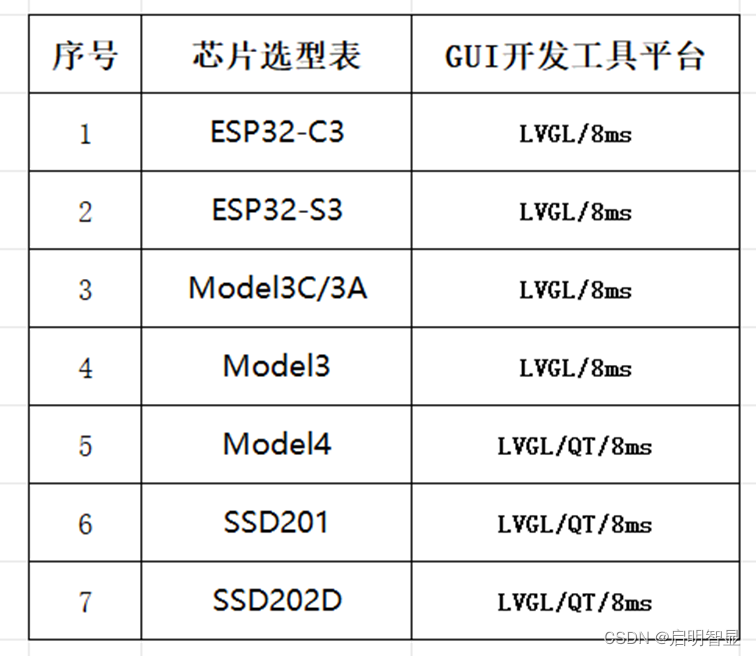
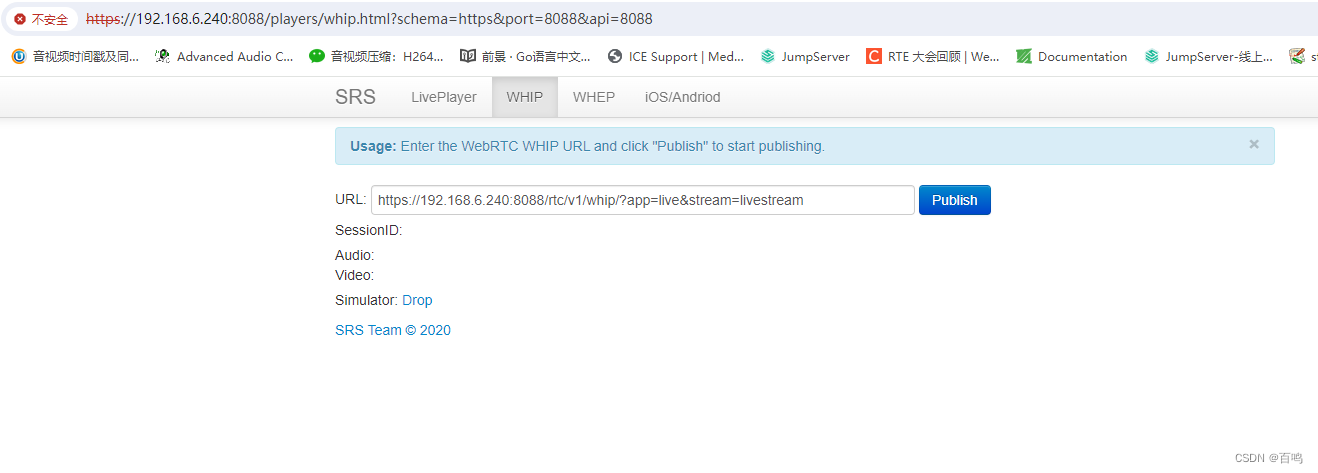
whip 報錯 404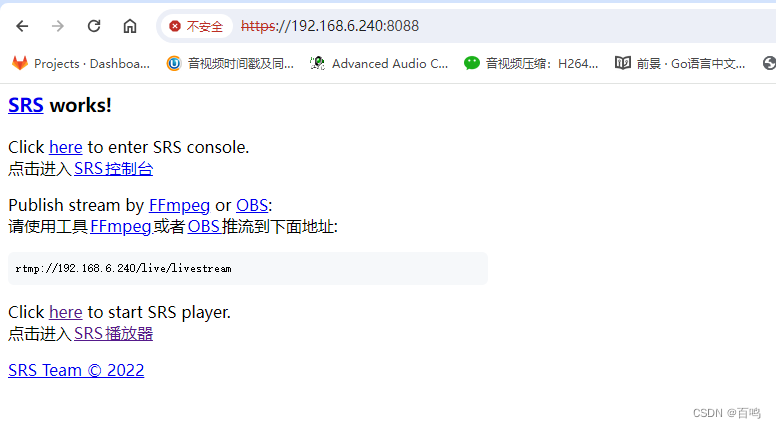
webrtc推流 小窗口一闪而过,然后查看f12回复404的报错信息
chrome版本:
正在检查更新
版本 123.0.6312.123(正式版本) (64 位)
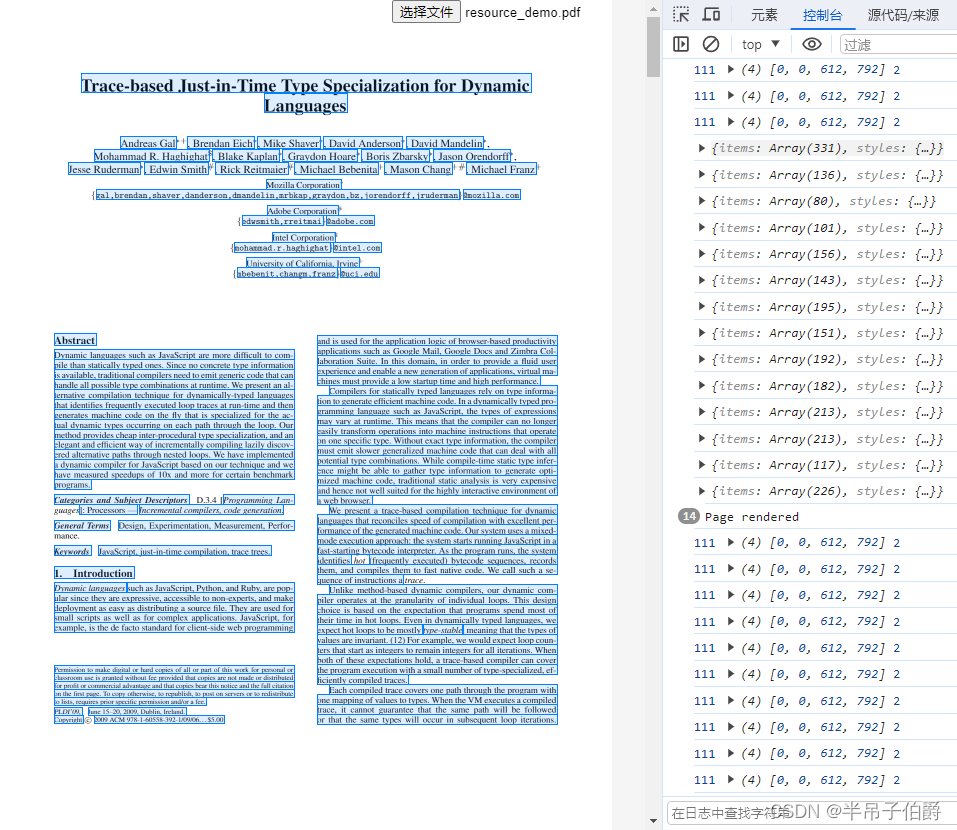
centos 7.9 源码安装部署,
代码分支5.0 完全按照官方的默认的文档编译运行:
CANDIDATE="192.168.6.240" && ./objs/srs -c conf/https.rtc.conf 8000/udp
通过nc测试没有问题
[root@paas-dev-srs01 ~]# nc -vuz 192.168.6.240 8088
Ncat: Version 7.50 ( https://nmap.org/ncat )
Ncat: Connected to 192.168.6.240:8088.
Ncat: Connection refused.
查看后台日志:典型的报错信息:[2024-04-17 14:01:23.248][ERROR][41358][k5810747][0] serve error code=4042(HttpsHandshake)(Failed to do handshake for HTTPS) : start : handshake : handshake r0=-1, r1=1
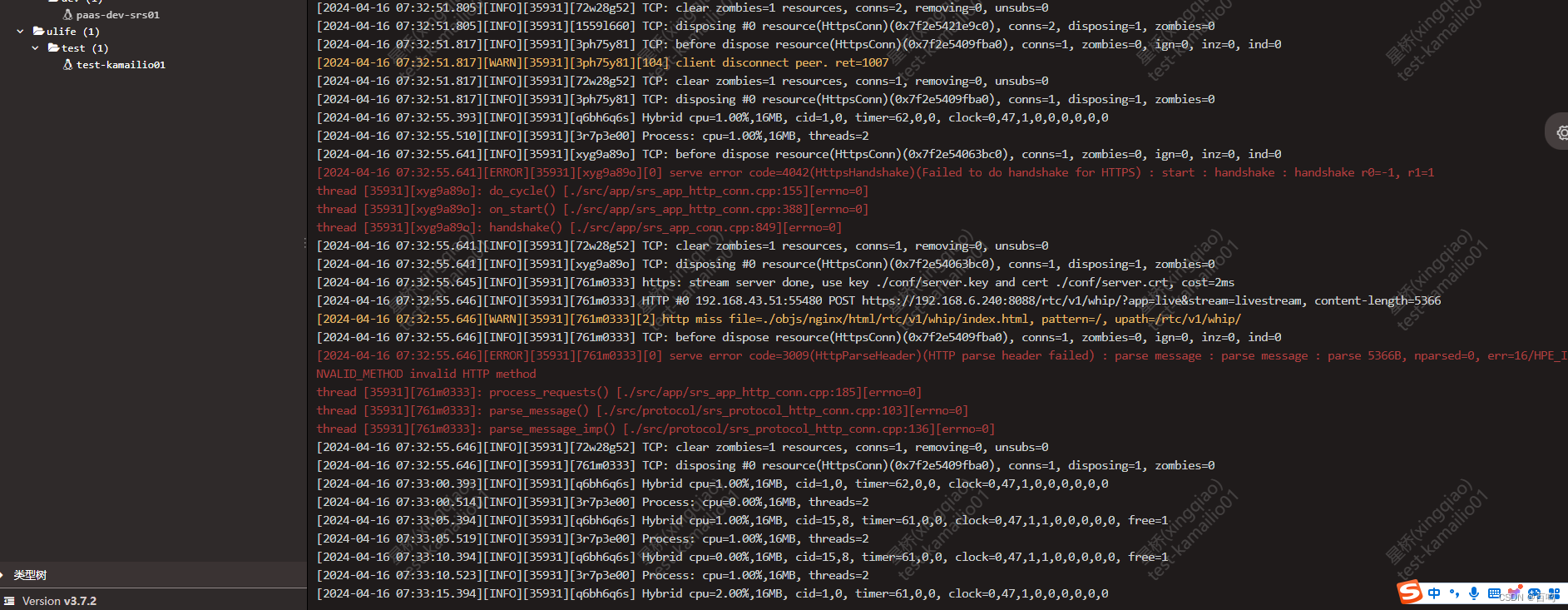
使用的是配置文件中默认的证书
后续尝试的方案总结如下:
1. 若是保持统一走8088端口的话,那就增加一个nginx代理的操作,参照文档如何给srs配置https协议,并通过nginx转发请求访问到srs_srs 配置nginx代理-CSDN博客,在windows下操作成功
2.whip和whep的交互不走8088端口,走另一个http api的监听端口1990 https://192.168.6.240:1990/rtc/v1/whip/?app=live&stream=livestream 和 https://192.168.6.240:1990/rtc/v1/whep/?app=live&stream=livestream
srs的配置文件:
[root@test-kamailio01 trunk]# cat conf/https.rtc.conf
listen 1935;
max_connections 1000;
daemon off;
srs_log_tank console;
http_server {
enabled on;
listen 8080;
dir ./objs/nginx/html;
https {
enabled on;
listen 8088;
key ./cert/server.key;
cert ./cert/server.crt;
}
}
http_api {
enabled on;
listen 1985;
https {
enabled on;
listen 1990;
key ./cert/server.key;
cert ./cert/server.crt;
}
}
stats {
network 0;
}
rtc_server {
enabled on;
listen 8000; # UDP port
# @see https://ossrs.net/lts/zh-cn/docs/v4/doc/webrtc#config-candidate
candidate 192.168.6.240;
}
vhost __defaultVhost__ {
rtc {
enabled on;
# @see https://ossrs.net/lts/zh-cn/docs/v4/doc/webrtc#rtmp-to-rtc
rtmp_to_rtc on;
# @see https://ossrs.net/lts/zh-cn/docs/v4/doc/webrtc#rtc-to-rtmp
rtc_to_rtmp on;
}
http_remux {
enabled on;
mount [vhost]/[app]/[stream].flv;
}
}签名生成:
openssl genrsa -out server.key 2048 && subj="/C=CN/ST=Beijing/L=Beijing/O=Me/OU=Me/CN=192.168.6.240" && openssl req -new -x509 -signkey server.key -out server.crt -days 3650 -subj $subj