目录
- 练习题
- 1. 显示当前的iptables规则
- 2. 允许所有来自192.168.1.0/24的TCP流量到本机的22端口(SSH)
- 3. 禁止所有来自10.0.0.0/8的ICMP流量
- 4. 允许所有出站流量
- 5. 拒绝所有来自外部的HTTP流量(80端口,tcp协议)
- 6. 删除INPUT链中的最后一条规则
- 7. 将默认策略设置为拒绝所有输入流量
- 9. 允许UDP流量从192.168.2.0/24到本机的53端口(DNS)
- 10. 保存当前的iptables规则到文件/etc/iptables/rules.v4(需要iptables-save命令)
- 11. 假设你有一个允许所有HTTP流量(80端口)的规则,但现在你只想允许来自192.168.0.0/16的HTTP流量,你应该如何修改这个规则?
- 12. 你想要允许某个特定的IP地址(例如192.168.1.100)访问你服务器上所有的服务,应如何设置规则?
练习题
1. 显示当前的iptables规则
[root@localhost ~]
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
DOCKER-USER all -- anywhere anywhere
DOCKER-ISOLATION-STAGE-1 all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
DOCKER all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain DOCKER (1 references)
target prot opt source destination
ACCEPT tcp -- anywhere 172.17.0.3 tcp dpt:radan-http
Chain DOCKER-ISOLATION-STAGE-1 (1 references)
target prot opt source destination
DOCKER-ISOLATION-STAGE-2 all -- anywhere anywhere
RETURN all -- anywhere anywhere
Chain DOCKER-ISOLATION-STAGE-2 (1 references)
target prot opt source destination
DROP all -- anywhere anywhere
RETURN all -- anywhere anywhere
Chain DOCKER-USER (1 references)
target prot opt source destination
RETURN all -- anywhere anywhere
2. 允许所有来自192.168.1.0/24的TCP流量到本机的22端口(SSH)
[root@localhost ~]
[root@localhost ~]
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 192.168.1.0/24 anywhere tcp dpt:ssh
3. 禁止所有来自10.0.0.0/8的ICMP流量
[root@localhost ~]
[root@localhost ~]
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 192.168.1.0/24 anywhere tcp dpt:ssh
DROP icmp -- 10.0.0.0/8 anywhere
4. 允许所有出站流量
[root@localhost ~]
[root@localhost ~]
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
5. 拒绝所有来自外部的HTTP流量(80端口,tcp协议)
[root@localhost ~]
[root@localhost ~]
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 192.168.1.0/24 anywhere tcp dpt:ssh
DROP icmp -- 10.0.0.0/8 anywhere
REJECT tcp -- anywhere anywhere tcp dpt:http reject-with icmp-port-unreachable
6. 删除INPUT链中的最后一条规则
iptables -D INPUT -1
注意:-1 表示删除最后一条规则。
[root@localhost ~]
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 ACCEPT tcp -- 192.168.1.0/24 anywhere tcp dpt:ssh
2 DROP icmp -- 10.0.0.0/8 anywhere
3 REJECT tcp -- anywhere anywhere tcp dpt:http reject-with icmp-port-unreachable
[root@localhost ~]
[root@localhost ~]
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 192.168.1.0/24 anywhere tcp dpt:ssh
DROP icmp -- 10.0.0.0/8 anywhere
7. 将默认策略设置为拒绝所有输入流量
iptables -P INPUT DROP
[root@localhost ~]
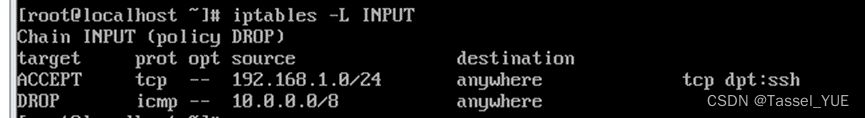
9. 允许UDP流量从192.168.2.0/24到本机的53端口(DNS)
iptables -A INPUT -s 192.168.2.0/24 -p udp --dport 53 -j ACCEPT
[root@localhost ~]
[root@localhost ~]
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 192.168.1.0/24 anywhere tcp dpt:ssh
DROP icmp -- 10.0.0.0/8 anywhere
ACCEPT udp -- 192.168.2.0/24 anywhere udp dpt:domain
10. 保存当前的iptables规则到文件/etc/iptables/rules.v4(需要iptables-save命令)
iptables-save > /etc/iptables/rules.v4
[root@localhost ~]
[root@localhost ~]
[root@localhost ~]
*nat
:PREROUTING ACCEPT [22:2930]
:INPUT ACCEPT [22:2930]
:OUTPUT ACCEPT [167:14376]
:POSTROUTING ACCEPT [180:15052]
:DOCKER - [0:0]
-A PREROUTING -m addrtype --dst-type LOCAL -j DOCKER
-A OUTPUT ! -d 127.0.0.0/8 -m addrtype --dst-type LOCAL -j DOCKER
-A POSTROUTING -s 172.17.0.0/16 ! -o docker0 -j MASQUERADE
-A POSTROUTING -s 172.17.0.3/32 -d 172.17.0.3/32 -p tcp -m tcp --dport 8088 -j MASQUERADE
-A DOCKER -i docker0 -j RETURN
-A DOCKER ! -i docker0 -p tcp -m tcp --dport 8088 -j DNAT --to-destination 172.17.0.3:8088
COMMIT
*mangle
:PREROUTING ACCEPT [37873:257277525]
:INPUT ACCEPT [30364:255656388]
:FORWARD ACCEPT [7509:1621137]
:OUTPUT ACCEPT [25976:1343905]
:POSTROUTING ACCEPT [33485:2965042]
COMMIT
*raw
:PREROUTING ACCEPT [37873:257277525]
:OUTPUT ACCEPT [25976:1343905]
COMMIT
*security
:INPUT ACCEPT [30332:255653088]
:FORWARD ACCEPT [7509:1621137]
:OUTPUT ACCEPT [25976:1343905]
COMMIT
*filter
:INPUT ACCEPT [344:30199]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:DOCKER - [0:0]
:DOCKER-ISOLATION-STAGE-1 - [0:0]
:DOCKER-ISOLATION-STAGE-2 - [0:0]
:DOCKER-USER - [0:0]
-A INPUT -s 192.168.1.0/24 -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -s 10.0.0.0/8 -p icmp -j DROP
-A INPUT -s 192.168.2.0/24 -p udp -m udp --dport 53 -j ACCEPT
-A FORWARD -j DOCKER-USER
-A FORWARD -j DOCKER-ISOLATION-STAGE-1
-A FORWARD -o docker0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -o docker0 -j DOCKER
-A FORWARD -i docker0 ! -o docker0 -j ACCEPT
-A FORWARD -i docker0 -o docker0 -j ACCEPT
-A OUTPUT -j ACCEPT
-A OUTPUT -j ACCEPT
-A DOCKER -d 172.17.0.3/32 ! -i docker0 -o docker0 -p tcp -m tcp --dport 8088 -j ACCEPT
-A DOCKER-ISOLATION-STAGE-1 -i docker0 ! -o docker0 -j DOCKER-ISOLATION-STAGE-2
-A DOCKER-ISOLATION-STAGE-1 -j RETURN
-A DOCKER-ISOLATION-STAGE-2 -o docker0 -j DROP
-A DOCKER-ISOLATION-STAGE-2 -j RETURN
-A DOCKER-USER -j RETURN
COMMIT
11. 假设你有一个允许所有HTTP流量(80端口)的规则,但现在你只想允许来自192.168.0.0/16的HTTP流量,你应该如何修改这个规则?
- 先找到并删除旧的规则(假设它是INPUT链中的第3条规则):
iptables -D INPUT 3
iptables -A INPUT -s 192.168.0.0/16 -p tcp --dport 80 -j ACCEPT
[root@localhost ~]
[root@localhost ~]
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 192.168.1.0/24 anywhere tcp dpt:ssh
DROP icmp -- 10.0.0.0/8 anywhere
ACCEPT udp -- 192.168.2.0/24 anywhere udp dpt:domain
ACCEPT tcp -- 192.168.0.0/16 anywhere tcp dpt:http
12. 你想要允许某个特定的IP地址(例如192.168.1.100)访问你服务器上所有的服务,应如何设置规则?
[root@localhost ~]
[root@localhost ~]
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 192.168.1.0/24 anywhere tcp dpt:ssh
DROP icmp -- 10.0.0.0/8 anywhere
ACCEPT udp -- 192.168.2.0/24 anywhere udp dpt:domain
ACCEPT tcp -- 192.168.0.0/16 anywhere tcp dpt:http
ACCEPT all -- 192.168.1.100 anywhere