本文为复现篇:
Refer to bugninja’s Write Up.
Host: venus.hackmyvm.eu
Port: 5000
User: hacker
Pass: havefun!
Flags 01
readme.txt
# EN
Hello hax0r,
Welcome to the HMVLab Chapter 1: Venus!
This is a CTF for beginners where you can practice your skills with Linux and CTF
so lets start! :)
First of all, the home of each user is in /pwned/USER and in it you will find a file called mission.txt which will contain
the mission to complete to get the password of the next user.
It will also contain the flagz.txt file, which if you are registered at https://hackmyvm.eu you can enter to participate in the ranking (optional).
And for a bit of improvisation, there are secret levels and hidden flags: D
You will not have write permissions in most folders so if you need to write a script or something
use /tmp folder, keep in mind that it is frequently deleted ...
And last (and not least) some users can modify the files that are in the
folder /www, these files are accessible from http://venus.hackmyvm.eu so if you get a user
that can modify the file /www/hi.txt, you can put a message and it will be reflected in http://venus.hackmyvm.eu/hi.txt.
If you have questions/ideas or want to comment us anything you can join
to our Discord: https://discord.gg/DxDFQrJ
Remember there are more people playing so be respectful.
Hack & Fun!
# ES
Hola hax0r,
Bienvenid@ al HMVLab Chapter 1: Venus!
Este es un CTF para principiantes donde podras practicar tus habilidades con Linux y los CTF
asi que vamos a trastear un poco! :)
Antes de nada, el home de cada usuario se encuentra en /pwned/USUARIO y en el encontraras un fichero llamado mission.txt el cual contendra
la mision a completar para conseguir la password del siguiente usuario.
Tambien contendra el fichero flagz.txt, que si estas registrado en https://hackmyvm.eu podras introducir para participar en el ranking (opcional).
Y para que haya un poco de improvisacion, hay niveles secretos y flags escondidas :D
No tendras permisos de escritura en la mayoria de carpetas asi que si necesitas escribir algun script o algo
usa la carpeta /tmp, ten en cuenta que es eliminada de manera frecuente...
Y por ultimo (y no menos importante) algunos usuarios pueden modificar los ficheros que estan en la
carpeta /www, estos ficheros son accesibles desde http://venus.hackmyvm.eu asi que si consigues un usuario
que pueda modificar el fichero /www/hi.txt, podras poner un mensaje y se verá reflejado en http://venus.hackmyvm.eu/hi.txt.
Si tienes dudas/ideas o quieres comentar cualquier cosa puedes unirte
a nuestro Discord: https://discord.gg/DxDFQrJ
Recuerda que hay mas gente jugando asi que se respetuoso.
Hack & Fun!
mission.txt
################
# MISSION 0x01 #
################
## EN ##
User sophia has saved her password in a hidden file in this folder. Find it and log in as sophia.
## ES ##
La usuaria sophia ha guardado su contraseña en un fichero oculto en esta carpeta.Encuentralo y logueate como sophia.
hacker@venus:~$ ls -la
total 36
drwxr-x--- 2 root hacker 4096 Apr 7 2022 .
drwxr-xr-x 55 root root 4096 Apr 7 2022 ..
-rw-r----- 1 root hacker 31 Apr 7 2022 ...
-rw-r--r-- 1 hacker hacker 220 Aug 4 2021 .bash_logout
-rw-r--r-- 1 hacker hacker 3526 Aug 4 2021 .bashrc
-rw-r----- 1 root hacker 16 Apr 7 2022 .myhiddenpazz
-rw-r--r-- 1 hacker hacker 807 Aug 4 2021 .profile
-rw-r----- 1 root hacker 287 Apr 7 2022 mission.txt
-rw-r----- 1 root hacker 2542 Apr 7 2022 readme.txt
hacker@venus:~$ cat .myhiddenpazz
Y1o645M3mR84ejc
hacker@venus:~$
hacker@venus:~$ cat .myhiddenpazz
Y1o645M3mR84ejc
hacker@venus:~$ su sophia
sophia@venus:/pwned/hacker$ cd ~
sophia@venus:~$ ls
flagz.txt mission.txt
sophia@venus:~$ cat flagz.txt
8===LUzzNuv8NB59iztWUIQS===D~~
sophia@venus:~$
Flags 02
mission.txt
################
# MISSION 0x02 #
################
## EN ##
The user angela has saved her password in a file but she does not remember where ... she only remembers that the file was called whereismypazz.txt
## ES ##
La usuaria angela ha guardado su password en un fichero pero no recuerda donde... solo recuerda que el fichero se llamaba whereismypazz.txt
sophia@venus:~$ find / -name "whereismypazz.txt" 2>/dev/null
/usr/share/whereismypazz.txt
sophia@venus:~$ cat /usr/share/whereismypazz.txt
oh5p9gAABugHBje
sophia@venus:~$
sophia@venus:~$ su angela
Password:
angela@venus:/pwned/sophia$ cd ~
angela@venus:~$ ls
findme.txt flagz.txt mission.txt
angela@venus:~$ cat flagz.txt
8===SjMYBmMh4bk49TKq7PM8===D~~
angela@venus:~$
Flags 03
mission.txt
################
# MISSION 0x03 #
################
## EN ##
The password of the user emma is in line 4069 of the file findme.txt
## ES ##
La password de la usuaria emma esta en la linea 4069 del fichero findme.txt

fIvltaGaq0OUH8O
angela@venus:~$ su emma
Password:
emma@venus:/pwned/angela$ cd ~
emma@venus:~$ ls
- flagz.txt mission.txt
emma@venus:~$ cat flagz.txt
8===0daqdDlmd9XogkiHu4yq===D~~
emma@venus:~$
Flags 04
missions.txt
################
# MISSION 0x04 #
################
## EN ##
User mia has left her password in the file -.
## ES ##
La usuaria mia ha dejado su password en el fichero -.
emma@venus:~$ ls
- flagz.txt mission.txt
emma@venus:~$ cat ./-
iKXIYg0pyEH2Hos
emma@venus:~$ su mia
Password:
mia@venus:/pwned/emma$ cd ~
mia@venus:~$ ls
flagz.txt mission.txt
mia@venus:~$ cat flagz.txt
8===FBMdY8hel2VMA3BaYJin===D~~
mia@venus:~$
Flags 05
missions.txt
################
# MISSION 0x05 #
################
## EN ##
It seems that the user camila has left her password inside a folder called hereiam
## ES ##
Parece que la usuaria camila ha dejado su password dentro de una carpeta llamada hereiam
mia@venus:~$ find / -name "hereiam" 2>/dev/null
/opt/hereiam
mia@venus:~$ cd /opt/hereiam/
mia@venus:/opt/hereiam$ ls
mia@venus:/opt/hereiam$ ls -la
total 12
drwxr-xr-x 2 root root 4096 Apr 7 2022 .
drwxr-xr-x 1 root root 4096 Apr 7 2022 ..
-rw-r--r-- 1 root root 16 Apr 7 2022 .here
mia@venus:/opt/hereiam$ cat .here
F67aDmCAAgOOaOc
mia@venus:/opt/hereiam$ su camila
Password:
camila@venus:/opt/hereiam$ cd ~
camila@venus:~$ ls
flagz.txt mission.txt muack
camila@venus:~$ cat flagz.txt
8===iDIi5sm1mDuqGmU5Psx6===D~~
camila@venus:~$
Flags 06
################
# MISSION 0x06 #
################
## EN ##
The user luna has left her password in a file inside the muack folder.
## ES ##
La usuaria luna ha dejado su password en algun fichero dentro de la carpeta muack.
camila@venus:~$ find ./muack/ -type f
./muack/111/111/muack
camila@venus:~$ cat ./muack/111/111/muack
j3vkuoKQwvbhkMc
camila@venus:~$ su luna
Password:
luna@venus:/pwned/camila$ cd ~
luna@venus:~$ ls
flagz.txt mission.txt
luna@venus:~$ cat flagz.txt
8===KCO34FpIq3nBmHbyZvFh===D~~
luna@venus:~$
Flags 07
missions.txt
################
# MISSION 0x07 #
################
## EN ##
The user eleanor has left her password in a file that occupies 6969 bytes.
## ES ##
La usuaria eleanor ha dejado su password en un fichero que ocupa 6969 bytes.
luna@venus:~$ find / -size 6969c 2>/dev/null
/usr/share/man/man1/h2xs.1.gz
/usr/share/moon.txt
luna@venus:~$ cat /usr/share/moon.txt
UNDchvln6Bmtu7b
luna@venus:~$ su eleanor
Password:
eleanor@venus:/pwned/luna$ cd ~
eleanor@venus:~$ ls
flagz.txt mission.txt
eleanor@venus:~$ cat flagz.txt
8===Iq5vbyiQl4ipNrLDArjD===D~~
eleanor@venus:~$
Flags 08
missions.txt
################
# MISSION 0x08 #
################
## EN ##
The user victoria has left her password in a file in which the owner is the user violin.
## ES ##
La usuaria victoria ha dejado su password en un fichero en el cual el propietario es el usuario violin.
eleanor@venus:~$ find / -user violin 2>/dev/null
/usr/local/games/yo
eleanor@venus:~$ cat /usr/local/games/yo
pz8OqvJBFxH0cSj
eleanor@venus:~$ su victoria
Password:
victoria@venus:/pwned/eleanor$ cd ~
victoria@venus:~$ ls
flagz.txt mission.txt passw0rd.zip
victoria@venus:~$ cat flagz.txt
8===NWyTFi9LLqVsZ4OnuZYN===D~~
victoria@venus:~$
Flags 09
missions.txt
################
# MISSION 0x09 #
################
## EN ##
The user isla has left her password in a zip file.
## ES ##
La usuaria isla ha dejado su password en un fichero zip.
victoria@venus:~$ mkdir /tmp/1/
victoria@venus:~$ ls
flagz.txt mission.txt passw0rd.zip
victoria@venus:~$ cp passw0rd.zip /tmp/1/
victoria@venus:~$ cd /tmp/1/
victoria@venus:/tmp/1$ unzip passw0rd.zip
Archive: passw0rd.zip
extracting: pwned/victoria/passw0rd.txt
victoria@venus:/tmp/1$ ls
passw0rd.zip pwned
victoria@venus:/tmp/1$ cd pwned/victoria/
victoria@venus:/tmp/1/pwned/victoria$ ls
passw0rd.txt
victoria@venus:/tmp/1/pwned/victoria$ cat passw0rd.txt
D3XTob0FUImsoBb
victoria@venus:/tmp/1/pwned/victoria$ su isla
Password:
isla@venus:/tmp/1/pwned/victoria$ cd ~
isla@venus:~$ ls
flagz.txt mission.txt passy
isla@venus:~$ cat flagz.txt
8===ZyZqc1suvGe4QlkZHFlq===D~~
isla@venus:~$
Flags 10
missions.txt
################
# MISSION 0x10 #
################
## EN ##
The password of the user violet is in the line that begins with a9HFX (these 5 characters are not part of her password.).
## ES ##
El password de la usuaria violet esta en la linea que empieza por a9HFX (sin ser estos 5 caracteres parte de su password.).
注 a9HFX 题干说不包含在 password 内
isla@venus:~$ cat passy | grep ^a9HFX
a9HFXWKINVzNQLKLDVAc
isla@venus:~$ su violet
Password:
violet@venus:/pwned/isla$ cd ~
violet@venus:~$ ls
end flagz.txt mission.txt
violet@venus:~$ cat flagz.txt
8===LzErk0qFPYJj16mNnnYZ===D~~
violet@venus:~$
Flags 11
missions.txt
################
# MISSION 0x11 #
################
## EN ##
The password of the user lucy is in the line that ends with 0JuAZ (these last 5 characters are not part of her password)
## ES ##
El password de la usuaria lucy se encuentra en la linea que acaba por 0JuAZ (sin ser estos ultimos 5 caracteres parte de su password)
注 0JuAZ 题干说不包含在 password 内
violet@venus:~$ cat end | grep 0JuAZ$
OCmMUjebG53giud0JuAZ
violet@venus:~$ ls
end flagz.txt mission.txt
violet@venus:~$ su lucy
Password:
lucy@venus:/pwned/violet$ cd ~
lucy@venus:~$ ls
file.yo flagz.txt mission.txt
lucy@venus:~$ cat flagz.txt
8===AdCJ4wl8pmbhi770Xbd3===D~~
lucy@venus:~$
Flags 12
missions.txt
################
# MISSION 0x12 #
################
## EN ##
The password of the user elena is between the characters fu and ck
## ES ##
El password de la usuaria elena esta entre los caracteres fu y ck
lucy@venus:~$ cat file.yo | grep ^fu.*ck$
fu4xZ5lIKYmfPLg9tck
lucy@venus:~$ su elena
Password:
elena@venus:/pwned/lucy$ cd ~
elena@venus:~$ ls
flagz.txt mission.txt
elena@venus:~$ cat flagz.txt
8===st1pTdqEQ0bvrJfWGwLA===D~~
elena@venus:~$
Flags 13
missions.txt
################
# MISSION 0x13 #
################
## EN ##
The user alice has her password is in an environment variable.
## ES ##
La password de alice esta en una variable de entorno.
elena@venus:~$ printenv | grep PASS
PASS=Cgecy2MY2MWbaqt
elena@venus:~$ su alice
Password:
alice@venus:/pwned/elena$ cd ~
alice@venus:~$ ls
flagz.txt mission.txt
alice@venus:~$ cat flagz.txt
8===Qj4NNWp8LOC96S9Rtgrk===D~~
alice@venus:~$
Flags 14
missions.txt
################
# MISSION 0x14 #
################
## EN ##
The admin has left the password of the user anna as a comment in the file passwd.
## ES ##
El admin ha dejado la password de anna como comentario en el fichero passwd.
alice@venus:~$ cat /etc/passwd | grep anna
anna:x:1015:1015::/pwned/anna:/bin/bash
alice@venus:~$ cat /etc/passwd | grep alice
alice:x:1014:1014:w8NvY27qkpdePox:/pwned/alice:/bin/bash
alice@venus:~$ su anna
Password:
anna@venus:/pwned/alice$ cd ~
anna@venus:~$ ls
flagz.txt mission.txt
anna@venus:~$ cat flagz.txt
8===5Y3DhT66fa6Da8RpLKG0===D~~
anna@venus:~$
Flags 15
missions.txt
################
# MISSION 0x15 #
################
## EN ##
Maybe sudo can help you to be natalia.
## ES ##
Puede que sudo te ayude para ser natalia.
anna@venus:~$ sudo -u natalia /bin/bash
natalia@venus:/pwned/anna$ cd ~
natalia@venus:~$ ls
base64.txt flagz.txt mission.txt nataliapass.txt
natalia@venus:~$ cat flagz.txt
8===JWHa1GQq1AYrBWNXEJrH===D~~
natalia@venus:~$
Flags 16
missions.txt
################
# MISSION 0x16 #
################
## EN ##
The password of user eva is encoded in the base64.txt file
## ES ##
El password de eva esta encodeado en el fichero base64.txt
cat base64.txt
dXBzQ0EzVUZ1MTBmREFPCg==
Encode : dXBzQ0EzVUZ1MTBmREFPCg==
Decode : upsCA3UFu10fDAO
natalia@venus:~$ su eva
Password:
eva@venus:/pwned/natalia$ cd ~
eva@venus:~$ ls
flagz.txt mission.txt
eva@venus:~$ cat flagz.txt
8===22cqk3iGkGYVqnYrHiof===D~~
eva@venus:~$
Flags 17
missions.txt
################
# MISSION 0x17 #
################
## EN ##
The password of the clara user is found in a file modified on May 1, 1968.
## ES ##
La password de la usuaria clara se encuentra en un fichero modificado el 01 de Mayo de 1968.
eva@venus:~$ find / -type f ! -newermt 1970-01-02 -ls 2>/dev/null
403708 4 -rw-r--r-- 1 root root 16 Jan 1 1970 /usr/lib/cmdo
eva@venus:~$ cat /usr/lib/cmdo
39YziWp5gSvgQN9
eva@venus:~$ su clara
Password:
clara@venus:/pwned/hacker$ cd ~
clara@venus:~$ ls
flagz.txt mission.txt protected.zip
clara@venus:~$ cat flagz.txt
8===EJWmHDEQeEN1vIR7NYiH===D~~
clara@venus:~$
Flags 18
missions.txt
################
# MISSION 0x18 #
################
## EN ##
The password of user frida is in the password-protected zip (rockyou.txt can help you)
## ES ##
La password de frida esta en el zip protegido con password.(rockyou.txt puede ayudarte)
└─$ sftp -P 5000 clara@venus.hackmyvm.eu
└─$ 39YziWp5gSvgQN9
clara@venus.hackmyvm.eu's password:
Connected to venus.hackmyvm.eu.
sftp> ls
flagz.txt mission.txt protected.zip
sftp> get protected.zip
Fetching /pwned/clara/protected.zip to protected.zip
/pwned/clara/protected.zip 100% 244 0.6KB/s 00:00
JohnTheRipper
└─$ zip2john protected.zip > hash.txt
└─$ john --format=PKZIP --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
pass123 (protected.zip/pwned/clara/protected.txt)
1g 0:00:00:00 DONE (2022-11-20 12:46) 100.0g/s 819200p/s 819200c/s 819200C/s 123456..whitetiger
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
└─$ unzip protected.zip
Archive: protected.zip
[protected.zip] pwned/clara/protected.txt password:
replace pwned/clara/protected.txt? [y]es, [n]o, [A]ll, [N]one, [r]ename: yes
extracting: pwned/clara/protected.txt
└─$ cd pwned/clara
└─$ cat protected.txt
Ed4ErEUJEaMcXli
clara@venus:~$ su frida
Password:
frida@venus:/pwned/clara$ cd ~
frida@venus:~$ cat flagz.txt
8===Ikg2qj8KT2bGJtWvR6hC===D~~
frida@venus:~$
Flags 19
missions.txt
################
# MISSION 0x19 #
################
## EN ##
The password of eliza is the only string that is repeated (unsorted) in repeated.txt.
## ES ##
La password de eliza es el unico string que se repite (sin estar ordenado) en repeated.txt.
frida@venus:~$ uniq -d repeated.txt
Fg6b6aoksceQqB9
frida@venus:~$ su eliza
Password:
eliza@venus:/pwned/frida$ cd ~
eliza@venus:~$ ls
flagz.txt mission.txt
eliza@venus:~$ cat flagz.txt
8===zwWIPyDf2ozwVhCTxm1I===D~~
eliza@venus:~$
uniq -d testfile 删重
Flags 20
missions.txt
################
# MISSION 0x20 #
################
## EN ##
The user iris has left me her key.
## ES ##
La usuaria iris me ha dejado su key.
eliza@venus:~$ ls -a
. .. .bash_logout .bashrc .iris_key .profile flagz.txt mission.txt
eliza@venus:~$ ls -la
total 36
drwxr-x--- 2 root eliza 4096 Apr 7 2022 .
drwxr-xr-x 1 root root 4096 Apr 7 2022 ..
-rw-r--r-- 1 eliza eliza 220 Aug 4 2021 .bash_logout
-rw-r--r-- 1 eliza eliza 3526 Aug 4 2021 .bashrc
-rw-r----- 1 root eliza 2602 Apr 7 2022 .iris_key
-rw-r--r-- 1 eliza eliza 807 Aug 4 2021 .profile
-rw-r----- 1 root eliza 31 Apr 7 2022 flagz.txt
-rw-r----- 1 root eliza 143 Apr 7 2022 mission.txt
eliza@venus:~$
[-i identity_file]
eliza@venus:~$ ssh -i .iris_key iris@localhost
The authenticity of host 'localhost (127.0.0.1)' can't be established.
ECDSA key fingerprint is SHA256:ARNXOhO4Aisq1Dv96z2ZNk96a8qycr+JIljSMY+JBe8.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
iris@venus:~$ ls
eloise flagz.txt irispass.txt mission.txt
iris@venus:~$ cat flagz.txt
8===ClrdWOqlZ1vL61zSk9Va===D~~
iris@venus:~$
Flags 21
missions.txt
################
# MISSION 0x21 #
################
## EN ##
User eloise has saved her password in a particular way.
## ES ##
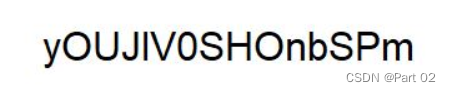
La usuaria eloise ha guardado su password de una forma particular.
iris@venus:~$ cat eloise
/9j/4AAQSkZJRgABAQEAYABgA......CiiigAooooAKKKKAP/9k=
方法一:
└─$ cat eloise | base64 -d > eloise.pdf
方法二:
CTF 常见的 base64 转图
https://tool.jisuapi.com/base642pic.html
yOUJlV0SHOnbSPm
iris@venus:~$ su eloise
Password:
eloise@venus:/pwned/iris$ cd ~
eloise@venus:~$ ls
flagz.txt hi mission.txt
eloise@venus:~$ cat flagz.txt
8===57CzBLKaEq2N8YBFRu31===D~~
eloise@venus:~$
Flags 22
missions.txt
################
# MISSION 0x22 #
################
## EN ##
User lucia has been creative in saving her password.
## ES ##
La usuaria lucia ha sido creativa en la forma de guardar su password.
CTF 中分析文件时,经常会看到这样的 16 进制
eloise@venus:~$ cat hi
00000000: 7576 4d77 4644 5172 5157 504d 6547 500a
eloise@venus:~$ cat hi | xxd -r
uvMwFDQrQWPMeGP
eloise@venus:~$ su lucia
Password:
lucia@venus:/pwned/eloise$ cd ~
lucia@venus:~$ ls
dict.txt flagz.txt mission.txt
lucia@venus:~$ cat flagz.txt
8===5Sr2pqeVTmn8RaaPmTPE===D~~
lucia@venus:~$
Flags 23
missions.txt
################
# MISSION 0x23 #
################
## EN ##
The user isabel has left her password in a file in the /etc/xdg folder but she does not remember the name, however she has dict.txt that can help her to remember.
## ES ##
La usuaria isabel ha dejado su password en un fichero en la carpeta /etc/xdg pero no recuerda el nombre, sin embargo tiene dict.txt que puede ayudarle a recordar.
lucia@venus:~$ while IFS= read -r line; do cat /etc/xdg/$line; done < dict.txt 2>/dev/null
H5ol8Z2mrRsorC0
lucia@venus:~$ su isabel
Password:
isabel@venus:/pwned/lucia$ cd ~
isabel@venus:~$ ls
different.txt flagz.txt mission.txt
isabel@venus:~$ cat flagz.txt
8===Md2CU83GtVfouhm9U0AS===D~~
isabel@venus:~$
Flags 24
missions.txt
################
# MISSION 0x24 #
################
## EN ##
The password of the user freya is the only string that is not repeated in different.txt
## ES ##
La password de la usuaria freya es el unico string que no se repite en different.txt
isabel@venus:~$ uniq -u different.txt
EEDyYFDwYsmYawj
isabel@venus:~$ su freya
Password:
freya@venus:/pwned/isabel$ cd ~
freya@venus:~$ cat flagz.txt
8===m1rRSv2pdm3sBGmgidul===D~~
freya@venus:~$
1-24 方法综合
1.User sophia has saved her password in a hidden file in this folder. Find it and log in as sophia.
> ls -la
2.The user angela has saved her password in a file but she does not remember where ... she only remembers that the file was called whereismypazz.txt
> find / -name "whereismypazz.txt" 2>/dev/null
3.The password of the user emma is in line 4069 of the file findme.txt
> vim findme.txt
4.User mia has left her password in the file -.
> cat ./-
5.It seems that the user camila has left her password inside a folder called hereiam
> find / -name "hereiam" 2>/dev/null
6.The user luna has left her password in a file inside the muack folder.
> find ./muack/ -type f
7.The user eleanor has left her password in a file that occupies 6969 bytes.
> find / -size 6969c 2>/dev/null
8.The user victoria has left her password in a file in which the owner is the user violin.
> find / -user violin 2>/dev/null
9.The user isla has left her password in a zip file.
> cp passw0rd.zip /tmp/1/
> cd /tmp/1/
> unzip passw0rd.zip
10.The password of the user violet is in the line that begins with a9HFX (these 5 characters are not part of her password.).
> cat passy | grep ^a9HFX
11.The password of the user lucy is in the line that ends with 0JuAZ (these last 5 characters are not part of her password)
> cat end | grep 0JuAZ$
12.The password of the user elena is between the characters fu and ck
> cat file.yo | grep ^fu.*ck$
13.The user alice has her password is in an environment variable.
> printenv | grep PASS
14.The admin has left the password of the user anna as a comment in the file passwd.
> cat /etc/passwd | grep anna
15.Maybe sudo can help you to be natalia.
> sudo -u natalia /bin/bash
16.The password of user eva is encoded in the base64.txt file
> cat base64.txt
dXBzQ0EzVUZ1MTBmREFPCg==
17.The password of the clara user is found in a file modified on May 1, 1968.
> find / -type f ! -newermt 1970-01-02 -ls 2>/dev/null
18.The password of user frida is in the password-protected zip (rockyou.txt can help you)
└─$ sftp -P 5000 clara@venus.hackmyvm.eu
sftp> ls
sftp> get protected.zip
└─$ zip2john protected.zip > hash.txt
└─$ john --format=PKZIP --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
└─$ unzip protected.zip
19.The password of eliza is the only string that is repeated (unsorted) in repeated.txt.
> uniq -d repeated.txt
20.The user iris has left me her key.
> ssh -i .iris_key iris@localhost
21.User eloise has saved her password in a particular way.
> cat eloise | base64 -d > eloise.pdf
22.User lucia has been creative in saving her password.
> cat hi | xxd -r
23.The user isabel has left her password in a file in the /etc/xdg folder but she does not remember the name, however she has dict.txt that can help her to remember.
> while IFS= read -r line; do cat /etc/xdg/$line; done < dict.txt 2>/dev/null
24.The password of the user freya is the only string that is not repeated in different.txt
> uniq -u different.txt

![[附源码]java毕业设计同城搬家平台](https://img-blog.csdnimg.cn/e8236b3b8bd74a6cb5112031ff9cea62.png)


![[Spring Cloud] Open Feign---扩展](https://img-blog.csdnimg.cn/79345d3cbaf7473095deb5898223d78b.png)
![[附源码]java毕业设计汽车租赁管理系统-](https://img-blog.csdnimg.cn/3a16081b544b4578a2252cf6bee4f493.png)
![【数据结构】线性表 _顺序表 链表的增删查改 _[细节分析+代码实现]](https://img-blog.csdnimg.cn/9d8bf5dfdd1c4098832ec49d831e56fd.png)


![[附源码]java毕业设计天悦酒店管理系统](https://img-blog.csdnimg.cn/8329e2c64a8444069383b33da0ec0848.png)