501、Refer to the exhibit. What is the effect of the configuration?

A. The device will allow users at 192.168.0.202 to connect to vty lines 0 through 4 using the password ciscotestkey
B. The device will allow only users at 192 168.0.202 to connect to vty lines 0 through 4
C. When users attempt to connect to vty lines 0 through 4. the device will authenticate them against TACACS* if local authentication fails
D. The device will authenticate all users connecting to vty lines 0 through 4 against TACACS+
502、
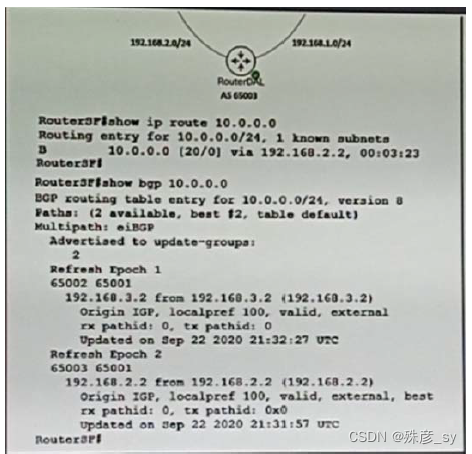
Refer to the exhibit.After configuring the BGP network,an engineer verifies that the path between server1 and server2 is functional,why did RouterSF choose the route from RouterDAL instead of the route from RouterCHI?
A. BGP is not running on RouterCHI
B. The Router-ID for Router DAL is lower than Router-ID for RouterCHI
C. There is a static route in RouterSF for 10.0.0.0/24
D. The route from RouterDAL has a lower MED
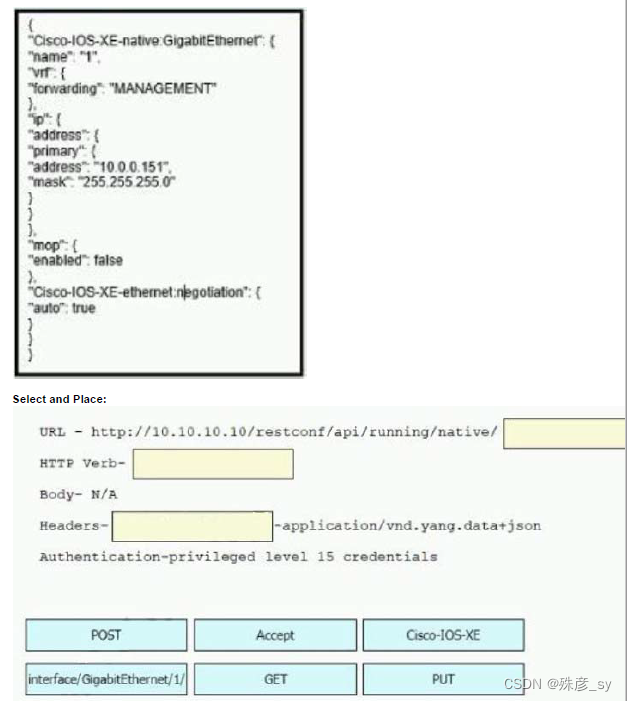
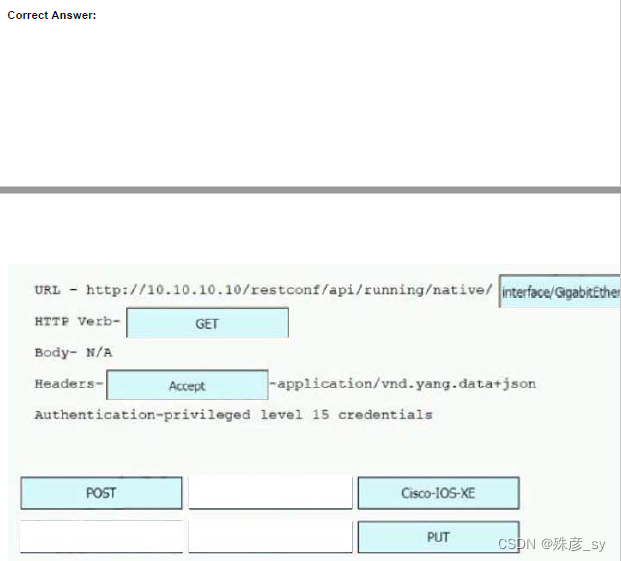
503、Refer to the exhibit Drag and drop the snippets into the RESTCONF request to form the request that returns this response. Not all options are used
504、 An engineer is configuring RADIUS-Based Authentication with EAP MS-CHAPv2 is configured on a client device.which outer method protocol must be configured on the ISE to support this anthentication type ?
A. EAP-TLS
B. LDAP
C. EAP-FAST
D. PEAP
505、Under which network conditions is an outbound QoS policy that is applied on a router WAN interface most beneficial?
A. under all network conditions
B. under network convergence conditions
C. under traffic classification and marking conditions
D. under interface saturation conditions
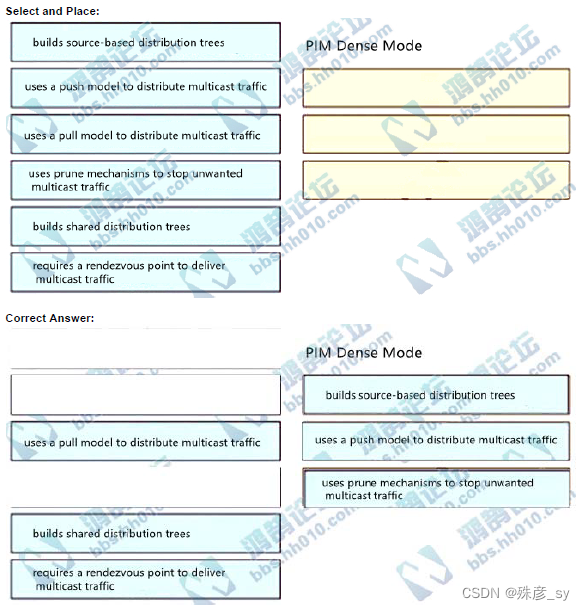
506、Drag and drop the characteristics of PIM Dense Mode from the left to the right.Not all options are used.
507、 Refer to the exhibit. Which command is required to verify NETCONF capability reply messages?
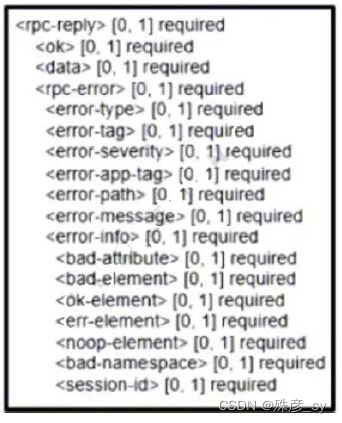
A. show netconf | section rpc-reply
B. show netconf rpc-reply
C. show netconf xml rpc-reply
D. show netconf schema | section rpc-reply
508、A network engineer must configure a router to send logging messages to a syslog server based on these
requirements:
uses syslog IP address: 10.10.10.1
uses a reliable protocol
must not use any well-known TCP/UDP ports
Which configuration must be used?
A. logging host 10.10.10.1 transport tcp port 1024
B. logging origin-id 10.10.10.1
C. logging host 10.10.10.1 transport udp port 1023
D. logging host 10.10.10.1 transport udp port 1024
509、

Refer to the exhibit.What is the value of the variable list after the code is run ?
A. [1,2,10]
B. [1,2,3,10]
C. [1,2,10,4]
D. [1,10,10,10]
510、A network engineer is designing a Qos policy for voice and video applications. which software queuing feature provides strict-priority servicing ?
A. Class-Based Weighted Fair Queuing
B. Link Fragmentation
C. Low Larency Queuing
D. Automatic Qos
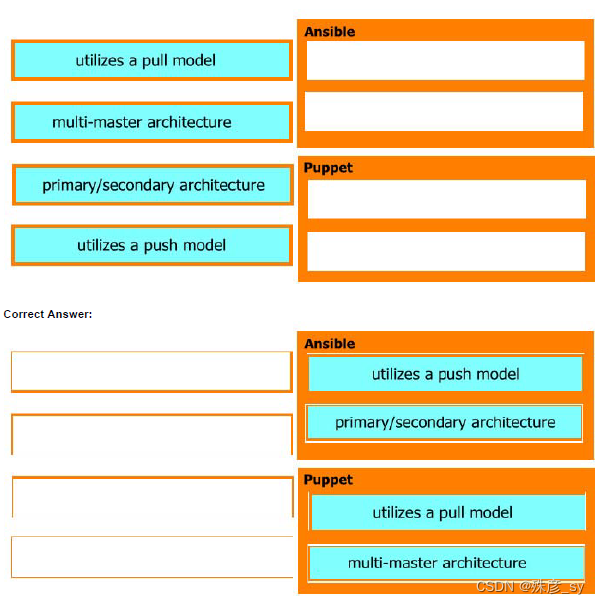
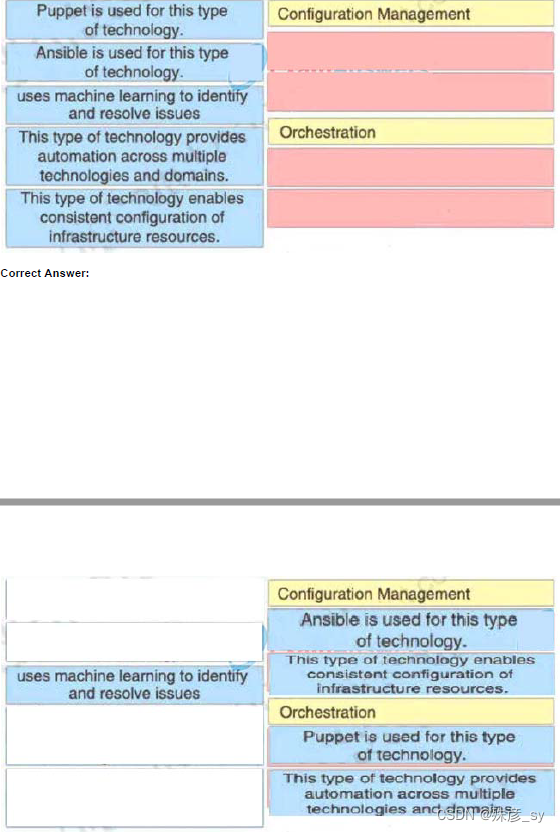
511、Drag and drop the characteristics from the left onto the orchestration tools they describe on the right.
Select and Place:
512、 Drag and drop the characteristics from the left onto the routing protocols they describe on the right.
Select and Place:
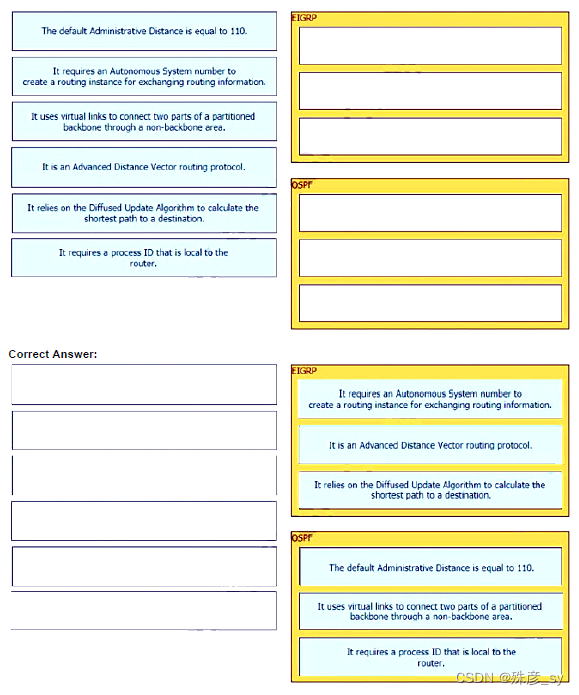
513、 An engineer is working with the Cisco DNA Center API Drag and drop the methods from the left onto the actions that they are used for on the right.
514、 A network engineer is adding an additional 10Gps link to an exiting 2x10Gps LACP-based LAG to augment its capacity. Network standards require a bundle interface to be taken out of service if one of its member links goes down, and the new link must be added with minimal impact to the production network. Drag and drop the tasks that the engineer must perform from the left into the sequence on the right. Not all options are used.

515、 Drag the characteristics from the left onto the routing protocols they describe on the right

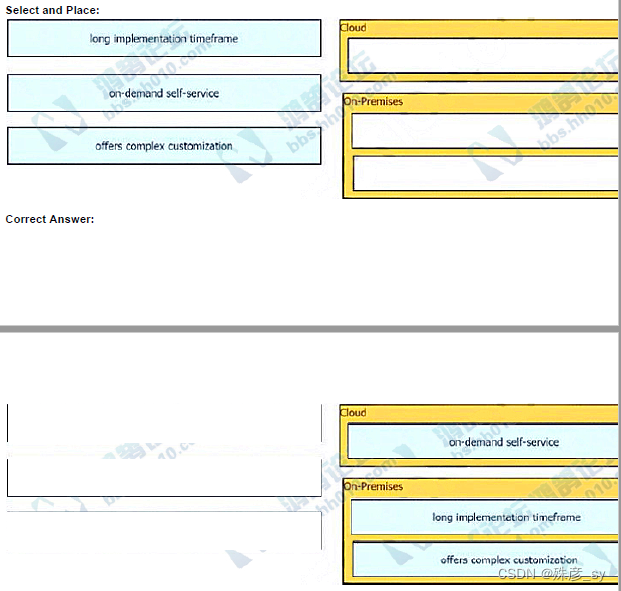
516、 Drag and drop the characteristics from the left onto the deployment models on the right
517、 What is the difference in dBm when an AP power increases from 25 mW to 100mW?
A. 75dBm
B. 150dBm
C. 6dBm
D. 125dBm
518、Which free application make REST call against DNA center?
A. Postman
B. Ansible
C. Chef
D. Puppet
519、Which marking field is used only as an internal marking within a router?
A. QoS Group
B. Discard Eligibility
C. IP Precedence
D. MPLS Experimental
520、Refer to the exhibit. Which command set enables router R2 to be configured via NETCONF? Administrator with PC LAN with a RADIUS Server, two PCs 10.0.1.0/24, R2 a link to the Internet cloud.
图缺
A. R2(config)#username Netconf privilege 15 password example_password
R2(config)#netconf-yang
R2(config)# netconf-yang feature candidate-datastore
B. R2(config)#snmp-server manager
R2(config)#snmp-server community ENCOR ro
C. R2(config)#snmp-server manager
R2(config)#snmp-server community ENCOR rw
D. R2(config)#netconf
R2(config)#ip http secure server
521、Which two actions are recommended as security best practice to protect REST API (Choose two)
A. Use TACACACS+ authentication
B. Enable dual authentication of the session
C. Enable out-of band authentication
D. Use SSL for encryption
E. Use a password hash
522、What are the two protocols redistributed into OMP?
A. OSPF
B. RIP
C. LDP
D. RSVP
E. EIGRP
523、An organization wants to use the cisco SD-WAN regionalized service-chaining feature to optimize cost and user experience with application in the network, which allows branch routers to analyze and steer traffic toward the required network function. Which feature meets this requirement?
A. Cloud Services Platform
B. VNF Service Chaning
C. Cloud onRamp for Colocation
D. Cloud onRamp for laaS
524、A customer has two Cisco WLCs that manage separate APs throughout a building. Each WLC advertises
the same SSID but terminates on different interfaces. Users report that they drop their connections and
change IP addresses when roaming. Which action resolves this issue?
A. Configure high availability
B. Enable test roaming
C. Enable client load balancing
D. Configure mobility groups
525、Refer to the exhibit. What is displayed when the code is run?

A. The answer is 25
B. The answer is 70
C. The answer is 5
D. The answer is 100
526、A script contains the statement “while loop != 999:”. Which value terminates the loop?
A. A value less then or equal to 999
B. A value greater then or equal to 999
C. A value not equal to 999
D. A value equal to 999
527、Which CISCO SD-WAN component authenticates the routers and the vSmart controllers?
A. vAnalytics
B. vBond orchestrator
C. vEdge
D. vManage NMS
528、When voice services are deployed over a wireless environment, which service must be disabled to ensure the quality of calls?
A. Aggressive load balancing
B. Dynamic transmit power control
C. Priority queuing
D. Fastlane
529、What is a characteristic of an AP operating in FlexConnect Mode?
A. All traffic traverses the WLC to ensure policy enforcement on client traffic
B. Forwarding continues when the AP loses connectivity to the WLC
C. APs connect in a mesh topology and elect a root AP
D. FlexConnect enables an AP to connect to multiple WLCs
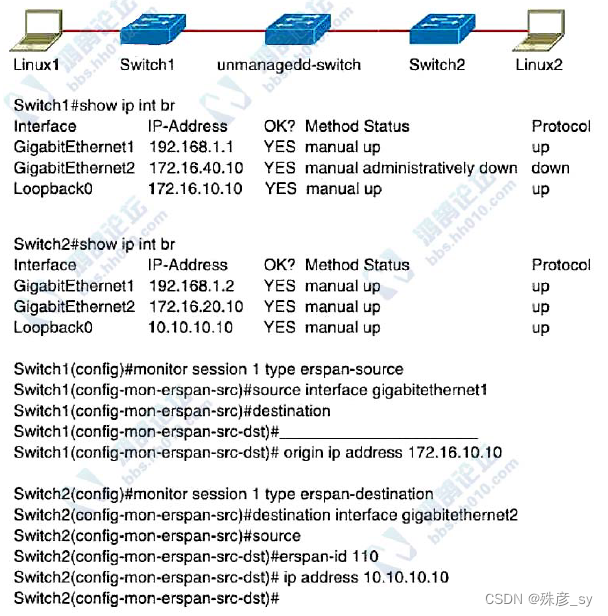
530、Refer to the exhibit. An engineer must configure an ERSPAN tunnel that mirrors traffic from Linux1 on Switch1 to Linux2 on Switch2. Which command must be added to the source configuration to enable the ERSPAN tunnel?
A. (config-mon-erspan-src-dst)#no shut
B. (config-mon-erspan-src-dst)#monitor session 1 activate
C. (config-mon-erspan-src-dst)#traffic bidirectional
D. (config-mon-erspan-src-dst)#ip address 10.10.10.10
531、Refer to the exhibit. An engineer configured the Bonjour Gateway on a Cisco WLC to support Apple Airplay. Users cannot see Apple TV while on the WLAN. Which action resolves this issue?
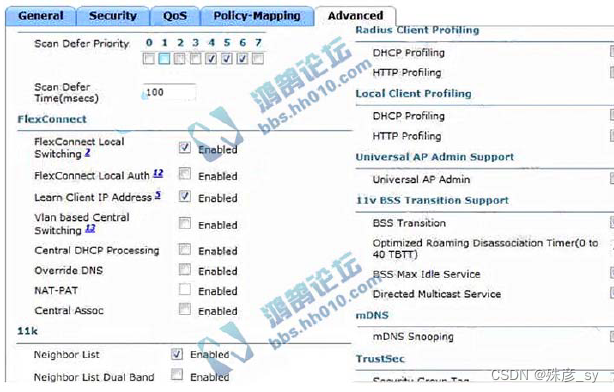
A. Disable Neighbor List Dual Band
B. Enable mDNS Snooping
C. Disable Directed Multicast
D. Enable FlexConnect Local Switching
532、Refer to the exhibit. What is the value of the variable list after the code is run?
list = [1, 2, 3, 4]
list[3] = 10
print(list)
A. [1, 10, 10, 10]
B. [1, 2, 10]
C. [1, 2, 10, 4]
D. [1, 2, 3, 10]
533、Refer to the exhibit.A network engineer must log in to the router via the console, but the RADIUS servers are not reachable. Which credentials allow console access?

A. the username “cisco” and the password “cisco123”
B. no username and only the password “test123”
C. no username and only the password “cisco123”
D. the username “cisco” and the password “cisco”
534、A customer transitions a wired environment to a Cisco SD-Access solution. The customer does not want to integrate the wireless network with the fabric. Which wireless deployment approach enables the two systems to coexist and meets the customer requirement?
A. Deploy a separate network for the wireless environment.
B. Implement a Cisco DNA Center to manage the two networks.
C. Deploy the wireless network over the top of the fabric.
D. Deploy the APs in autonomous mode.
535、Which two solutions are used for backing up a Cisco DNA Center Assurance database? (Choose two)
A. NFS share
B. local server
C. non-linux server
D. . remote server
E. bare metal server
536、Refer to the exhibit. Which command set must be applied on R1 to establish a BGP neighborship with R2 and to allow communication from R1 to reach the networks?
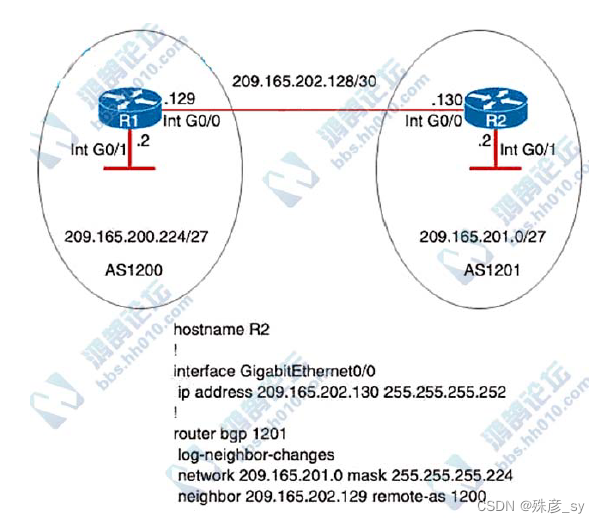
A. router bgp 1200
network 209.165.200.224 mask 255.255.255.224
neighbor 209.165.202.130 remote-as 1201
B. router bgp 1200
network 209.165.201.0 mask 255.255.255.224
neighbor 209.165.202.130 remote-as 1201
C. router bgp 1200
network 209.165.200.224 mask 255.255.255.224
neighbor 209.165.202.130 remote-as 1200
D. router bgp 1200
network 209.165.200.224 mask 255.255.255.224
neighbor 209.165.201.2 remote-as 1200
537、A customer wants to provide wireless access to contractors using a guest portal on Cisco ISE. The portal is also used by employees. A solution is implemented, but contractors receive a certificate error when they attempt to access the portal. Employees can access the portal without any errors. Which change must be implemented to allow the contractors and employees to access the portal?
A. Install a trusted third-party certificate on the Cisco ISE
B. Install an internal CA signed certificate on the Cisco ISE.
C. Install a trusted third-party certificate on the contractor devices.
D. Install an internal CA signed certificate on the contractor devices.
538、Refer the exhibit. Which configuration elects SW4 as the root bridge for VLAN 1 and puts G0/2 on SW2 into a blocking state?
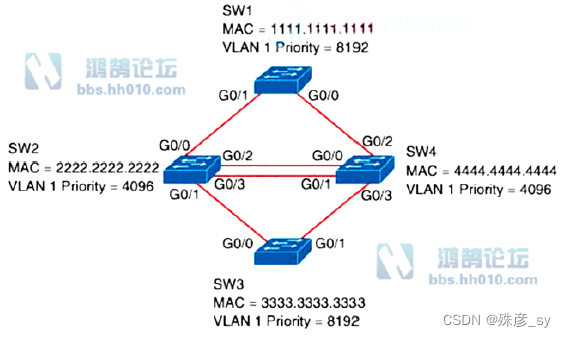
A. SW4(config)#spanning-tree vlan 1 priority 32768
!
SW2(config)#interface G0/2
SW2(config-if)#spanning-tree vlan 1 port-priority 0
B. SW4(config)#spanning-tree vlan 1 priority 32768
!
SW2(config)#int G0/2
SW2(config-if)#spanning-tree cost 128
C. SW4(config)#spanning-tree vlan 1 priority 0
!
SW2(config)#int G0/2
SW2(config-if)#spanning-tree cost 128
D. SW4(config)#spanning-tree vlan 1 priority 0
!
SW2(config)#interface G0/2
SW2(config-if)#spanning-tree vlan 1 port-priority 64
539、Which Python code snippet must be added to the script to save the returned configuration as a JSONformatted file?
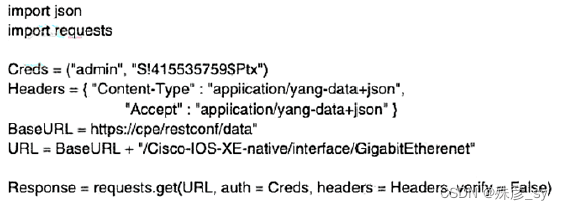
A. with open(“ifaces.json”, “w”) as OutFile:
OutFile.write(Response.text)
B. with open(“ifaces.json”, “w”) as OutFile:
OutFile.write(Response.json())
C. with open(“ifaces.json”, “w”) as OutFile:
JSONResponse = json.loads(Response.text)
OutFile.write(JSONResponse)
D. with open(“ifaces.json”, “w”) as OutFile:
OutFile.write(Response)
540、Refer to the exhibit. An engineer must configure an ERSPAN session with the remote end of the session 10.10.0.1. Which commands must be added to complete the configuration?
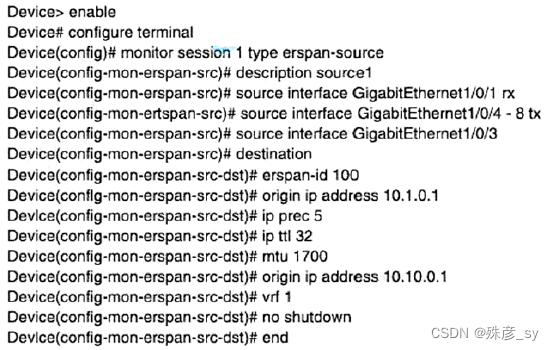
A. Device(config)# monitor session 1 type erspan-source
Device(config-mon-erspan-src)# destination
Device(config-mon-erspan-src-dst)#no origin ip address 10.10.0.1
Device(config-mon-erspan-src-dst)#ip address 10.10.0.1
B. Device(config)# monitor session 1 type erspan-destination
Device(config-mon-erspan-src)# source
Device(config-mon-erspan-src-dst)#origin ip address 10.1.0.1
C. Device(config)# monitor session 1 type erspan-source
Device(config-mon-erspan-src)# destination
Device(config-mon-erspan-src-dst)#no origin ip address 10.10.0.1
Device(config-mon-erspan-src-dst)#ip destination address 10.10.0.1
D. Device(config)# monitor session 1 type erspan-source
Device(config-mon-erspan-src)# destination
Device(config-mon-erspan-src-dst)#no vrf 1
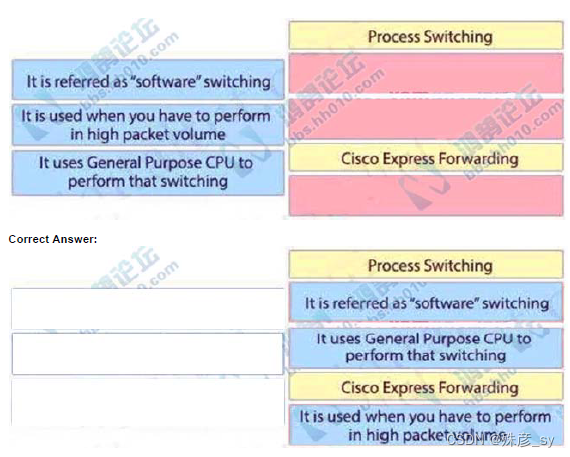
541、Drag and drop packet switching architecture from the left onto the correct positions on the right.
Select and Place:
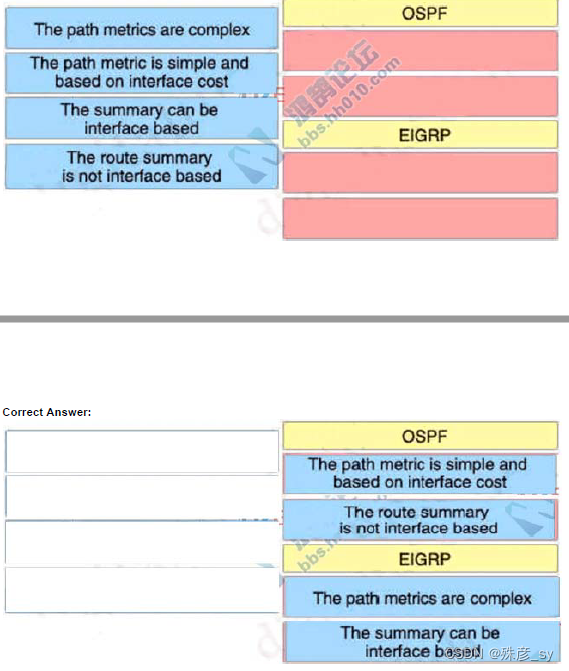
542、 Drag and drop the characteristics from the left onto the routing protocol types on the right.
Select and Place:
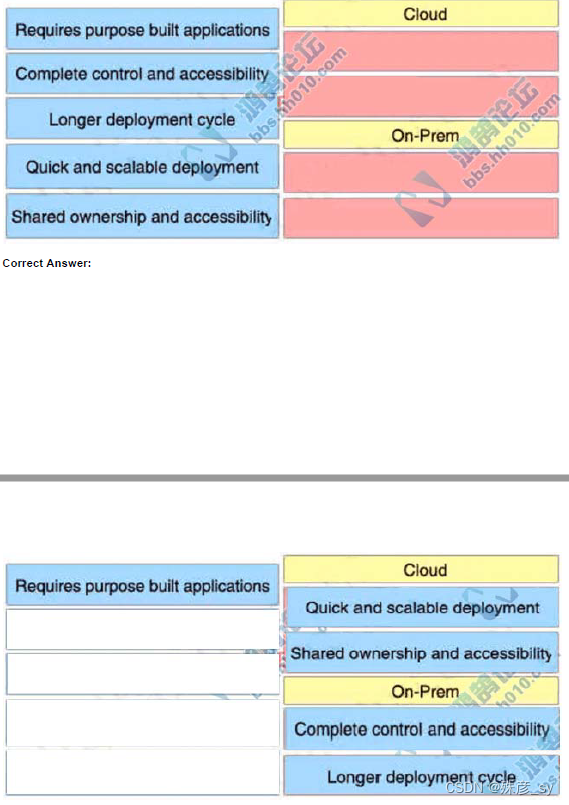
543、 Drag and drop the characteristics from the left onto the correct infrastructure deployment types on the right.
Select and Place:
544、 Drag and drop the characteristics from the left onto the technology types on the right.
Select and Place:
545、 What is the result when an active route processor fails in a design that combines NSF with SSO?
A. An NSF-aware device immediately updates the standby route processor RIB without churning the network.
B. The standby route processor temporarily forwards packets until route convergence is complete.
C. An NSF-capable device immediately updates the standby route processor RIB without churning the network.
D. The standby route processor immediately takes control and forwards packets along known routes
546、An engineer uses the Design workflow to create a new network infrastructure in Cisco DNA Center. How is
the physical network device hierarchy structured?
A. by location
B. by role
C. by organization
D. by hostname naming convention
547、Refer to the exhibit. A network engineer must configure NETCONF. After creating the configuration, the engineer gets output from the command show line, but not from show runningconfig. Which command completes the configuration?

A. Device(config)#netconf lock-time 500
B. Device(config)#netconf max-message 1000
C. Device(config)#no netconf ssh acl 1
D. Device(config)#netconf max-sessions 100
548、Refer to the exhibit. Router BRDR-1 is configured to receive the 0.0.0.0/0 and 172.17.1.0/24 network via BGP and advertise them into OSPF are 0. An engineer has noticed that the OSPF domain is receiving only the 172.17.1.0/24 route and default route 0.0.0.0/0 is still missing. Which configurating must engineer apply to resolve the problem?
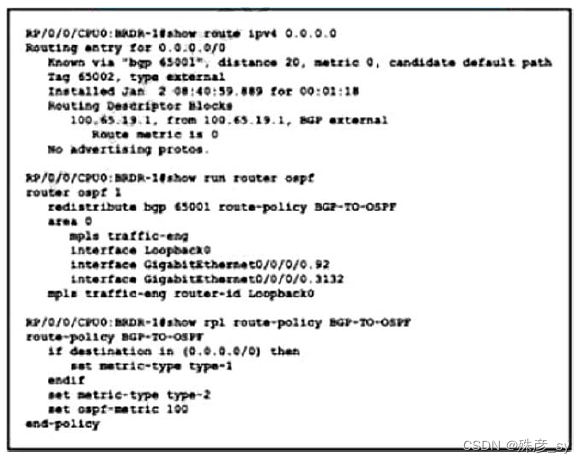
A. router ospf 1
default-information originate always
end
B. router ospf 1
redistribute bgp 65001 metic 100 route-policy BGP-TO-OSPF
end
C. router ospf 1
default-metric 100
end
D. router ospf 1
default-information originate
end
549、An engineer must create an EEM script to enable OSPF debugging in the event the OSPF neighborship
goes down. Which script must the engineer apply?
A. event manager applet ENABLE_OSPF_DEBUG
event syslog pattern''%OSPF-5-ADJCHG Process 5,Nbr 1.1.1.1 on serial0/0 from LOADING to FULL''
action 1.0 cli command''enable''
action 2.0 cli command'' debug ip ospf event''
action 3.0 cli command'' debug ip ospf adj''
action 4.0 syslog priority informational msg'' ENABLE_OSPF_DEBUG''
B. event manager applet ENABLE_OSPF_DEBUG
event syslog pattern''%OSPF-5-ADJCHG Process 5,Nbr 1.1.1.1 on serial0/0 from LOADING to FULL''
action 2.0 cli command'' debug ip ospf event''
action 3.0 cli command'' debug ip ospf adj''
action 4.0 syslog priority informational msg'' ENABLE_OSPF_DEBUG''
C. event manager applet ENABLE_OSPF_DEBUG
event syslog pattern''%OSPF-5-ADJCHG Process 6,Nbr 1.1.1.1 on serial0/0 from FULL to DOWN''
action 1.0 cli command''enable''
action 2.0 cli command'' debug ip ospf event''
action 3.0 cli command'' debug ip ospf adj''
action 4.0 syslog priority informational msg'' ENABLE_OSPF_DEBUG''
D. event manager applet ENABLE_OSPF_DEBUG
event syslog pattern''%OSPF-1-ADJCHG Process 5,Nbr 1.1.1.1 on serial0/0 from FULL to DOWN''
action 2.0 cli command'' debug ip ospf event''
action 3.0 cli command'' debug ip ospf adj''
action 4.0 syslog priority informational msg'' ENABLE_OSPF_DEBUG''
550、An engineer is implementing a Cisco MPLS TE tunnel to improve the streaming experience for the clients
of a video-on-demand server. Which action must the engineer perform to configure extended discovery to
support the MPLS LDP session between the headend and tailend routers?
A. Configure the interface bandwidth to handle TCP and UDP traffic between the LDP peers
B. Configure a Cisco MPLS TE tunnel on both ends of the session
C. Configure an access list on the interface to permit TCP and UDP traffic
D. Configure a targeted neighbor session.