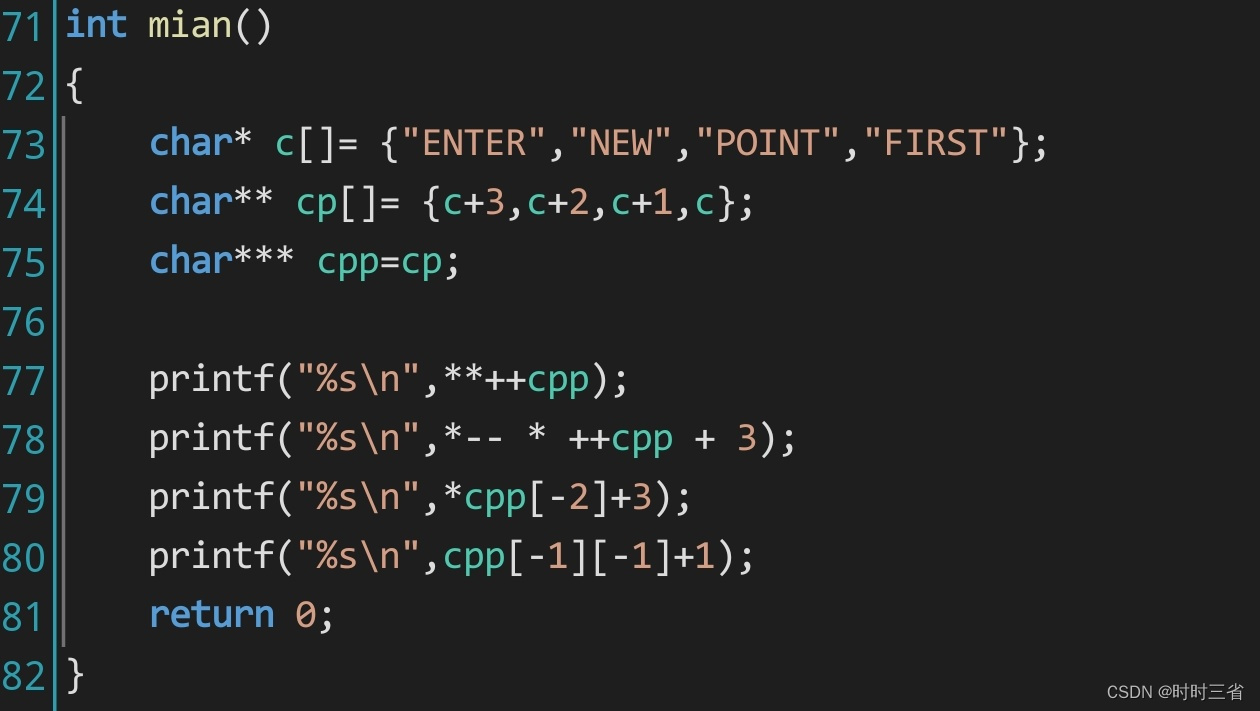
题目来源:各种绕过哟 - Bugku CTF
访问页面,得到代码如下:
<?php
highlight_file('flag.php');
$_GET['id'] = urldecode($_GET['id']);
$flag = 'flag{xxxxxxxxxxxxxxxxxx}';
if (isset($_GET['uname']) and isset($_POST['passwd'])) {
if ($_GET['uname'] == $_POST['passwd'])
print 'passwd can not be uname.';
else if (sha1($_GET['uname']) === sha1($_POST['passwd'])&($_GET['id']=='margin'))
die('Flag: '.$flag);
else
print 'sorry!';
}
?>sha1、md5 都能通过数组绕过;
最后构造payload ,bp要加个头部 Content-Type: application/x-www-form-urlencoded

得到flag