrationRole.yml \
--capabilities CAPABILITY_NAMED_IAM
2.在目标账户创建AWSCloudFormationStackSetExecutionRole角色
使用以下命令在目标账户中配置角色,需要加入额外参数AdministratorAccountId指定管理账户
目标账户的对应角色需要权限来执行cfn堆栈操作,模板中指定为admin
可以在权限中进一步限制可以使用的资源和可以assume到该角色的主体
aws cloudformation create-stack \
--stack-name MyStacksetExecRole \
--template-url https://s3.amazonaws.com/cloudformation-stackset-sample-templates-us-east-1/AWSCloudFormationStackSetExecutionRole.yml \
--capabilities CAPABILITY_NAMED_IAM \
--parameter ParameterKey=AdministratorAccountId,ParameterValue=xxxxxxxx \
--profile group
使用堆栈集
我们使用简单的s3桶来测试堆栈实例的资源创建
AWSTemplateFormatVersion: "2010-09-09"
Resources:
S3Bucket:
Type: AWS::S3::Bucket
Properties:
VersioningConfiguration:
Status: Suspended
PublicAccessBlockConfiguration:
BlockPublicAcls: true
BlockPublicPolicy: true
IgnorePublicAcls: true
RestrictPublicBuckets: true
BucketEncryption:
ServerSideEncryptionConfiguration:
- ServerSideEncryptionByDefault:
SSEAlgorithm: AES256
在管理账户部署堆栈集
aws cloudformation create-stack-set --stack-set-name my-awsconfig-stackset --template-url https://xxxx.s3.cn-north-1.amazonaws.com.cn/cfn/resources.yaml
管理账户堆栈状态
aws cloudformation list-stack-sets
{
"Summaries": [
{
"StackSetName": "test-stackset",
"StackSetId": "test-stackset:73c2d435-0b3a-40d2-a2ca-ee95c0005bb0",
"Description": "test-stackset",
"Status": "ACTIVE",
"DriftStatus": "NOT_CHECKED"
},
}
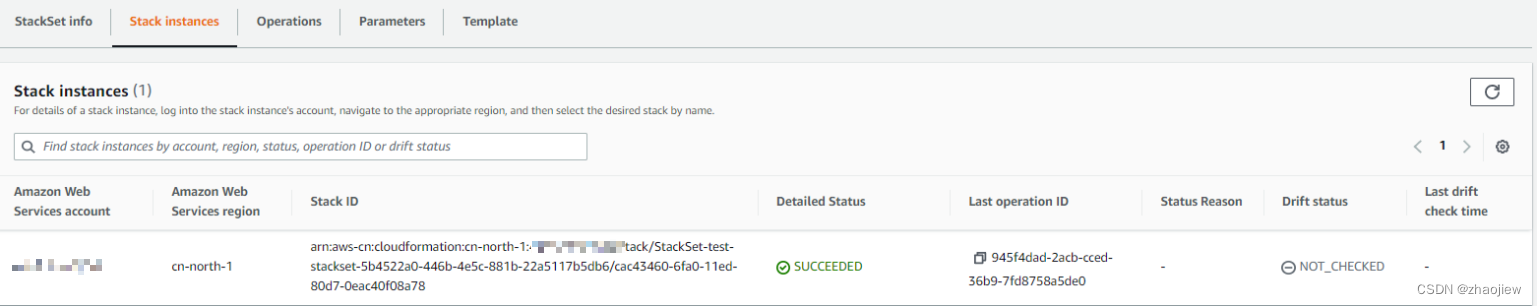
目标账户堆栈状态
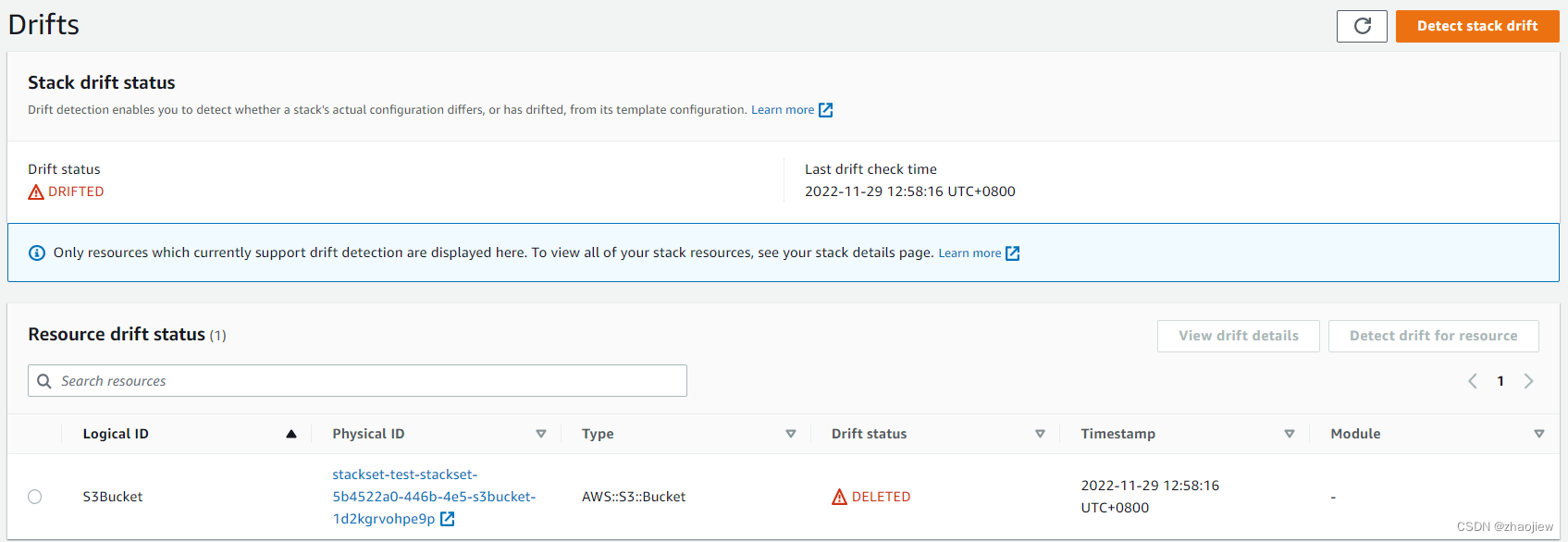
偏差检测
将上一步在目标账户创建的资源删除,之后在管理账户检测偏差,这项操作最终会在目标账户执行,检测到s3桶被删除并返回结果到stackset中
Inactive
Drift status
DRIFTED
1/1 drifted
Last drift check time
2022-11-29 12:58:15 UTC+0800
执行偏差检测的逻辑
When CloudFormation performs drift detection on a stack set, it performs drift detection on the stack associated with each stack instance in the stack set. To do this, CloudFormation compares the current state of each resource in the stack with the expected state of that resource, as defined in the stack’s template and any specified input parameters. If the current state of a resource varies from its expected state, that resource is considered to have drifted. If one or more resources in a stack have drifted, then the stack itself is considered to have drifted, and the stack instances that the stack is associated with is considered to have drifted as well. If one or more stack instances in a stack set have drifted, the stack set itself is considered to have drifted.



![[附源码]计算机毕业设计springboot基于Java的日用品在线电商平台](https://img-blog.csdnimg.cn/0b3e0de816594f41befe507d7aecd354.png)