一、搭建高可用OpenStack(Queen版)集群之部署认证服务(Keystone)控制节点集群
一、Identity 服务简介
1、Identity概述
Identity为认证管理,授权管理和服务目录服务管理提供单点整合。其它Openstack服务将身份认证服务当作统一API来使用。
当某个Openstack服务收到来自用户的请求时,该服务会直接询问Identitiy服务,验证该用户是否有权限进行此次请求。
2、keystone各组件概念
- 用户:使用openstack云服务的用户、系统或者服务,身份服务验证用户提交的请求。用户需要登录,然后可能会分配令牌已访问资源。多用户可以直接分配给特定的租户,并且表现的就像他们包含该租户内。
- 认证信息:确认用户身份的数据。比如用户名和密码,用户名和API键,或者身份服务提供的认证令牌
- 认证:确认用户身份的过程。Openstack身份服务通过验证用户提供的认证信息确认请求,当认证信息被验证后,Openstack认证服务发给用户认证令牌,在后续的请求中用户将使用该令牌。
- 令牌:文本形式的字母-数字字符串,使用该字符串访问Openstack的API和资源。令牌在有限的时间内是有效的,可能在任何时间被取消。
- 租户:分组或隔离资源容器,租户也用于分组或隔离身份对象。基于服务操作者,租户可能映射为客户、组织或项目
- 服务:一个openstack服务提供了一个或多个端点,在端点内用户可以访问资源或者执行操作。
- 角色:定义了执行特定操作的用户权限的集合。在身份服务中,发给用户的令牌包括角色的列表。被用户访问的服务确定如何解释用户拥有的角色和每个角色可以访问的操作和资源。
- keystone客户端:openstack身份服务API的命令行接口。
3、Keystone 拓扑图
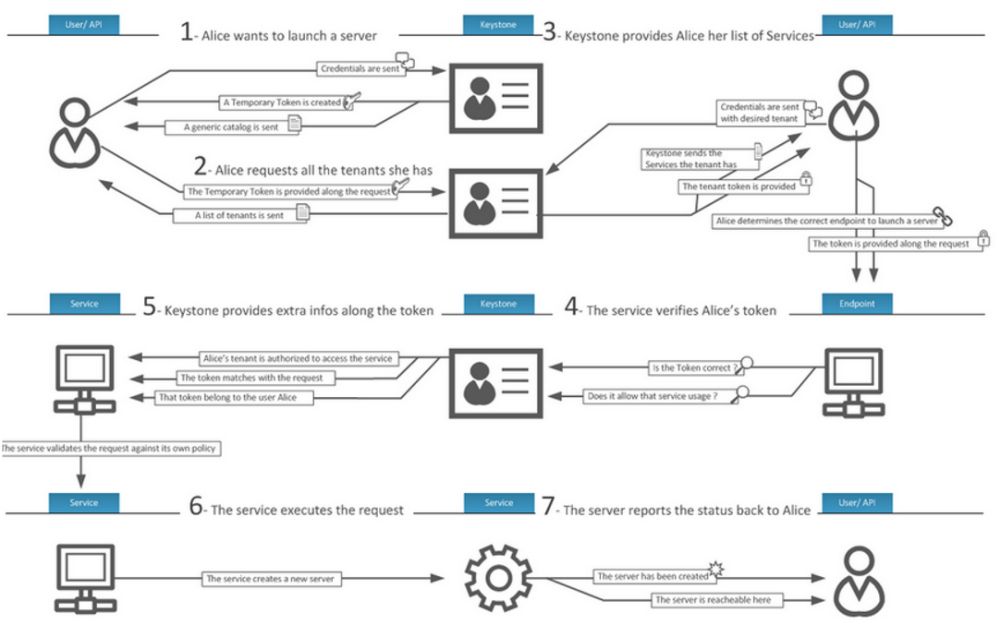
4、keystone验证的过程
认证方式(两种):用户名/密码;基于令牌(Token)
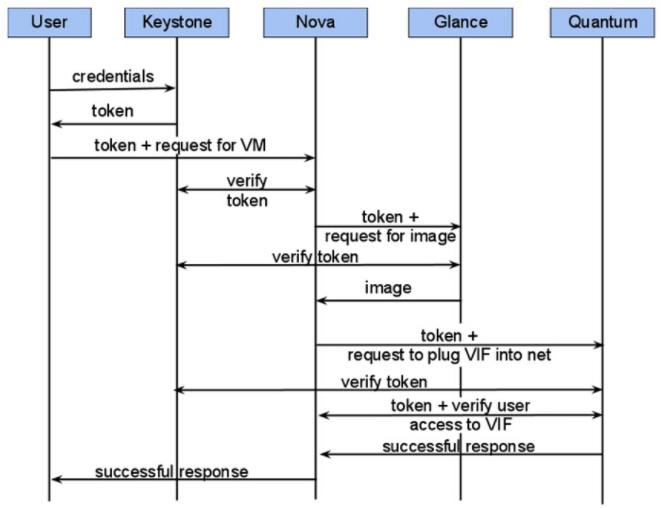
二、部署认证服务(Keystone)集群
1、创建keystone数据库(任意一个控制节点操作)
mysql -u root -p
CREATE DATABASE keystone; GRANT ALL PRIVILEGES ON keystone.* TO 'keystone'@'localhost' IDENTIFIED BY '123456'; GRANT ALL PRIVILEGES ON keystone.* TO 'keystone'@'%' IDENTIFIED BY '123456'; flush privileges; exit;
2、安装keystone
在全部控制节点安装keystone
yum install openstack-keystone httpd mod_wsgi mod_ssl -y
3、更改配置文件keystone.conf
在全部控制节点设置
# cp -rp /etc/keystone/keystone.conf{,.bak}
# egrep -v "^$|^#" /etc/keystone/keystone.conf
[DEFAULT]
[application_credential]
[assignment]
[auth]
[cache]
backend = oslo_cache.memcache_pool
enabled = true
memcache_servers = controller01:11211,controller02:11211,controller03:11211
[catalog]
[cors]
[credential]
[database]
connection = mysql+pymysql://keystone:123456@controller/keystone
[domain_config]
[endpoint_filter]
[endpoint_policy]
[eventlet_server]
[federation]
[fernet_tokens]
[healthcheck]
[identity]
[identity_mapping]
[ldap]
[matchmaker_redis]
[memcache]
[oauth1]
[oslo_messaging_amqp]
[oslo_messaging_kafka]
[oslo_messaging_notifications]
[oslo_messaging_rabbit]
[oslo_messaging_zmq]
[oslo_middleware]
[oslo_policy]
[paste_deploy]
[policy]
[profiler]
[resource]
[revoke]
[role]
[saml]
[security_compliance]
[shadow_users]
[signing]
[token]
provider = fernet
[tokenless_auth]
[trust]
[unified_limit]
配置部分解释
[DEFAULT]
...
admin_token = ADMIN_TOKEN
# ADMIN_TOKEN 替换为openssl 生成的随机字符串,例如:
admin_token = 8c67dd7baaf367136f01
在[database] 部分,配置数据库访问
[database]
...
connection = mysql+pymysql://keystone:keystone@controller/keystone
# 注意这里 controller 已经在/etc/hosts 中解析为 vip 地址
在``[token]``部分,配置Fernet UUID令牌的提供者。
[token]
...
provider = fernet
4、同步数据库
任意控制节点操作
同步数据库
su -s /bin/sh -c "keystone-manage db_sync" keystone
查看验证
mysql -h controller01 -ukeystone -p123456 -e "use keystone;show tables;"
5、初始化fernet秘钥
每个节点都需要生成fernet keys 但是三个节点的 fernet keys 必须保持一致,否则认证的时候会报错。
选定任意控制节点(controller01)做fernet秘钥初始化,在/etc/keystone/生成相关秘钥及目录
keystone-manage fernet_setup --keystone-user keystone --keystone-group keystone keystone-manage credential_setup --keystone-user keystone --keystone-group keystone
向controller02/03节点同步秘钥
scp -r /etc/keystone/fernet-keys/ /etc/keystone/credential-keys/ root@10.20.9.190:/etc/keystone/ scp -r /etc/keystone/fernet-keys/ /etc/keystone/credential-keys/ root@10.20.9.45:/etc/keystone/
同步后,注意controller02/03节点上秘钥权限
chown keystone:keystone /etc/keystone/credential-keys/ -R chown keystone:keystone /etc/keystone/fernet-keys/ -R
6、配置httpd.conf
在全部控制节点设置
cp /etc/httpd/conf/httpd.conf /etc/httpd/conf/httpd.conf.bak
sed -i "s/#ServerName www.example.com:80/ServerName ${HOSTNAME}/" /etc/httpd/conf/httpd.conf
注意不同的节点替换不同的ip地址
sed -i "s/Listen\ 80/Listen\ 10.20.9.189:80/g" /etc/httpd/conf/httpd.conf sed -i "s/Listen\ 80/Listen\ 10.20.9.190:80/g" /etc/httpd/conf/httpd.conf sed -i "s/Listen\ 80/Listen\ 10.20.9.45:80/g" /etc/httpd/conf/httpd.conf
7、配置wsgi-keystone.conf
在全部控制节点操作
1、复制wsgi-keystone.conf文件;或者针对wsgi-keystone.conf创建软链接
cp /usr/share/keystone/wsgi-keystone.conf /etc/httpd/conf.d/
2、修改wsgi-keystone.conf文件,注意各节点对应的ip地址或主机名等
sed -i "s/Listen\ 5000/Listen\ 10.20.9.189:5000/g" /etc/httpd/conf.d/wsgi-keystone.conf sed -i "s/Listen\ 35357/Listen\ 10.20.9.189:35357/g" /etc/httpd/conf.d/wsgi-keystone.conf sed -i "s/*:5000/10.20.9.189:5000/g" /etc/httpd/conf.d/wsgi-keystone.conf sed -i "s/*:35357/10.20.9.189:35357/g" /etc/httpd/conf.d/wsgi-keystone.conf
8、认证引导
任意控制节点操作
初始化admin用户(管理用户)与密码,3种api端点,服务实体可用区等
keystone-manage bootstrap --bootstrap-password admin_pass \ --bootstrap-admin-url http://controller:35357/v3/ \ --bootstrap-internal-url http://controller:5000/v3/ \ --bootstrap-public-url http://controller:5000/v3/ \ --bootstrap-region-id RegionTest
9、启动服务
在全部控制节点操作
systemctl enable httpd.service systemctl restart httpd.service systemctl status httpd.service
10、openstack client 环境变量脚本
1、admin-openrc
openstack client环境脚本定义client调用openstack api环境变量,以方便api的调用(不必在命令行中携带环境变量);
根据不同的用户角色,需要定义不同的脚本;
这里以“认证引导”章节定义的admin用户为例,设置其环境脚本,再根据需要分发到需要运行openstack client工具的节点;
一般将脚本创建在用户主目录
cat>admin-openrc<<EOF export OS_PROJECT_DOMAIN_NAME=Default export OS_USER_DOMAIN_NAME=Default export OS_PROJECT_NAME=admin export OS_USERNAME=admin export OS_PASSWORD=admin_pass export OS_AUTH_URL=http://controller:5000/v3 # 从安全角度考虑,一般不对client暴露admin-api,这里admin-api与public-api共用1个vip地址 # export OS_AUTH_URL=http://controller:35357/v3 export OS_IDENTITY_API_VERSION=3 export OS_IMAGE_API_VERSION=2 EOF chmod u+x admin-openrc
使变量生效
source admin-openrc
验证
openstack token issue
2、demo-openrc
同admin-openrc,注意project/user/password的区别
cat>demo-openrc<<EOF export OS_PROJECT_DOMAIN_NAME=Default export OS_USER_DOMAIN_NAME=Default export OS_PROJECT_NAME=demo export OS_USERNAME=demo export OS_PASSWORD=demo_pass export OS_AUTH_URL=http://controller:5000/v3 export OS_IDENTITY_API_VERSION=3 export OS_IMAGE_API_VERSION=2 EOF chmod u+x demo-openrc
使变量生效
source demo-openrc
验证
openstack token issue
3、分发脚本
scp admin-openrc demo-openrc root@10.20.9.190:~/ scp admin-openrc demo-openrc root@10.20.9.45:~/
11、创建domain, projects, users, 与roles
1、domain
projrct/user等基于domain存在;
在”认证引导”章节中,初始化admin用户即生成”default” domain
[root@controller01 ~]# openstack domain list +---------+---------+---------+--------------------+ | ID | Name | Enabled | Description | +---------+---------+---------+--------------------+ | default | Default | True | The default domain | +---------+---------+---------+--------------------+
如果需要生成新的domain
[root@controller01 ~]# openstack domain create --description "An Example Domain" example +-------------+----------------------------------+ | Field | Value | +-------------+----------------------------------+ | description | An Example Domain | | enabled | True | | id | e2ad8bb0985b42eaa2640102a1f04dc9 | | name | example | | tags | [] | +-------------+----------------------------------+ [root@controller01 ~]# openstack domain list +----------------------------------+---------+---------+--------------------+ | ID | Name | Enabled | Description | +----------------------------------+---------+---------+--------------------+ | default | Default | True | The default domain | | e2ad8bb0985b42eaa2640102a1f04dc9 | example | True | An Example Domain | +----------------------------------+---------+---------+--------------------+
若如下错误,说明环境变量没有设置对(请检查10)
错误一:
openstack domain list openstack: 'domain list' is not an openstack command. See 'openstack --help'. Did you mean one of these?
错误二:
Missing value auth-url required for auth plugin password
2、projects
project属于某个domain;
以创建demo项目为例,demo项目属于”default” domain
[root@controller01 ~]# openstack project create --domain default --description "Demo Project" demo +-------------+----------------------------------+ | Field | Value | +-------------+----------------------------------+ | description | Demo Project | | domain_id | default | | enabled | True | | id | a271f4c73cdc4780a0c3ee5154f12171 | | is_domain | False | | name | demo | | parent_id | default | | tags | [] | +-------------+----------------------------------+
3、users
user属于某个domain;
以创建demo用户为例,demo用户属于”default” domain
[root@controller01 ~]# openstack user create --domain default --password=demo_pass demo
+---------------------+----------------------------------+
| Field | Value |
+---------------------+----------------------------------+
| domain_id | default |
| enabled | True |
| id | 335788ba925b4ceb8c3a75f605a6d6ce |
| name | demo |
| options | {} |
| password_expires_at | None |
+---------------------+----------------------------------+
4、roles
创建普通用户角色(区别于admin用户)
[root@controller01 ~]# openstack role create user +-----------+----------------------------------+ | Field | Value | +-----------+----------------------------------+ | domain_id | None | | id | 59066f0348464b9d807f0aeaee4bb225 | | name | user | +-----------+----------------------------------+
向demo项目的demo用户赋予user权限,这个没有返回值
openstack role add --project demo --user demo user
查看权限分配
[root@controller01 ~]# openstack user list +----------------------------------+-------+ | ID | Name | +----------------------------------+-------+ | 335788ba925b4ceb8c3a75f605a6d6ce | demo | | 5eaaba0a94934af1b78fa7fd37c57e67 | admin | +----------------------------------+-------+ [root@controller01 ~]# openstack role list +----------------------------------+-------+ | ID | Name | +----------------------------------+-------+ | 298192bad24143d9a1bef54837277e2d | admin | | 59066f0348464b9d807f0aeaee4bb225 | user | +----------------------------------+-------+ [root@controller01 ~]# openstack role assignment list +----------------------------------+----------------------------------+-------+----------------------------------+--------+-----------+ | Role | User | Group | Project | Domain | Inherited | +----------------------------------+----------------------------------+-------+----------------------------------+--------+-----------+ | 59066f0348464b9d807f0aeaee4bb225 | 335788ba925b4ceb8c3a75f605a6d6ce | | a271f4c73cdc4780a0c3ee5154f12171 | | False | | 298192bad24143d9a1bef54837277e2d | 5eaaba0a94934af1b78fa7fd37c57e67 | | 109783812ec540e982640e382f967065 | | False | | 298192bad24143d9a1bef54837277e2d | 5eaaba0a94934af1b78fa7fd37c57e67 | | | | False | +----------------------------------+----------------------------------+-------+----------------------------------+--------+-----------+
12、设置pcs资源
在任意控制节点操作
pcs实际控制的是各节点system unit控制的httpd服务(没有返回值)
pcs resource create openstack-keystone systemd:httpd --clone interleave=true
验证
[root@controller01 ~]# pcs resource
vip (ocf::heartbeat:IPaddr2): Started controller01
Clone Set: lb-haproxy-clone [lb-haproxy]
Started: [ controller01 ]
Stopped: [ controller02 controller03 ]
Clone Set: openstack-keystone-clone [openstack-keystone]
Started: [ controller01 controller02 controller03 ]