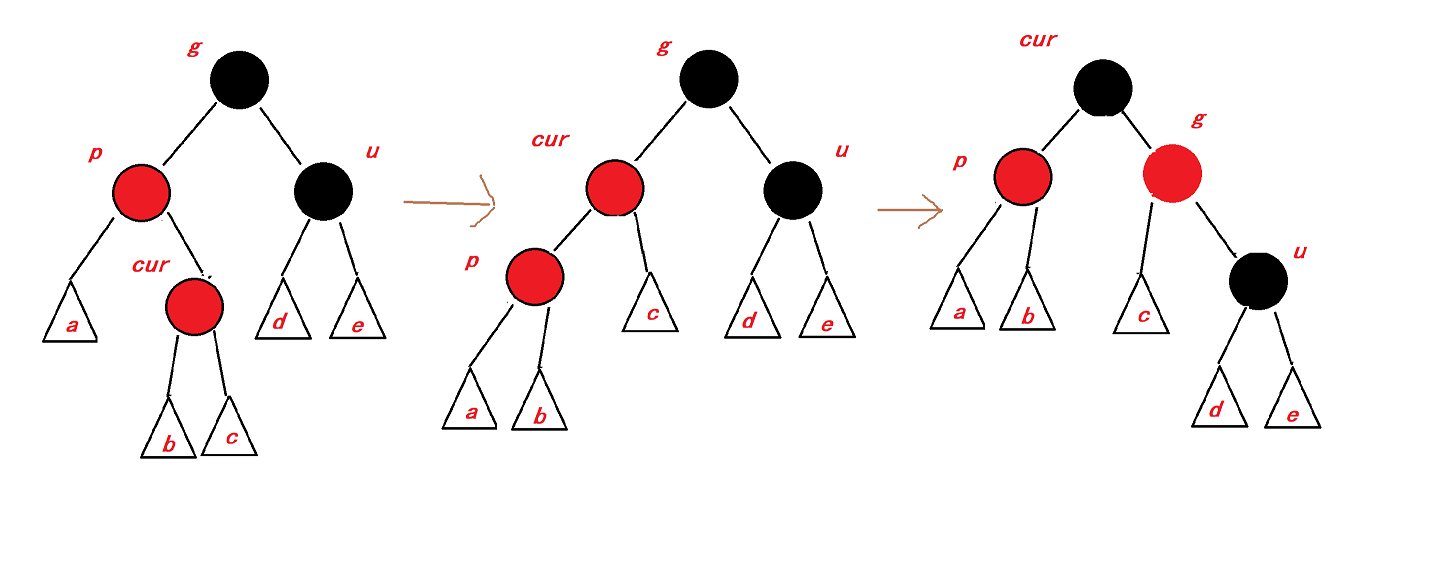
本实验的网络拓扑图如下所示:

Task 1: Launching ICMP Redirect Attack
- 在Victim主机上查看路由表,结果如下:

2.在Victim上Ping 192.168.60.60.5,结果如下:

3.在Attkaker主机上创建redirect_attack.py文件,
内容如下:

4.接下来查看traceroute,这里的结果要和攻击后的结果进行对比,所以先记录下来:
在Victim主机执行mtr -n 192.168.60.5 命令,这是攻击之前的结果

5.在Victim主机上先查看ip route cache,确保没有记录,然后ping 192.168.60/24
子网:

6.Attacker主机开始攻击:

7.等待Attacker主机发送成功1秒后,Victim主机已经接收到重定向的数据包后,不要停止ping 192.168.60.5。然后查看ip route,
结果如下:

发现路由表没有变化,接入192.168.60.0/24子网还是通过10.9.0.11,而不是10.9.0.111。
再查看ip route cache:

可以看到,ip route cache 里已经有了这一项。
8.在Victim主机执行mtr -n 192.168.60.5 命令,这是攻击之后的结果:

发现,经过攻击后,tracetoute确实多了一项10.9.0.111,说明攻击成功。
针对实验手册中提出的问题,我们回答如下:
• Question 1: Can you use ICMP redirect attacks to redirect to a remote machine? Namely, the IP address assigned to icmp.gw is a computer not on the local LAN. Please show your experiment result, and explain your observation.
修改文件内容为:

重复上述操作,最后查看结果:

说明不可以是外网。
• Question 2: Can you use ICMP redirect attacks to redirect to a non-existing machine on the same network? Namely, the IP address assigned to icmp.gw is a local computer that is either offlfline or non-existing. Please show your experiment result, and explain your observation.
修改文件内容为:

重复上述操作,查看结果为:

说明不可以是不存在的地址。
• Question 3: If you look at the docker-compose.yml fifile, you will fifind the following entries for the malicious router container. What are the purposes of these entries? Please change their value to 1, and launch the attack again. Please describe and explain your observation.
关闭路由转发的意思
修改系统参数:

重复上述步骤。结果为:

说明不可以将参数改变为1。
综上所述,通过执行以上操作,我们完成了Launching ICMP Redirect Attack任务。
Task 2: Launching the MITM Attack
攻击前的准备:
改写配置文件:

在192.168.60.5主机上使用netcat开启监听服务:

攻击流程
- 在Victim主机上查看traceroute,正常如下:

在恶意路由器(10.9.0.111)上编写数据包篡改程序,因为ip route cache会过期,所以需要重复进行上个实验中的攻击步骤。先在Victim(10.9.0.5)机器上ping 192.168.60.5机器。
在Attacker(10.9.0.105)上执行redirect_attack.py:

5.此时Victim机器的ip route cache已经重新拥有10.9.0.111条目
:

6.开始在恶意路由器上进行攻击,在恶意路由器上执行mitm_sample.py程序,开始等待数据包:

7.在Victim(10.9.0.5)上执行nc 192.168.60.5 9090进行连接并发送一些带有name缩写的字符串。
8.在192.168.60.5机器上看到name被替换了:

同时在恶意路由器上也可以看到响应的数据包:

针对实验手册中提出的问题,我们回答如下:
After you have succeeded in the attack, please answer the following questions:
• Question 4: In your MITM program, you only need to capture the traffifics in one direction. Please indicate which direction, and explain why.
Victim->192.168.60.5
只需要使victim往外发的消息被我们获取及改写就可以了。
• Question 5: In the MITM program, when you capture the nc traffifics from A (10.9.0.5), you can use A’s IP address or MAC address in the fifilter. One of the choices is not good and is going to create issues, even though both choices may work. Please try both, and use your experiment results to show which choice is the correct one, and please explain your conclusion.
经过尝试,发现IP地址更好一些。
猜测是因为IP地址相比MAC地址更上层一些。
综上所述,通过执行以上操作,我们完成了Launching the MITM Attack任务。