451、what is the function of the LISP map resolver?
A. to send traffic to non-LISP sites when connected to a service provider that does not accept nonroutable EIDs as packet sources
B. to connect a site to the LISP-capabie part of a core network, publish the EID-to-RLOC mappings for the site, and respond to map-request messages
C. to decapsulate map-request messages from ITRs and forward the messages to the MS
D. to advertise routable non-LISP traffic from one address family to LISP sites in a different address family
452、An engineer configures HSRP group 37.The configuration does not modify the default virtual MAC address.which virtual MAC address does the group use ?
A. 00:00:0c:07:ac:25
B. c0:39:97:39:655:5
C. c0:00:00:25:00:00
D. 00:00:0c:07:ac:37
453、If the noise floor is -90 dBm and the wireless client is receiving a signal of -75 dBm,what is the SNR?
A. 15
B. 1.2
C. -165
D. 83
454、
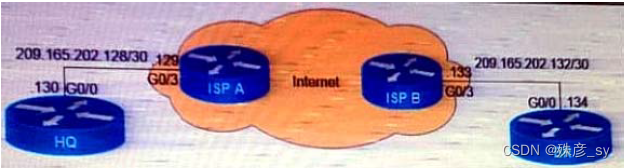
Refer to the exhibit. What is the effect of these commands on the BR and HQ tunnel interfaces?
BR(config)#interface tunnel 1
BR(config-if)#keepalive 5 3
HQ(config)#interface tunnel 1
HQ(config-if)#keepalive 5 3
A. The tunnel line protocol goes down when the keepalive counter reaches 5
B. The keepalives are sent every 5 seconds and 3 retnes
C. The keepalives are sent every 3 seconds and 5 retnes
D. The tunnel line protocol goes down when the keepalive counter reaches 6
455、Drag and drop the snippets onto the blanks within the code to construct a script that advertises the network
prefix 192.168.5.0/24 session.Not all options are used.
Select and Place:

456、 What is used to perform QoS packet classification?
A. the Options field in the Layer 3 header
B. the Type field in the Layer 2 frame
C. the Flags field in the Layer 3 header
D. the ToS field in the Layer 3 header
457、Which LISP component is required for a LISP site to communicate with a non-LISP site?
A. ETR
B. ITR
C. Proxy ETR
D. Proxy ITR
458、Which technology is used as the basis for the Cisco SD-Access data plane?
A. IPsec
B. LISP
C. VXLAN
D. 802.1Q
459、While configuring an IOS router for HSRP with a virtual IP of 10.1.1.1, an engineer sees this log message:
Jan 1 12:12:14.122: %HSRP-4-DIFFVIP1: GigabitEthernet0/0 Grp 1 active routers virtual IP address 10.1.1.1 is different to the locally configured address 10.1.1.25
Which configuration change must the engineer make?
A. Change the HSRP group configuration on the remote router to 1
B. Change the HSRP virtual address on the local router to 10.1.1.1
C. Change the HSRP virtual address on the remote router to 10.1.1.1
D. Change the HSRP group configuration on the local router to 1
460、What is a characteristic of YANG?
A. It is a Cisco proprietary language that models NETCONF data
B. It allows model developers to create custom data types
C. It structures data in an object-oriented fashion to promote model reuse
D. It provides loops and conditionals to control now within models
461、When is an external antenna used inside a building?
A. only when using 5 GHz
B. only when using 2.4 GHz
C. when it provides the required coverage
D. only when using Mobility Express
462、Drag and drop the snippets onto the blanks within the code construct a script that configure a loopback interface with an IP address. Not all options are used.
Select and Place:

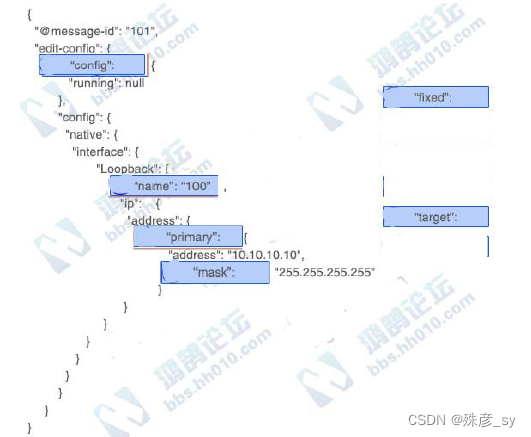
463、 Refer to the exhibit.

How was spanning-tree configured on this interface?
A. By entering the command spanning-tree portfast trunk in the interface configuration mode.
B. By entering the command spanning-tree portfast in the interface configuration mode
C. By entering the command spanning-tree mst1 vlan 10,20,30,40 in the global configuration mode
D. By entering the command spanning-tree vlan 10,20,30,40 root primary in the interface configuration mode
464、An engineer is troubleshooting the AP join process using DNS. Which FQDN must be resolvable on the network for the access points to successfully register to the WLC?
A. cisco-capwap-controller.domain.com
B. wlchostname.domain.com
C. ap-manager.domain.com
D. primary-wlc.domain.com
465、How is Layer 3 roaming accomplished in a unified wireless deployment?
A. An EoIP tunnel is created between the client and the anchor controller to provide seamless connectivity as the client is associated with the new AP
B. The client entry on the original controller is passed to the database on the new controller
C. The new controller assigns an IP address from the new subnet to the client
D. The client database on the original controller is updated the anchor entry, and the new controller database is updated with the foreign entry.
466、A network administrator has designed a network with two multilayer switches on the distribution layer, which act as default gateways for the end hosts. Which two technologies allow every end host in a VLAN to use both gateways? (Choose two)
A. HSRP
B. GLBP
C. MHSRP
D. VRRP
E. VSS
467、Which measurement is used from a post wireless survey to depict the cell edge of the access points?
A. CCI
B. Noise
C. SNR
D. RSSI
468、Refer to the exhibit.

While troubleshooting a routing issue, an engineer issues a ping from S1 to S2. Which two actions from the
initial value of the TTL? (Choose two)
A. The packet reaches R3, and the TTL expires
B. R2 replies with a TTL exceeded message
C. R1 replies with a TTL exceeded message
D. The packet reaches R2 and the TTL expires
E. R3 replies with a TTL exceeded message
F. The packet reaches R1 and the TTL expires
469、Refer to the exhibit.
![]()
Which command set must be added to permit and log all traffic that comes from 172.20.10.1 in interface
GigabitEthernet0/1 without impacting the functionality of the access list?
A. Router(config)#ip access-list extended 100
Router(config-ext-nacl)#5 permit ip 172.20.10.0 0.0.0.255 any log
Router(config)#interface GigabitEthernet0/1
Router(config-if)#access-group 100 in
B. Router(config)#no access-list 100 permit ip 172.16.0.0 0.0.15.255 any
Router(config)#access-list 100 permit ip 172.16.0.0 0.0.15.255 any log
Router(config)#interface Gigabit Ether net0/1
Router(config-if)#access-group 100 in
C. Router(config)#access-list 100 permit ip host 172.20.10.1 any log
Router(config)#interface GigabitEthernet0/1
Router(config-if)#access-group 100 in
D. Router(config)#access-list 100 seq 5 permit ip host 172.20.10.1 any log
Router(config)#interface GigabitEthernet0/1
Router(config-if)#access-group 100 in
470、How are the different versions of IGMP compatible?
A. IGMPv2 is compatible only with IGMPv1
B. IGMPv2 is compatible only with IGMPv2
C. IGMPv3 is compatible only with IGMPv3
D. IGMPv3 is compatible only with IGMPv1
471、An engineer runs the code against an API of Cisco DNA Center, and the platform returns this output.

What does the response indicate?
A. The authentication credentials are incorrect
B. The URI string is incorrect
C. The Cisco DNA Center API port is incorrect
D. The HTTP method is incorrect
472、What is one difference between Saltstack and Ansible?
A. SaltStack uses an API proxy agent to program Cisco boxes on agent mode, whereas Ansible uses a Telnet connection
B. SaltStack uses the Ansible agent on the box, whereas Ansible uses a Telnet server on the box
C. SaltStack is constructed with minion, whereas Ansible is constructed with YAML
D. SaltStack uses SSH to interact with Cisco devices, whereas Ansible uses an event bus
473、What is the centralized control policy in a Cisco SD-WAN deployment?
A. list of ordered statements that define user access policies
B. list of enabled services for all nodes within the cloud
C. set of rules that governs nodes authentication within the cloud
D. set of statements that defines how routing is performed
474、Refer to the exhibit.
![]()
After configurating an IPsec VPN, an engineer enters the show command to verify the ISAKMP SA status.
What does the status show?
A. Peers have exchanged keys, but ISAKMP SA remains unauthenticated.
B. ISAKMP SA is authenticated and can be used for Quick Mode.
C. VPN peers agreed on parameters for the ISAKMP SA
D. ISAKMP SA has been created, but it has not continued to form.
475、Refer to the exhibit.

An engineer attempts to create a configuration to allow the Blue VRF to leak into the global routing table,
but the configuration does not function as expected. Which action resolves this issue?
A. Change the access-list number in the route map
B. Change the source network that is specified in access-list 101
C. Change the route-map configuration to VRF_BLUE
D. Change the access-list destination mask to a wildcard
476、Which Cisco DNA center application is responsible for group-based access control permissions?
A. Design
B. Provision
C. Assurance
D. Policy
477、A client device roams between wireless LAN controllers that are mobility peers. Both controllers have dynamic interface on the same client VLAN. Which type of roam is described?
A. intra-VLAN
B. intra-controller
C. inter-controller
D. inter-subnet
478、Which line must be added in the Python function to return the JSON object {“cat_9k”:”FXS193202SE”)?

A. return (json.dumps({d[‘hostname’]: d[‘serialNumber’] for d in json.loads(test_json)[‘response’]}))
B. return (json.loads({for d in json.dumps(test_json)[‘response’]: d[‘hostname’]: d[‘serialNumber’]}))
C. return (json.loads({d[‘hostname’]: d[‘serialNumber’] for d in json.dumps(test_json)[‘response’]}))
D. return (json.dumps({for d in json.loads(test_json)[‘response’]: d[‘hostname’]: d[‘serialNumber’]}))
479、Refer to the exhibit. A network engineer troubleshoots an issue with the port channel between SW1 and SW2. Which command resolves the issue?

*Aug 12 02:22:23.233: %LINK-3-UPDOWN: Interface Port-channel10, changed state to down
*Aug 12 02:22:24.236: %LINEPROTO-5-UPDOWN: Line protocol on Interface Port-channel10,changed
state to down
*Aug 12 02:22:27.237: %ETC-5-L3DONTBNDL2: Gi0/1 suspended: LACP currently not enabled on the
remote port
*Aug 12 02:22:29.233: %ETC-5-L3DONTBNDL2: Gi0/0 suspended: LACP currently not enabled on the remote port
A. SW1(config-if)#channel-group 10 mode active
B. SW1(config-if)#channel-group 10 mode desirable
C. SW2(config-if)#channel-group 10 mode on
D. SW2(config-if)#switchport mode trunk
480、Drag and drop the characteristics from the left onto the routing protocols they describe on the right.
Select and Place:

481、 Drag and drop the characteristics from the left onto the protocols they apply to on the right.
Select and Place:

482、 How is 802.11 traffic handled in a fabric-enabled SSID?
A. converted by the AP into 802.3 and encapsulated into a VLAN
B. centrally switched back to WLC where the user traffic is mapped to a VXLAN on the WLC
C. centrally switched back to WLC where the user traffic is mapped to a VLAN on the WLC
D. converted by the AP into 802.3 and encapsulated into VXLAN
483、Drag and drop the wireless elements on the left to their definitions on the right.

484、 Refer to the exhibit.

A network engineer configures NAT on R1 and enters the show command to verify the configuration. What does the output confirm?
A. R1 is configured with NAT overload parameters
B. The first packet triggered NAT to add on entry to NAT table
C. A Telnet from 160.1.1.1 to 10.1.1.10 has been initiated
D. R1 to configured with PAT overload parameters
485、Which congestion queuing method on Cisco IOS based routers uses four static queues?
A. low latency
B. custom
C. weighted fair
D. Priority
486、What does the Cisco DNA REST response indicate?

A. Cisco DNA Center has the incorrect credentials for cat9000-1
B. Cisco DNA Center is unable to communicate with cat9000-1
C. Cisco DNA Center has the incorrect credentials for RouterASR-1
D. Cisco DNA Center has the incorrect credentials for cat3850-1
487、Refer to the exhibit.

Rapid PVST+ is enabled on all switches. Which command set must be configured on Switch1 to achieve
the following results on port fa0/1?
+ When a device is connected, the port transitions immediately to a forwarding state
+ The interface should not send or receive BPDUs.
+ If a BPDU is received, it continues operating normally.
A. Switch1(config)# interface f0/1
Switch1(config-if)# spanning-tree portfast
Switch1(config-if)# spanning-tree bpduguard enable
B. Switch1(config)# spanning-tree portfast bpduguard default
Switch1(config)# interface f0/1
Switch1(config-if)# spanning-tree portfast
C. Switch1(config)#interface f0/1
Switch1(config-if)# spanning-tree portfast
D. Switch1(config)#spanning-tree portfast bpdufilter default
Switch1(config)# interface f0/1
Switch1(config-if)# spanning-tree portfast
488、Refer to the exhibit.

After running the code in the exhibit. Which step reduces the amount of data that NETCONF server returns to the NETCONF client, to only the interface’s configuration?
A. Create an XML filter as a string and pass it to get_config() method as an argument
B. Use the txml library to parse the data returned by the NETCONF server for the interface’s configuration
C. Create a JSON filter as a string and pass it to the get_config() method as an argument
D. Use the JSON library to parse the data returned by the NETCONF server for the interface’s
configuration
489、Refer to the exhibit

External users require HTTP connectivity to an internal company web server that is listening on TCP port
8080. Which command set accomplishes this requirement?
A. interface G0/0
ip address 209.165.200.225 255.255.255.224
ip nat inside
B. interface G0/0
ip address 209.165.200.225 255.256.255.224
ip nat inside
interface G0/1
ip address 10.1.1.1 255.255.255.0
ip nat outside
ip nat inside source static tcp 209.165.200.225 80 10.1.1.100 8080
C. interface G0/0
ip address 209.165.200.225 255.255.255.224
ip nat inside
interface G0/1
ip address 10.1.1.1 255.255.255.0
ip nat outside
ip nat inside source static tcp 10.1.1.1 8080 209.166.200.225 80
D. interface G0/0
ip address 209.165.200.225 255.255.255.224
ip nat outside
interface G0/1
ip address 10.1.1.1 255.255.255.0
ip nat inside
ip nat inside source static tcp 10.1.1.100 8080 interface G0/0 80
E. interface G0/0
ip address 209.165.200.225 255.255.255.224
ip nat outside
interface G0/1
ip address 10.1.1.1 255.255.255.0
ip nat inside
ip nat inside source static tcp 209.165.200.225 8080 10.1.1.100 8080
490、A network engineer configures BGP between R1 and R2. Both routers use BGP peer group CORP and are set up to use MD5 authentication. This message is logged to the console of router R1:*Jun 5 33:34:33.033: %TCP-6-BADAUTH: Invalid MD5 digest from 10.10.10.1 (29832) to 10.120.10.1 (179) tableid -0
Which two configurations allow a peering session to form between R1 and R2? (Choose two)
A. R2(config-router)#neighbor 10.10.10.1 peer-group CORP
R2(config-router)#neighbor CORP password Cisco
B. R2(config-router)#neighbor 10.10.10.1 peer-group CORP
R2(Config-router)#neighbor PEER password Cisco
C. R1(config-router)#neighbor 10.10.10.1 peer-group CORP
R1(config-router)#neighbor CORP password Cisco
D. R1(config-router)#neighbor 10.120.10.1 peer-group CORP
R1(config-router)#neighbor CORP password Cisco
E. R2(config-router)#neighbor 10.120.10.1 peer-group CORP
R2(config-router)#neighbor CORP password Cisco
491、Which three elements determine Air Time efficiency? (Choose three)
A. evert-driven RRM
B. data rate (modulation density) or QAM
C. channel bandwidth
D. number of spatial streams and spatial reuse
E. RF group leader
F. dynamic channel assignment
492、Which features does Cisco EDR use to provide threat detection and response protection?
A. containment, threat intelligence, and machine learning
B. firewalling and intrusion prevention
C. container-based agents
D. cloud analysis and endpoint firewall controls
493、Which two threats does AMP4E have the ability to block? (Choose two)
A. DDoS
B. ransomware
C. SQL injection
D. Microsoft Word macro attack
E. email phishing
494、Refer to the exhibit.
%OSPF-5-ADJCHG: Process 1, Nbr 10.0.0.2 on FastEthernet0/0 from FULL to DOWN,
Neighbor Down: Interface down or detached
%OSPF-6-AREACHG: 10.0.0.1/32 changed from area 0 to area 1
%OSPF-4-ERRRCV: Received invalid packet: mismatch area ID, from
backbone area must be virtual-link but not found from 10.0.0.2, FastEthernet0/0
What is the cause of the log messages?
A. OSPF area change
B. hello packet mismatch
C. MTU mismatch
D. IP address mismatch
495、What are two characteristics of VXLAN? (Choose two)
A. It uses VTEPs to encapsulate and decapsulate frames.
B. It has a 12-bit network identifier
C. It extends Layer 2 and Layer 3 overlay networks over a Layer 2 underlay.
D. It lacks support for host mobility
E. It allows for up to 16 million VXLAN segments
496、Refer to the exhibit.

A network engineer configures a new GRE tunnel and enters the show run command. What does the output verify?
A. The tunnel keepalive is configured incorrectly because they must match on both sites
B. The tunnel destination will be known via the tunnel interface
C. The tunnel will be established and work as expected
D. The default MTU of the tunnel interface is 1500 byte.
497、Which design principle slates that a user has no access by default to any resource, and unless a resource is explicitly granted, it should be denied?
A. least privilege
B. fail-safe defaults
C. economy of mechanism
D. complete mediation
498、How does an on-premises infrastructure compare to a cloud infrastructure?
A. On-premises can increase compute power faster than cloud
B. On-premises requires less power and cooling resources than cloud
C. On-premises offers faster deployment than cloud
D. On-premises offers lower latency for physically adjacent systems than cloud.
499、What is the function of a VTEP in VXLAN?
A. provide the routing underlay and overlay for VXLAN headers
B. dynamically discover the location of end hosts in a VXLAN fabric
C. encapsulate and de-encapsulate traffic into and out of the VXLAN fabric
D. statically point to end host locations of the VXLAN fabric
500、Refer to the exhibit. An engineer implemented several configuration changes and receives the logging message on switch1. Which action should the engineer take to resolve this issue?
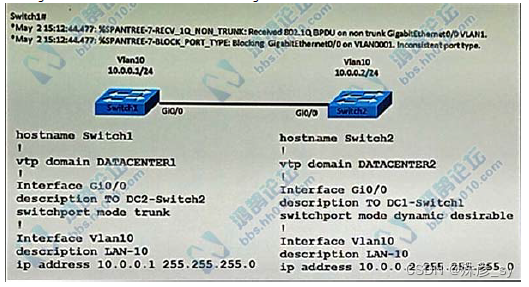
A. Change the VTP domain to match on both switches
B. Change Switch2 to switch port mode dynamic auto
C. Change Switch1 to switch port mode dynamic auto
D. Change Switch1 to switch port mode dynamic desirable