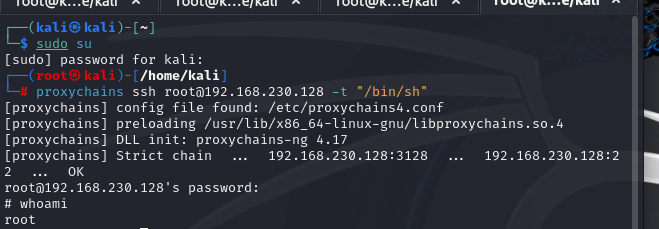
看反汇编
; __unwind {
.text:0000000000001514 F3 0F 1E FA endbr64
.text:0000000000001518 55 push rbp
.text:0000000000001519 48 89 E5 mov rbp, rsp
.text:000000000000151C 53 push rbx
.text:000000000000151D 48 83 EC 68 sub rsp, 68h
.text:0000000000001521 89 7D 9C mov [rbp+var_64], edi
.text:0000000000001524 48 89 75 90 mov [rbp+var_70], rsi
.text:0000000000001528 64 48 8B 04 25 28 00 00 00 mov rax, fs:28h
.text:0000000000001531 48 89 45 E8 mov [rbp+var_18], rax
.text:0000000000001535 31 C0 xor eax, eax
.text:0000000000001537 48 8D 3D CD 0A 00 00 lea rdi, name ; "_"
.text:000000000000153E E8 AD FB FF FF call _getenv
.text:000000000000153E
.text:0000000000001543 48 89 45 A8 mov [rbp+var_58], rax
.text:0000000000001547 48 8B 45 90 mov rax, [rbp+var_70]
.text:000000000000154B 48 8B 00 mov rax, [rax]
.text:000000000000154E 48 89 45 B0 mov [rbp+ptr], rax
.text:0000000000001552 48 8B 45 B0 mov rax, [rbp+ptr]
.text:0000000000001556 48 3B 45 A8 cmp rax, [rbp+var_58]
.text:000000000000155A 75 0A jnz short loc_1566
.text:000000000000155A
.text:000000000000155C BF FF FF FF FF mov edi, 0FFFFFFFFh ; status
.text:0000000000001561 E8 2A FC FF FF call _exit
.text:0000000000001561
.text:0000000000001566 ; ---------------------------------------------------------------------------
.text:0000000000001566
.text:0000000000001566 loc_1566: ; CODE XREF: main+46↑j
.text:0000000000001566 BF 08 00 00 00 mov edi, 8 ; size
.text:000000000000156B E8 F0 FB FF FF call _malloc
.text:000000000000156B
.text:0000000000001570 48 89 45 B8 mov [rbp+dest], rax
.text:0000000000001574 48 8B 45 B0 mov rax, [rbp+ptr]
.text:0000000000001578 48 89 C7 mov rdi, rax
.text:000000000000157B E8 B4 FD FF FF call sub_1334
.text:000000000000157B
.text:0000000000001580 48 89 C1 mov rcx, rax
.text:0000000000001583 48 8B 45 B8 mov rax, [rbp+dest]
.text:0000000000001587 BA 08 00 00 00 mov edx, 8 ; n
.text:000000000000158C 48 89 CE mov rsi, rcx ; src
.text:000000000000158F 48 89 C7 mov rdi, rax ; dest
.text:0000000000001592 E8 79 FB FF FF call _strncpy
.text:0000000000001592
.text:0000000000001597 48 B8 51 17 53 43 54 46 7B 77 mov rax, 777B465443531751h
.text:00000000000015A1 48 BA 75 64 33 5F 30 6E 40 2C mov rdx, 2C406E305F336475h
.text:00000000000015AB 48 89 45 D0 mov qword ptr [rbp+src], rax
.text:00000000000015AF 48 89 55 D8 mov qword ptr [rbp+var_28], rdx
.text:00000000000015B3 C7 45 E0 33 34 70 7D mov dword ptr [rbp+var_28+8], 7D703433h
.text:00000000000015BA C6 45 E4 00 mov [rbp+var_28+0Ch], 0
.text:00000000000015BE B8 14 00 00 00 mov eax, 14h
.text:00000000000015C3 48 98 cdqe
.text:00000000000015C5 48 89 C7 mov rdi, rax ; size
.text:00000000000015C8 E8 93 FB FF FF call _malloc
.text:00000000000015C8
.text:00000000000015CD 48 89 45 C0 mov [rbp+var_40], rax
.text:00000000000015D1 B8 14 00 00 00 mov eax, 14h
.text:00000000000015D6 48 63 D0 movsxd rdx, eax ; n
.text:00000000000015D9 48 8D 4D D0 lea rcx, [rbp+src]
.text:00000000000015DD 48 8B 45 C0 mov rax, [rbp+var_40]
.text:00000000000015E1 48 89 CE mov rsi, rcx ; src
.text:00000000000015E4 48 89 C7 mov rdi, rax ; dest
.text:00000000000015E7 E8 24 FB FF FF call _strncpy
.text:00000000000015E7
.text:00000000000015EC 48 8B 45 C0 mov rax, [rbp+var_40]
.text:00000000000015F0 48 89 C7 mov rdi, rax
.text:00000000000015F3 E8 C1 FD FF FF call sub_13B9
.text:00000000000015F3
.text:00000000000015F8 B8 14 00 00 00 mov eax, 14h
.text:00000000000015FD 48 98 cdqe
.text:00000000000015FF 48 89 C7 mov rdi, rax ; size
.text:0000000000001602 E8 59 FB FF FF call _malloc
.text:0000000000001602
.text:0000000000001607 48 89 45 C8 mov [rbp+var_38], rax
.text:000000000000160B B8 14 00 00 00 mov eax, 14h
.text:0000000000001610 48 63 D8 movsxd rbx, eax
.text:0000000000001613 48 8B 55 B8 mov rdx, [rbp+dest]
.text:0000000000001617 48 8D 45 D0 lea rax, [rbp+src]
.text:000000000000161B 48 89 D6 mov rsi, rdx
.text:000000000000161E 48 89 C7 mov rdi, rax
.text:0000000000001621 E8 63 FC FF FF call sub_1289
.text:0000000000001621
.text:0000000000001626 48 89 C1 mov rcx, rax
.text:0000000000001629 48 8B 45 C8 mov rax, [rbp+var_38]
.text:000000000000162D 48 89 DA mov rdx, rbx ; n
.text:0000000000001630 48 89 CE mov rsi, rcx ; src
.text:0000000000001633 48 89 C7 mov rdi, rax ; dest
.text:0000000000001636 E8 D5 FA FF FF call _strncpy
.text:0000000000001636
.text:000000000000163B 48 8B 55 B8 mov rdx, [rbp+dest]
.text:000000000000163F 48 8B 45 C8 mov rax, [rbp+var_38]
.text:0000000000001643 48 89 D6 mov rsi, rdx
.text:0000000000001646 48 89 C7 mov rdi, rax
.text:0000000000001649 E8 3B FC FF FF call sub_1289
.text:0000000000001649
.text:000000000000164E 48 89 45 C8 mov [rbp+var_38], rax
.text:0000000000001652 48 8B 45 C8 mov rax, [rbp+var_38]
.text:0000000000001656 48 89 C7 mov rdi, rax
.text:0000000000001659 E8 4D FE FF FF call sub_14AB
.text:0000000000001659
.text:000000000000165E 48 8B 45 C0 mov rax, [rbp+var_40]
.text:0000000000001662 48 89 C7 mov rdi, rax ; ptr
.text:0000000000001665 E8 96 FA FF FF call _free
.text:0000000000001665
.text:000000000000166A 48 8B 45 C8 mov rax, [rbp+var_38]
.text:000000000000166E 48 89 C7 mov rdi, rax ; ptr
.text:0000000000001671 E8 8A FA FF FF call _free
.text:0000000000001671
.text:0000000000001676 48 8B 45 B0 mov rax, [rbp+ptr]
.text:000000000000167A 48 89 C7 mov rdi, rax ; ptr
.text:000000000000167D E8 7E FA FF FF call _free
.text:000000000000167D
.text:0000000000001682 B8 00 00 00 00 mov eax, 0
.text:0000000000001687 48 8B 5D E8 mov rbx, [rbp+var_18]
.text:000000000000168B 64 48 33 1C 25 28 00 00 00 xor rbx, fs:28h
.text:0000000000001694 74 05 jz short loc_169B
.text:0000000000001694
.text:0000000000001696 E8 B5 FA FF FF call ___stack_chk_fail发现74 0A jz short loc_1566时就exit 退出函数了,所以不让退出,直接跳过,用pwn中的set更改rip的值,再看反编译的程序发现有三个free应该结果输出。
gdb pwn1
用gdb调试

start
开始运行

i b
查看断点
b *$rebase(0x153e)
设置断点。为什么会有$rebase 是应为程序在这里面是随机生成的地址(设置到exit之前即可)
b *$rebase(0x1665)
设置到最后一个free之前

c
跳转到第一个断点处(ni是一样的道理只是ni是单步执行比较慢)

ni
直到ni到但exit处停止(当连续ni时,第二次及以后可以直接enter执行)


set $rip=$rebase(0x1566)
set 是修改命令 把寄存器的地址改成0x1566,跳过exit函数。
p $rip
查看修改后的地址
c
跳转到下一个断点

ni
ni到最后一个free(为什么要运行但最后一个是因为malloc动态内存分配,开起来后面的堆)

heap
查看堆

tel 0x555555559290
从第二个开始(一般第一个不是)
enter 继续查看发现带有flag的字样,复制地址
x/s 0x5555555594e0
详细的查看此地址的内容


![re题(25)BUUFCTF-[GUET-CTF2019]re](https://i-blog.csdnimg.cn/blog_migrate/05437e17bfb1189ab11a35ca9a1731a2.png)