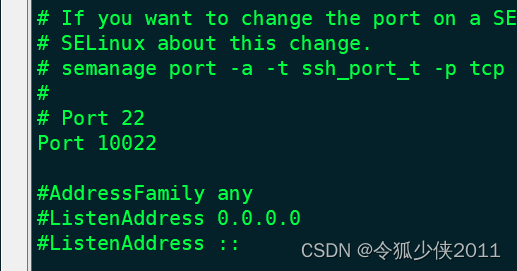
- 配置SSH服务器的管理网口IP地址。
<HUAWEI> system-view [HUAWEI] sysname SSH Server [SSH Server] interface meth 0/0/0 [SSH Server-MEth0/0/0] ip address 10.248.103.194 255.255.255.0 [SSH Server-MEth0/0/0] quit
- 在SSH服务器端生成本地密钥对。
[SSH Server] rsa local-key-pair create The key name will be:Host The range of public key size is (2048, 4096). NOTE: Key pair generation will take a short while. Please input the modulus [default = 3072]:3072
- 配置SSH服务器的VTY用户界面。
[SSH Server] user-interface vty 0 4 [SSH Server-ui-vty0-4] authentication-mode aaa [SSH Server-ui-vty0-4] protocol inbound ssh [SSH Server-ui-vty0-4] quit

若配置登录协议为SSH,则设备将自动禁止Telnet功能。
- 在服务器端创建本地用户,并配置用户服务方式。
[SSH Server] aaa [SSH Server-aaa] local-user admin123 password Please configure the login password (8-128) It is recommended that the password consist of at least 2 types of characters, including lowercase letters, uppercase letters, numerals and special characters. Please enter password: Please confirm password: Info: Add a new user. [SSH Server-aaa] local-user admin123 service-type ssh [SSH Server-aaa] local-user admin123 privilege level 3 [SSH Server-aaa] quit
- 在服务器端创建SSH用户,并配置认证方式。
[SSH Server] ssh user admin123 [SSH Server] ssh user admin123 authentication-type rsa
- 配置SSH服务器的公钥算法、加密算法、密钥交换算法列表、HMAC认证算法和最小密钥长度。
[SSH Server] ssh server cipher aes128_ctr aes256_ctr aes192_ctr aes128_gcm aes256_gcm [SSH Server] ssh server hmac sha2_256 sha2_512 [SSH Server] ssh server key-exchange dh_group_exchange_sha256 dh_group16_sha512 [SSH Server] ssh server publickey rsa_sha2_256 rsa_sha2_512 [SSH Server] ssh server dh-exchange min-len 3072
- SSH客户端使用OpenSSH创建RSA密钥对,并将密钥对中的公钥拷贝至SSH服务器。
进入Windows的命令行提示符,创建RSA密钥对,并保存到本地id_rsa.pub文件中(以下内容仅为示例)。
C:\Users\User1> ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (C:\Users\User1/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in C:\Users\User1/.ssh/id_rsa. Your public key has been saved in C:\Users\User1/.ssh/id_rsa.pub. The key fingerprint is: SHA256:c43yubJjCUjY3JqH0aVZwJFM3gWJcH4YI5+4HUDAIqo The key's randomart image is: +---[RSA 3072]----+ | ..o==B=.o. | |o . O=*+. | |o. +.oB=o | |. . =o=o o | |. ..*. S o . | |E = o = . | | . . .o | | = . | | ..+. | +----[SHA256]-----+
- SSH服务器编辑SSH客户端OpenSSH生成的公钥,并将编辑后的公钥分配给SSH用户。
[SSH Server] rsa peer-public-key rsa01 encoding-type openssh [SSH Server-rsa-public-key] public-key-code begin [SSH Server-rsa-public-key-rsa-key-code] ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCg5Ag490i6ilB7QuCVb35B8RJEh1DIYB88h2p1qjdh7qdMQv8rpJaVAgQWxwzKZO0XdFuz4ReGQzTCSf7Det7Ajicddw3qi+6P8hRqZj6MPdLg/o3RN4aPCfr/LFWCwqJ3gWGHlOC7qqjRk+6pySVoiWcSk5/elBkU7WVk/cSWrt4qFXJV373OCesKcEVeDvAa1Tvx6L3LQroBqUO0EXzDgOthPCmOqiqvS5h3JipzqVsesdSKjeInooCQzSOv5eePpBcFcIvU6wFiLIZ5vnf6YtypgTVzHuje/sh4xM7Iuuon7AYXKHT8NpO9jd9zA/lKaRPXyDtei1O1Bt/5lxnn [SSH Server-rsa-public-key-rsa-key-code] public-key-code end [SSH Server-key-code] peer-public-key end [SSH Server] ssh user admin123 assign rsa-key rsa01
- 使能STelnet功能,并配置用户的服务类型为STelnet。
[SSH Server] stelnet server enable [SSH Server] ssh server-source all-interface [SSH Server] ssh user admin123 service-type stelnet
- 配置ACL规则。
[SSH Server] acl 2000 [SSH Server-acl4-basic-2000] rule permit source 10.248.103.0 24 [SSH Server-acl4-basic-2000] quit [SSH Server] ssh server acl 2000
检查配置结果
客户端通过OpenSSH软件登录SSH服务器。进入Windows的命令行提示符,执行OpenSSH命令,通过STelnet方式访问设备。
C:\Users\User1> ssh admin123@10.248.103.194
Enter passphrase for key 'C:\Users\User/.ssh/id_rsa':
Info: The max number of VTY users is 21, the number of current VTY users online is 4, and total number of terminal users online is 4.
The current login time is 2020-12-15 15:58:03.
<SSH Server>
配置脚本
# sysname SSH Server # acl number 2000 rule 5 permit source 10.248.103.0 0.0.0.255 # rsa peer-public-key rsa01 encoding-type openssh public-key-code begin ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCg5Ag490i6ilB7QuCVb35B8RJEh1DIYB88h2p1qjdh7qdMQv8rpJaVAgQWxwzKZO0XdFuz4ReGQzTCSf7Det7Ajicddw3qi+6P8hRqZj6MPdLg/o3RN4aPCfr/LFWCwqJ3gWGHlOC7qqjRk+6pySVoiWcSk5/elBkU7WVk/cSWrt4qFXJV373OCesKcEVeDvAa1Tvx6L3LQroBqUO0EXzDgOthPCmOqiqvS5h3JipzqVsesdSKjeInooCQzSOv5eePpBcFcIvU6wFiLIZ5vnf6YtypgTVzHuje/sh4xM7Iuuon7AYXKHT8NpO9jd9zA/lKaRPXyDtei1O1Bt/5lxnn rsa-key public-key-code end peer-public-key end # aaa local-user admin123 password irreversible-cipher $1d$+,JS+))\\2$KVNj(.3`_5x0FCKGv}H&.kUTI`Ff&H*eBqO.ua>)$ local-user admin123 service-type terminal ssh local-user admin123 privilege level 3 # interface MEth0/0/0 ip address 10.248.103.194 255.255.255.0 # stelnet server enable ssh user admin123 ssh user admin123 authentication-type rsa ssh user admin123 assign rsa-key rsa01 ssh user admin123 service-type stelnet ssh server-source all-interface ssh server acl 2000 # ssh server cipher aes128_ctr aes256_ctr aes192_ctr aes128_gcm aes256_gcm ssh server hmac sha2_256 sha2_512 ssh server key-exchange dh_group_exchange_sha256 dh_group16_sha512 ssh server publickey rsa_sha2_256 rsa_sha2_512 ssh server dh-exchange min-len 3072 # user-interface vty 0 4 authentication-mode aaa protocol inbound ssh # return